Содержание
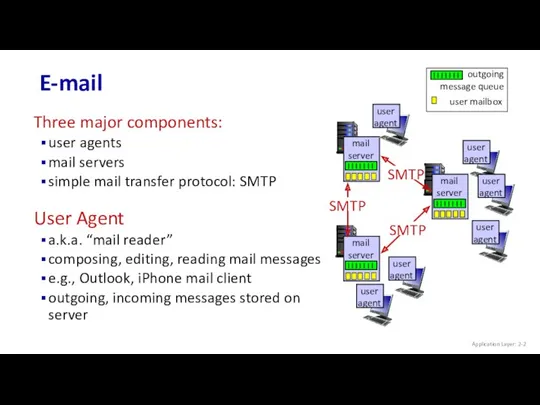
- 2. E-mail Application Layer: 2- Three major components: user agents mail servers simple mail transfer protocol: SMTP
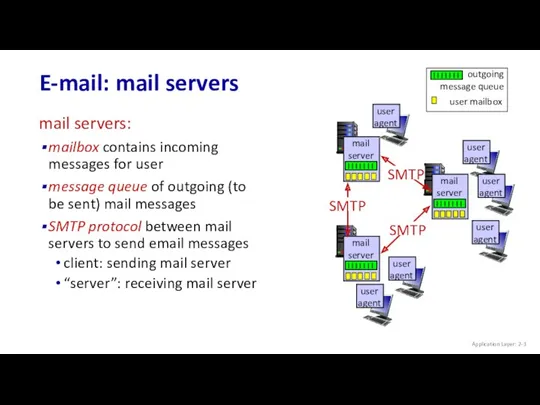
- 3. E-mail: mail servers Application Layer: 2- mail servers: mailbox contains incoming messages for user message queue
- 4. E-mail: the RFC (5321) Application Layer: 2- uses TCP to reliably transfer email message from client
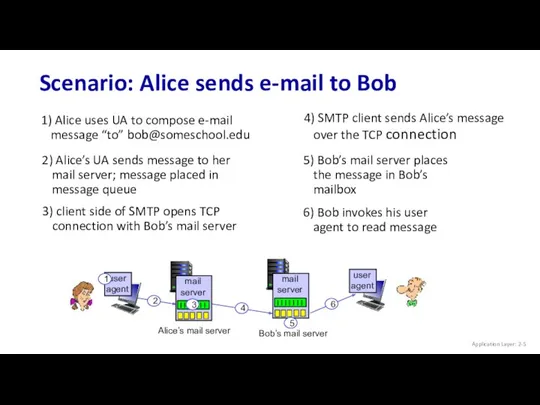
- 5. Scenario: Alice sends e-mail to Bob Application Layer: 2- 1) Alice uses UA to compose e-mail
- 6. Sample SMTP interaction Application Layer: 2- S: 220 hamburger.edu C: HELO crepes.fr S: 250 Hello crepes.fr,
- 7. Try SMTP interaction for yourself: Application Layer: 2- telnet 25 see 220 reply from server enter
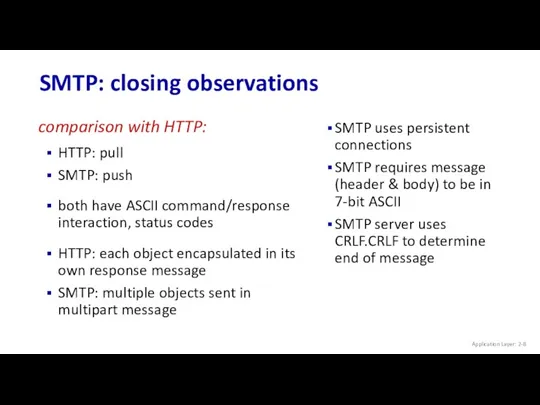
- 8. SMTP: closing observations Application Layer: 2- SMTP uses persistent connections SMTP requires message (header & body)
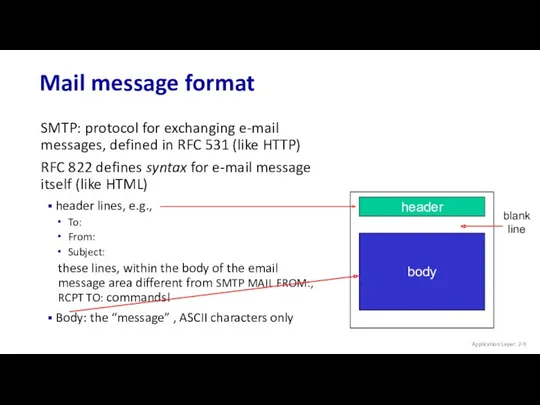
- 9. Mail message format Application Layer: 2- SMTP: protocol for exchanging e-mail messages, defined in RFC 531
- 10. Mail access protocols Application Layer: 2- SMTP: delivery/storage of e-mail messages to receiver’s server mail access
- 11. Application Layer: Overview Principles of network applications Web and HTTP E-mail, SMTP, IMAP The Domain Name
- 12. DNS: Domain Name System Application Layer: 2- people: many identifiers: SSN, name, passport # Internet hosts,
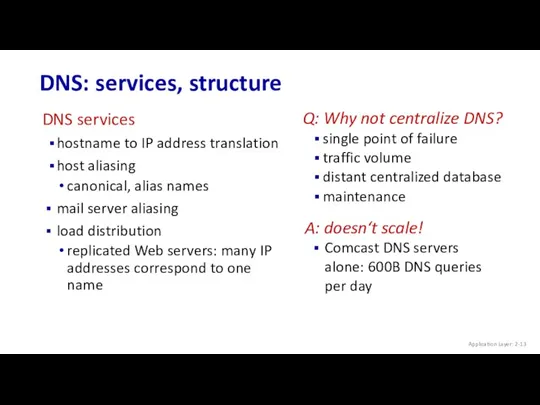
- 13. DNS: services, structure Application Layer: 2- Q: Why not centralize DNS? single point of failure traffic
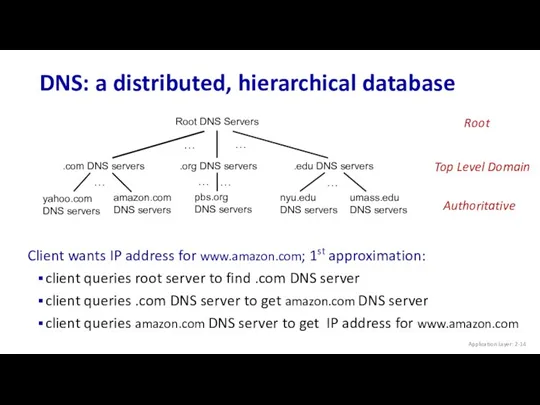
- 14. DNS: a distributed, hierarchical database Application Layer: 2- … … Client wants IP address for www.amazon.com;
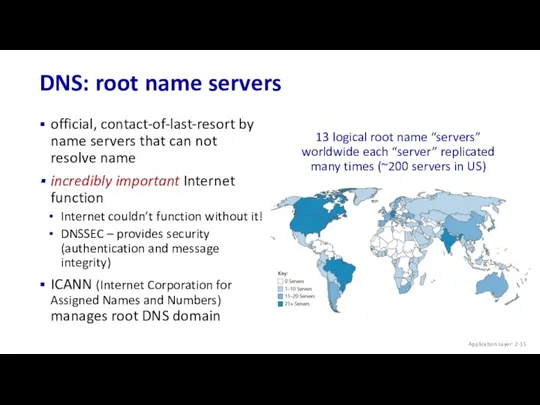
