Содержание
- 2. In computer science, a space–time or time–memory tradeoff is a situation where the memory use can
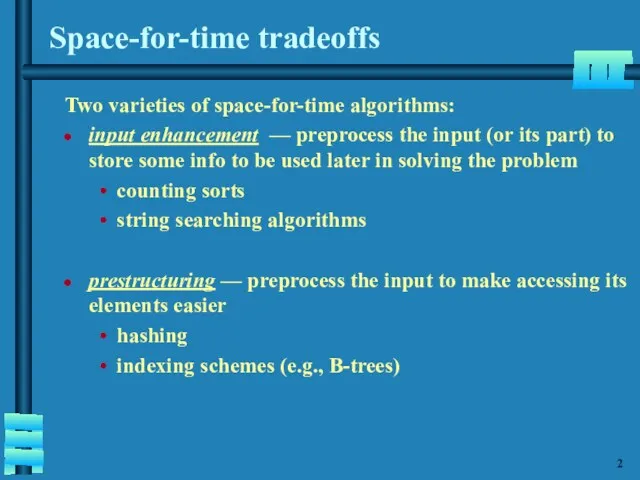
- 3. Space-for-time tradeoffs Two varieties of space-for-time algorithms: input enhancement — preprocess the input (or its part)
- 4. Review: String searching by brute force pattern: a string of m characters to search for text:
- 5. String searching by preprocessing Several string searching algorithms are based on the input enhancement idea of
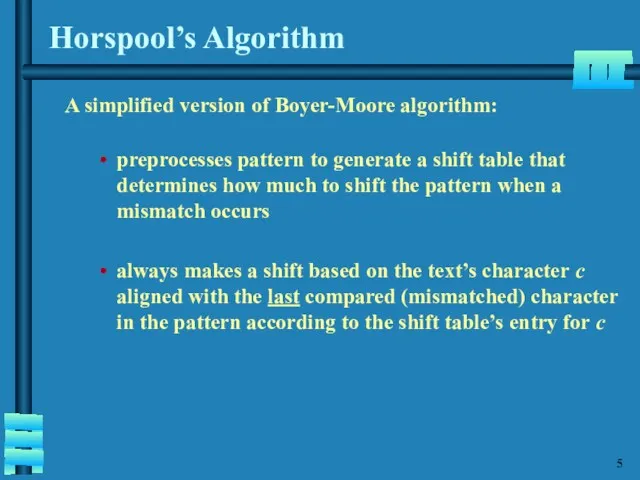
- 6. Horspool’s Algorithm A simplified version of Boyer-Moore algorithm: preprocesses pattern to generate a shift table that
- 7. How far to shift? Look at first (rightmost) character in text that was compared: The character
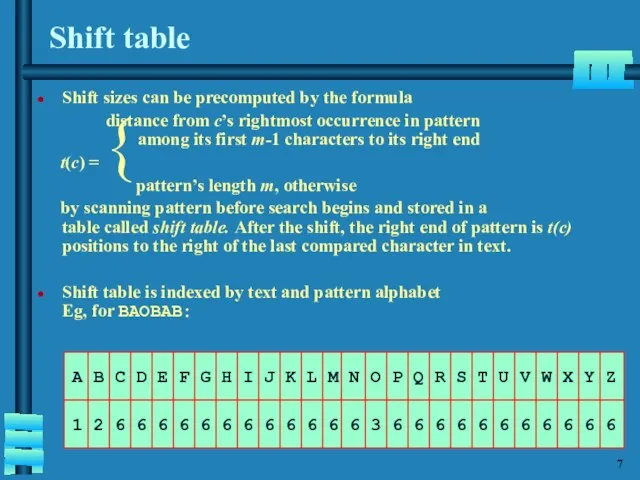
- 8. Shift table Shift sizes can be precomputed by the formula distance from c’s rightmost occurrence in
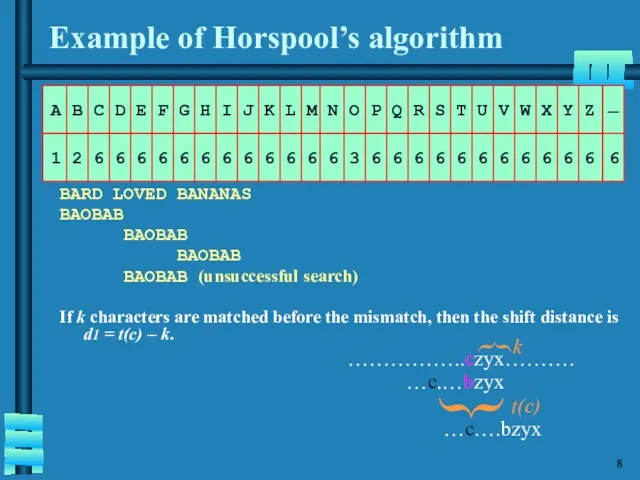
- 9. Example of Horspool’s algorithm BARD LOVED BANANAS BAOBAB BAOBAB BAOBAB BAOBAB (unsuccessful search) If k characters
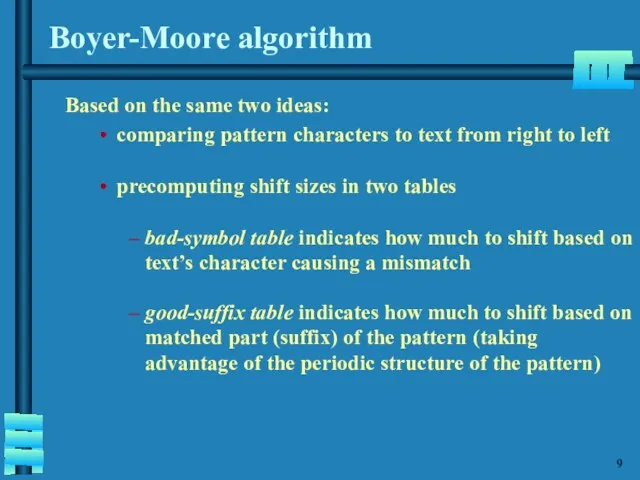
- 10. Boyer-Moore algorithm Based on the same two ideas: comparing pattern characters to text from right to
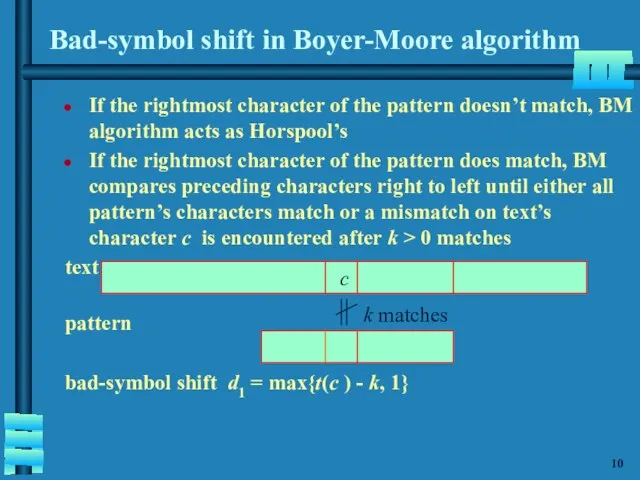
