Содержание
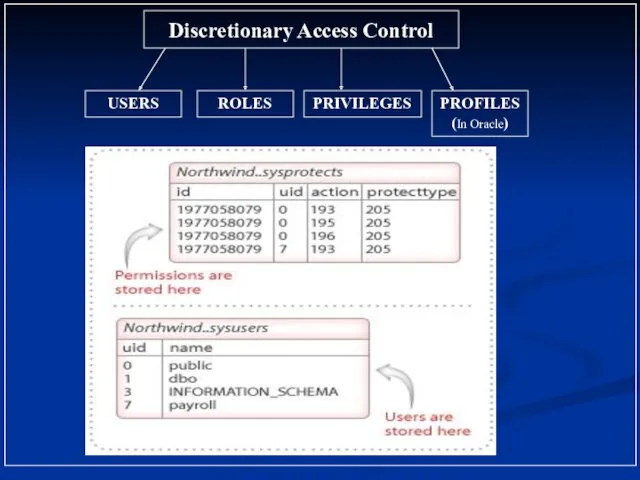
- 2. Discretionary Access Control USERS ROLES PRIVILEGES PROFILES (In Oracle)
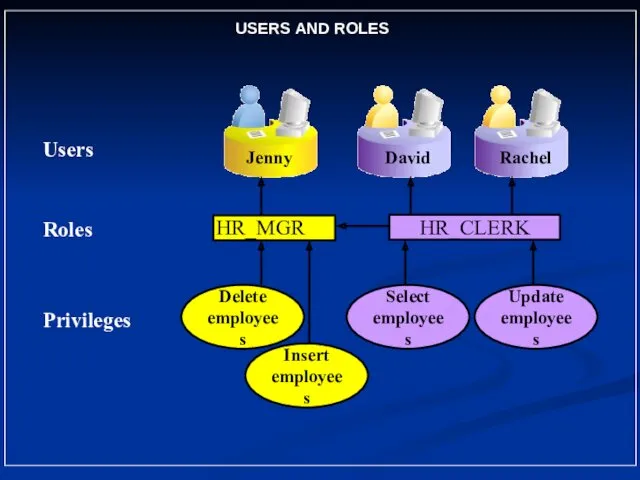
- 3. Users Privileges HR_CLERK HR_MGR Jenny David Rachel Delete employees Select employees Update employees Insert employees USERS
- 4. Privileges Database security: System security Data security System privileges: Gaining access to the database Object privileges:
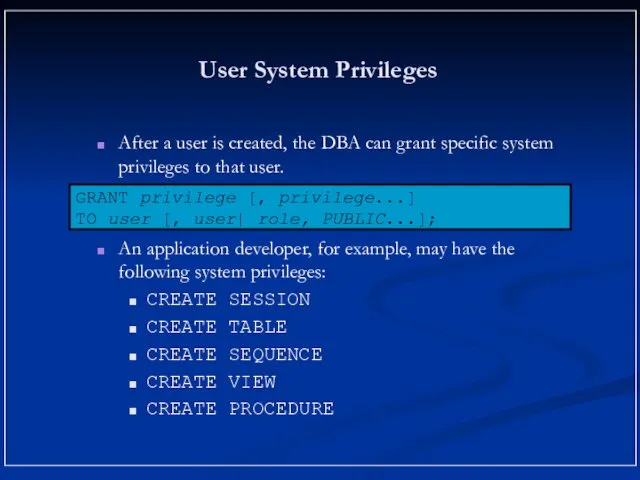
- 5. System Privileges More than 100 privileges are available. The database administrator has high-level system privileges for
- 6. Oracle Access Control
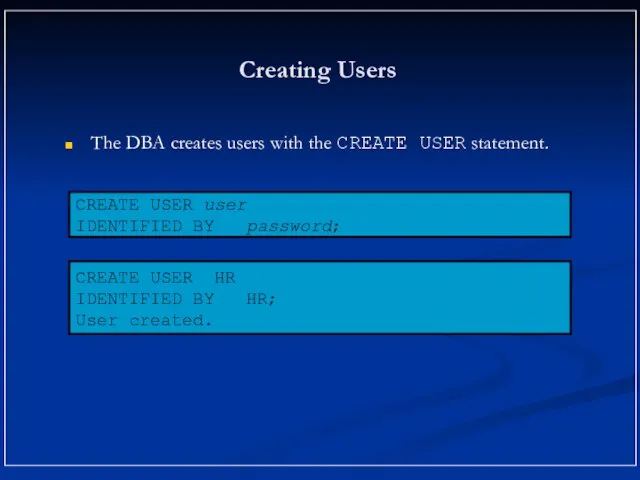
- 7. Creating Users The DBA creates users with the CREATE USER statement. CREATE USER HR IDENTIFIED BY
- 8. User System Privileges After a user is created, the DBA can grant specific system privileges to
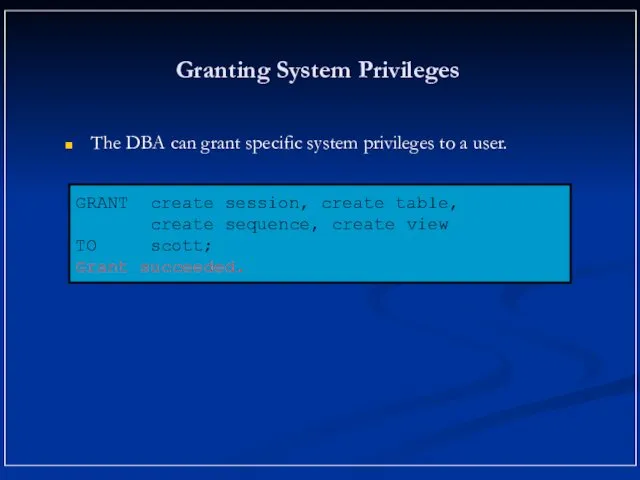
