- Главная
- Информатика
- Lecture 1. Network. Fundamentals

Содержание
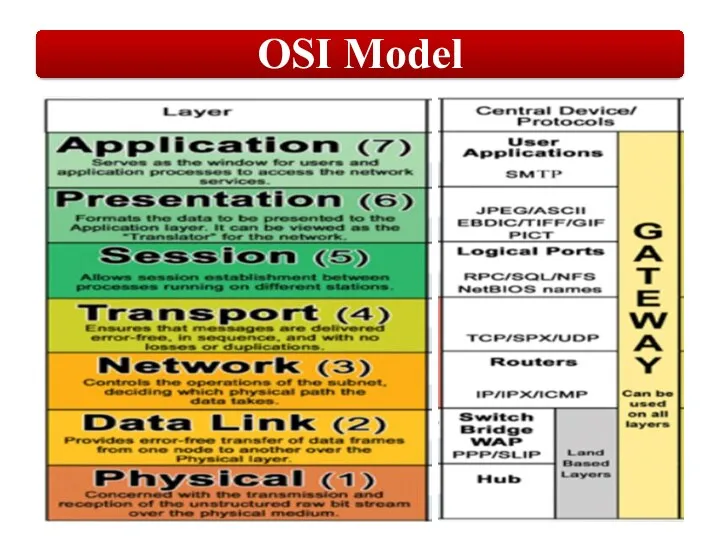
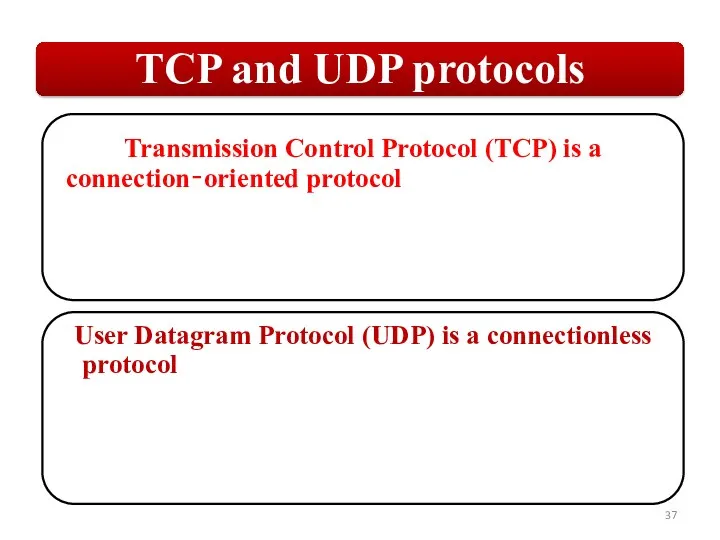
Слайд 2
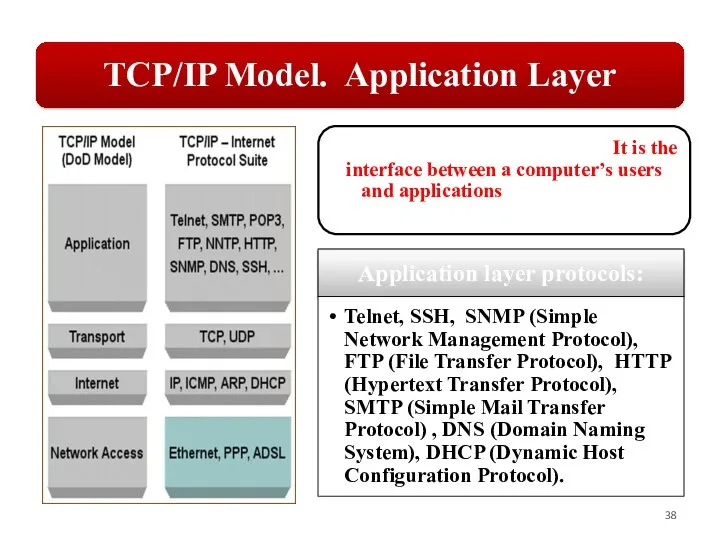
Слайд 3
Слайд 4
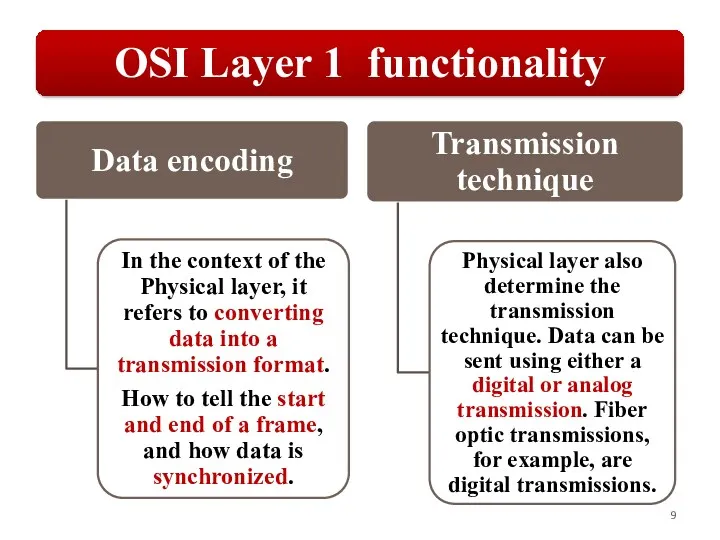
Слайд 5
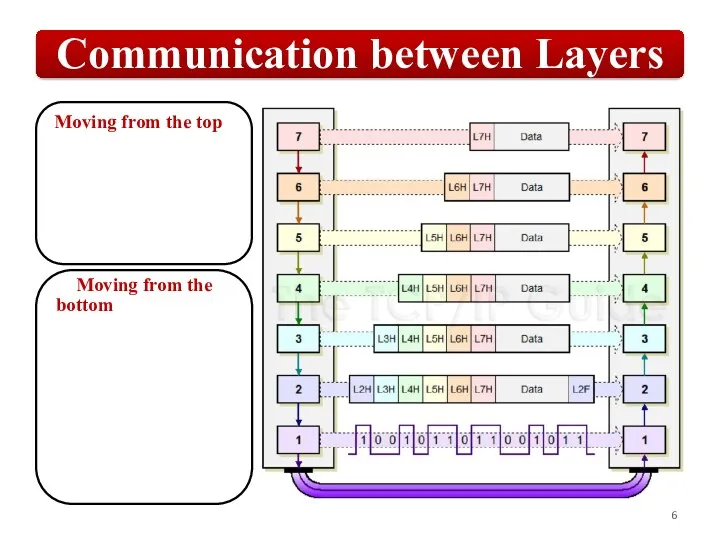
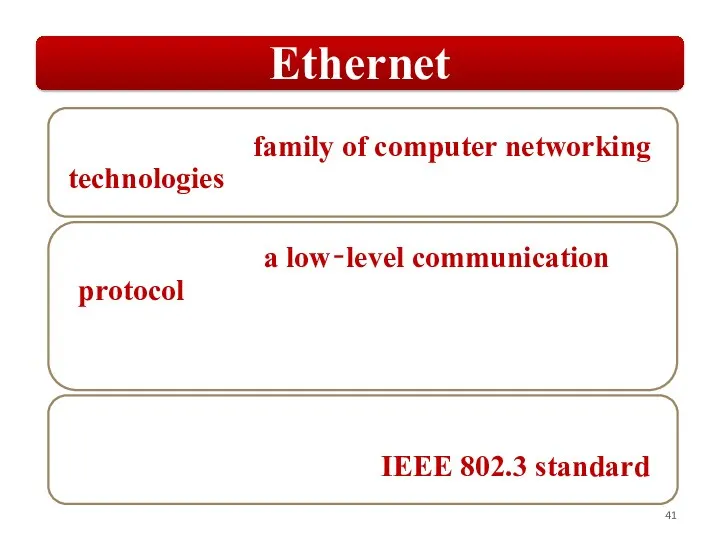
Слайд 6
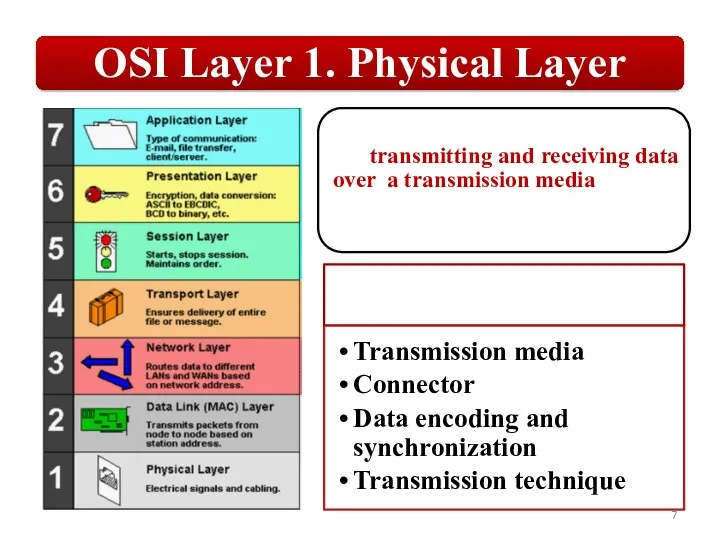
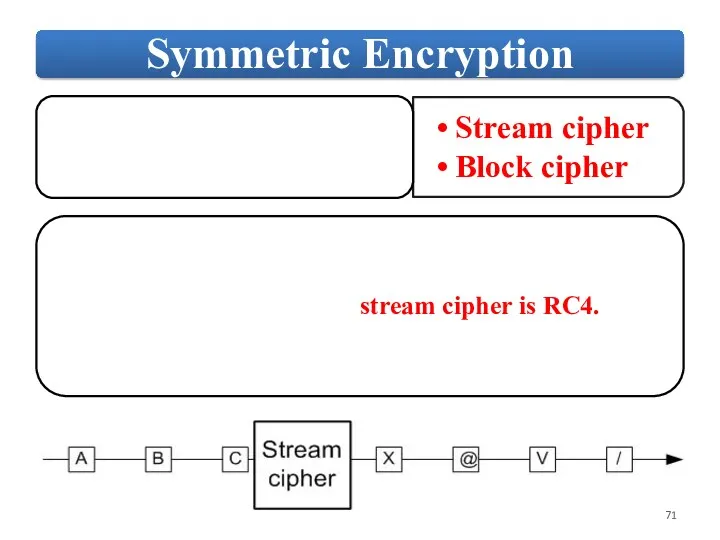
Слайд 7
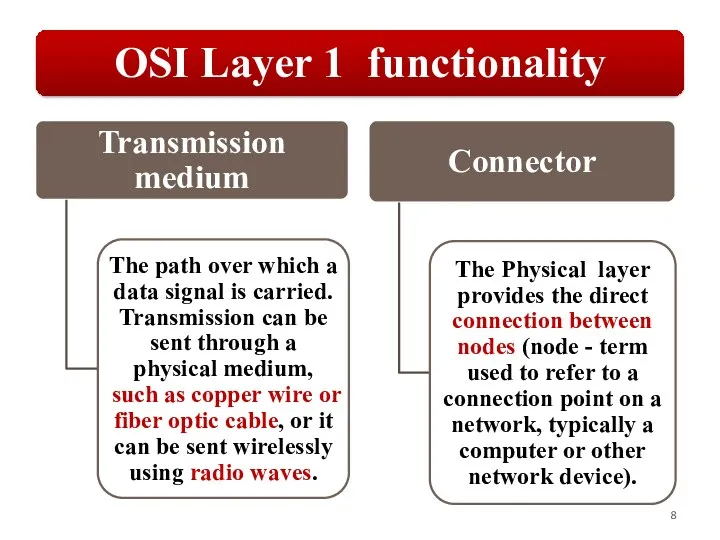
Слайд 8
Слайд 9
Слайд 10
Слайд 11
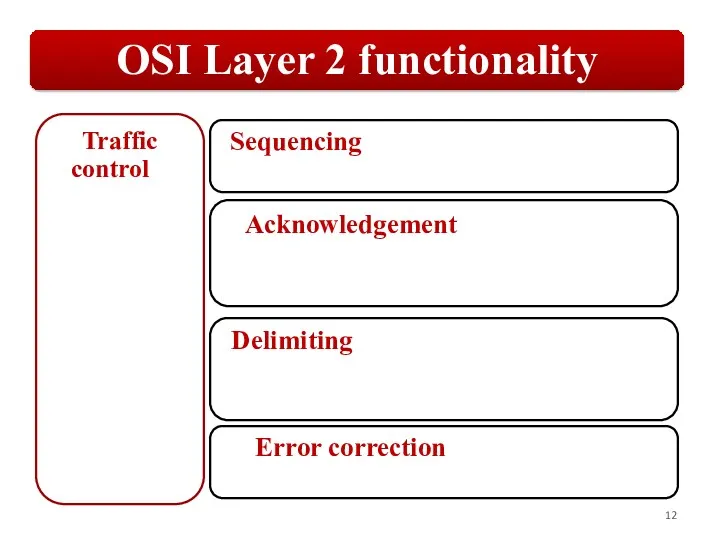
Слайд 12
Слайд 13
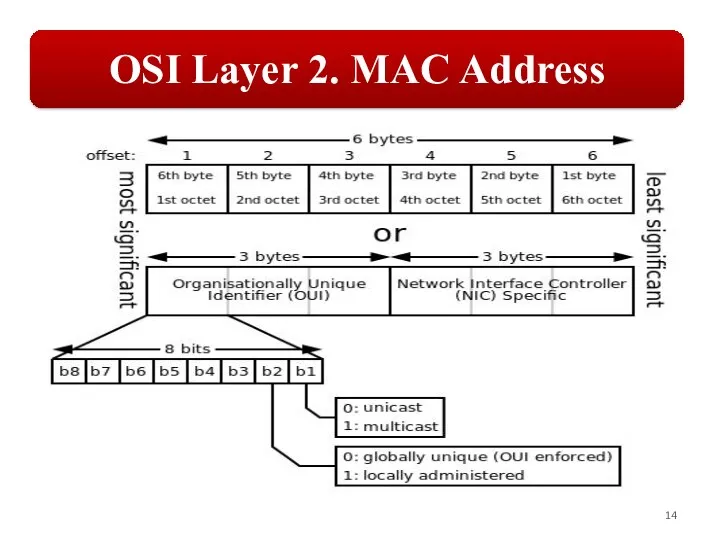
Слайд 14
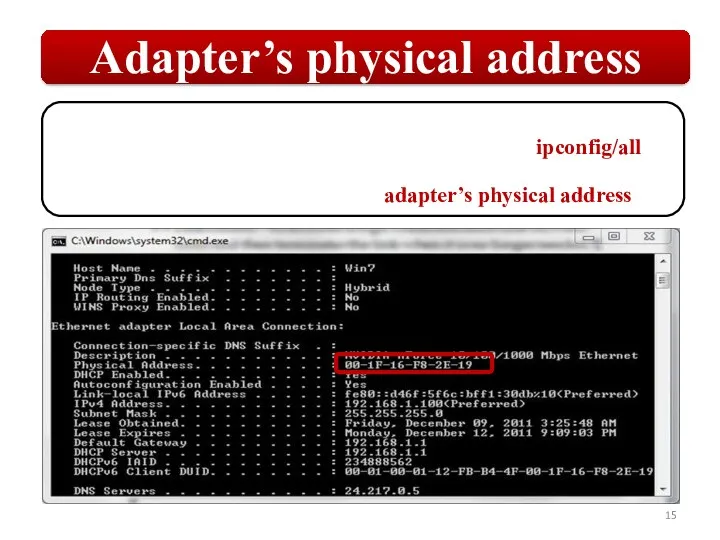
Слайд 15
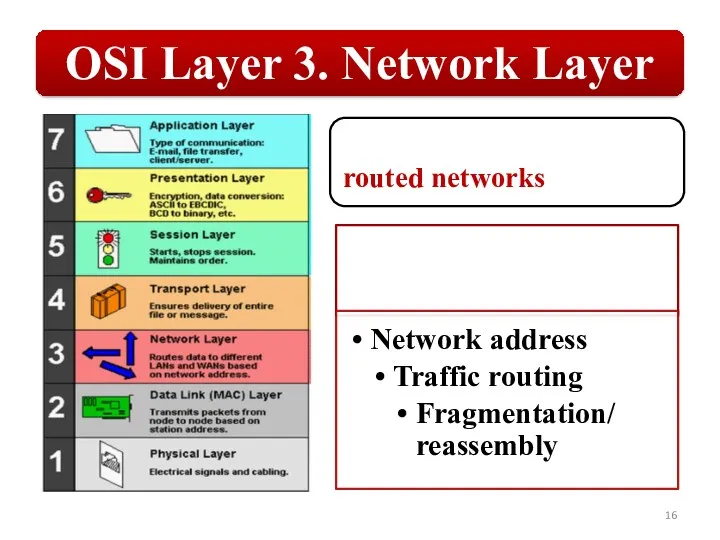