- 11. Bad-symbol shift in Boyer-Moore algorithm If the rightmost character of the pattern doesn’t match, BM algorithm
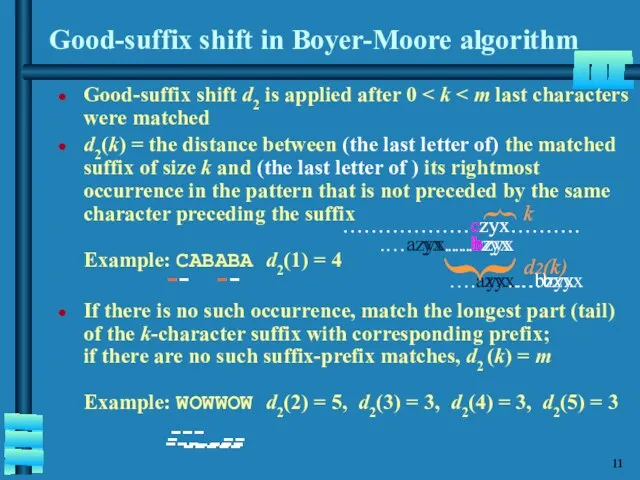
- 12. Good-suffix shift in Boyer-Moore algorithm Good-suffix shift d2 is applied after 0 d2(k) = the distance
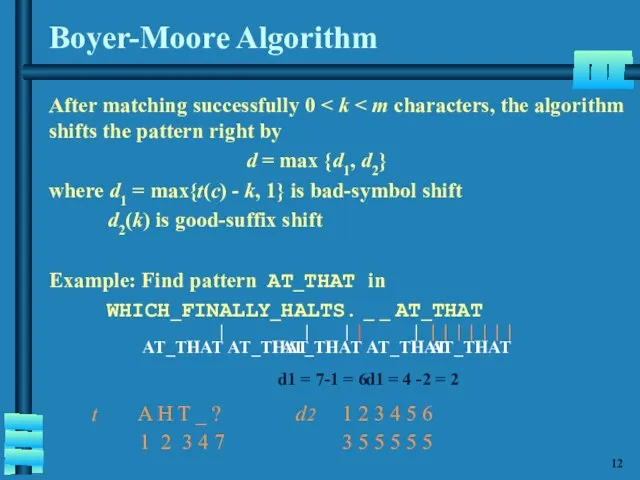
- 13. Boyer-Moore Algorithm After matching successfully 0 d = max {d1, d2} where d1 = max{t(c) -
- 14. Boyer-Moore Algorithm (cont.) Step 1 Fill in the bad-symbol shift table Step 2 Fill in the
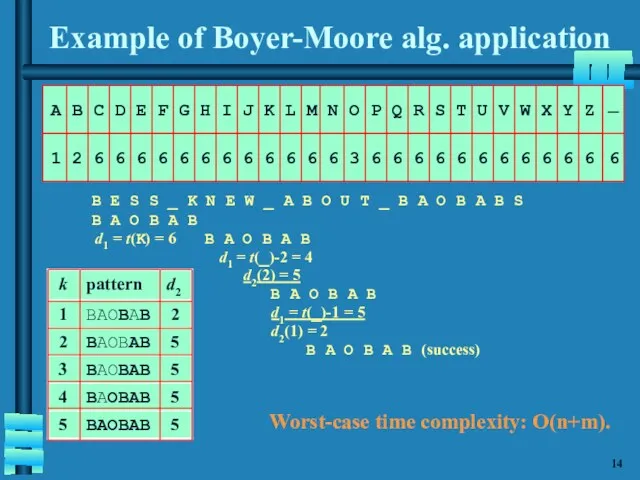
- 15. Example of Boyer-Moore alg. application B E S S _ K N E W _ A
- 16. Hashing A very efficient method for implementing a dictionary, i.e., a set with the operations: find
- 17. Hash tables and hash functions The idea of hashing is to map keys of a given
- 18. Collisions If h(K1) = h(K2), there is a collision Good hash functions result in fewer collisions
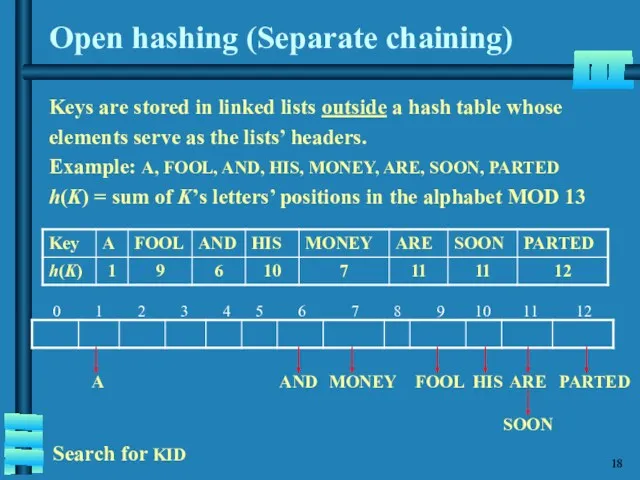
- 19. Open hashing (Separate chaining) Keys are stored in linked lists outside a hash table whose elements
- 21. Скачать презентацию








 Автоматизация тестирования. Jenkins CI. Лекция 9. A1QA - Jenkins CI
Автоматизация тестирования. Jenkins CI. Лекция 9. A1QA - Jenkins CI 7 класс, урок Устройства ввода-вывода