- 15. DNS: root name servers Application Layer: 2- official, contact-of-last-resort by name servers that can not resolve
- 16. TLD: authoritative servers Application Layer: 2- Top-Level Domain (TLD) servers: responsible for .com, .org, .net, .edu,
- 17. Local DNS name servers Application Layer: 2- does not strictly belong to hierarchy each ISP (residential
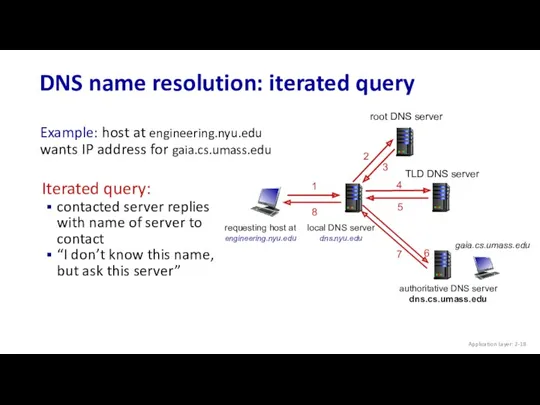
- 18. DNS name resolution: iterated query Application Layer: 2- Example: host at engineering.nyu.edu wants IP address for
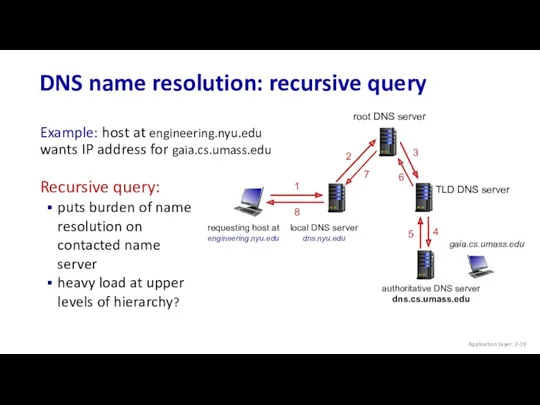
- 19. DNS name resolution: recursive query Application Layer: 2- requesting host at engineering.nyu.edu gaia.cs.umass.edu root DNS server
- 20. Caching, Updating DNS Records Application Layer: 2- once (any) name server learns mapping, it caches mapping
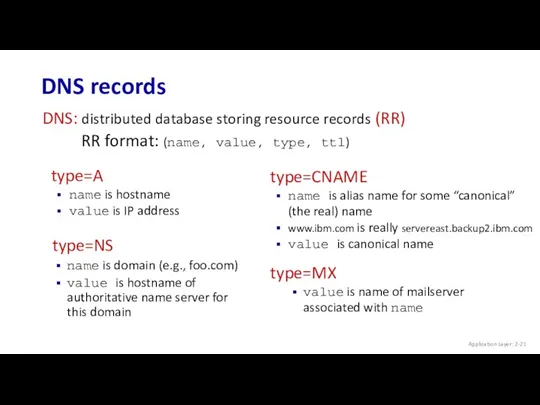
- 21. DNS records Application Layer: 2- DNS: distributed database storing resource records (RR) type=NS name is domain
- 22. DNS protocol messages Application Layer: 2- DNS query and reply messages, both have same format: message
- 23. Application Layer: 2- DNS query and reply messages, both have same format: name, type fields for
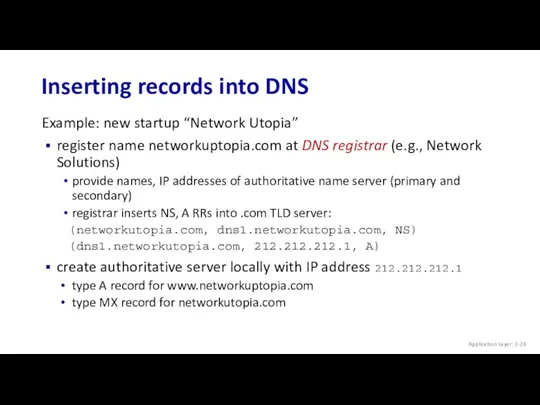
- 24. Inserting records into DNS Application Layer: 2- Example: new startup “Network Utopia” register name networkuptopia.com at
- 25. DNS security Application Layer: 2- DDoS attacks bombard root servers with traffic not successful to date
- 26. Application Layer: Overview Principles of network applications Web and HTTP E-mail, SMTP, IMAP The Domain Name
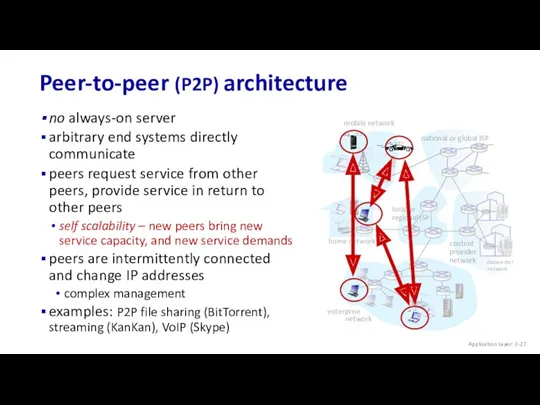
- 27. mobile network home network enterprise network national or global ISP local or regional ISP datacenter network
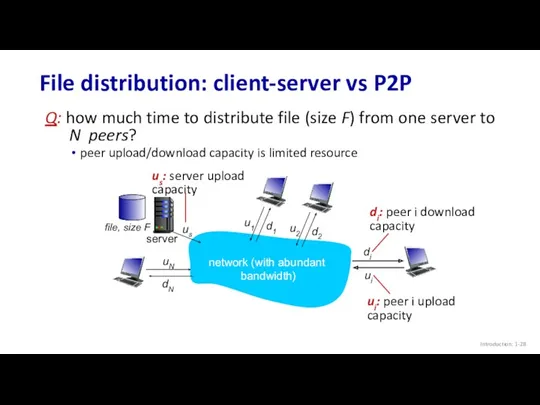