Слайд 16
Слайд 17
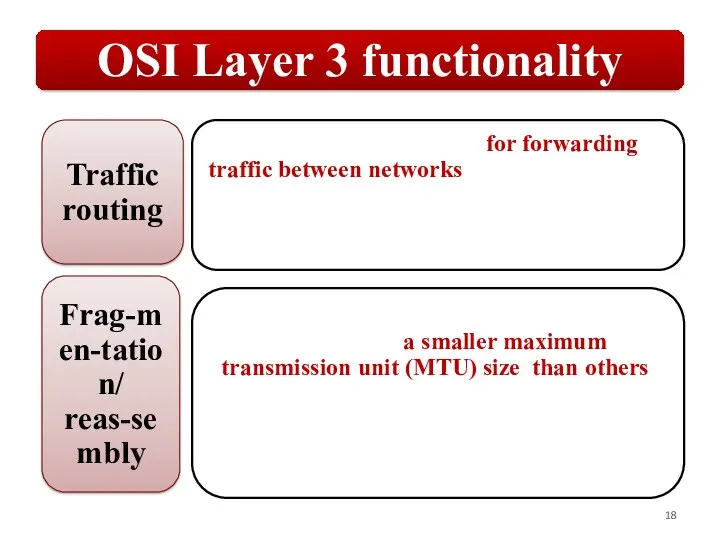
Слайд 18
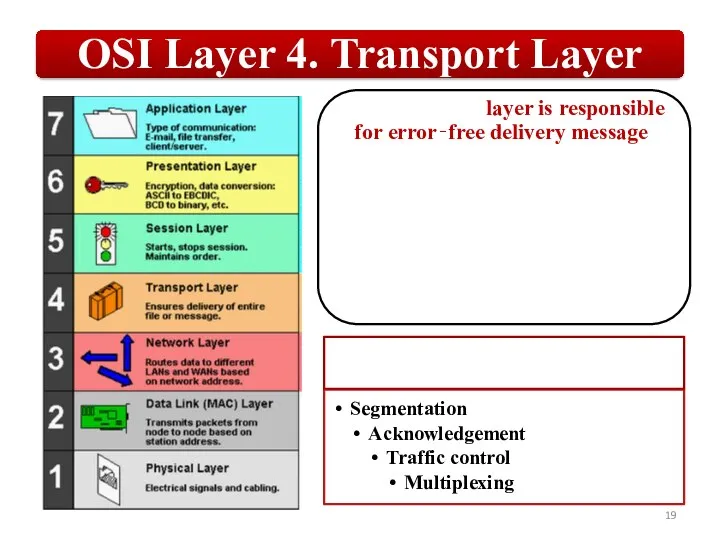
Слайд 19
Слайд 20
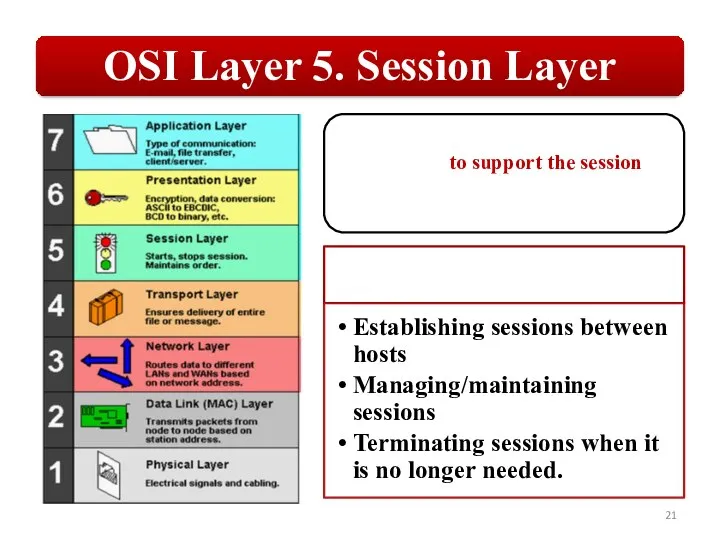
Слайд 21
Слайд 22
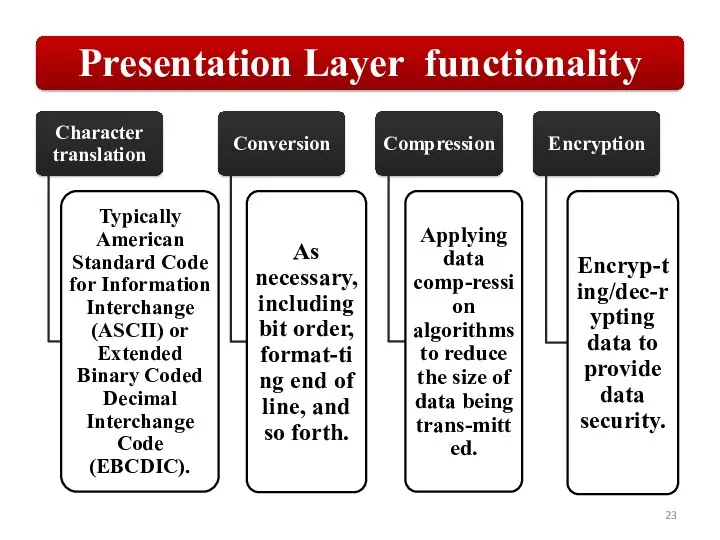
Слайд 23
Слайд 24
Слайд 25
Слайд 26
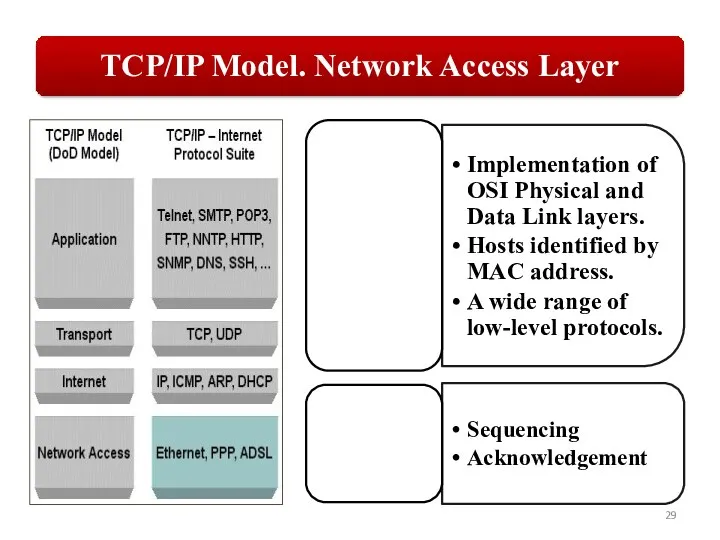
Слайд 27
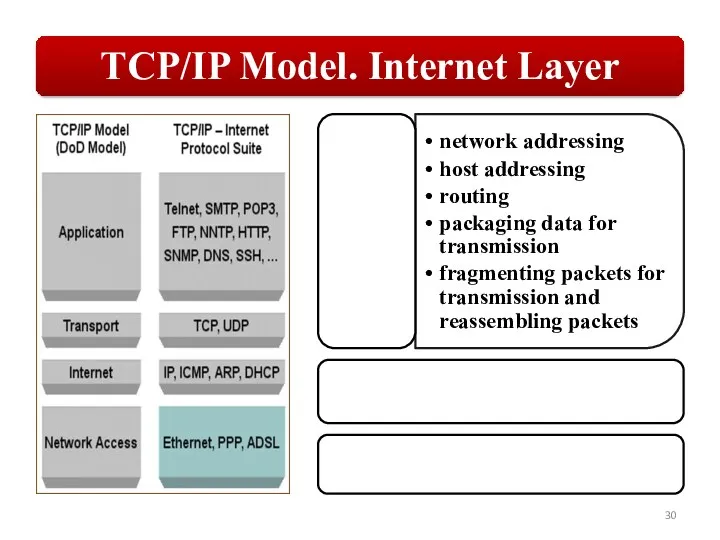
Слайд 28
Слайд 29
Слайд 30
Слайд 31
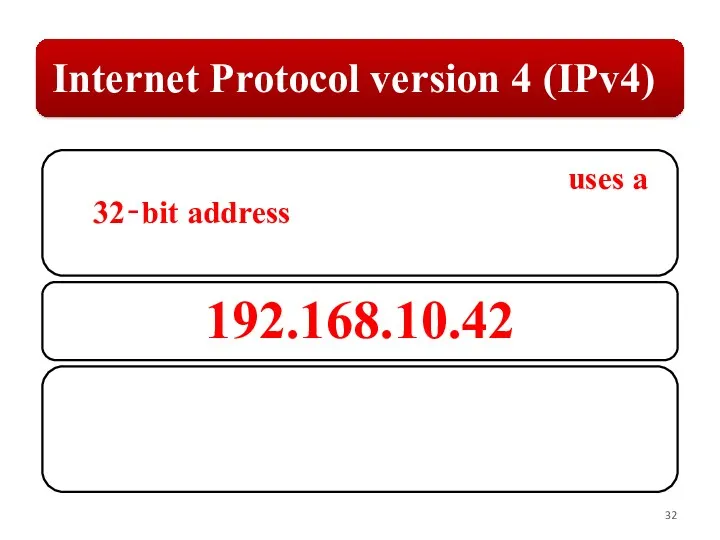
Слайд 32
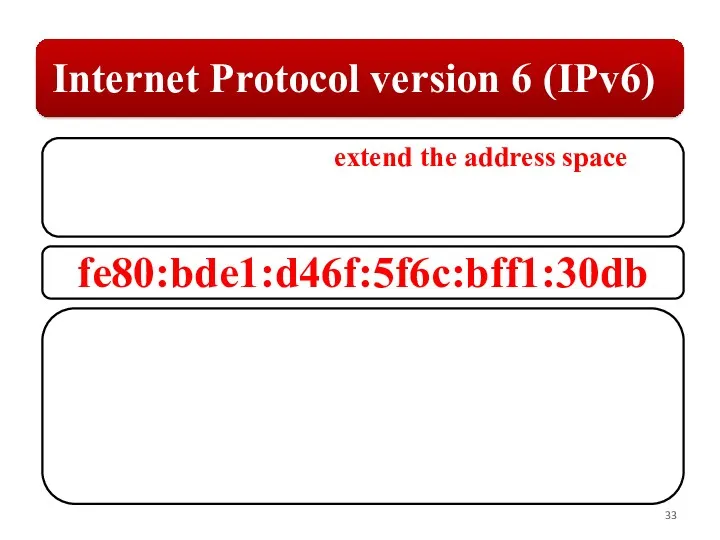
Слайд 33
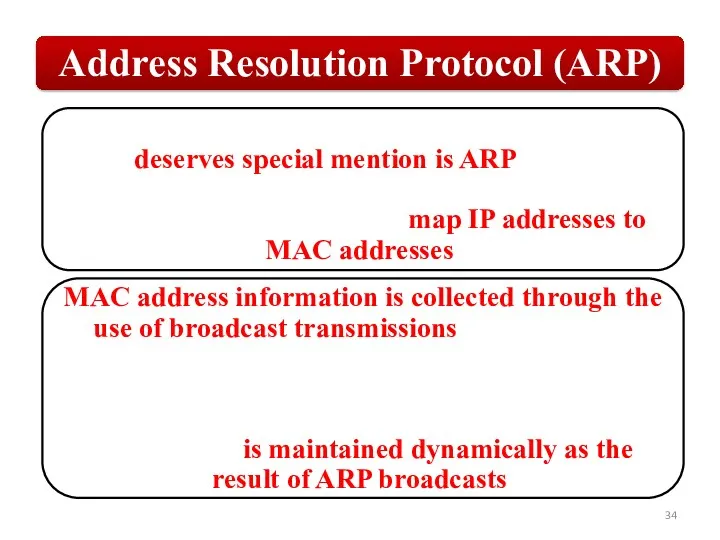
Слайд 34
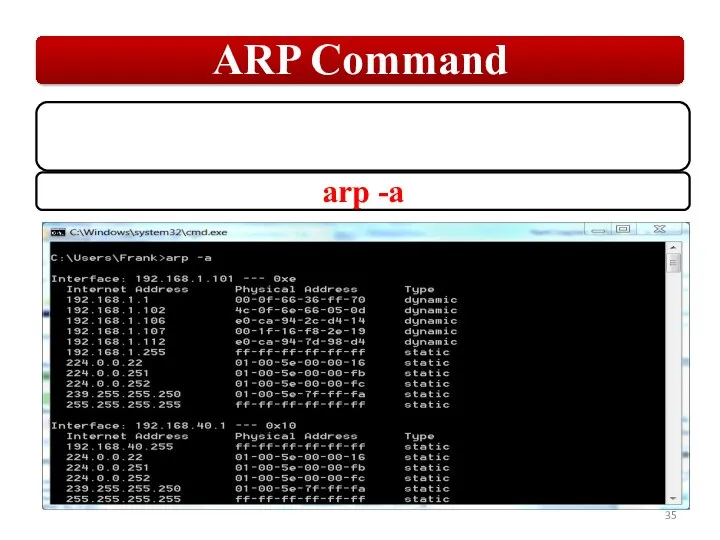
Слайд 35
Слайд 36
Слайд 37
Слайд 38
Слайд 39
Слайд 40
Слайд 41
Слайд 42
Слайд 43
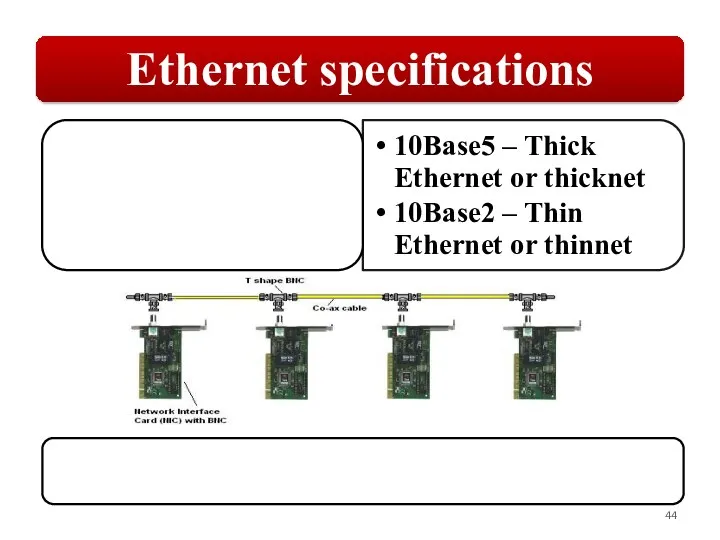
