Содержание
- 2. whoami Security consultant at NCC Group +10 years in web application security Researcher and bug hunter
- 3. Flash Isn’t Quite Dead Yet! They ignore it, they laugh at it, but they have to
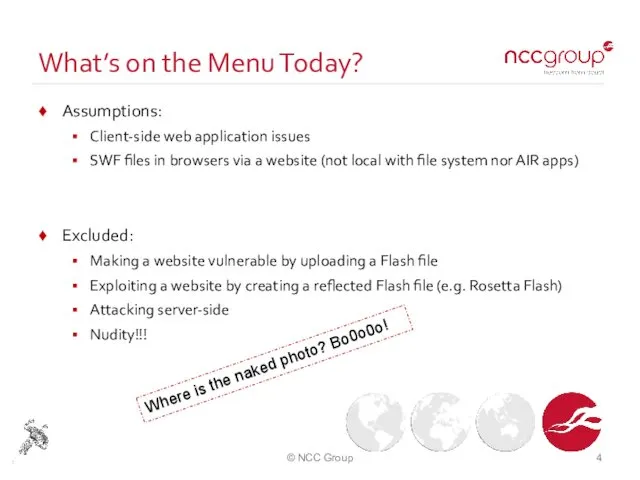
- 4. What’s on the Menu Today? Assumptions: Client-side web application issues SWF files in browsers via a
- 5. Introduction ActionScript is based on ECMAScript ? .SWF -> A compiled Flash file (binary) -> We
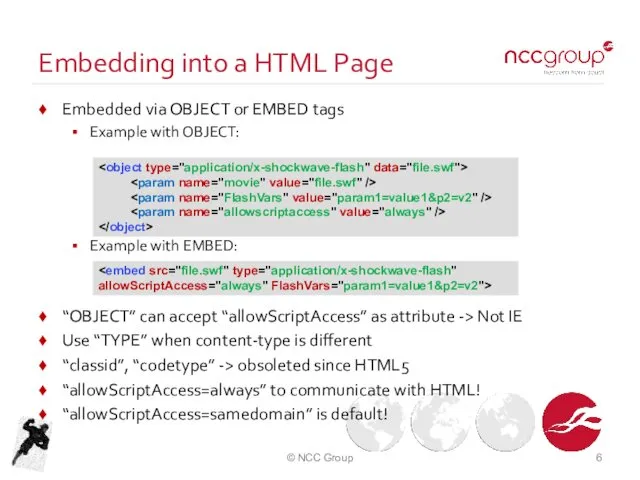
- 6. Embedding into a HTML Page Embedded via OBJECT or EMBED tags Example with OBJECT: Example with
- 7. Bug Hunting Strategy Finding Flash Files Google… filetype:swf site:example.com Download open source apps/libs Search in contents
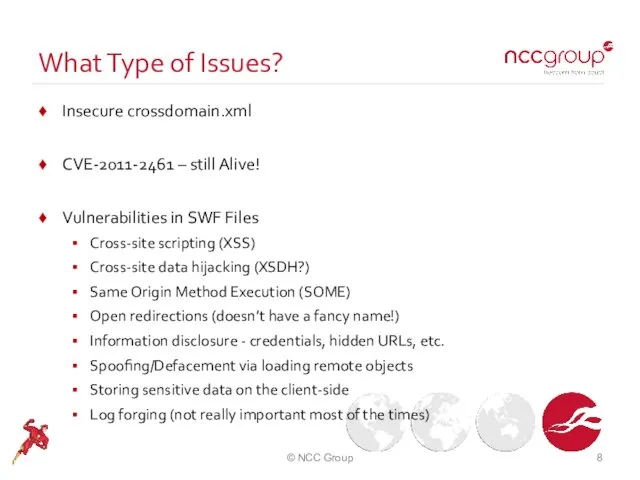
- 8. What Type of Issues? Insecure crossdomain.xml CVE-2011-2461 – still Alive! Vulnerabilities in SWF Files Cross-site scripting
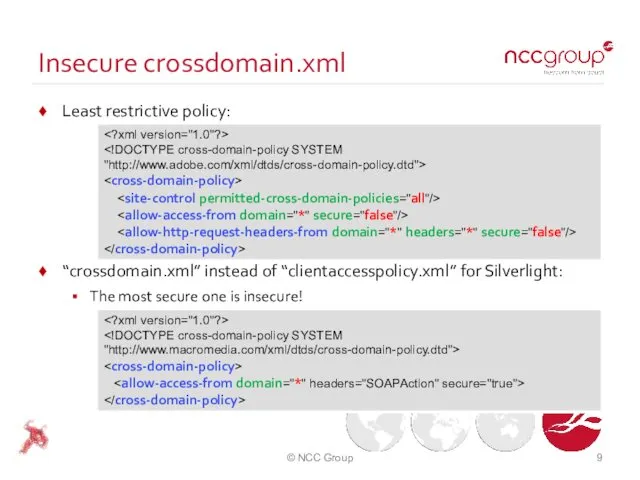
- 9. Insecure crossdomain.xml Least restrictive policy: “crossdomain.xml” instead of “clientaccesspolicy.xml” for Silverlight: The most secure one is
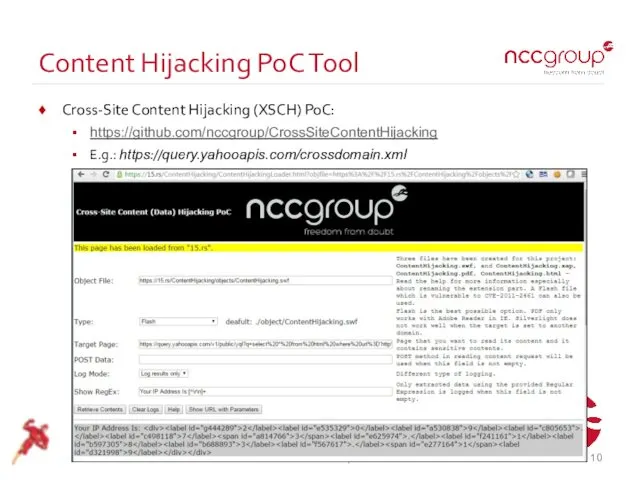
- 10. Content Hijacking PoC Tool Cross-Site Content Hijacking (XSCH) PoC: https://github.com/nccgroup/CrossSiteContentHijacking E.g.: https://query.yahooapis.com/crossdomain.xml © NCC Group
- 11. CVE-2011-2461 - The Dead is Alive! Flex SDK issue (between 3.x and 4.5.1) A new input
