Содержание
- 2. Firewall A firewall can be a hardware device or Software a program that controls traffic between
- 3. Packet Filtering In packet filtering the firewall analyses the packets that are sent against a set
- 4. Encryption Encryption is the process whereby a message can be securely stored and transmitted so that
- 5. Symmetric encryption Symmetric encryption uses the same algorithm and key for the encryption and the decryption
- 6. Assymmetric encryption Assymmetric encryption is a secured technique . Two keys are used, called the Public
- 7. The Digital Certificate contains: The holder’s name an ID number an expiry date(certificates are valid for
- 8. Digital Signature The sender could add a digital signature to the email. Digital signature are used
- 9. Authenticate & Authorisation Authentication When two parties communicate, the procedures in place are designed to ensure
- 10. Authorisation Authorisation is the control of a user’s access to computer resources. Measures taken to do
- 11. Any computer that is to be connected to a network, needs to have a network interface
- 12. Hub A receives all the signals from the individual computers and then broadcasts them back to
- 13. Protocol A Protocol is a set of rules which is used by computers to communicate with
- 14. Router When a computer sends data to another computer on the Internet, the data packets will
- 15. The router maintains a table with all the hardware addresses to which it has the direct
- 16. Gateway A gateway allows one network to be connected to another so that the packets from
- 17. PC network with a 3270 mainframe environment or a device that allows a Windows NT network
- 18. Both gateways and routers are used to regulate traffic into more separate networks. gateway it is
- 19. Packet Switching and Circuit Switching When a message is sent from one computer to another particularly
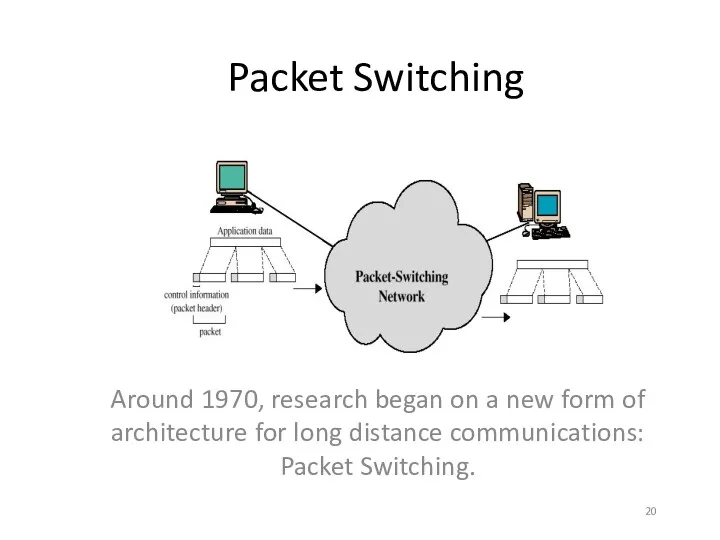
- 20. Packet Switching Around 1970, research began on a new form of architecture for long distance communications:
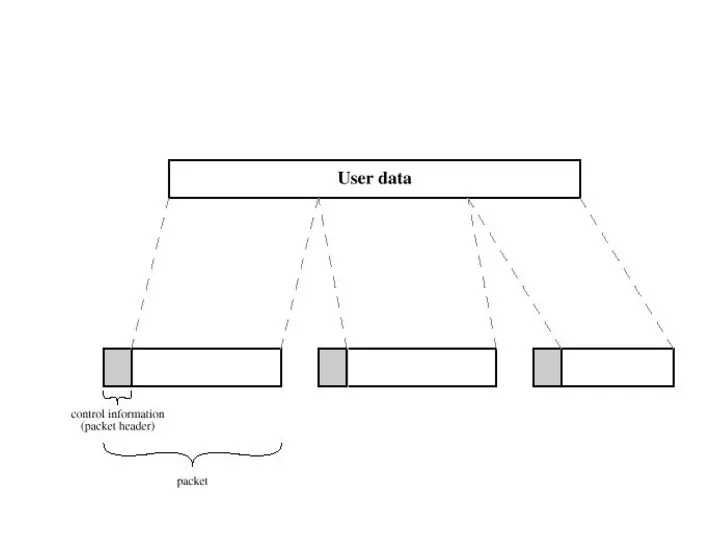
- 21. Packet Switching refers to protocols in which messages are divided into packets before they are sent.