Слайд 44
Слайд 45
Слайд 46
Слайд 47
Слайд 48
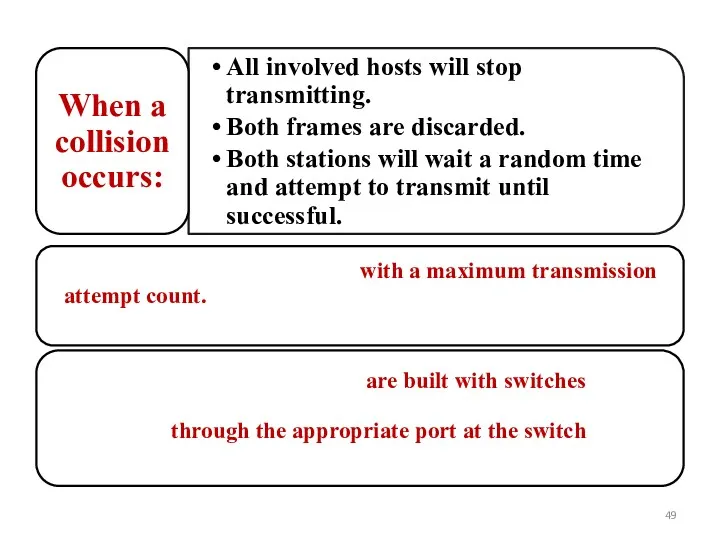
Слайд 49
Слайд 50
Слайд 51
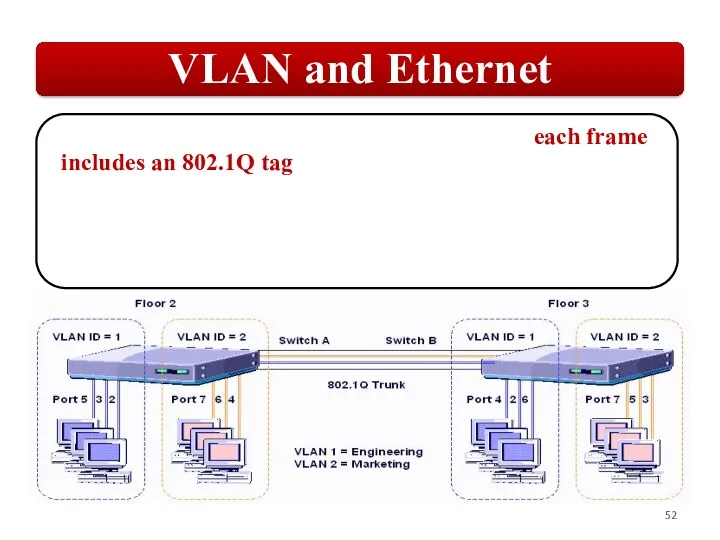
Слайд 52
Слайд 53
Слайд 54
Слайд 55
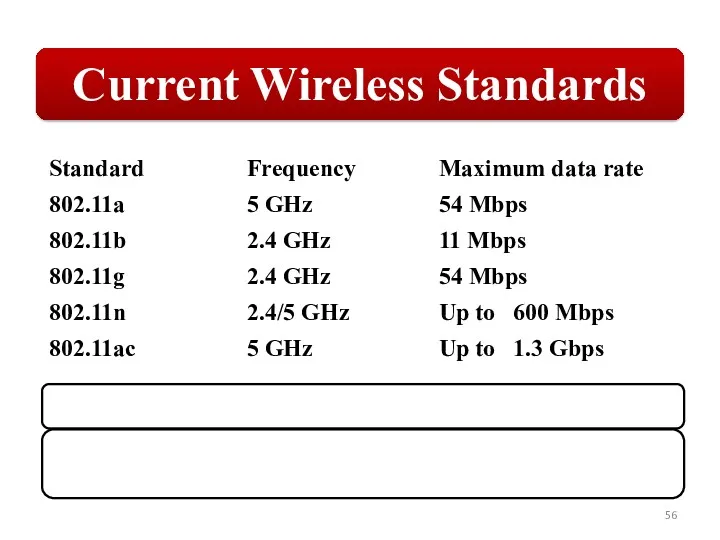
Слайд 56
Слайд 57
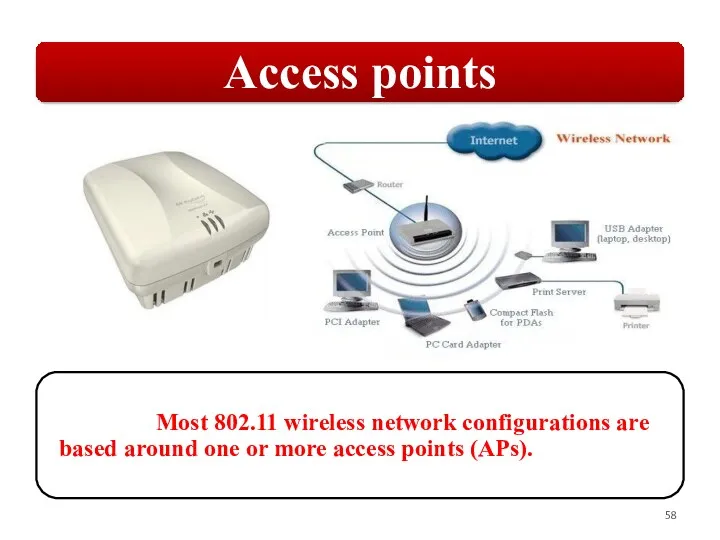
Слайд 58
Слайд 59
Слайд 60
Слайд 61
Слайд 62
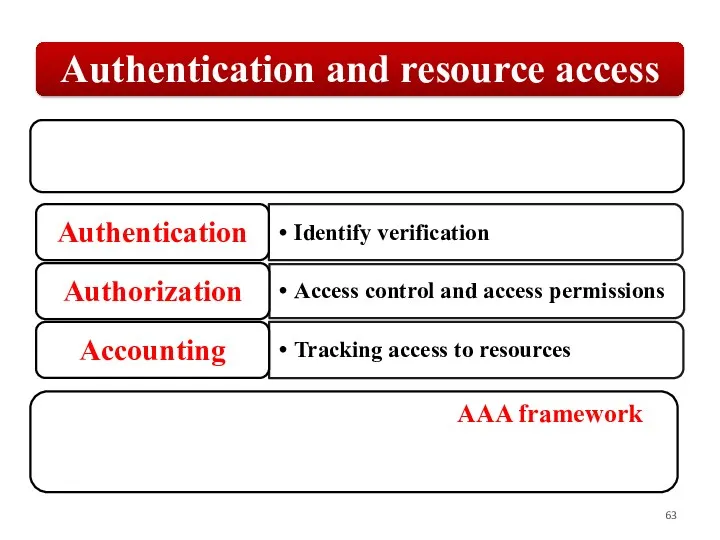
Слайд 63
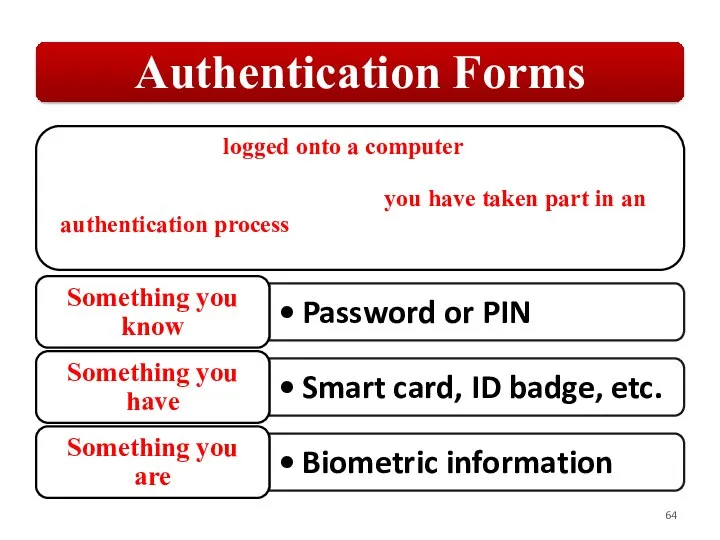
Слайд 64
Слайд 65
Слайд 66
Слайд 67
Слайд 68
Слайд 69
Слайд 70
Слайд 71
Слайд 72
Слайд 73
Asymmetric Encryption
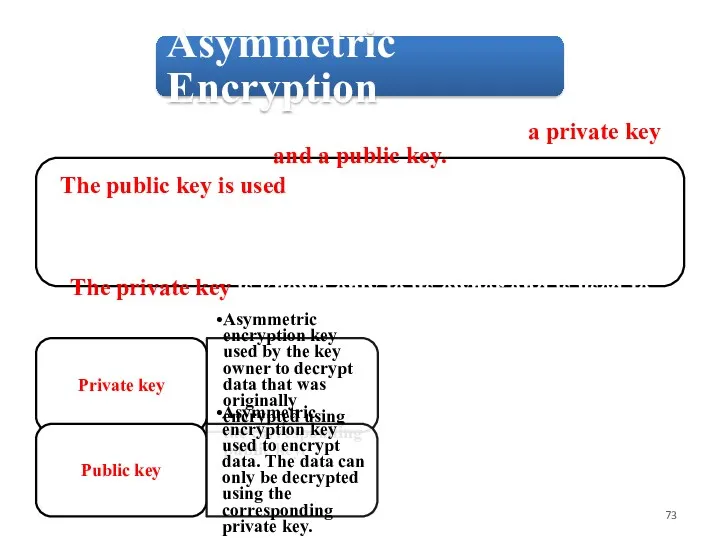
Asymmetric encryption is based on two keys: a private key
Asymmetric Encryption
Asymmetric encryption is based on two keys: a private key