7 класс, урок Устройства ввода-вывода Telegram бот для постановки задач в Jira
Telegram бот для постановки задач в Jira Автоматизированные системы управления
Автоматизированные системы управления Оценка информационных рисков при использовании облачных сервисов
Оценка информационных рисков при использовании облачных сервисов Локальды компьютерлік желілер. Локальды желілердің түрлері
Локальды компьютерлік желілер. Локальды желілердің түрлері Эффективный поиск в интернете. Сайты спортивных федераций РФ
Эффективный поиск в интернете. Сайты спортивных федераций РФ Школа подготовки технических администраторов. Домены, хостинги, сайты. (Занятие 11)
Школа подготовки технических администраторов. Домены, хостинги, сайты. (Занятие 11) Операторы цикла. Цикл с предусловием
Операторы цикла. Цикл с предусловием Жизненный цикл программного обеспечения
Жизненный цикл программного обеспечения ГПБ Ипотека SC. Инструкция
ГПБ Ипотека SC. Инструкция Презентация к уроку Информационные процессы
Презентация к уроку Информационные процессы Базы данных. Лекция 7
Базы данных. Лекция 7 Корректировка гистограммы контейнера при встраивании данных с использованием кодов Хэмминга
Корректировка гистограммы контейнера при встраивании данных с использованием кодов Хэмминга Проектная технология на уроках информатики