- 9. Granting System Privileges The DBA can grant specific system privileges to a user. GRANT create session,
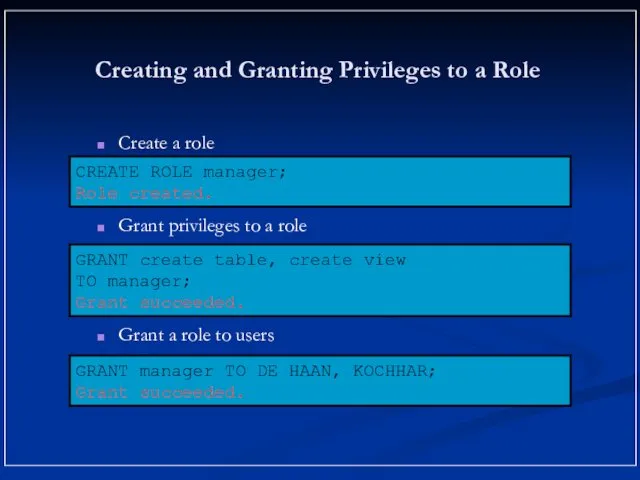
- 10. Creating and Granting Privileges to a Role Create a role Grant privileges to a role Grant
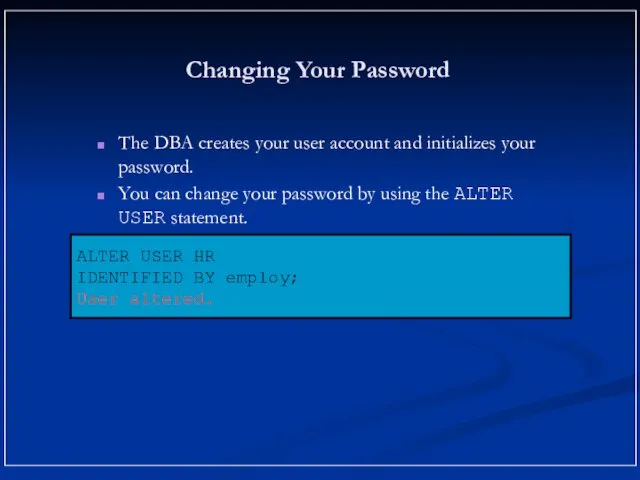
- 11. Changing Your Password The DBA creates your user account and initializes your password. You can change
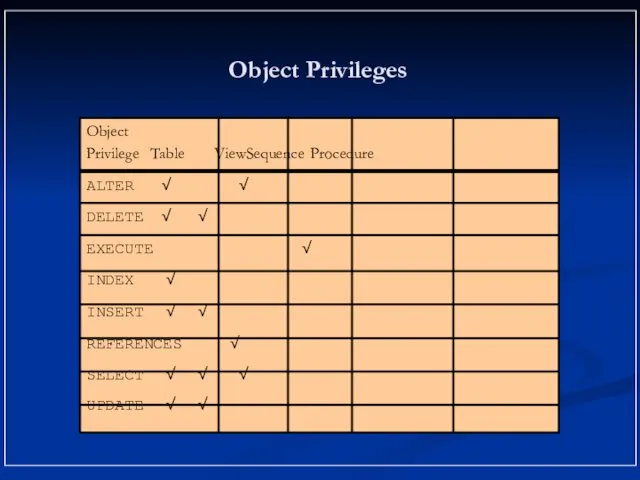
- 12. Object Privileges
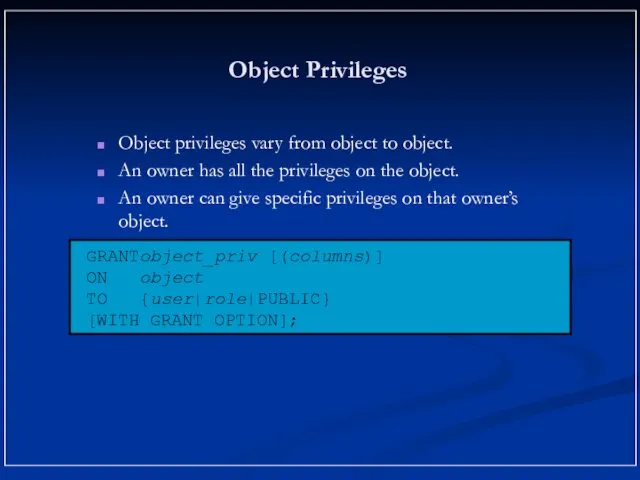
- 13. Object Privileges Object privileges vary from object to object. An owner has all the privileges on
- 14. Granting Object Privileges Grant query privileges on the EMPLOYEES table. Grant privileges to update specific columns
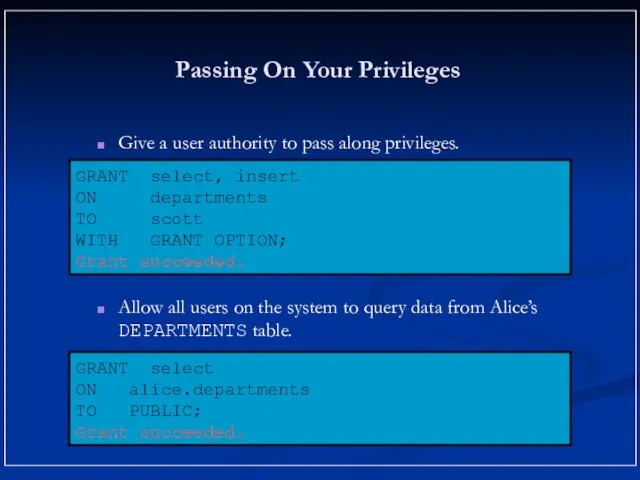
- 15. Passing On Your Privileges Give a user authority to pass along privileges. Allow all users on
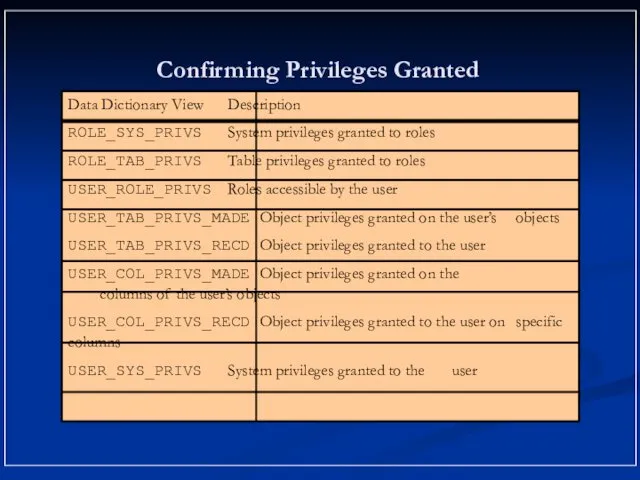
- 16. Confirming Privileges Granted
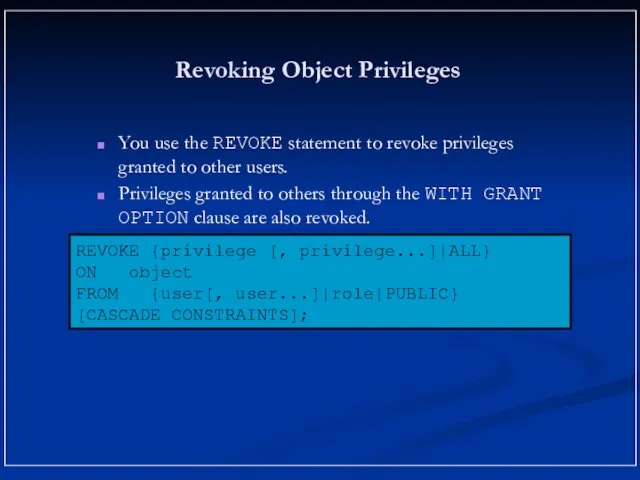