- 12. Finding CVE-2011-2461 ParrotNG to the rescue! with Burp Suite extension (passive scan)! Make sure it is
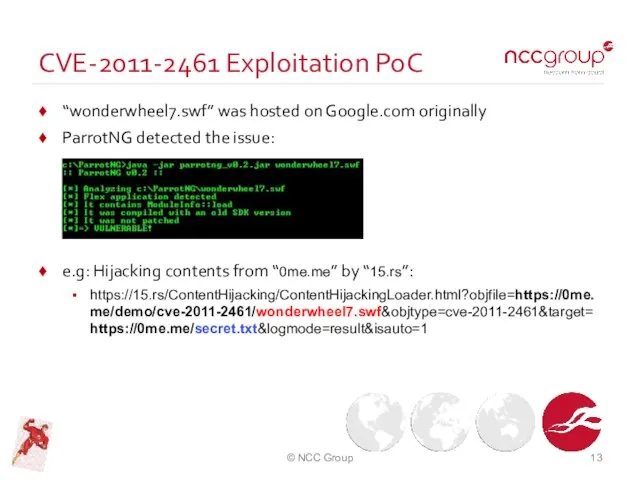
- 13. CVE-2011-2461 Exploitation PoC “wonderwheel7.swf” was hosted on Google.com originally ParrotNG detected the issue: e.g: Hijacking contents
- 14. Important: Do Not Reinvent the Wheel! Search for known vulnerabilities e.g.: https://web.archive.org/web/20130730223443/http://web.appsec.ws/FlashExploitDatabase.php Search their issue tracker
- 15. Automated Testing Listed in OWASP Flash Security Project: FlashDiggity Decompile -> Search using RegEx Extractable Rules:
- 16. Updated SWFIntruder + Updated SWFIntruder: Dirty fix for the original SWFIntruder Uses several payloads for each
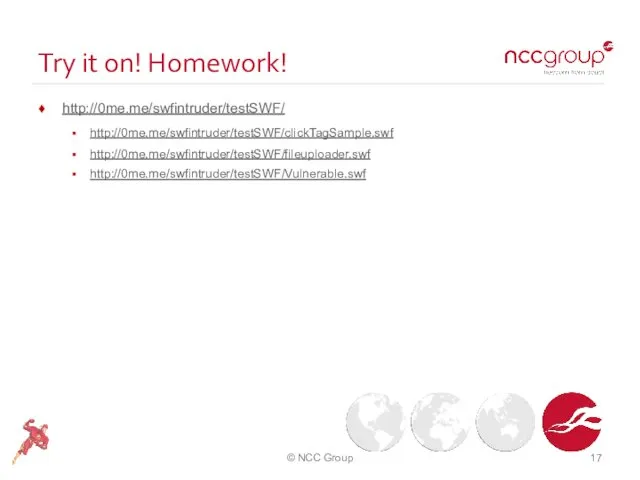
- 17. Try it on! Homework! http://0me.me/swfintruder/testSWF/ http://0me.me/swfintruder/testSWF/clickTagSample.swf http://0me.me/swfintruder/testSWF/fileuploader.swf http://0me.me/swfintruder/testSWF/Vulnerable.swf © NCC Group
- 18. Manual Testing Preparing testing environment Compiling ActionScript files Decompiling SWF files Finding inputs (sources) Finding usage
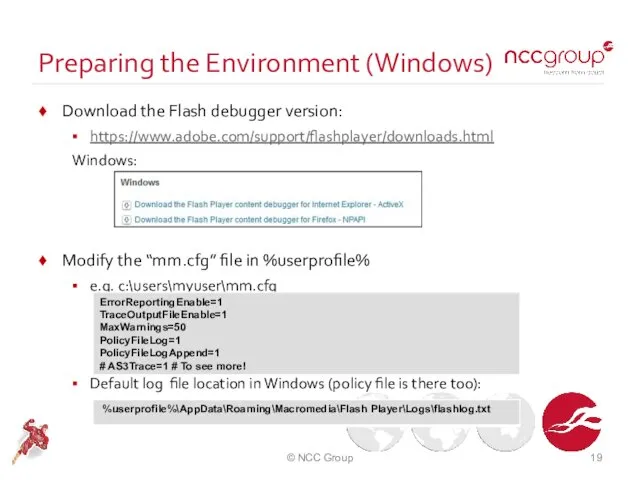
- 19. Preparing the Environment (Windows) Download the Flash debugger version: https://www.adobe.com/support/flashplayer/downloads.html Windows: Modify the “mm.cfg” file in
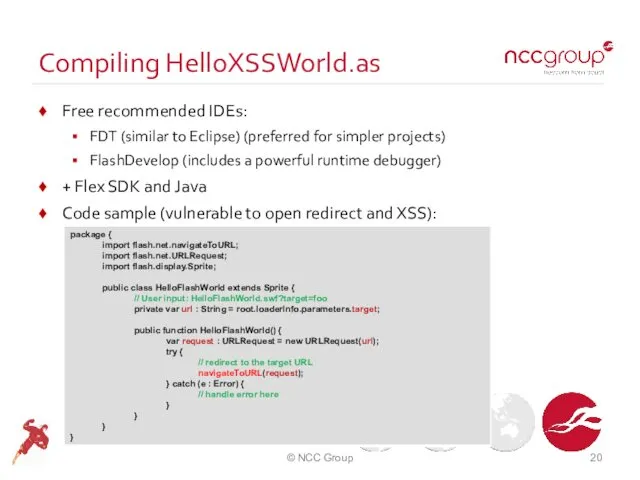