- 23. In packet switching, the message is split into number of equal-sized packets(or datagrams). Each packet has
- 24. Most modern Wide Area Network (WAN) protocols, including TCP/IP, X.25, and Frame Relay, are based on
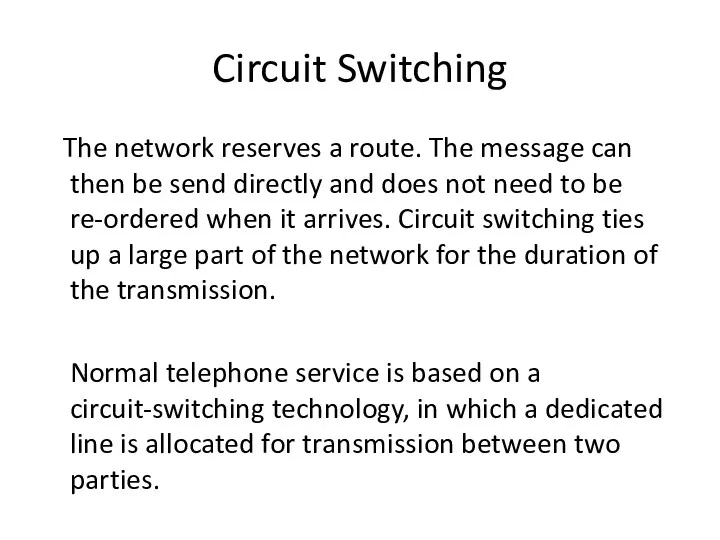
- 25. Circuit Switching The network reserves a route. The message can then be send directly and does
- 26. Circuit-switching is ideal when data must be transmitted quickly and must arrive in the same order
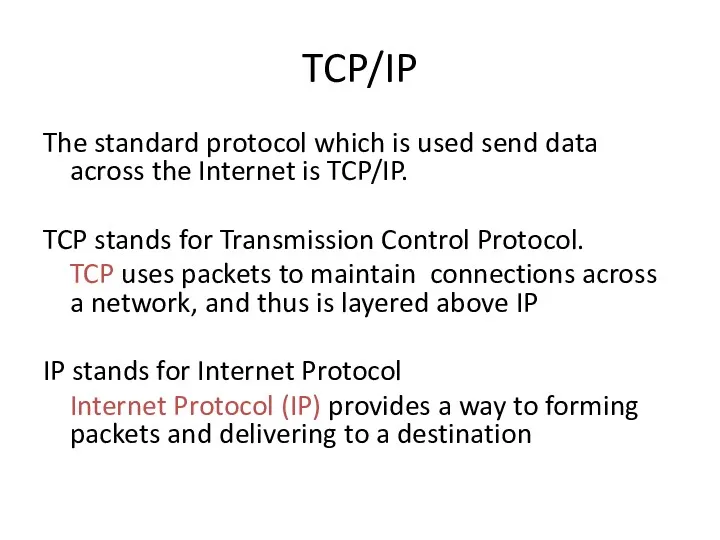
- 27. TCP/IP The standard protocol which is used send data across the Internet is TCP/IP. TCP stands
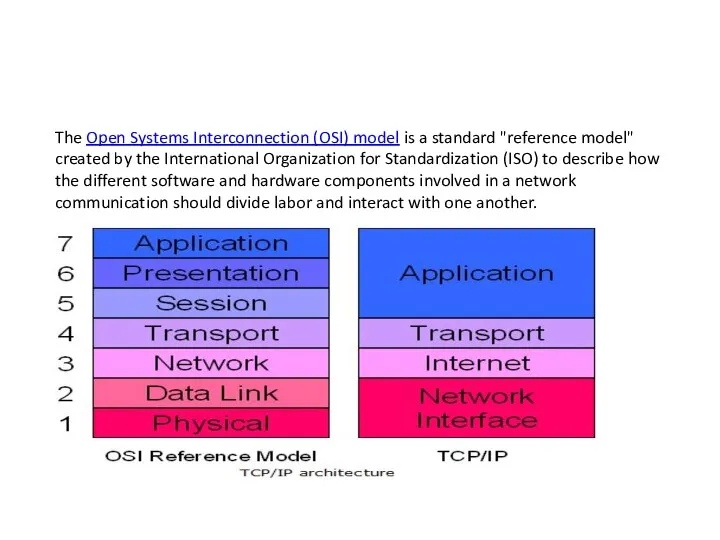
- 28. The Open Systems Interconnection (OSI) model is a standard "reference model" created by the International Organization
