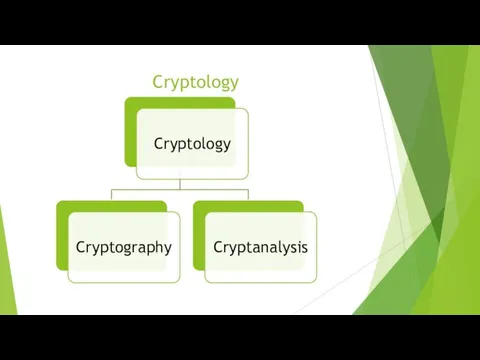
Слайд 2
Слайд 3
Cryptography and Cryptanalysis
Cryptography is the art and science of making a
cryptosystem that is capable of providing information security.
The art and science of breaking the cipher text is known as cryptanalysis.
Слайд 4

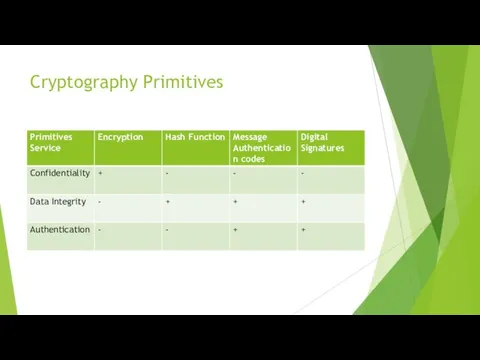
Cryptography Primitives
Encryption
Hash functions
Message Authentication codes (MAC)
Digital Signatures
Слайд 5
Слайд 6
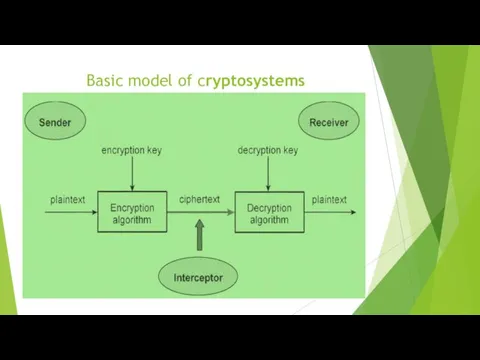
Basic model of cryptosystems
Слайд 7

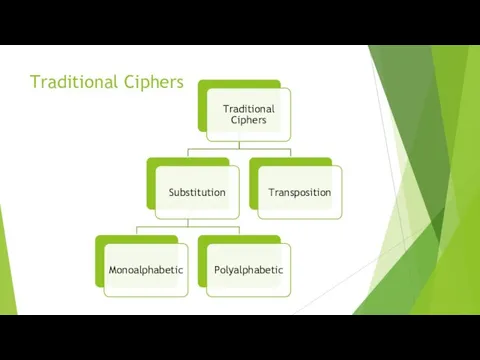
Types of Cryptosystems
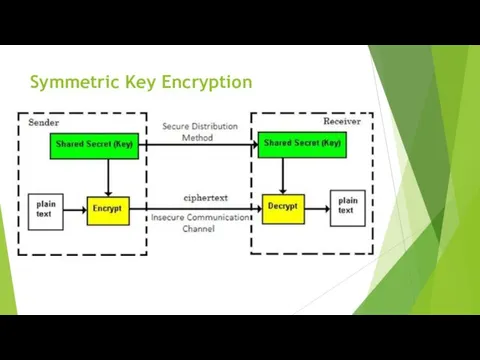
Symmetric Key Encryption
Asymmetric Key Encryption
The main difference between these
cryptosystems is the relationship between the encryption and the decryption key.
Слайд 8

Symmetric Key Encryption
Advanced Encryption Standard (AES)
Digital Encryption Standard (DES)
Triple-DES (3DES)
IDEA
BLOWFISH
Слайд 9
Слайд 10
Слайд 11
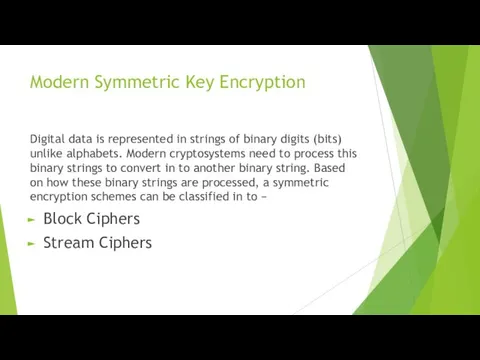
Modern Symmetric Key Encryption
Digital data is represented in strings of binary
digits (bits) unlike alphabets. Modern cryptosystems need to process this binary strings to convert in to another binary string. Based on how these binary strings are processed, a symmetric encryption schemes can be classified in to −
Block Ciphers
Stream Ciphers
Слайд 12