- 20. Compiling HelloXSSWorld.as Free recommended IDEs: FDT (similar to Eclipse) (preferred for simpler projects) FlashDevelop (includes a
- 21. Decompiling a SWF File Recommended decompiler: JPEXS Free Flash Decompiler Easy to use UI Can edit
- 22. Decompiled, Now What? AS1/2 or AS3? http://dev.sitedaniel.com/swfinfo/swfinfo.swf - added to Updated SWF Intruder Find input parameters
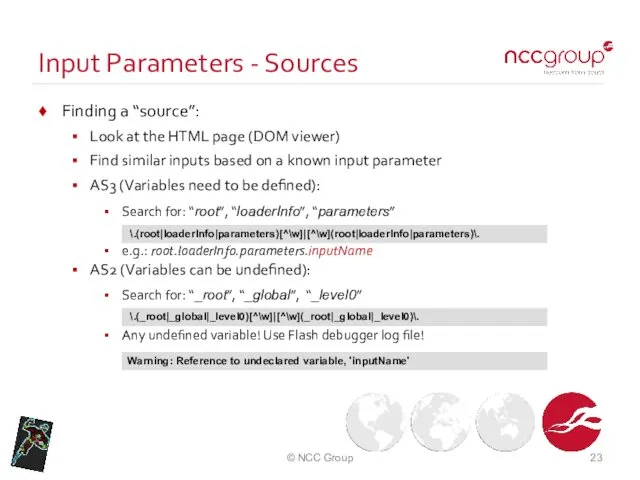
- 23. Input Parameters - Sources Finding a “source”: Look at the HTML page (DOM viewer) Find similar
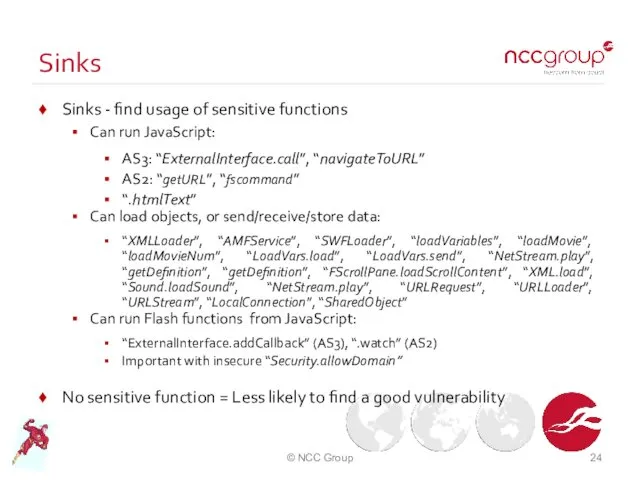
- 24. Sinks Sinks - find usage of sensitive functions Can run JavaScript: AS3: “ExternalInterface.call”, “navigateToURL” AS2: “getURL”,
- 25. Source Sink Flow! Tainted source --> … --> sink! Sink Any validation? What is allowed? Is
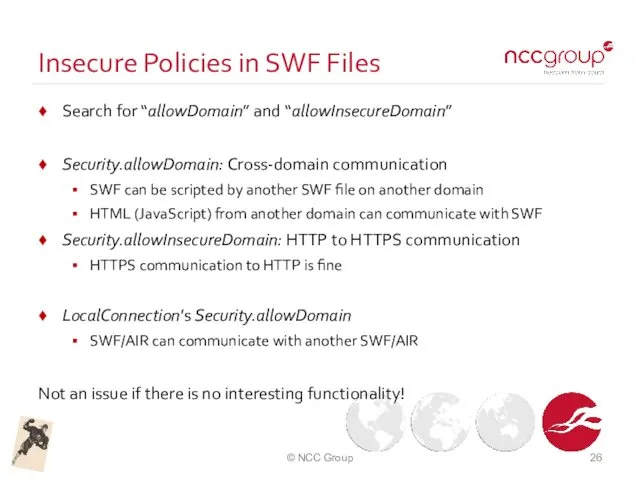
- 26. Insecure Policies in SWF Files Search for “allowDomain” and “allowInsecureDomain” Security.allowDomain: Cross-domain communication SWF can be
- 27. Sensitive Data / Hidden URLs / Gems! Think like a forensic analyst! Search for: URLs Emails
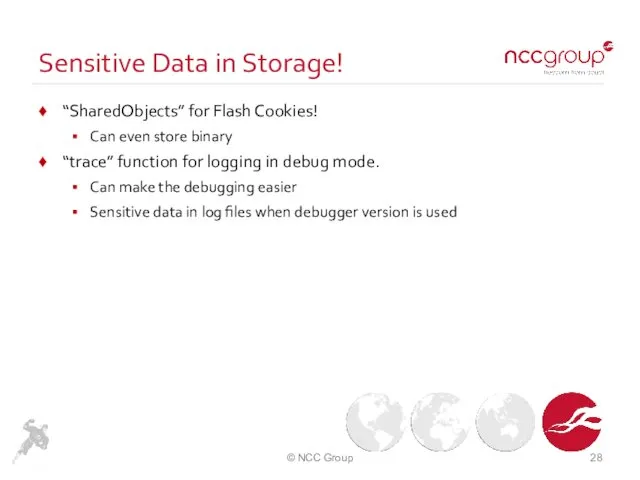
- 28. Sensitive Data in Storage! “SharedObjects” for Flash Cookies! Can even store binary “trace” function for logging
- 29. Find More! Be creative! Always look at the FlashVars parameter names Anything called “onload”, “onclick”, or
- 30. “ExternalInterface.call” XSS Confusion! Accept JS function name and its parameters Both can lead to XSS The