- 29. Subnet The subnet mask defines the size of the network. The subnet mask helps to tell
- 30. http://tuxgraphics.org/toolbox/network_address_calculator_add.html
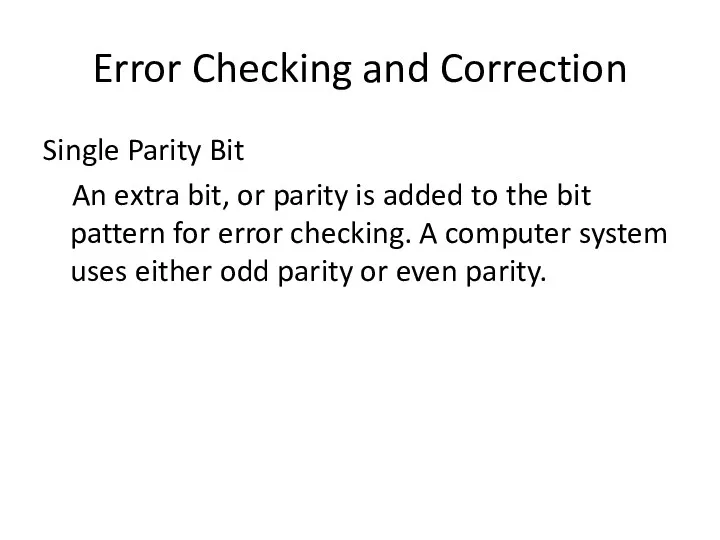
- 31. Error Checking and Correction Single Parity Bit An extra bit, or parity is added to the
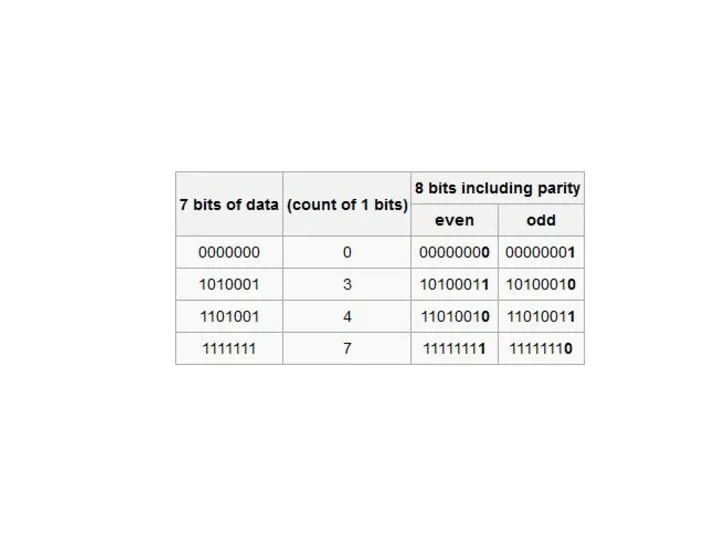
- 32. Odd Parity In odd-parity system, an extra bit set so that the total number of 1
- 33. Even Parity In an even-parity system the parity bit is set so that the total number
- 34. Exercise A computer system uses even parity. Complete the following _ 0100001 _1010011 _1000011 _1001001
- 35. Exercise A computer system uses odd parity. Which of the following bit patterns contain an error?
