Содержание
- 2. * About me bee13oy of CloverSec Labs Security Vulnerabilities Researcher, interested in: Microsoft Windows Kernel Microsoft
- 3. * Agenda Attacking Antivirus Software Finding Antivirus Kernel Vulnerabilities Exploiting Kernel Vulnerabilities Conclusion
- 4. * Agenda Attacking Antivirus Software Finding Antivirus Kernel Vulnerabilities Exploiting Kernel Vulnerabilities Conclusion
- 5. Motivation Reason for choosing AV Widely Used Typical and Challenging Choose my first target “Avast Free
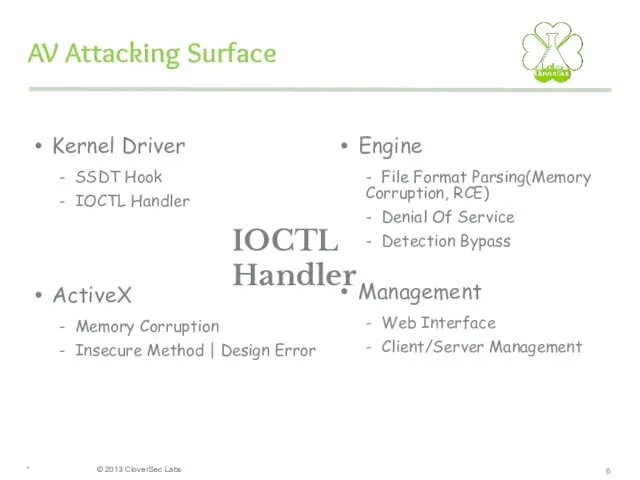
- 6. AV Attacking Surface Kernel Driver - SSDT Hook - IOCTL Handler ActiveX - Memory Corruption -
- 7. * AV Kernel Attacking Surface DeviceIoControl What We Care Mostly hDevice dwIoControlCode lpInBuffer & nInBufferSize
- 8. * Agenda Attacking Antivirus Software Finding Antivirus Kernel Vulnerabilities Exploiting Kernel Vulnerabilities Conclusion
