Содержание
- 2. Internet Security Internet security is a branch of computer security. It encompasses the Internet, browser security,
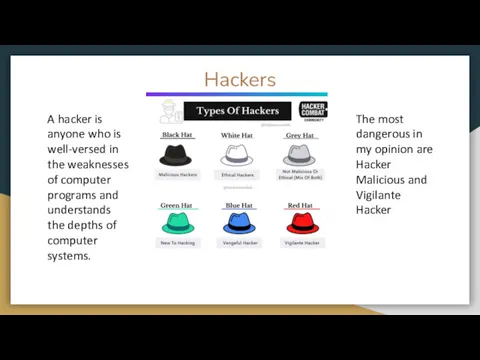
- 3. Hackers The most dangerous in my opinion are Hacker Malicious and Vigilante Hacker A hacker is
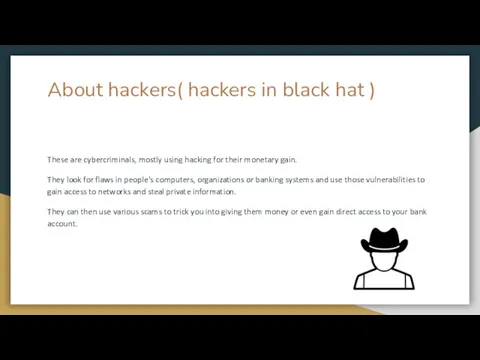
- 4. About hackers( hackers in black hat ) These are cybercriminals, mostly using hacking for their monetary
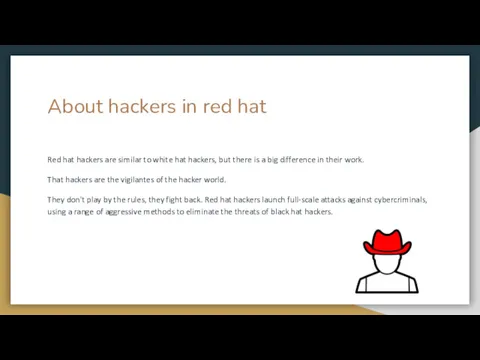
- 5. About hackers in red hat Red hat hackers are similar to white hat hackers, but there
- 6. Green hat hackers These are beginners who want to become professional hackers. They have a great
- 7. Blue Hat Hackers They are amateur hackers, not interested in learning the intricacies of hacking. Their
- 8. About Spam Spamming is the use of messaging systems to send multiple unsolicited messages (spam) to
- 9. Phishing what is this? Phishing is a type of social engineering where an attacker sends a
- 10. Phishing in Email Most phishing messages are delivered by email, and are not personalized or targeted
- 11. Threat identies A threat to information security is understood as a set of conditions and factors,
- 12. In the process of analyzing threats to information it is necessary to evaluate: the source of
- 13. Conclusion on information security. The conclusion is that there are a lot of hackers in the
- 14. Presentation test. What are the most dangerous hackers? Black hackers (1) Blue hat hackers Green hat
- 15. What is this phishing? Is a type of social engineering where an attacker sends a fraudulent
- 16. Put the information in the right order the source of risk.(1) risk area.(2) the hypothetical perpetrator.(3)
- 17. What types of phishing do you know? Tell us about phishing on the Internet that you
- 19. Скачать презентацию







 Антивирусные программы
Антивирусные программы Возможности динамических (электронных) таблиц. Лекция
Возможности динамических (электронных) таблиц. Лекция Компьютерные игры: вредно или полезно
Компьютерные игры: вредно или полезно Переменные. Модуль 1. Урок 2. Международная школа программирования для детей
Переменные. Модуль 1. Урок 2. Международная школа программирования для детей Персональные данные
Персональные данные Файловые архивы. Поиск информации в сети Интернет.
Файловые архивы. Поиск информации в сети Интернет. Main Game
Main Game Дискретный анализ. Лекция 1
Дискретный анализ. Лекция 1 9-2-4
9-2-4 План-конспект урока информатики Решение расчетных задач с помощью электронных таблиц
План-конспект урока информатики Решение расчетных задач с помощью электронных таблиц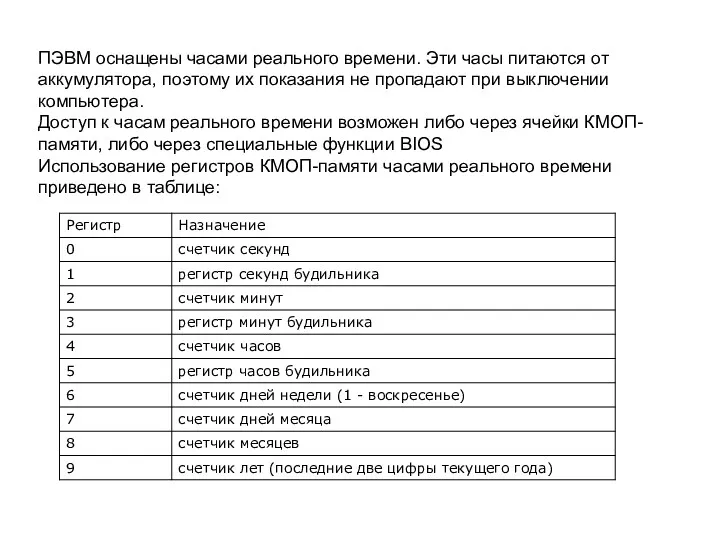 Оснащение ПЭВМ часами реального времени
Оснащение ПЭВМ часами реального времени Проведение онлайн-смены летнего лагеря
Проведение онлайн-смены летнего лагеря Дистанційне навчання
Дистанційне навчання Свойства алгоритма
Свойства алгоритма Реляционная база данных
Реляционная база данных Разработка урока Знакомство с Visual Basic
Разработка урока Знакомство с Visual Basic Пенсійний фонд України. Організація впровадження централізованої системи призначення та виплати пенсій
Пенсійний фонд України. Організація впровадження централізованої системи призначення та виплати пенсій Тема 15. Инерциальные навигационные системы. Занятие 3. Инерциальная курсовертикаль ИКВ-1
Тема 15. Инерциальные навигационные системы. Занятие 3. Инерциальная курсовертикаль ИКВ-1 Графические возможности табличного процессора MS Excel 2010 при работе с базами данных
Графические возможности табличного процессора MS Excel 2010 при работе с базами данных Числа со знаком. Операции в языке С. Ассемблерные команды, им соответствующие
Числа со знаком. Операции в языке С. Ассемблерные команды, им соответствующие Геймінг – це гра у відеоігри на колективних турнірах
Геймінг – це гра у відеоігри на колективних турнірах Современные проблемы информационной эпохи: новые вызовы для человека и общества
Современные проблемы информационной эпохи: новые вызовы для человека и общества Настройка информационной системы домена
Настройка информационной системы домена Объекты и множества. Объекты изучения в информатике. Признаки объектов
Объекты и множества. Объекты изучения в информатике. Признаки объектов Компьютерные вирусы
Компьютерные вирусы История языков программирования. 9 класс
История языков программирования. 9 класс Операційна система Windows
Операційна система Windows Электронды пошта. Хабарлар құру және хаттармен жұмыс
Электронды пошта. Хабарлар құру және хаттармен жұмыс