- 37. Exercise Detect and Correct the error in the following Hammed Code with even parity: 01101001011
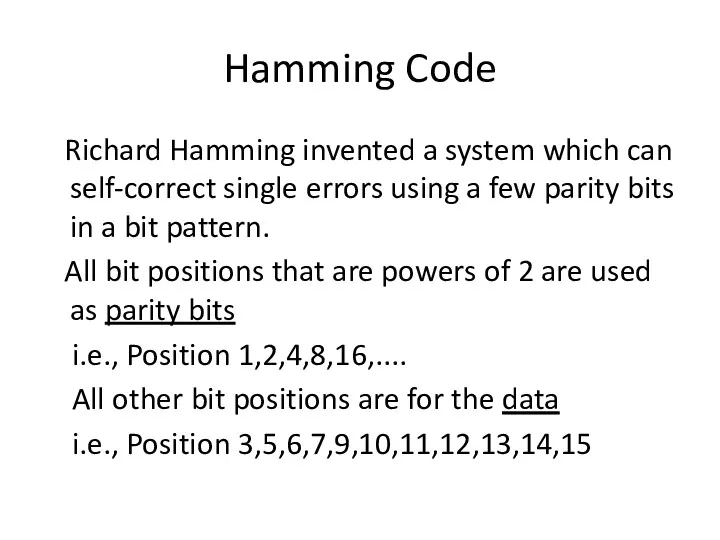
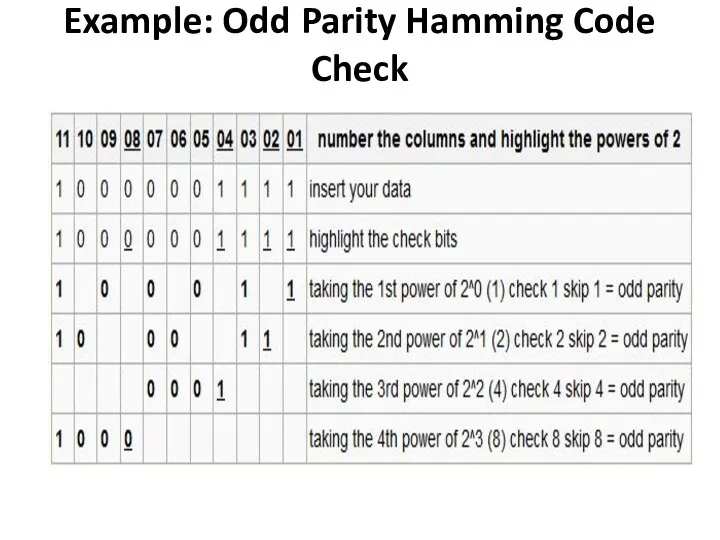
- 38. Hamming Code Richard Hamming invented a system which can self-correct single errors using a few parity
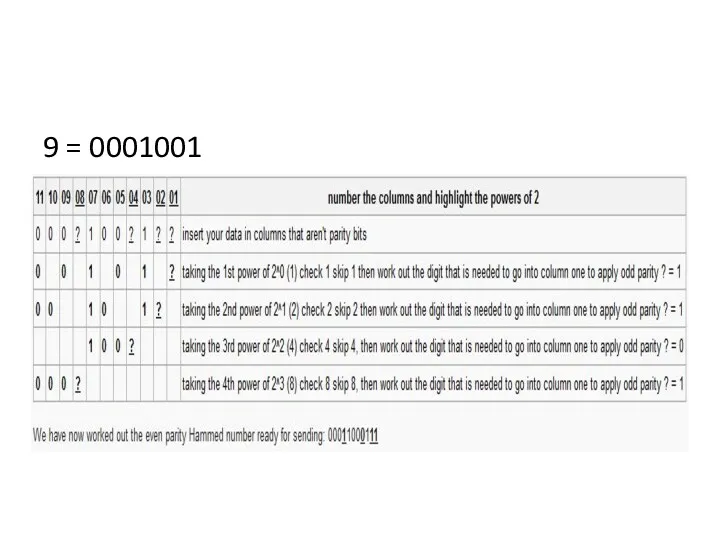
- 39. Checking if correct Number the column headings Highlight the column headings that are powers of 2
- 40. Example: Odd Parity Hamming Code Check
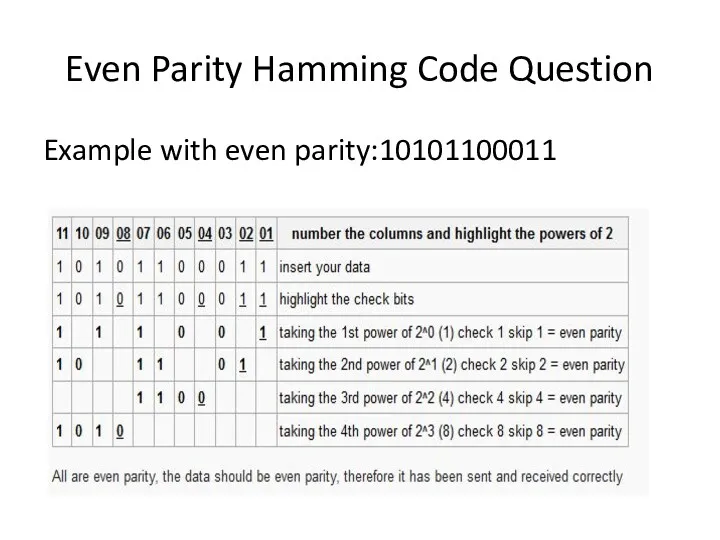
- 41. Example with even parity:10101100011 Even Parity Hamming Code Question
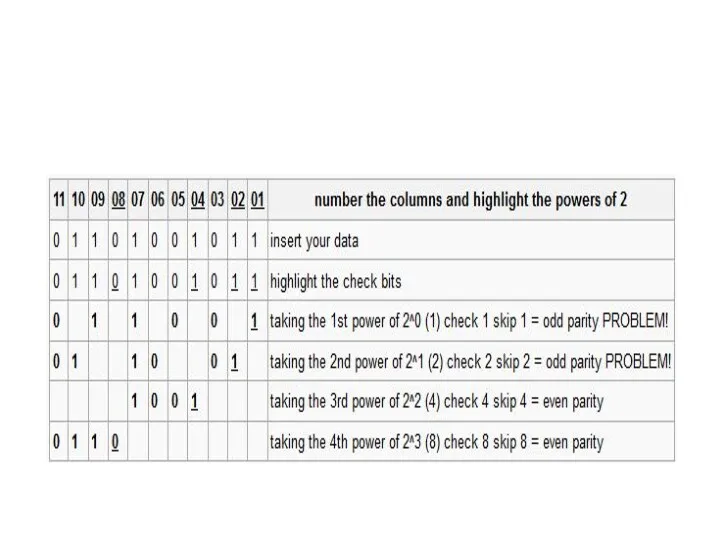
- 43. 11011110010 being sent with odd parity
- 44. 00100011110 being sent with even parity
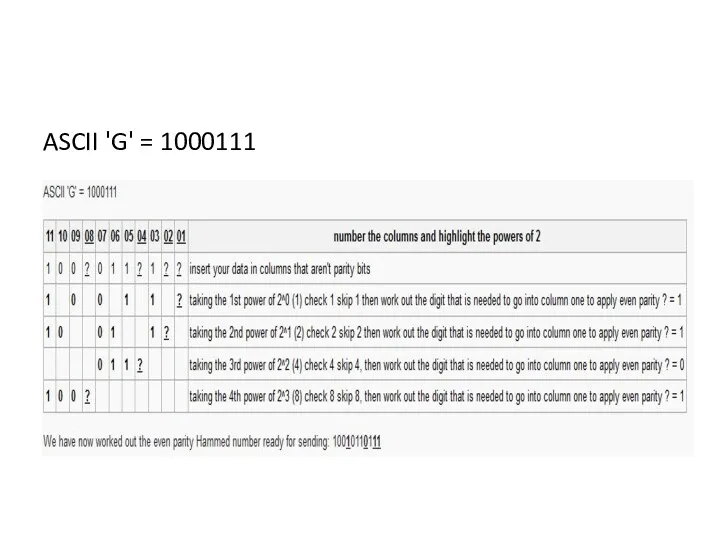
- 45. Applying Hamming code to an ASCII character Apply even parity hamming code so we can transmit
- 46. Exercise Apply even parity hamming code so we can transmit the ASCII character 'G': Apply odd
- 47. ASCII 'G' = 1000111
- 48. 9 = 0001001
- 49. Questions on Network A business uses the Internet to communicate with suppliers and to pay bills