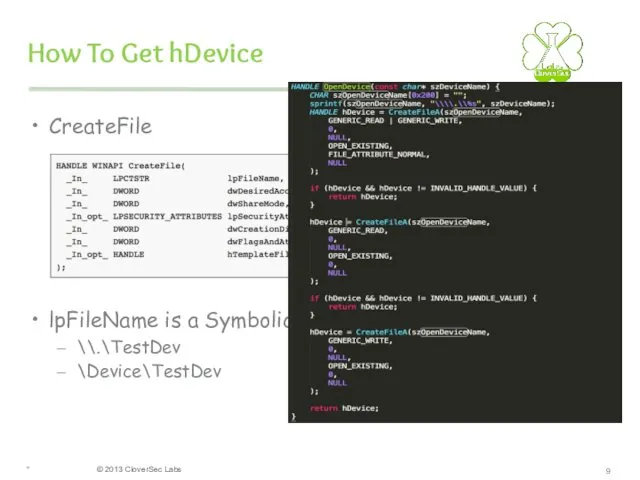
- 9. * How To Get hDevice CreateFile lpFileName is a SymbolicLink Device Name \\.\TestDev \Device\TestDev
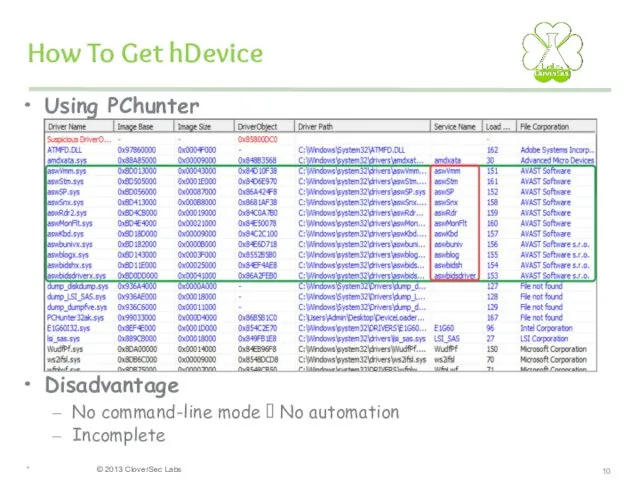
- 10. How To Get hDevice Using PChunter Disadvantage No command-line mode ? No automation Incomplete *
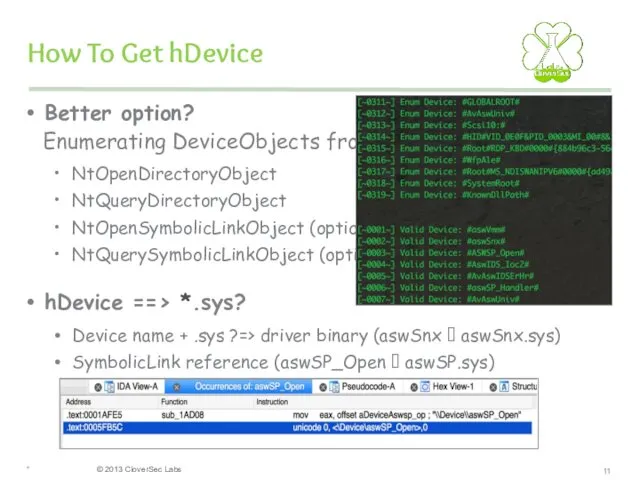
- 11. How To Get hDevice Better option? Enumerating DeviceObjects from user mode: NtOpenDirectoryObject NtQueryDirectoryObject NtOpenSymbolicLinkObject (optional) NtQuerySymbolicLinkObject
- 12. How To Get dwIoControlCode But… No Source code No Symbols High complexity We have… IDA Pro
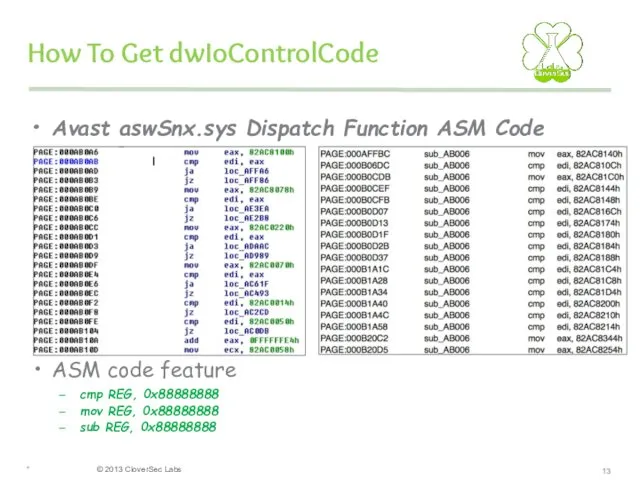
- 13. How To Get dwIoControlCode Avast aswSnx.sys Dispatch Function ASM Code ASM code feature cmp REG, 0x88888888
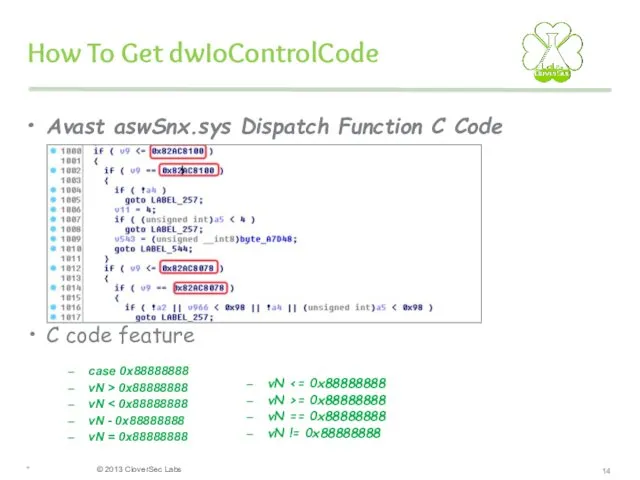