- 28. Introduction: 1- File distribution: client-server vs P2P Q: how much time to distribute file (size F)
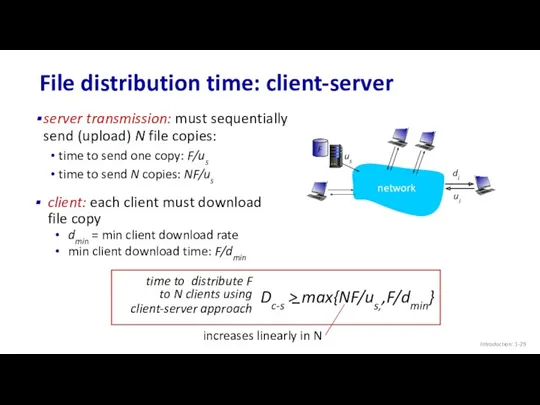
- 29. Introduction: 1- File distribution time: client-server server transmission: must sequentially send (upload) N file copies: time
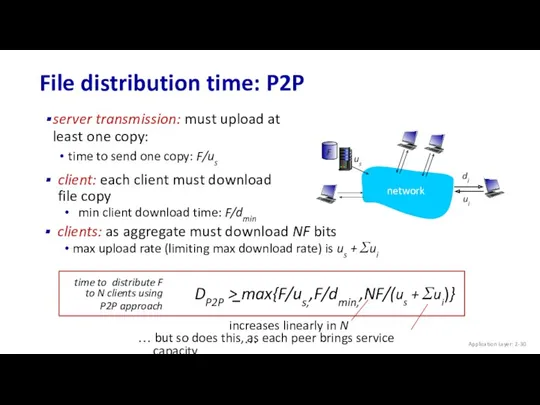
- 30. File distribution time: P2P server transmission: must upload at least one copy: time to send one
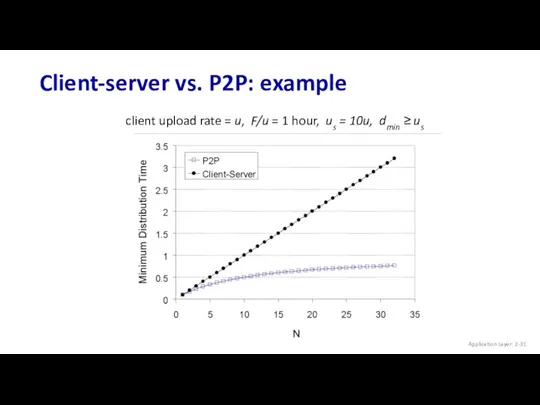
- 31. Client-server vs. P2P: example client upload rate = u, F/u = 1 hour, us = 10u,
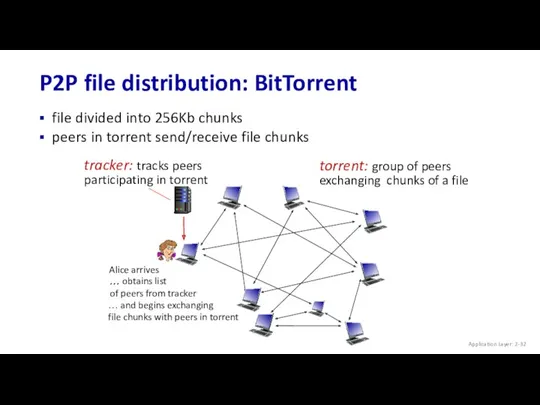
- 32. P2P file distribution: BitTorrent file divided into 256Kb chunks peers in torrent send/receive file chunks tracker:
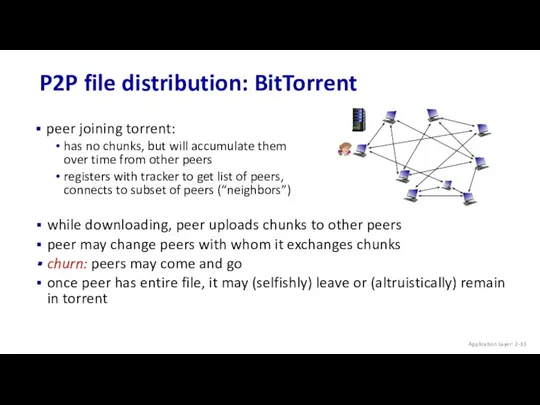
- 33. P2P file distribution: BitTorrent peer joining torrent: has no chunks, but will accumulate them over time
- 34. BitTorrent: requesting, sending file chunks Requesting chunks: at any given time, different peers have different subsets
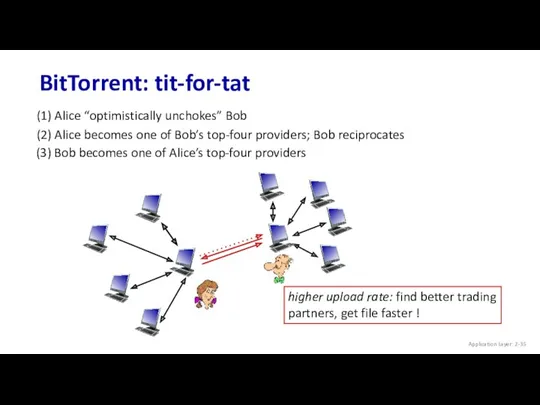
- 35. BitTorrent: tit-for-tat (1) Alice “optimistically unchokes” Bob (2) Alice becomes one of Bob’s top-four providers; Bob
- 36. Application layer: overview Principles of network applications Web and HTTP E-mail, SMTP, IMAP The Domain Name
- 37. Video Streaming and CDNs: context stream video traffic: major consumer of Internet bandwidth Netflix, YouTube, Amazon
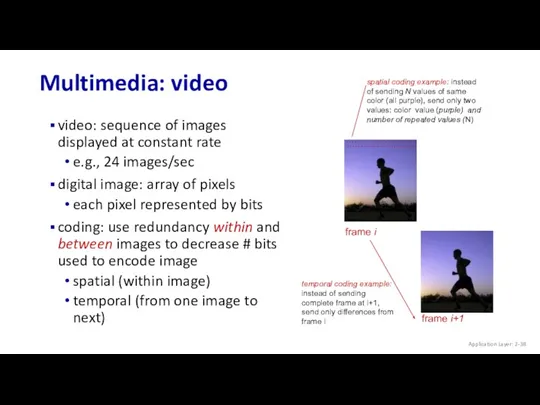
- 38. Multimedia: video video: sequence of images displayed at constant rate e.g., 24 images/sec digital image: array
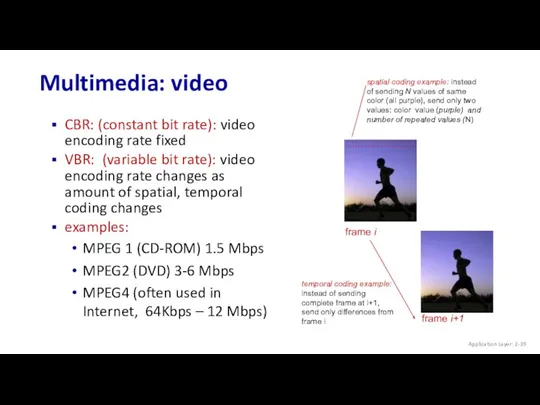
- 39. Multimedia: video CBR: (constant bit rate): video encoding rate fixed VBR: (variable bit rate): video encoding
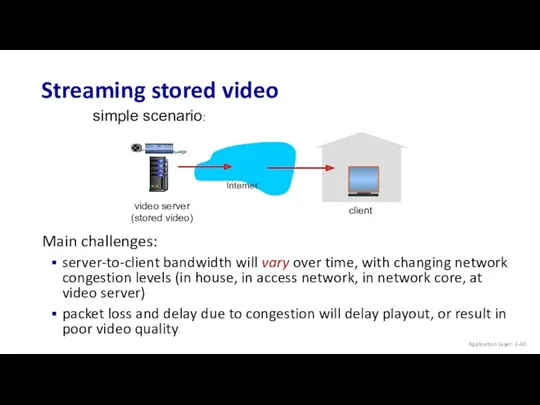
- 40. Main challenges: server-to-client bandwidth will vary over time, with changing network congestion levels (in house, in