and a public key.
The public key is used to encrypt data by a user who needs to send confidential data to the key owner. The key owner will share the public key with senders who need to be able to encrypt data before it is sent.
The private key is known only to its owner and is used to decrypt data.
The public key is used to encrypt data by a user who needs to send confidential data to the key owner. The key owner will share the public key with senders who need to be able to encrypt data before it is sent.
The private key is known only to its owner and is used to decrypt data.
Private key
Asymmetric encryption key used by the key owner to decrypt data that was originally encrypted using the corresponding public key.
Public key
Asymmetric encryption key used to encrypt data. The data can only be decrypted using the corresponding private key.
Следующая -
Зоя Космодемьянская

































 Вступ до паралельних та розподілених обчислень. Лекція 1
Вступ до паралельних та розподілених обчислень. Лекція 1 Предложение о работе. Компания Первый Бит
Предложение о работе. Компания Первый Бит Московский государственный медико-стоматологический университет им. А.И.Евдокимова
Московский государственный медико-стоматологический университет им. А.И.Евдокимова Копирайтинг. Группа ВК, страница в Instagram,
Копирайтинг. Группа ВК, страница в Instagram, Задачи на скорость передачи информации. 8 класс
Задачи на скорость передачи информации. 8 класс Анимации в презентации
Анимации в презентации Устройства ввода и вывода информации
Устройства ввода и вывода информации Наше время! Ноябрь-декабрь, 2019. Выпуск № 2
Наше время! Ноябрь-декабрь, 2019. Выпуск № 2 Локальная вычислительная сеть управления северной железной дороги
Локальная вычислительная сеть управления северной железной дороги Разработка информационной системы организации ООО Зоолайф
Разработка информационной системы организации ООО Зоолайф Глобальная компьютерная сеть Интернет
Глобальная компьютерная сеть Интернет Квантовий комп'ютер
Квантовий комп'ютер Microsoft Access-те кестелермен жұмыс жасау