- 50. Must safeguard against unauthorised access to the computer system. Firewall use access to known sources Control
- 51. A health ministry has decided that it would be useful for doctors in that country to
- 52. Describe what is meant by Intranet. Intranet: Restricted access to specific members authorised by the health
- 53. Explain why an intranet was used rather than an open network like the world wide web.
- 54. An import/export company is based in two offices in London and Lahore. Each office has an
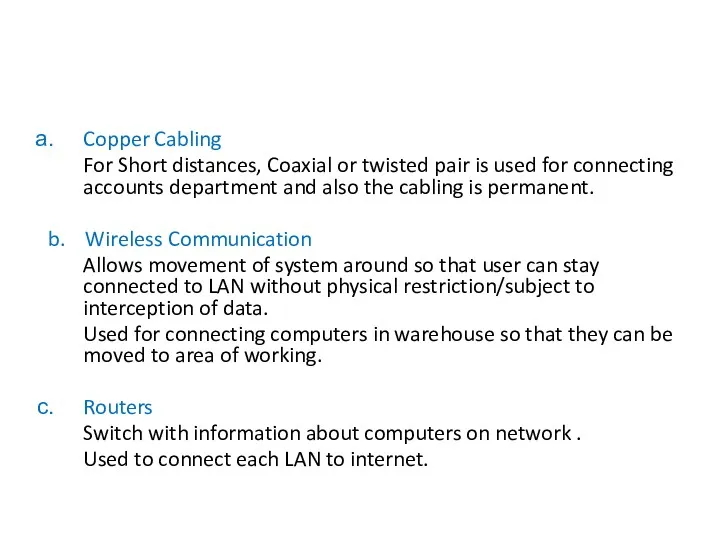
- 55. Copper Cabling For Short distances, Coaxial or twisted pair is used for connecting accounts department and
- 56. e. Bridges Links two LANs/Limits access between the LANs Links the accounts and warehouse LANs while
- 58. Asynchronous and Synchronous Transmission With asynchronous transmission signal timing is not required; signals are sent in
- 59. Serial and Parallel Communication Data can be transmitted between a sender and a receiver in two
- 60. Serial communication is the method of transferring one bit at a time through a medium.