Block Cipher Schemes
Digital Encryption Standard (DES) − The popular block cipher
of the 1990s. It is now considered as a ‘broken’ block cipher, due primarily to its small key size.
Triple DES − It is a variant scheme based on repeated DES applications. It is still a respected block ciphers but inefficient compared to the new faster block ciphers available.
Advanced Encryption Standard (AES) − It is a relatively new block cipher based on the encryption algorithm Rijndael that won the AES design competition.
IDEA − It is a sufficiently strong block cipher with a block size of 64 and a key size of 128 bits. A number of applications use IDEA encryption, including early versions of Pretty Good Privacy (PGP) protocol. The use of IDEA scheme has a restricted adoption due to patent issues.
Twofish − This scheme of block cipher uses block size of 128 bits and a key of variable length. It was one of the AES finalists. It is based on the earlier block cipher Blowfish with a block size of 64 bits.
Serpent − A block cipher with a block size of 128 bits and key lengths of 128, 192, or 256 bits, which was also an AES competition finalist. It is a slower but has more secure design than other block cipher.
Слайд 13
Слайд 14
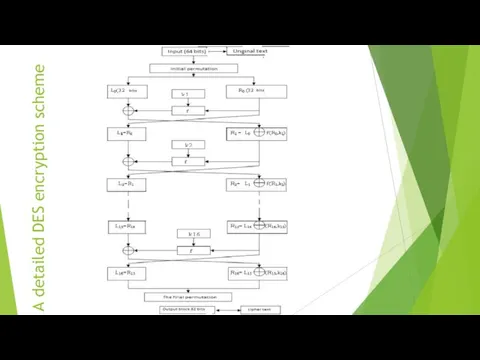
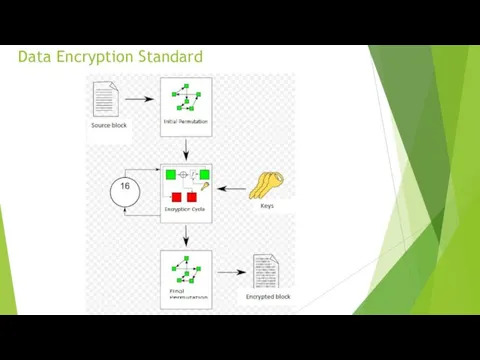
A detailed DES encryption scheme
Слайд 15
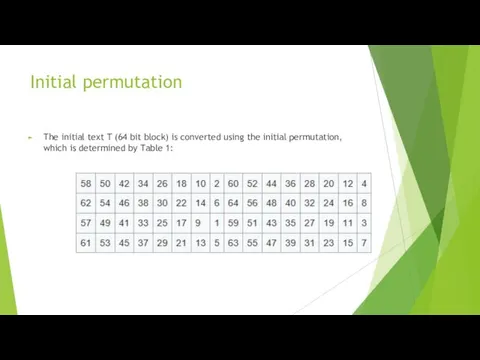
Initial permutation
The initial text T (64 bit block) is converted using
the initial permutation, which is determined by Table 1:
Слайд 16
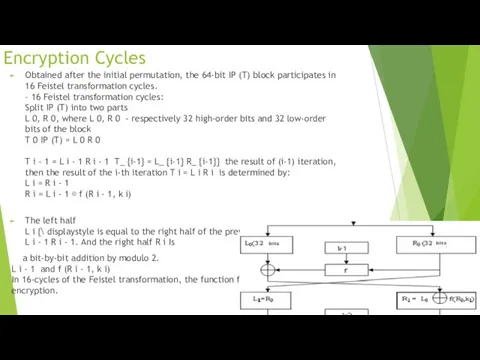
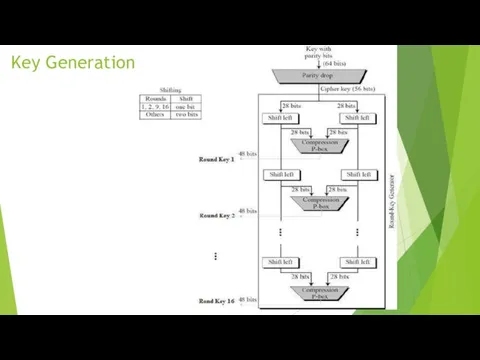
Encryption Cycles
Obtained after the initial permutation, the 64-bit IP (T) block
participates in 16 Feistel transformation cycles.
- 16 Feistel transformation cycles:
Split IP (T) into two parts
L 0, R 0, where L 0, R 0 - respectively 32 high-order bits and 32 low-order bits of the block
T 0 IP (T) = L 0 R 0
T i - 1 = L i - 1 R i - 1 T_ {i-1} = L_ {i-1} R_ {i-1}} the result of (i-1) iteration, then the result of the i-th iteration T i = L i R i is determined by:
L i = R i - 1
R i = L i - 1 ⊕ f (R i - 1, k i)
The left half
L i {\ displaystyle is equal to the right half of the previous vector
L i - 1 R i - 1. And the right half R i Is
a bit-by-bit addition by modulo 2.
L i - 1 and f (R i - 1, k i)
In 16-cycles of the Feistel transformation, the function f plays the role of encryption.
Слайд 17
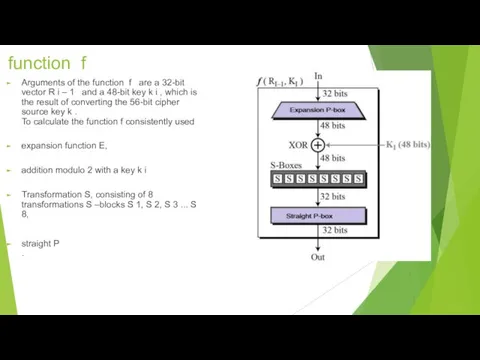
function f
Arguments of the function f are a 32-bit vector R
i – 1 and a 48-bit key k i , which is the result of converting the 56-bit cipher source key k .
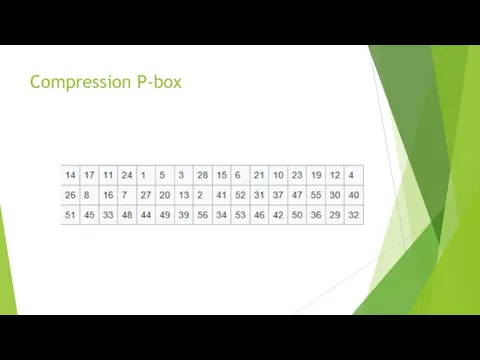
To calculate the function f consistently used
expansion function E,
addition modulo 2 with a key k i
Transformation S, consisting of 8 transformations S –blocks S 1, S 2, S 3 ... S 8,
straight P
.
Слайд 18