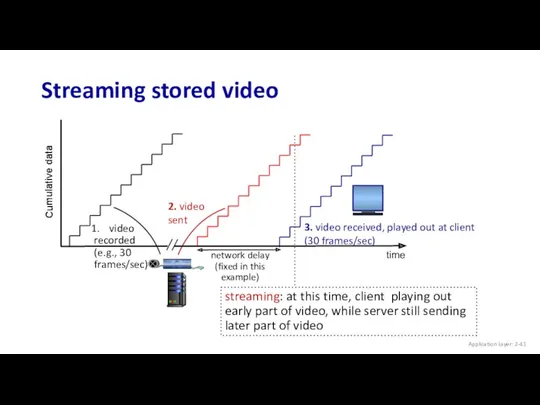
- 41. Streaming stored video Cumulative data time Application Layer: 2-
- 42. Streaming stored video: challenges continuous playout constraint: once client playout begins, playback must match original timing
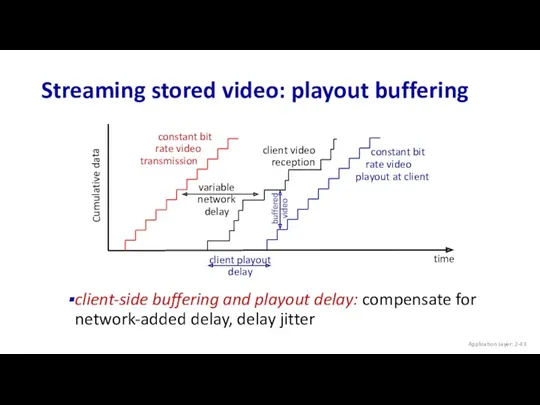
- 43. Streaming stored video: playout buffering constant bit rate video transmission Cumulative data time client-side buffering and
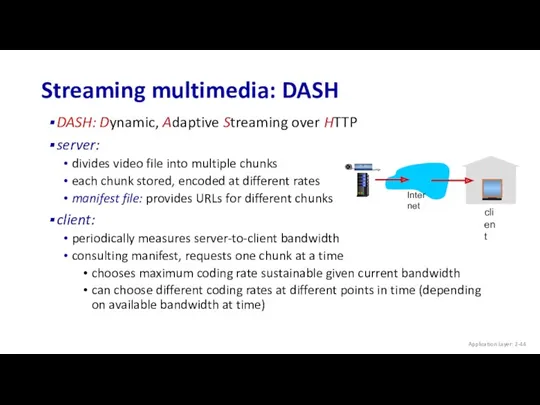
- 44. Streaming multimedia: DASH DASH: Dynamic, Adaptive Streaming over HTTP server: divides video file into multiple chunks
- 45. Streaming multimedia: DASH “intelligence” at client: client determines when to request chunk (so that buffer starvation,
- 46. Content distribution networks (CDNs) challenge: how to stream content (selected from millions of videos) to hundreds
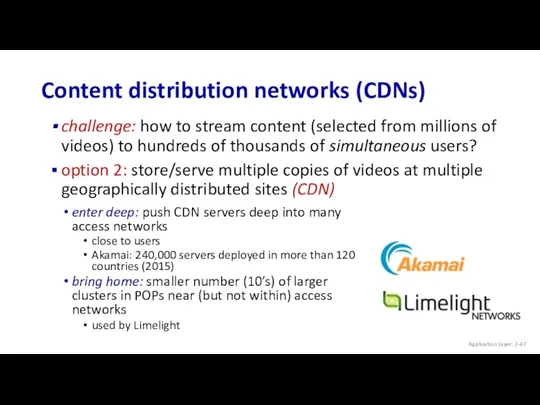
- 47. Content distribution networks (CDNs) challenge: how to stream content (selected from millions of videos) to hundreds
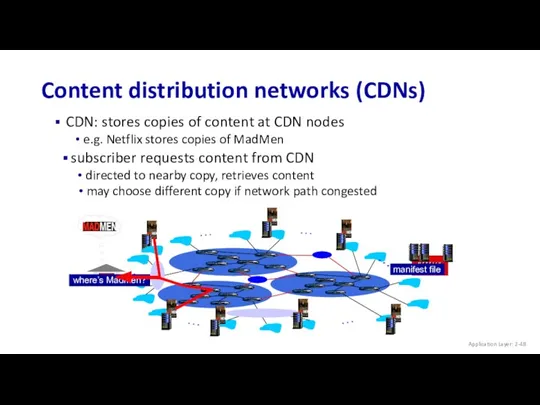
- 48. subscriber requests content from CDN Content distribution networks (CDNs) CDN: stores copies of content at CDN
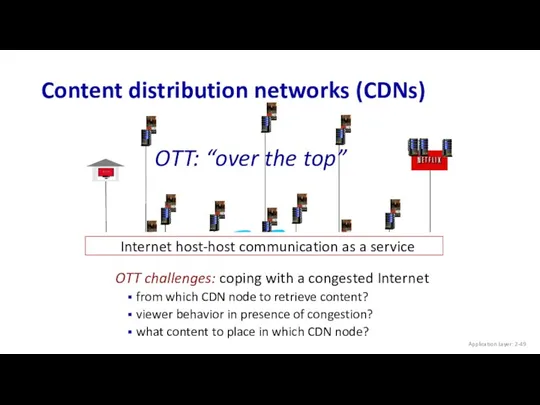
- 49. OTT challenges: coping with a congested Internet from which CDN node to retrieve content? viewer behavior
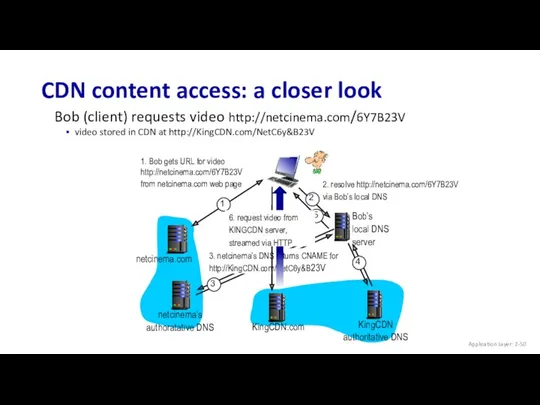
- 50. CDN content access: a closer look netcinema.com KingCDN.com 1. Bob gets URL for video http://netcinema.com/6Y7B23V from
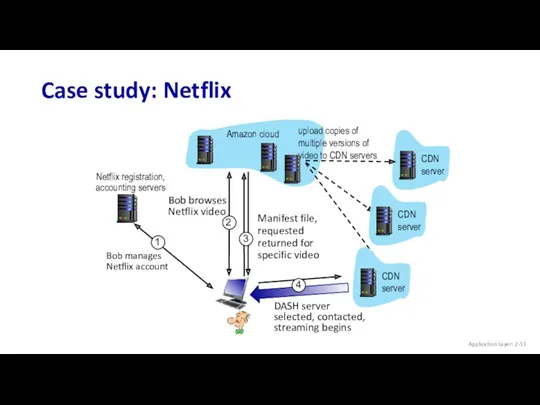
- 51. Case study: Netflix Bob manages Netflix account Netflix registration, accounting servers Amazon cloud Bob browses Netflix
- 52. Application Layer: Overview Principles of network applications Web and HTTP E-mail, SMTP, IMAP The Domain Name
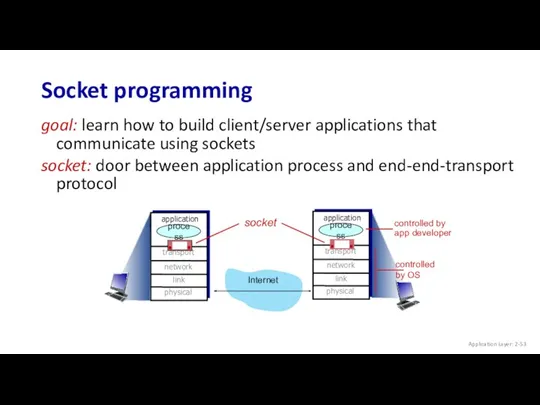