- 14. How To Get dwIoControlCode Avast aswSnx.sys Dispatch Function C Code C code feature * case 0x88888888
- 15. How To Get dwIoControlCode C++ std::regex to match ASM code feature C++ std::regex to match C
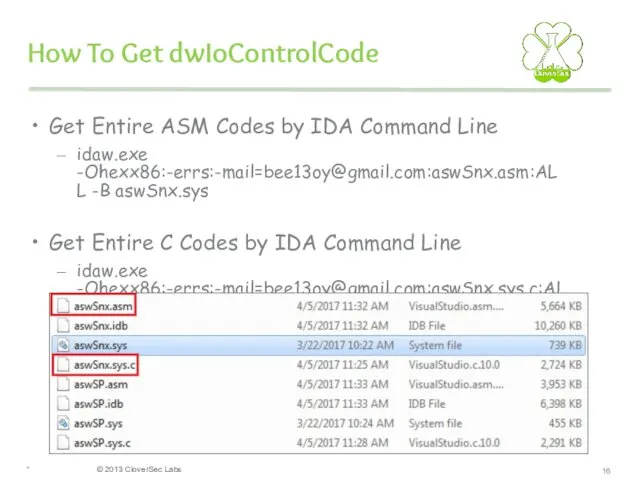
- 16. How To Get dwIoControlCode Get Entire ASM Codes by IDA Command Line idaw.exe -Ohexx86:-errs:-mail=bee13oy@gmail.com:aswSnx.asm:ALL -B aswSnx.sys
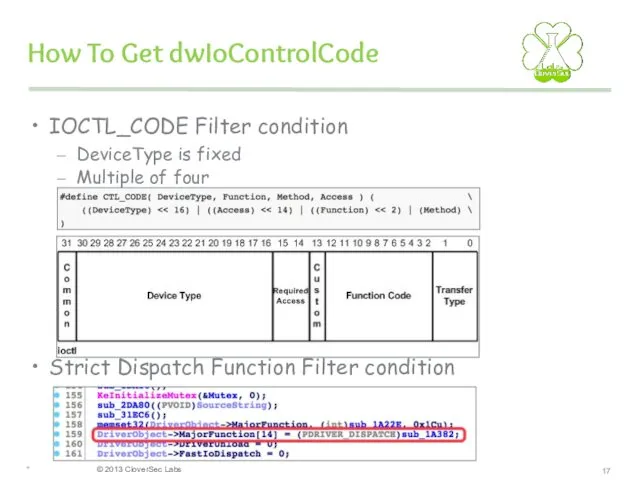
- 17. How To Get dwIoControlCode IOCTL_CODE Filter condition DeviceType is fixed Multiple of four Strict Dispatch Function
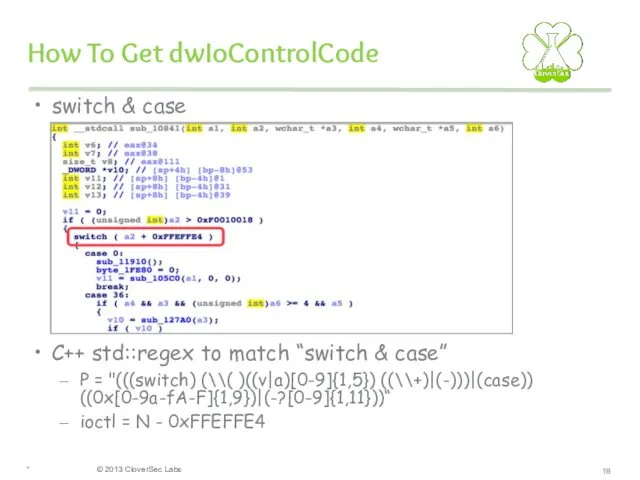
- 18. How To Get dwIoControlCode switch & case C++ std::regex to match “switch & case” P =
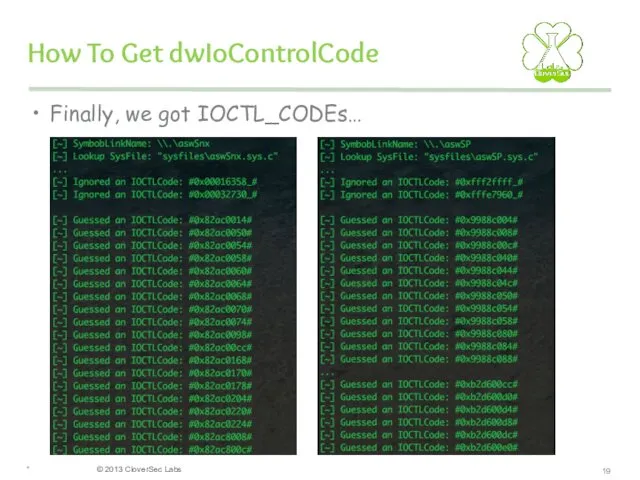
- 19. How To Get dwIoControlCode Finally, we got IOCTL_CODEs… *
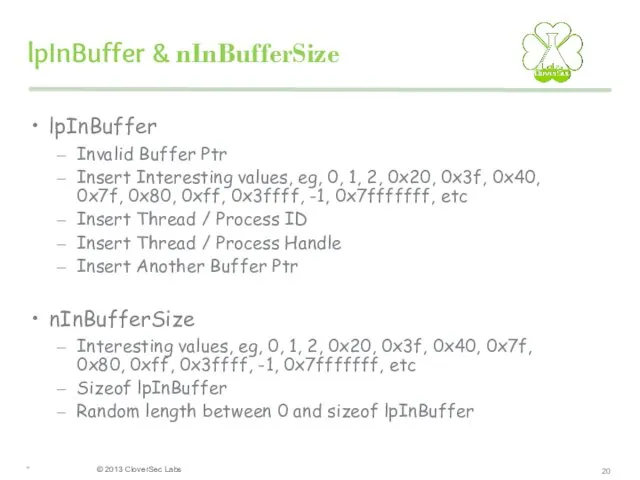
- 20. lpInBuffer & nInBufferSize lpInBuffer Invalid Buffer Ptr Insert Interesting values, eg, 0, 1, 2, 0x20, 0x3f,