Проектная технология на уроках информатики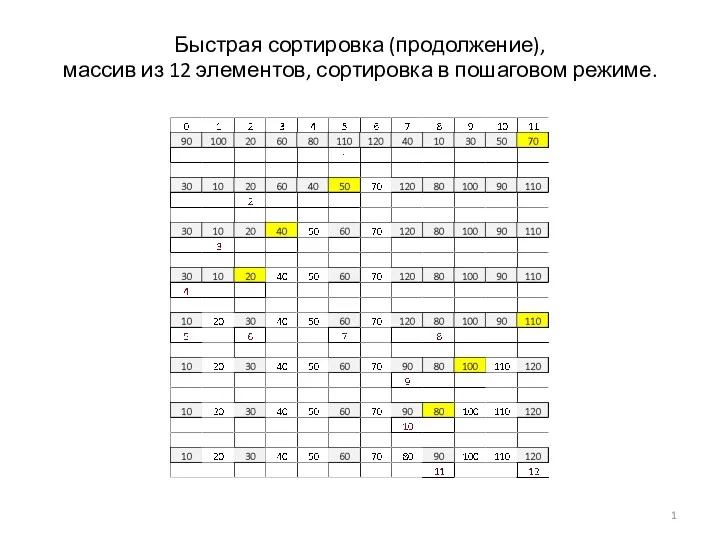 Быстрая сортировка. Массив из 12 элементов, сортировка в пошаговом режиме
Быстрая сортировка. Массив из 12 элементов, сортировка в пошаговом режиме UML. Диаграмма классов
UML. Диаграмма классов Развитие детского и молодежного информационного пространства
Развитие детского и молодежного информационного пространства Запросы к нескольким таблицам. Работа с SQL
Запросы к нескольким таблицам. Работа с SQL Линейные алгоритмы в паскале
Линейные алгоритмы в паскале Протокол разделения секрета и другие протоколы
Протокол разделения секрета и другие протоколы Веселый тест
Веселый тест Автоматическая обработка информации
Автоматическая обработка информации Устройства управления
Устройства управления Проверка на нормальность распределения. Законы распределения вероятностей в R
Проверка на нормальность распределения. Законы распределения вероятностей в R Интеллектуальные информационные системы. Понятие ИИС
Интеллектуальные информационные системы. Понятие ИИС Пошаговая инструкция по регистрации добровольных пожарных на портале Госуслуги
Пошаговая инструкция по регистрации добровольных пожарных на портале Госуслуги Information technologies in the professional sphere
Information technologies in the professional sphere