- 53. Socket programming goal: learn how to build client/server applications that communicate using sockets socket: door between
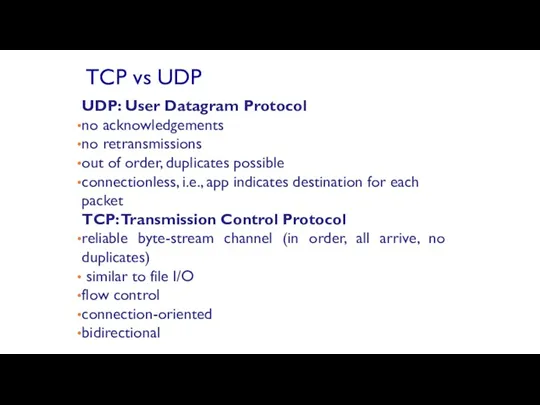
- 54. UDP: User Datagram Protocol no acknowledgements no retransmissions out of order, duplicates possible connectionless, i.e., app
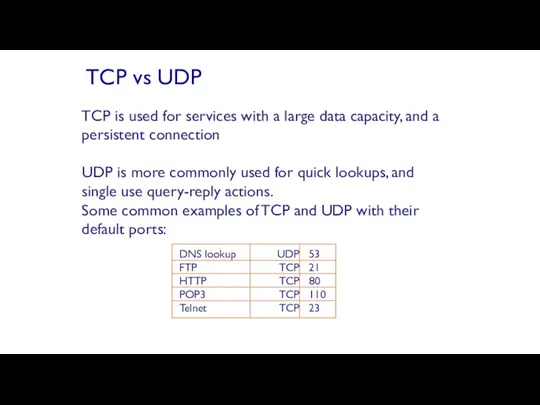
- 55. TCP is used for services with a large data capacity, and a persistent connection UDP is
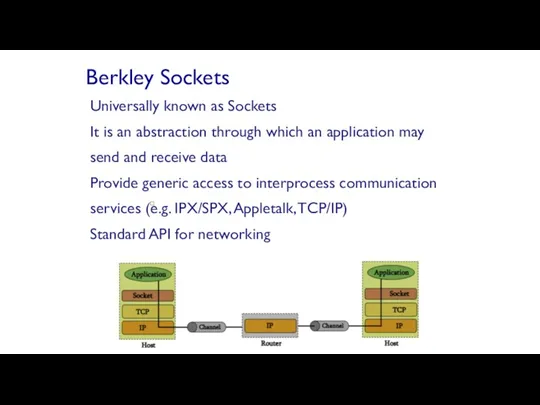
- 56. Universally known as Sockets It is an abstraction through which an application may send and receive
- 57. Uniquely identified by: an internet address, an end-to-end protocol (e.g. TCP or UDP), a port number
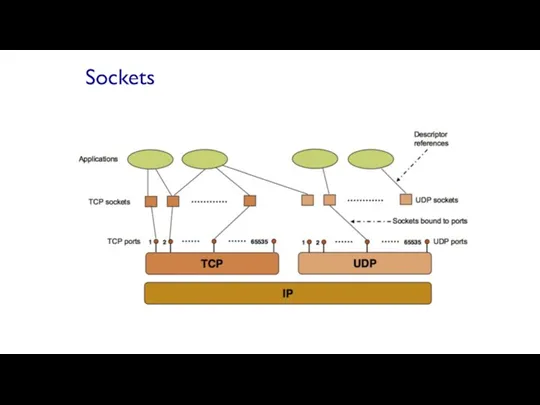
- 58. Sockets
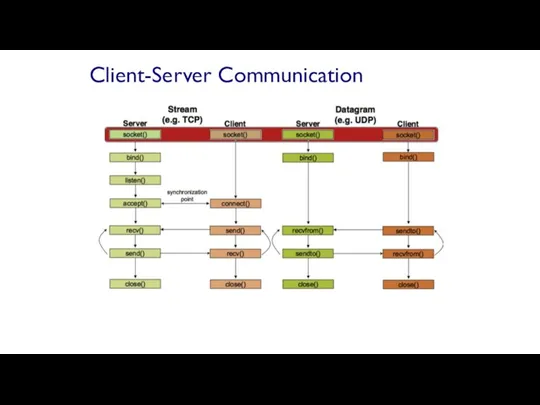
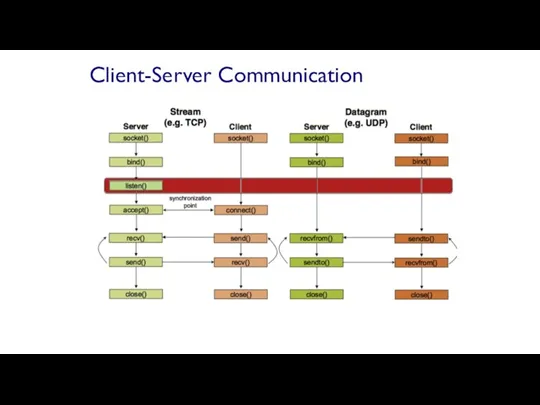
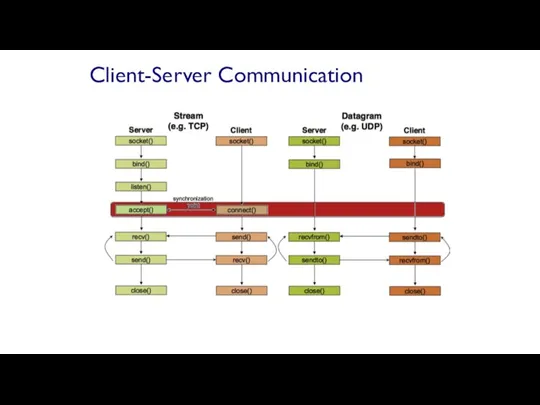
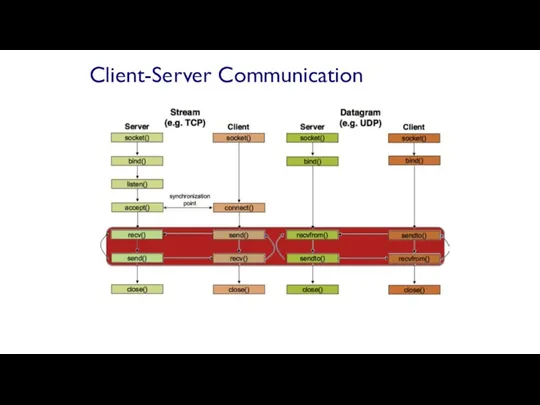
- 59. Client-Server Communication Server passively waits for and responds to clients passive socket Client initiates the communication
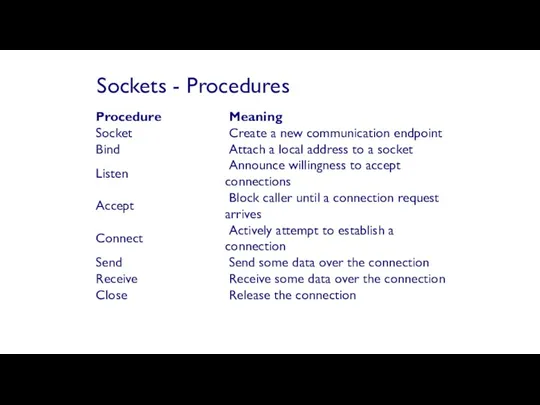
- 60. Sockets - Procedures
- 61. Client-Server Communication
- 62. fint sockid = socket(family, type, protocol); sockid: socket descriptor, an integer (like a file-handle) family: integer,
- 63. Client-Server Communication
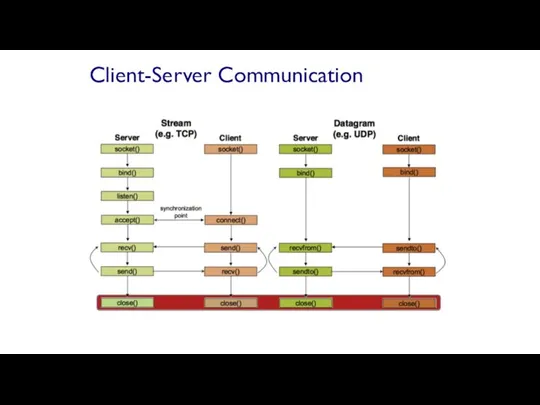
- 64. When finished using a socket, the socket should be closed status = close(sockid); sockid: the file
- 65. Socket API defines a generic data type for addresses: struct sockaddr { unsigned short sa__family; /*
- 66. Client-Server Communication
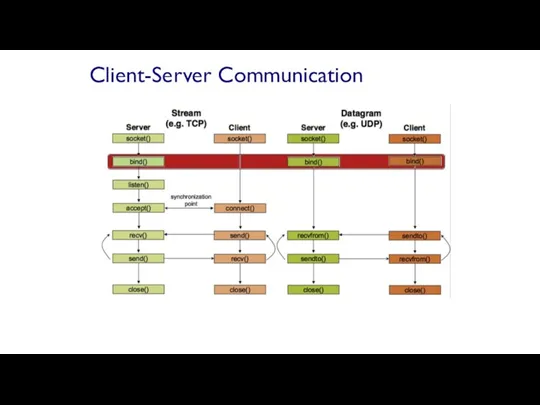
- 67. associates and reserves a port for use by the socket int status = bind(sockid, fiaddrport, size);
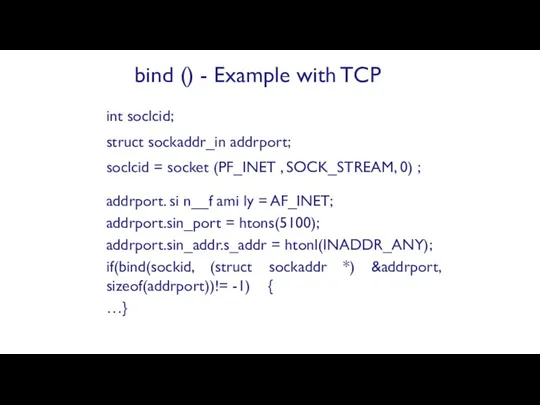