- 17. Revoking Object Privileges You use the REVOKE statement to revoke privileges granted to other users. Privileges
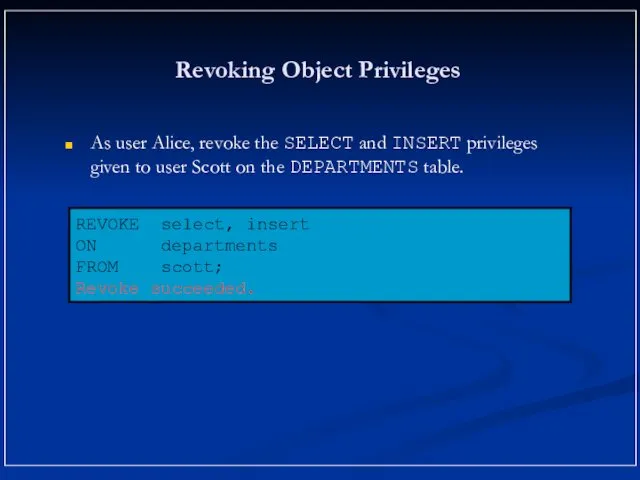
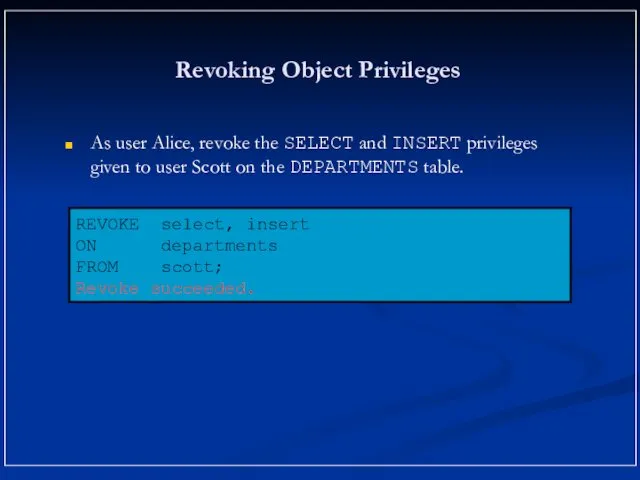
- 18. Revoking Object Privileges As user Alice, revoke the SELECT and INSERT privileges given to user Scott
- 19. Revoking Object Privileges As user Alice, revoke the SELECT and INSERT privileges given to user Scott
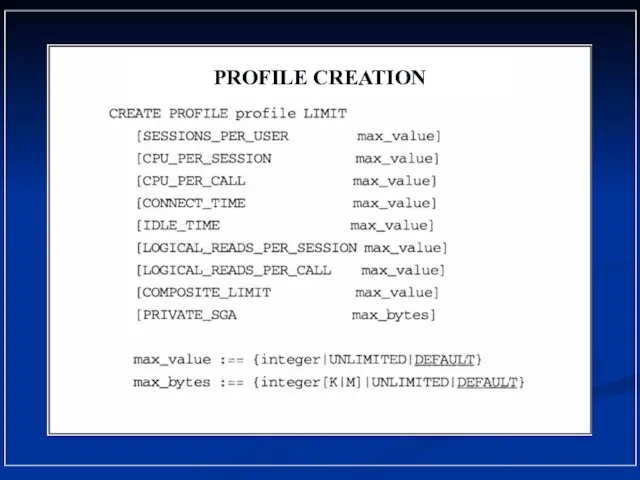
- 20. PROFILE CREATION
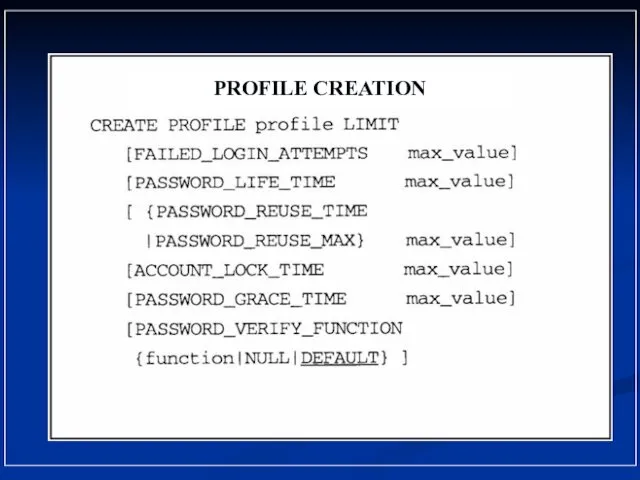
- 21. PROFILE CREATION
- 22. SQL Server Access Control
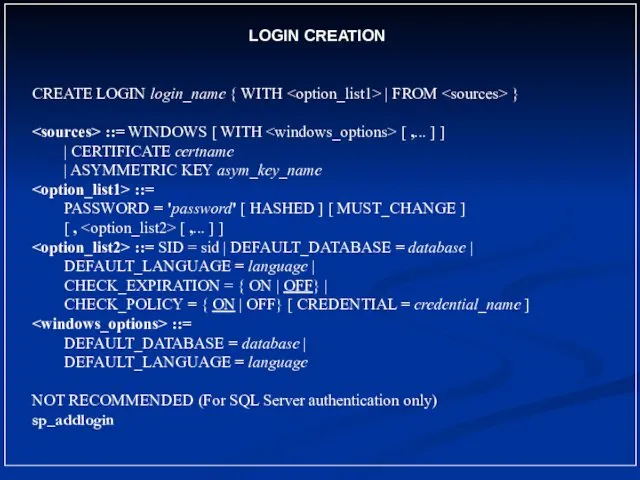
- 23. LOGIN CREATION CREATE LOGIN login_name { WITH | FROM } ::= WINDOWS [ WITH [ ,...
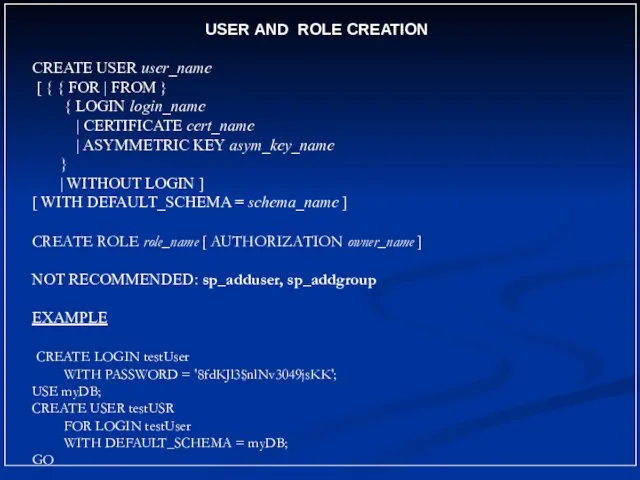
- 24. USER AND ROLE CREATION CREATE USER user_name [ { { FOR | FROM } { LOGIN
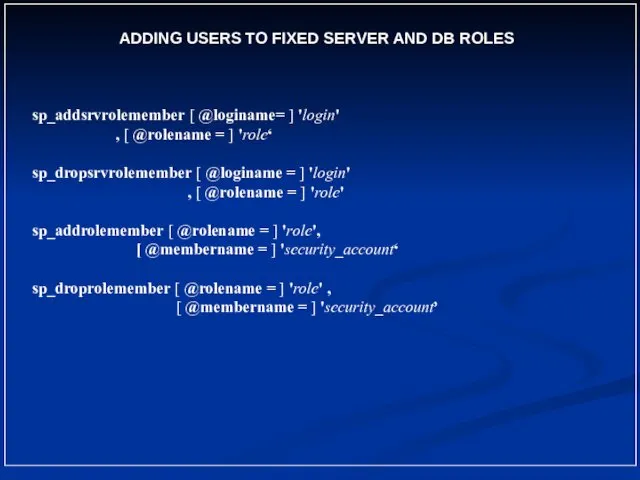
- 25. ADDING USERS TO FIXED SERVER AND DB ROLES sp_addsrvrolemember [ @loginame= ] 'login' , [ @rolename
