Содержание
- 2. Main concepts authentication (who I am) authorization (what I can do) encryption
- 3. Authentication used by a server when it needs to know exactly who is accessing their information
- 4. Authorization defines a process by which a server determines if the client has permission to use
- 5. Encryption a process of transforming data so that it is unreadable by anyone who does not
- 6. Maven dependencies spring-security-web (groupId: org.springframework.security) spring-security-config (groupId: org.springframework.security)
- 7. Web configuration additions define a filter org.springframework.web.filter.DelegatingFilterProxy define a listener org.springframework.web.context.ContextLoaderListener context-param: contextConfigLocation points to security-config.xml
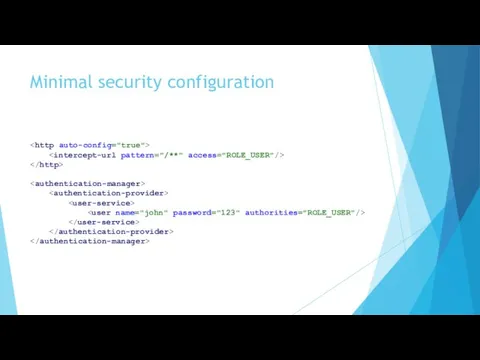
- 8. Minimal security configuration
- 9. Database configuration create two tables users (fields: username, password, enabled) authorities (fields: username, authority) create a
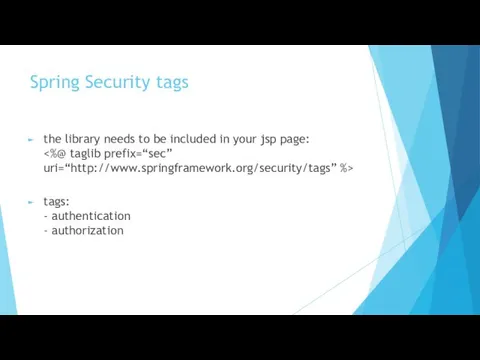
- 10. Spring Security tags the library needs to be included in your jsp page: tags: - authentication
- 11. Authentication tag used to gain access to the authenticated user object has a property attribute for
- 12. Authorize tag used to control access to parts of the page has such attributes: - url
- 13. Password encryption MD5 hash BCrypt
- 14. MD5 hash one of the first hash algorithms update the database with a new password
- 15. BCrypt more secure than MD5 update the database with a new password
- 16. Basic authentication usually used for REST applications when you enter a url, browser will show a
- 17. Custom login form define an intercept-url with access to any user add a form-login tag instead
- 19. Скачать презентацию








 Представление графических данных. Форматы графических данных
Представление графических данных. Форматы графических данных Создание современного новостного сайта, с постоянным наполнением контентом
Создание современного новостного сайта, с постоянным наполнением контентом Классификация СУБД. Тема 7.1
Классификация СУБД. Тема 7.1 Развитие музеев. Конец 20, начало 21 века
Развитие музеев. Конец 20, начало 21 века Базы данных, как основа современных CALS-технологий
Базы данных, как основа современных CALS-технологий Введение в программирование
Введение в программирование Программирование мобильных приложений. Сенсоры. Кубик
Программирование мобильных приложений. Сенсоры. Кубик Понятие информационной безопасности. Основные составляющие. Важность проблемы
Понятие информационной безопасности. Основные составляющие. Важность проблемы Business designing & deploying network solutions for small and medium business. (Lecture 3)
Business designing & deploying network solutions for small and medium business. (Lecture 3) SQL. База данных
SQL. База данных Презентация Весна.
Презентация Весна. Устройство компьютера
Устройство компьютера АИС РТРС. Эксплуатация. Система мобильного мониторинга
АИС РТРС. Эксплуатация. Система мобильного мониторинга Стандарт кодирования видео и звуковой информации. MPEG-4
Стандарт кодирования видео и звуковой информации. MPEG-4 Кодирование и обработка числовой информации. Методическая разработка
Кодирование и обработка числовой информации. Методическая разработка Операционные системы
Операционные системы Работа с личным кабинетом (ЛК)
Работа с личным кабинетом (ЛК) Турботаргет. Таргетированная реклама
Турботаргет. Таргетированная реклама Комп’ютерні віруси і антивіруси
Комп’ютерні віруси і антивіруси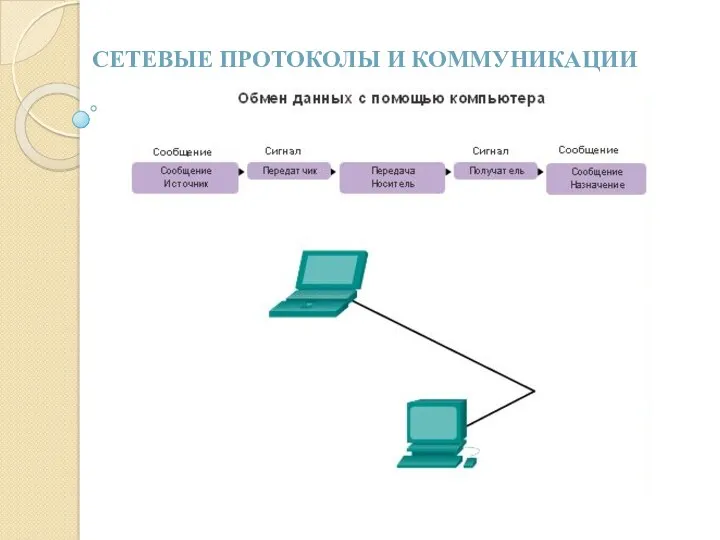 Сетевые протоколы и коммуникации
Сетевые протоколы и коммуникации Задачи
Задачи Медиаконвергенция: осмысление феномена под разным углом
Медиаконвергенция: осмысление феномена под разным углом Перечисления. Объявление и использование перечислений
Перечисления. Объявление и использование перечислений Выявление и устранение типовых неисправностей приводов, HDD, SSD, Flash
Выявление и устранение типовых неисправностей приводов, HDD, SSD, Flash Решение логических задач
Решение логических задач Чит-код социальных сетей
Чит-код социальных сетей История Tik Tok
История Tik Tok Решение задач в ALOHA
Решение задач в ALOHA