- 68. int soclcid; struct sockaddr_in addrport; soclcid = socket (PF_INET , SOCK_STREAM, 0) ; addrport. si n__f
- 69. bind() can be skipped for both types of sockets Datagram socket: if only sending, no need
- 70. Client-Server Communication
- 71. Instructs TCP protocol implementation to listen for connections int status = listen(sockid, queueLimit); sockid: integer, socket
- 72. Client-Server Communication
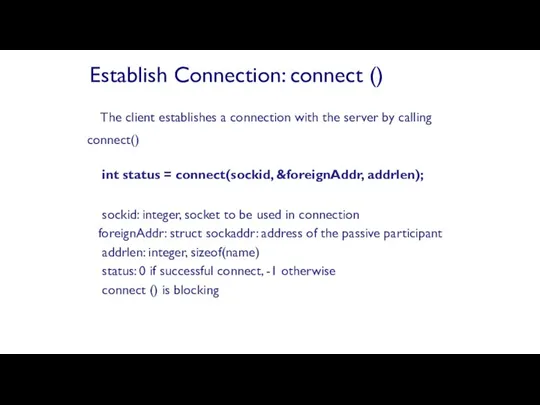
- 73. The client establishes a connection with the server by calling connect() int status = connect(sockid, &foreignAddr,
- 74. The server gets a socket for an incoming client connection by calling accept() int s =
- 75. Client-Server Communication
- 76. int count = send(sockid, msg, msgLen, flags); msg: const void[], message to be transmitted msgLen: integer,
- 77. int count = sendto(sockid, msg, msgLen, flags, &foreignAddr, addrlen); msg, msgLen, flags, count: same with send
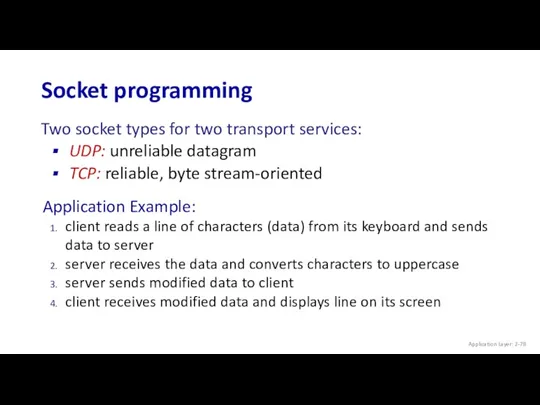
- 78. Socket programming Two socket types for two transport services: UDP: unreliable datagram TCP: reliable, byte stream-oriented
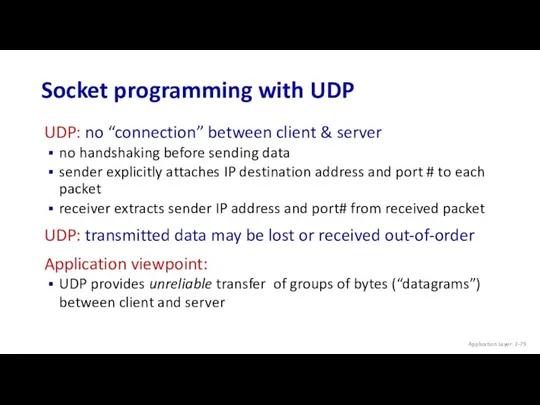
- 79. Socket programming with UDP UDP: no “connection” between client & server no handshaking before sending data
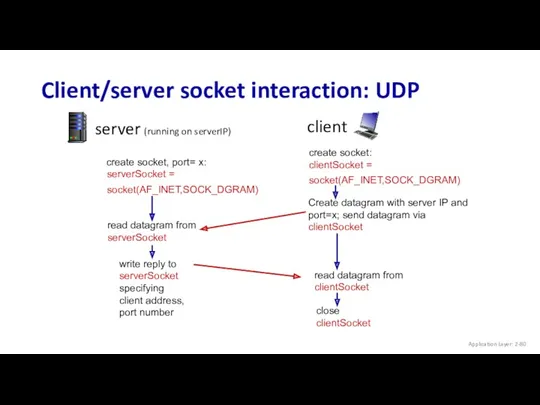
- 80. Client/server socket interaction: UDP create socket, port= x: serverSocket = socket(AF_INET,SOCK_DGRAM) server (running on serverIP) client
- 81. Example app: UDP client from socket import * serverName = ‘hostname’ serverPort = 12000 clientSocket =
- 82. Example app: UDP server Python UDPServer from socket import * serverPort = 12000 serverSocket = socket(AF_INET,
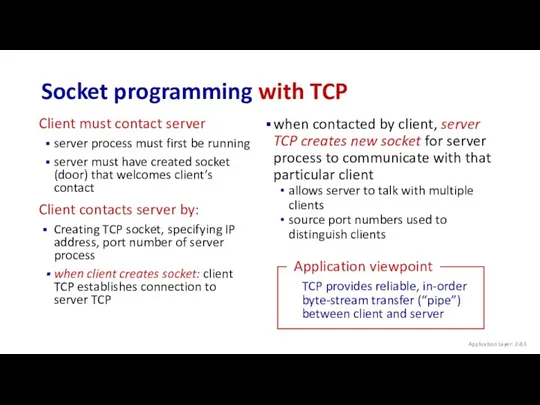
- 83. Socket programming with TCP Client must contact server server process must first be running server must