- 26. PRIVELEGES GRANT SYMPLIFIED SYNTAX GRANT { ALL [ PRIVILEGES ] } permission [ ( column [
- 27. PRIVELEGES REVOKE SYMPLIFIED SYNTAX REVOKE [ GRANT OPTION FOR ] { [ ALL [ PRIVILEGES ]
- 28. PRIVELEGES DENY SYMPLIFIED SYNTAX DENY { ALL [ PRIVILEGES ] } | permission [ ( column
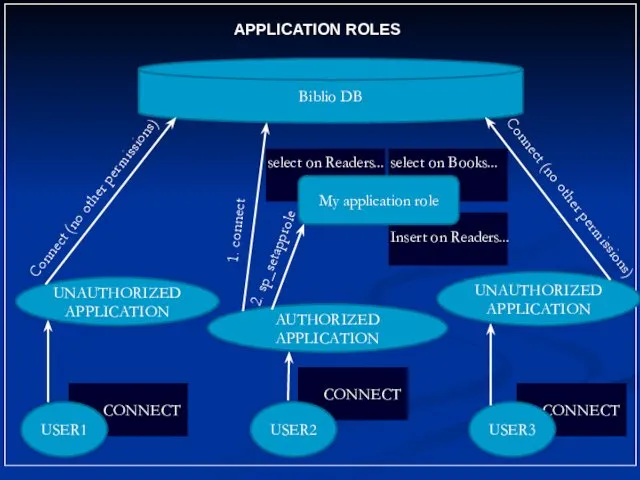
- 29. CONNECT APPLICATION ROLES CONNECT USER1 USER2 CONNECT USER3 AUTHORIZED APPLICATION UNAUTHORIZED APPLICATION UNAUTHORIZED APPLICATION Biblio DB
- 30. USING APPLICATIONS ROLES CREATING APPLICATION ROLE CREATE APPLICATION ROLE application_role_name WITH PASSWORD = 'password' [ ,
- 32. Скачать презентацию





![PRIVELEGES GRANT SYMPLIFIED SYNTAX GRANT { ALL [ PRIVILEGES ]](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/6336/slide-25.jpg)
![PRIVELEGES REVOKE SYMPLIFIED SYNTAX REVOKE [ GRANT OPTION FOR ]](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/6336/slide-26.jpg)
![PRIVELEGES DENY SYMPLIFIED SYNTAX DENY { ALL [ PRIVILEGES ]](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/6336/slide-27.jpg)