- 31. Bypassing Client Side Protections Protections on the client side only make it more user friendly Not
- 32. More Issues… Identify and review the sensitive functions Such as login or encryption functions Flash files
- 33. FlashVars Tips! Passing parameters in URL: File.swf?param1=value1&p2=v2 Removes invalid encoding param1=value1 -> pa%Xram1=val%Yue1 param1=value1 -> pa%=ram1=val%#ue1
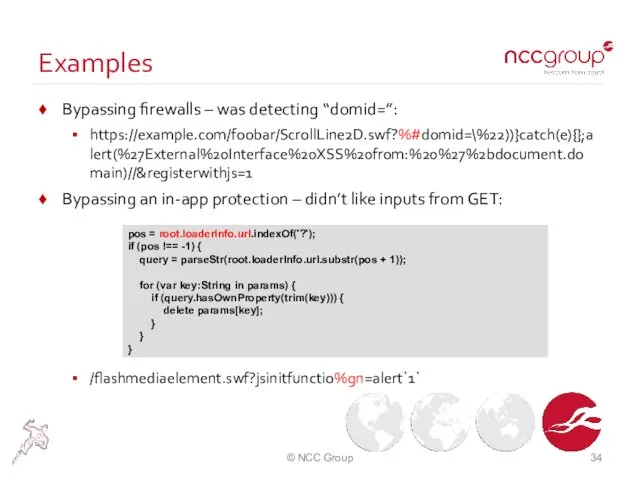
- 34. Examples Bypassing firewalls – was detecting “domid=”: https://example.com/foobar/ScrollLine2D.swf?%#domid=\%22))}catch(e){};alert(%27External%20Interface%20XSS%20from:%20%27%2bdocument.domain)//®isterwithjs=1 Bypassing an in-app protection – didn’t like inputs
- 35. Demo – Finding Vulnerabilities! clickTagSample.swf ? ActionScript2 vulnerable.swf ? ActionSctipt2 Homework: fileuploader.swf ? ActionScript3 Answer (in
- 36. Used RegExes in Demo AS3 Inputs: \.(root|loaderInfo|parameters)[^\w]|[^\w](root|loaderInfo|parameters)\. AS2 Inputs (remember undefined inputs – follow the sinks):
- 37. Final Notes Search in your proxy logs for “SWF” files! JS libraries and plugins can contain
- 38. Thank you! Questions? Really? Why?! ;) Sample files in: https://github.com/irsdl/Flash-Files-Vulnerability-Database © NCC Group
- 39. References & Further Reading - 1 Securely deploying cross-domain policy files http://blogs.adobe.com/security/2009/11/securely_deploying_cross-domai.html Related to Flash policy