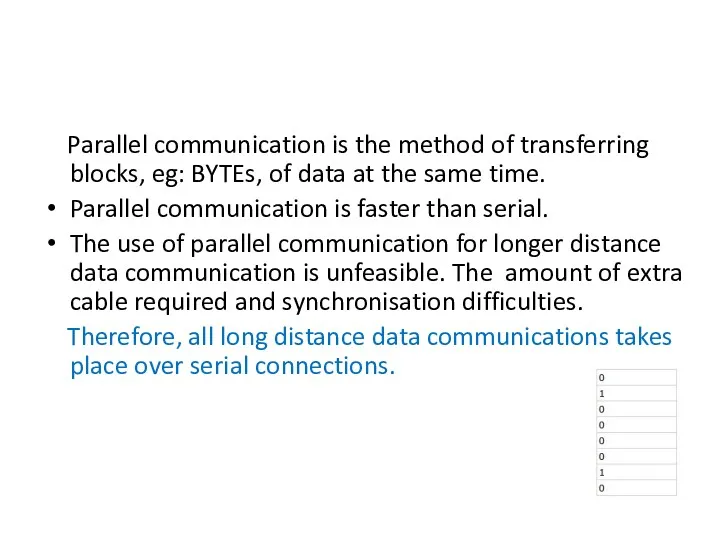
- 61. Parallel communication is the method of transferring blocks, eg: BYTEs, of data at the same time.
- 62. Synchronous Synchronous transmission sends data as one long bit stream or block of data. There are
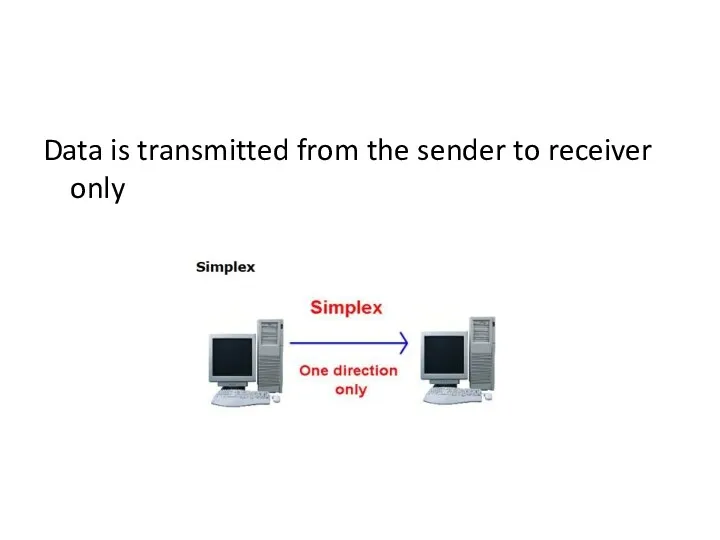
- 63. Data is transmitted from the sender to receiver only
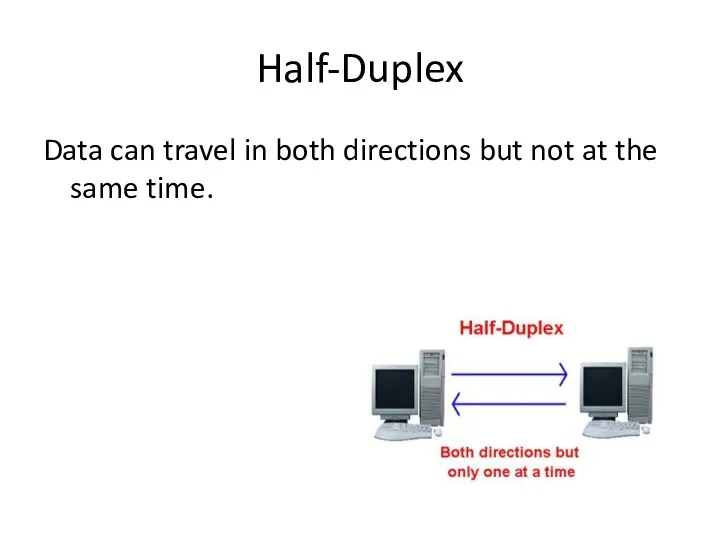
- 64. Half-Duplex Data can travel in both directions but not at the same time.