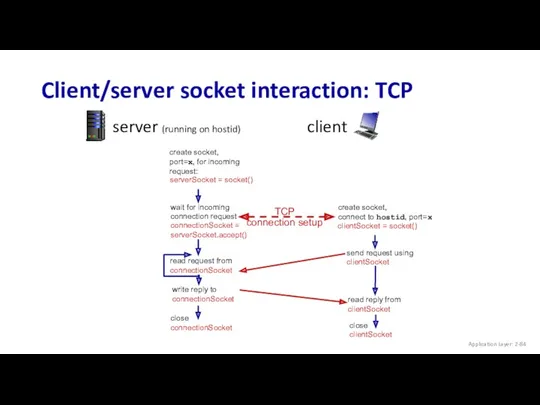
- 84. Client/server socket interaction: TCP server (running on hostid) client Application Layer: 2-
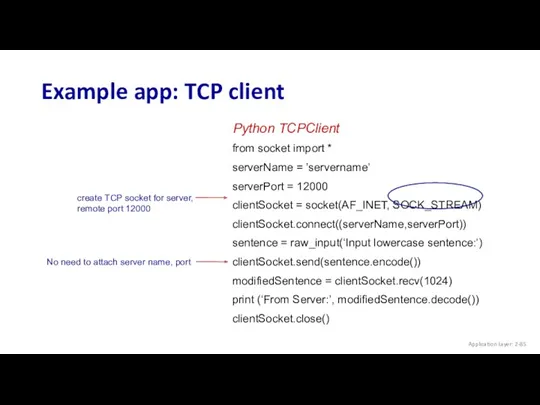
- 85. Example app: TCP client from socket import * serverName = ’servername’ serverPort = 12000 clientSocket =
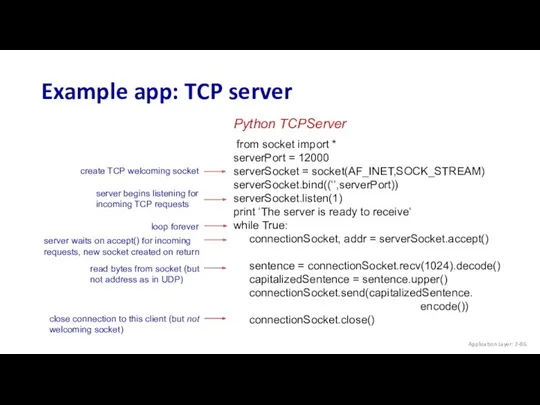
- 86. Example app: TCP server from socket import * serverPort = 12000 serverSocket = socket(AF_INET,SOCK_STREAM) serverSocket.bind((‘’,serverPort)) serverSocket.listen(1)
- 87. Topic 2: Summary application architectures client-server P2P application service requirements: reliability, bandwidth, delay Internet transport service
- 89. Скачать презентацию





















![int count = send(sockid, msg, msgLen, flags); msg: const void[],](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/385753/slide-75.jpg)



 Задача физической передачи данных. Основные методы доступа
Задача физической передачи данных. Основные методы доступа Инструкция ZOOM. Техническое оснащение вебинара
Инструкция ZOOM. Техническое оснащение вебинара Вредоносные и антивирусные программы
Вредоносные и антивирусные программы Формирование решений средствами таблиц MS Excel
Формирование решений средствами таблиц MS Excel Презентация Архитектура ПК
Презентация Архитектура ПК Презентация Условный оператор по программированию.
Презентация Условный оператор по программированию. Урок информатики по теме Умозаключение как форма мышления 6 класс
Урок информатики по теме Умозаключение как форма мышления 6 класс Информатика как единство науки и технологии
Информатика как единство науки и технологии Відкриваємо секрети програмування. Анімація об’єктів. Встановлення тла
Відкриваємо секрети програмування. Анімація об’єктів. Встановлення тла Условный оператор в Паскале. 9 класс
Условный оператор в Паскале. 9 класс Услуги: 1С БухОбслуживание