- 21. Make it together *
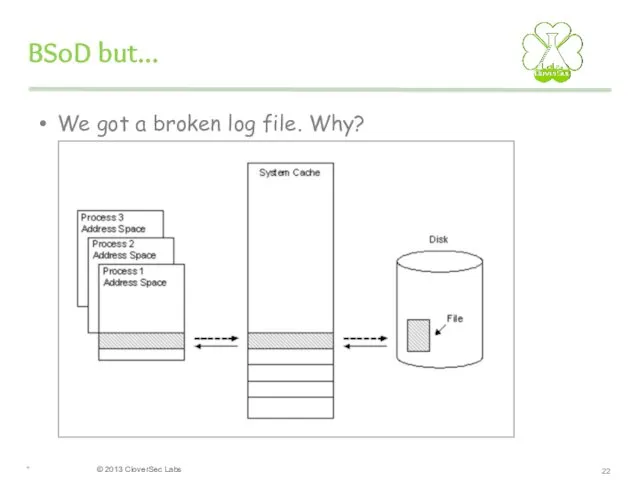
- 22. BSoD but... We got a broken log file. Why? *
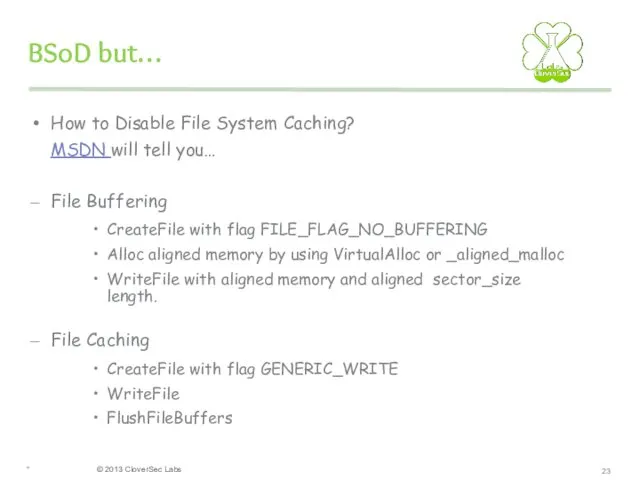
- 23. BSoD but… How to Disable File System Caching? MSDN will tell you… File Buffering CreateFile with
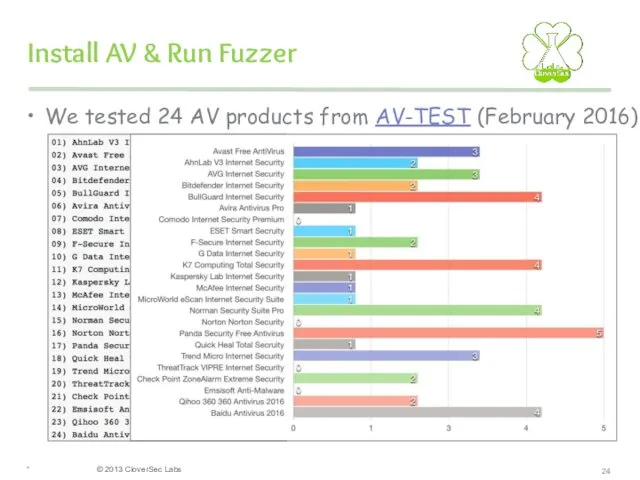
- 24. Install AV & Run Fuzzer We tested 24 AV products from AV-TEST (February 2016) *
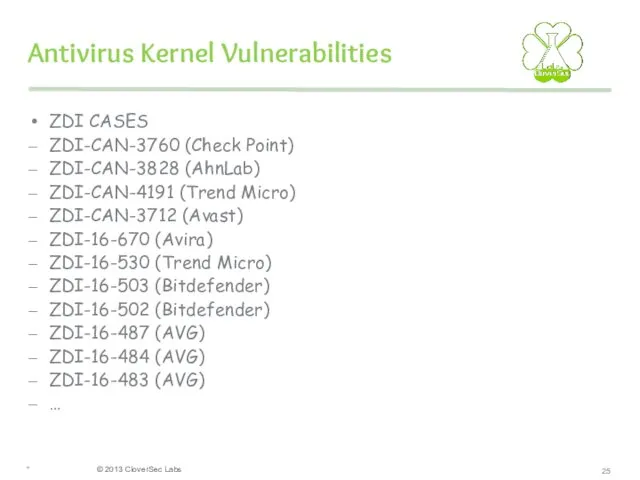
- 25. Antivirus Kernel Vulnerabilities ZDI CASES ZDI-CAN-3760 (Check Point) ZDI-CAN-3828 (AhnLab) ZDI-CAN-4191 (Trend Micro) ZDI-CAN-3712 (Avast) ZDI-16-670
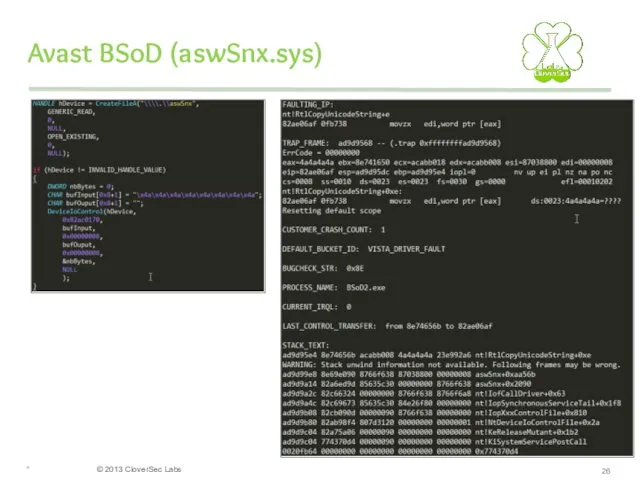
- 26. Avast BSoD (aswSnx.sys) *
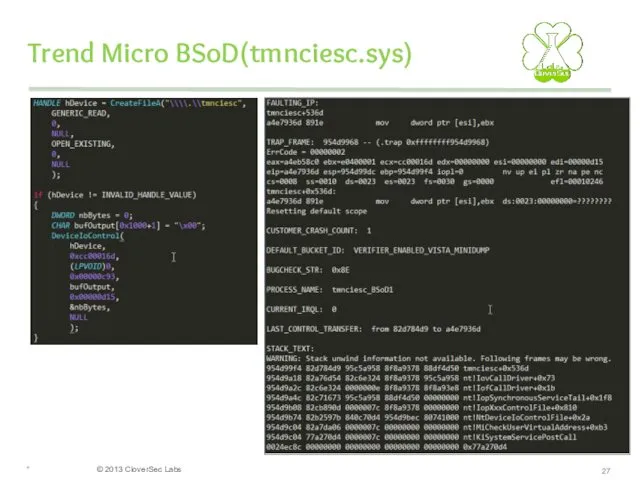
- 27. Trend Micro BSoD(tmnciesc.sys) *
- 28. * Agenda Attacking Antivirus Software Finding Antivirus Kernel Vulnerabilities Exploiting Kernel Vulnerabilities Conclusion