- 40. References & Further Reading - 2 ParrotNG project to find CVE-2011-2461 vulnerable files https://github.com/ikkisoft/ParrotNG Testing for
- 42. Скачать презентацию

















![Used RegExes in Demo AS3 Inputs: \.(root|loaderInfo|parameters)[^\w]|[^\w](root|loaderInfo|parameters)\. AS2 Inputs (remember](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/93543/slide-35.jpg)


 Базы данных. Введение
Базы данных. Введение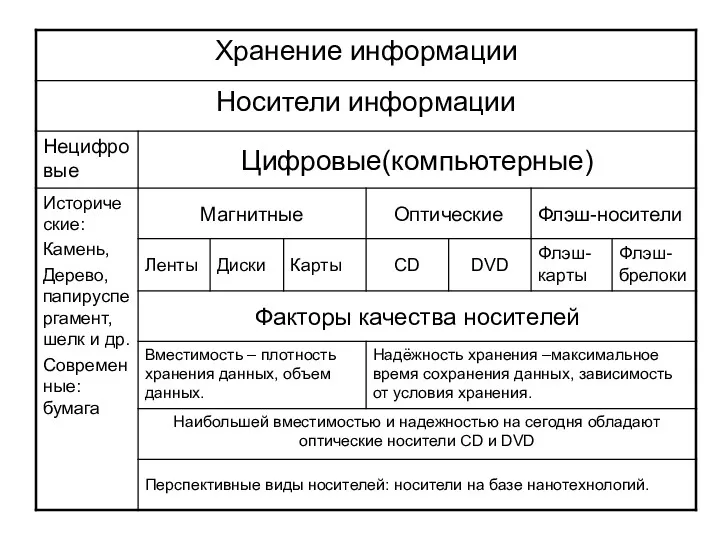 Хранение информации. Носители информации
Хранение информации. Носители информации Формы мышления. Логика
Формы мышления. Логика Использование модели eTOM при разработке и внедрении систем OSS/BSS
Использование модели eTOM при разработке и внедрении систем OSS/BSS Анекс Тур. Электронный документооборот для агентов
Анекс Тур. Электронный документооборот для агентов Криптография. Симметричные алгоритмы шифрования
Криптография. Симметричные алгоритмы шифрования Арифметические основы организации ЭВМ
Арифметические основы организации ЭВМ Среда исполнителя Робот
Среда исполнителя Робот Мікроконтролерна система цифрової ідентифікації персоналу для ЧДУ ім. П. Могили
Мікроконтролерна система цифрової ідентифікації персоналу для ЧДУ ім. П. Могили Кибербезопасность или как защитить личные данные в сети
Кибербезопасность или как защитить личные данные в сети Тестирование. Подготовка тестовых данных
Тестирование. Подготовка тестовых данных Послеаварийное восстановление работоспособности компьютерной сети