Microsoft Access-те кестелермен жұмыс жасау Законодательство в сфере информационной безопасности
Законодательство в сфере информационной безопасности Позиционирование и продвижение в соцсетях
Позиционирование и продвижение в соцсетях Представление числовой информации с помощью систем счисления
Представление числовой информации с помощью систем счисления Информационная деятельность человека
Информационная деятельность человека Устройство компьютера
Устройство компьютера Язык программирования Pascal Массивы
Язык программирования Pascal Массивы Важный документ
Важный документ Газеты и журналы в библиотеке. МБУК Вышневолоцкая ЦБ Терелесовская библиотека
Газеты и журналы в библиотеке. МБУК Вышневолоцкая ЦБ Терелесовская библиотека Использование игровой среды программирования Scratch, как интуитивного программирования, при изучении раздела Алгоритмизация
Использование игровой среды программирования Scratch, как интуитивного программирования, при изучении раздела Алгоритмизация Программирование линейных алгоритмов
Программирование линейных алгоритмов Графический редактор Paint
Графический редактор Paint Этапы моделирования
Этапы моделирования Створення ігрових комп’ютерних програм на прикладі гри Монополія
Створення ігрових комп’ютерних програм на прикладі гри Монополія Вирусы. Классификация вирусов
Вирусы. Классификация вирусов Курс Програмування Kodu Game Lab
Курс Програмування Kodu Game Lab