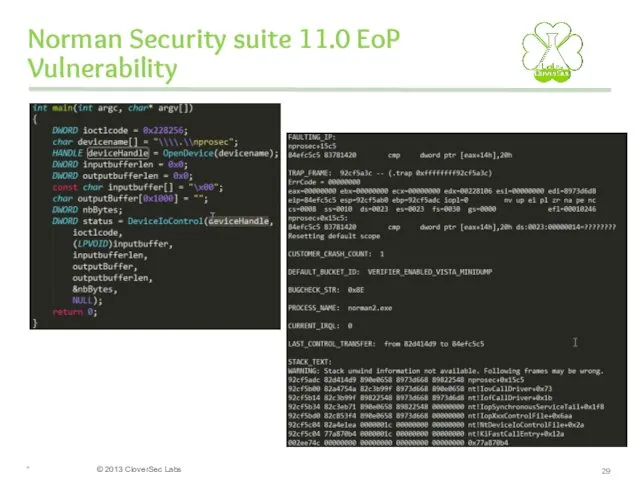
- 29. Norman Security suite 11.0 EoP Vulnerability *
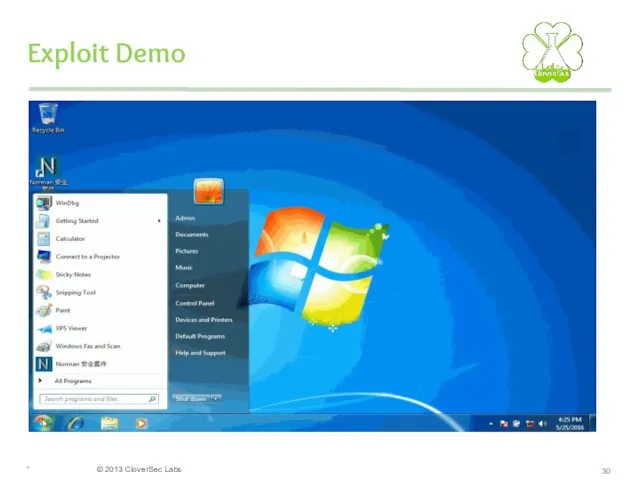
- 30. Exploit Demo *
- 31. * Agenda Attacking Antivirus Software Finding Antivirus Kernel Vulnerabilities Exploiting Kernel Vulnerabilities Conclusion
- 32. Conclusion Recommendations for AV Companies Audit your drivers: source code reviews & fuzzing Don’t trust the
- 34. Скачать презентацию










 Выбор конфигурации компьютера
Выбор конфигурации компьютера Психологические особенности детей подросткового возраста
Психологические особенности детей подросткового возраста Пожарная безопасность
Пожарная безопасность Творчий проект Переборні задачі Паскаль
Творчий проект Переборні задачі Паскаль Изоляторы
Изоляторы С 8 марта поздравляем
С 8 марта поздравляем Лазерные технологии в амбулаторной оториноларингологии