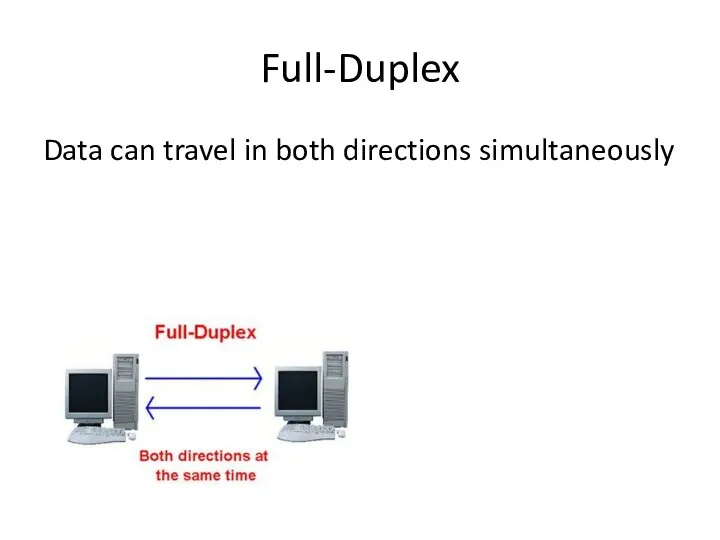
- 65. Full-Duplex Data can travel in both directions simultaneously
- 66. Bit or Data Transmission Rate (DTR) is measured in bits per seconds (bps). The data transmission
- 67. Bridge A Bridge is used to connect two LAN segments. The Bridge maintains a table showing
- 68. Switch A switch receives message, reads the destination label attached to it and only sends it
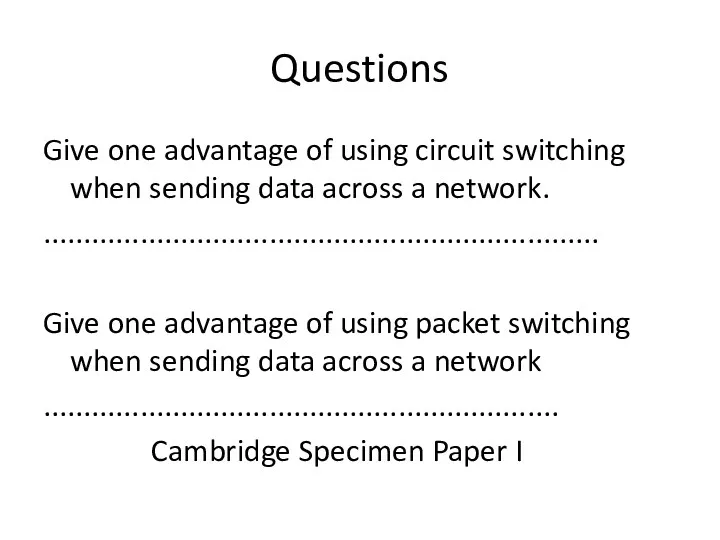
- 69. Questions Give one advantage of using circuit switching when sending data across a network. ..................................................................... Give
- 71. [3] Cambridge 9691 Paper II Q8 June 2011
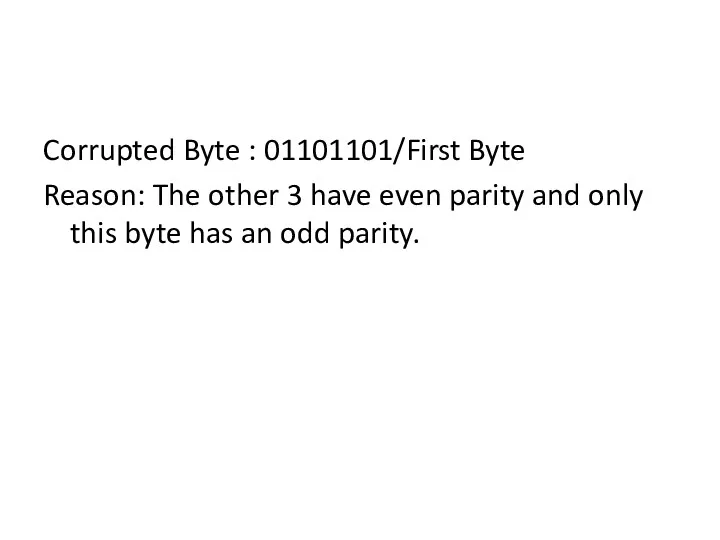
- 72. Corrupted Byte : 01101101/First Byte Reason: The other 3 have even parity and only this byte
- 73. The computers in a school classroom are networked. It is decided that this network should be
- 74. Hardware : Router/Gateway/Modem/Cables Software : Browser/Communications Software/Modem Driver/Firewall
- 75. When a video file is accessed on a network it an be watched as it is
- 76. Video files contain large volumes of data. If watched at a later time then it does
- 77. A Supermarket has a number of point-of-sale terminals. Data is read from goods at the terminals
- 78. Printer – To print the receipt Beeper- To indicate the correctly read the Bar Code
- 79. Validation Validation is a computer check on data which is being input. It is a check
- 80. Range Length Character Format Limit Presence Consistency Check Digit – Extra digit which is calculated from
- 82. Скачать презентацию









































![[3] Cambridge 9691 Paper II Q8 June 2011](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/201580/slide-70.jpg)








 Автоматизированная система организации спортивных мероприятий
Автоматизированная система организации спортивных мероприятий Увлекательный киберспорт, или какие игры лучше для трансляций
Увлекательный киберспорт, или какие игры лучше для трансляций Причины и типы ошибок
Причины и типы ошибок Информационные ресурсы современного общества
Информационные ресурсы современного общества Методика обеспечения строительного контроля с использованием информационной модели здания
Методика обеспечения строительного контроля с использованием информационной модели здания Файлы и файловая система