 Основы защиты информации. Информационная безопасность
Основы защиты информации. Информационная безопасность Ethernet. Arhitectura originala Ethernet
Ethernet. Arhitectura originala Ethernet Microsoft word-бұл құжаттарды құру, қарап шығу, өзгерту және басып шығару үшін арналған Microsoft Office
Microsoft word-бұл құжаттарды құру, қарап шығу, өзгерту және басып шығару үшін арналған Microsoft Office Информатика и информация
Информатика и информация Процессы и потоки
Процессы и потоки Язык SQL (DML)
Язык SQL (DML) Своя игра. Лабиринт информации
Своя игра. Лабиринт информации Типы, переменные, управляющие инструкции. (Тема 2.1)
Типы, переменные, управляющие инструкции. (Тема 2.1) Мультимедиа технологии. Технологии виртуальной реальности
Мультимедиа технологии. Технологии виртуальной реальности Знакомство с библиотекой
Знакомство с библиотекой Dota 2. Мир моиx увлечений
Dota 2. Мир моиx увлечений Моделирование. Модели и оригиналы
Моделирование. Модели и оригиналы Разработка КИМ с помощью специализированной онлайн-платформы LearningApps.org., для оценки предметных результатов
Разработка КИМ с помощью специализированной онлайн-платформы LearningApps.org., для оценки предметных результатов Заполнение электронной аттестационной формы (ЭАФ) для оцениваемого
Заполнение электронной аттестационной формы (ЭАФ) для оцениваемого Информация, ее измерение и представление в компьютере
Информация, ее измерение и представление в компьютере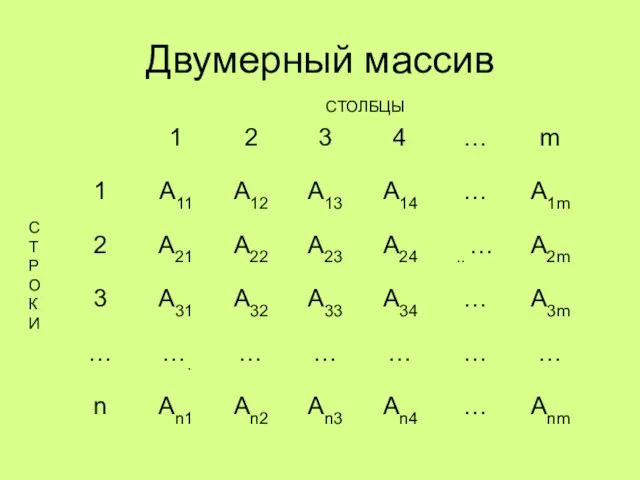 Двумерный массив
Двумерный массив Проект автоматизированной информационной системы управления муниципальных закупок города Симферополя
Проект автоматизированной информационной системы управления муниципальных закупок города Симферополя Основы языка HTML
Основы языка HTML Основные понятия и особенности объектно-ориентированного программирования