Лазерные технологии в амбулаторной оториноларингологии Кітап оқуға баулу
Кітап оқуға баулу Исследование функции на монотонность и экстремумы
Исследование функции на монотонность и экстремумы Імпресіонізм
Імпресіонізм Фотоальбом группы Весёлые зайчата
Фотоальбом группы Весёлые зайчата кто нас защищает_ ПОЛИЦИЯ
кто нас защищает_ ПОЛИЦИЯ ПрезентацияНарушение прав человека
ПрезентацияНарушение прав человека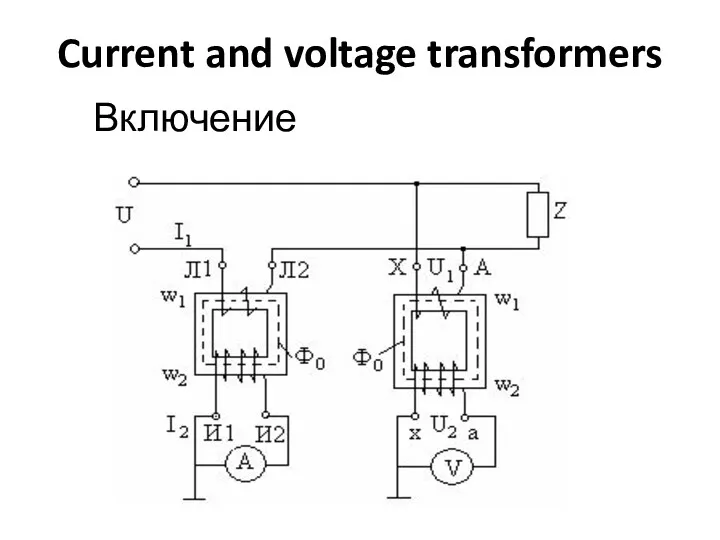 Current and voltage transformers
Current and voltage transformers Объёмы прямоугольного параллелепипеда и куба
Объёмы прямоугольного параллелепипеда и куба Знакомимся с великими пирамидами
Знакомимся с великими пирамидами Создание кроссворда средствами Microsoft Word
Создание кроссворда средствами Microsoft Word Патогенез себореи (акне)
Патогенез себореи (акне) Приемы и техники массажа. Движение
Приемы и техники массажа. Движение Даниил Гранин
Даниил Гранин Семь законов обучения. То что нужно знать учителю о своем служении
Семь законов обучения. То что нужно знать учителю о своем служении Растениеводство. Кормовые однолетние и многолетние культуры
Растениеводство. Кормовые однолетние и многолетние культуры Чрезвычайные ситуации природного и техногенного характера. Причины и возможные последствия их возникновения
Чрезвычайные ситуации природного и техногенного характера. Причины и возможные последствия их возникновения Агропромышленный комплекс России
Агропромышленный комплекс России Первое родительское собрание в 1 классе
Первое родительское собрание в 1 классе Внешний вид курильщика
Внешний вид курильщика Мостай Кәрим Урманда, 3 класс, дәрес планы
Мостай Кәрим Урманда, 3 класс, дәрес планы Условные знаки в спортивном ориентировании
Условные знаки в спортивном ориентировании