Слайд 19

Слайд 20

Слайд 21

Слайд 22
Слайд 23

Слайд 24

Слайд 25
Слайд 26

homework
cryptographic primitives: definitions, examples of use;
stream symmetric algorithms: definitions, examples,
purposes of use;
advantages and disadvantages of DES.

























 Выступление по теме: Организация метапредметного урока в начальной школе в условиях технологии проблемно-диалогического обучения
Выступление по теме: Организация метапредметного урока в начальной школе в условиях технологии проблемно-диалогического обучения Урок в 8 классе Реки России
Урок в 8 классе Реки России Технологии производства стали. Лекция №5-7
Технологии производства стали. Лекция №5-7 Презентация к уроку Галогены в организме человека
Презентация к уроку Галогены в организме человека Проведение промежуточной аттестации по предмету изобразительное искусство в начальных классах
Проведение промежуточной аттестации по предмету изобразительное искусство в начальных классах Особенности консультирования одаренных детей и подростков
Особенности консультирования одаренных детей и подростков Первичный туберкулез
Первичный туберкулез Димоходи та вентиляційні канали
Димоходи та вентиляційні канали Презентация по сказке В. Сутеева Петух и краски
Презентация по сказке В. Сутеева Петух и краски Тиск газів і рідин
Тиск газів і рідин Часовые пояса
Часовые пояса Обучение письму в 1 классе
Обучение письму в 1 классе Острый аппендицит и инвагинация кишечника
Острый аппендицит и инвагинация кишечника Ray the Firefly FOT Craftsmanship Report
Ray the Firefly FOT Craftsmanship Report Театральный Омск
Театральный Омск презентация учащегося по результатам проведённого исследования по теме: Метеостанция в городе Павловский Посад Московской области.
презентация учащегося по результатам проведённого исследования по теме: Метеостанция в городе Павловский Посад Московской области. Центр молодых специалистов 1С - от стажера до сотрудника фирмы
Центр молодых специалистов 1С - от стажера до сотрудника фирмы Шедеври північного Відродження
Шедеври північного Відродження Климатические пояса мира.
Климатические пояса мира. Презентация 5 класс ФГОС Планеты Солнечной системы
Презентация 5 класс ФГОС Планеты Солнечной системы Типы девиантного поведения и их особенности
Типы девиантного поведения и их особенности Основы религиозных культур и светской этики
Основы религиозных культур и светской этики Отчет о прохождении рассредоточенной практики на базе Международного союза детских общественных объединений
Отчет о прохождении рассредоточенной практики на базе Международного союза детских общественных объединений Презентация Правила пожарной безопасности в лесу
Презентация Правила пожарной безопасности в лесу Великое Княжество Тверское. 15 - 16 век
Великое Княжество Тверское. 15 - 16 век Лекция 7. Балки покрытия
Лекция 7. Балки покрытия Основи нормованої годівлі тварин
Основи нормованої годівлі тварин Эпидемии современного мира
Эпидемии современного мира