Основные понятия и особенности объектно-ориентированного программирования Анализ алгоритма, содержащего цикл и ветвление. Решение 20 задачи ЕГЭ
Анализ алгоритма, содержащего цикл и ветвление. Решение 20 задачи ЕГЭ Метод Гомори решения задач ЦЛП. Лекция 8
Метод Гомори решения задач ЦЛП. Лекция 8 Предмет и задачи информатики. Обзор технического и программного обеспечения ЭВМ
Предмет и задачи информатики. Обзор технического и программного обеспечения ЭВМ C++ Network Programming Systematic Reuse with ACE & Frameworks
C++ Network Programming Systematic Reuse with ACE & Frameworks Работа с Power Point
Работа с Power Point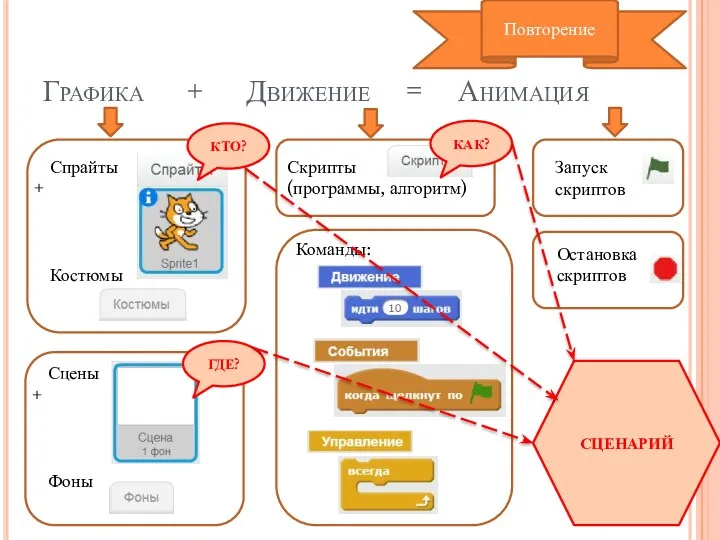 Сообщество Scratch
Сообщество Scratch Опыт и перспективы работы педагогов дополнительного образования в дистанционном формате
Опыт и перспективы работы педагогов дополнительного образования в дистанционном формате Программирование задач 1 части ЕГЭ
Программирование задач 1 части ЕГЭ Модельдер және оның тұрлері
Модельдер және оның тұрлері