Услуги: 1С БухОбслуживание Інформаційна війна та маніпулювання
Інформаційна війна та маніпулювання Циклы разработки Web-приложений. Лекция №1
Циклы разработки Web-приложений. Лекция №1 Текст для сайта. Сервис Shato
Текст для сайта. Сервис Shato Алгоритмы. Стандартный набор алгоритмов
Алгоритмы. Стандартный набор алгоритмов Описание классов и объектов. Статические методы. Конструкторы. Классы-обертки встроенных типов
Описание классов и объектов. Статические методы. Конструкторы. Классы-обертки встроенных типов Единая образовательная сеть www.dnevnik.ru
Единая образовательная сеть www.dnevnik.ru Светодиодная матрица
Светодиодная матрица Мультисервисная сеть на основе SoftSwitch
Мультисервисная сеть на основе SoftSwitch Индексирование: понятие индекса, типы индексных файлов. Создание, активация и удаление индекса. Переиндексирование
Индексирование: понятие индекса, типы индексных файлов. Создание, активация и удаление индекса. Переиндексирование Memory management. Implementation issues & segmentation
Memory management. Implementation issues & segmentation Підготовка документа до друкування. Друкування документа
Підготовка документа до друкування. Друкування документа Мошенничества в интернет
Мошенничества в интернет Основы информационно-библиографической культуры
Основы информационно-библиографической культуры Сложные структуры данных. Связные списки
Сложные структуры данных. Связные списки Мастер-класс на районном методическом объединении учителей информатики Создание визитки на электронной площадке КузВики
Мастер-класс на районном методическом объединении учителей информатики Создание визитки на электронной площадке КузВики Java Best Practice. Лучшие практики разработки на Java
Java Best Practice. Лучшие практики разработки на Java Антивирусные программы
Антивирусные программы