Послеаварийное восстановление работоспособности компьютерной сети PL/SQL. Процедурное расширение языка SQL. (Лекция 7)
PL/SQL. Процедурное расширение языка SQL. (Лекция 7) Диалог с информационной системой
Диалог с информационной системой JavaScript. Java-апплет
JavaScript. Java-апплет Виды Баз Данных
Виды Баз Данных Микропроцессорные системы управления
Микропроцессорные системы управления Масштабируемая веб-архитектура и распределенные системы
Масштабируемая веб-архитектура и распределенные системы Gestures and memes
Gestures and memes Моделирование на UML. Определение UML. Лекция 1
Моделирование на UML. Определение UML. Лекция 1 Боты на .Net, информация и примеры
Боты на .Net, информация и примеры Подходы к оценке информации
Подходы к оценке информации Применение искусственного интеллекта в косметологии
Применение искусственного интеллекта в косметологии Презентация Графический метод решения уравнений в Excel
Презентация Графический метод решения уравнений в Excel Програмування пристрою для контролю температури на базі мікроконтролера RISC-архітектури
Програмування пристрою для контролю температури на базі мікроконтролера RISC-архітектури Программирование. Лекция 4
Программирование. Лекция 4 Мультимедиа библиотек (02)
Мультимедиа библиотек (02) Мастер-класс. Создание онлайн курсов с помощью STEPIK.ORG
Мастер-класс. Создание онлайн курсов с помощью STEPIK.ORG