Файлы и файловая система Устройство компьютера. Носители информации ( 5 класс)
Устройство компьютера. Носители информации ( 5 класс) Применение динамических массивов в структурном подходе
Применение динамических массивов в структурном подходе Методическая разработка урока по теме Компьютерные вирусы. Антивирусные программы
Методическая разработка урока по теме Компьютерные вирусы. Антивирусные программы Сетевая этика. Культура общения в сети
Сетевая этика. Культура общения в сети Верификация программного обеспечения. Дефекты
Верификация программного обеспечения. Дефекты WEB-программирование, семинар 5
WEB-программирование, семинар 5 Новые пакеты услуг Кибернетики
Новые пакеты услуг Кибернетики Работа в ПО Sieble
Работа в ПО Sieble Графические редакторы MediaBang Paint Pro и Artwaver Free
Графические редакторы MediaBang Paint Pro и Artwaver Free База данных как модель предметной области
База данных как модель предметной области Повышение эффективности работы баз данных. Обработка транзакций OLTP-OLAP системы мониторы транзакций
Повышение эффективности работы баз данных. Обработка транзакций OLTP-OLAP системы мониторы транзакций Парсинг HTML. Краткий обзор технологий для понимания сбора и обработки данных
Парсинг HTML. Краткий обзор технологий для понимания сбора и обработки данных Примеры решения задания 14, ОГЭ по информатике
Примеры решения задания 14, ОГЭ по информатике Программы для видеоконференций. Введение
Программы для видеоконференций. Введение Онлайн-сервисы для создания электронных игр и викторин
Онлайн-сервисы для создания электронных игр и викторин Автоматизация научных исследований
Автоматизация научных исследований Цвет. Background. Градиент
Цвет. Background. Градиент Методическая разработка внеклассного мероприятия (интеллектуальная игра) по физике и информатике для учащихся 5-11 классов Кто хочет стать отличником
Методическая разработка внеклассного мероприятия (интеллектуальная игра) по физике и информатике для учащихся 5-11 классов Кто хочет стать отличником Операционная система
Операционная система Нові можливості функцій в мові С++
Нові можливості функцій в мові С++ Переход от инфологического моделирования к моделям данных и знаний. Логико-лингвистические модели представления знаний
Переход от инфологического моделирования к моделям данных и знаний. Логико-лингвистические модели представления знаний КВН по информатике
КВН по информатике