Слайд 2
Information
Information is derived from the Latin word informatio, which means information
about the state of affairs or someone's actions, a statement, or a collection of information about something. However, data cannot be equated with information. The information contains only information that reduces the inaccuracies of the cases in which we are interested.
Слайд 3

Information protection is a set of measures aimed at ensuring information
security (integrity of information, sources of access, restrictions, use of information and its resources). A system is said to be secure if it is accessible only to a limited number of users using the appropriate information and software. Scope - read, write, create, delete. In general, there are no absolutely safe systems. Here we are talking about reliable systems. The system will be reliable - if it allows a predetermined group of users to process information on the basis of software and information equipment.
Слайд 4
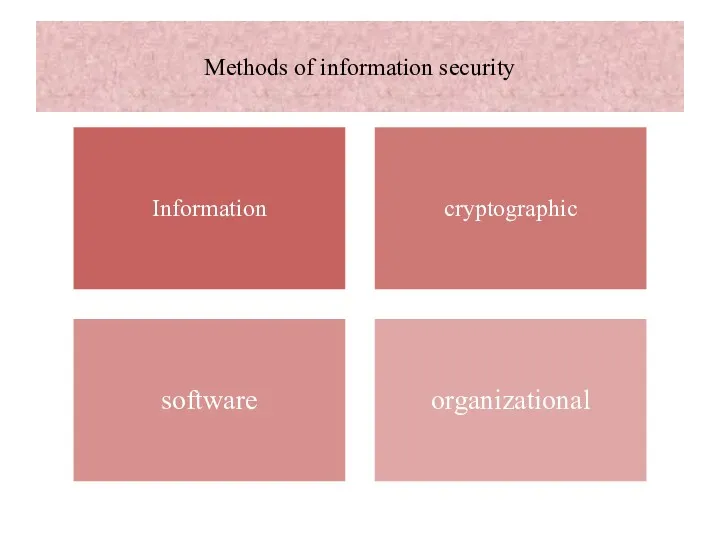
Methods of information security
Слайд 5
The use of hardware methods of protection suggests the use of
the following technical means:
1. Detector of TRD-800 category radio transmitters and tape recorders, which protects against listening and recording devices;
2. Modular numbers that form a hidden video surveillance;
3. Schemes of verification of information to ensure the accuracy of information delivery;
4. SAFE-400 fax message scramblers for sending confidential documents. Hardware methods of protection require a large expenditure of resources. Software methods recommend the removal of unauthorized use of computing algorithms and programs that restrict access. Software methods perform the following functions:
1. Identification, authentication, authorization (via Pin codes, password systems);
2. Backup and recovery procedures;
3. Active use of anti-virus programs and frequent updating of anti-virus resources; 4. Transaction processing.
Слайд 6

Classification of computer viruses
There are several ways to classify computer viruses:
1 By the environment in which the virus is spread
2 By the method of infection
3 On destructive possibilities
4 On the features of the working algorithm
Слайд 7

Malicious software (malware) is software that the developer or sender has
malicious intent. While many of the programs and files you install or download are completely harmless, some are designed to further create a hidden agenda, such as deleting files, stealing information, or getting paid. For a long time, malware has used various methods to obtain malware on as many computers as possible. In 1982, the first computer virus called Elk Cloner was discovered on a Mac. In 1986, the first computer malware known as Brain was released.
Слайд 8

Malware in the 21st century
The proliferation of exploits (programs used by
cybercriminals to exploit system vulnerabilities) led to the explosion of malware delivered to the Internet in the 2000s. Automated SQL injection (a method used to attack data-driven applications) and other types of mass websites increase deployment capabilities. Since then, the number of malware attacks has doubled or more each year.







 Як святкують новий рік у різних країнах світу
Як святкують новий рік у різних країнах світу Общие черты и особенности экономического развития Германии и США в конце 19-ого-начале 20-ого века
Общие черты и особенности экономического развития Германии и США в конце 19-ого-начале 20-ого века интеллектуальный марафон
интеллектуальный марафон Организация практики
Организация практики Осциллографы
Осциллографы Материк Евразия. Обобщение. 7 класс
Материк Евразия. Обобщение. 7 класс Древний Египет
Древний Египет Методы защиты от коррозии
Методы защиты от коррозии Вазоконстрикторы и антигипотензивные средства
Вазоконстрикторы и антигипотензивные средства Химико-технологическая система, ее состав и структура
Химико-технологическая система, ее состав и структура Экология. Общая экология. Экологическое право. Экология популяций и экосистем
Экология. Общая экология. Экологическое право. Экология популяций и экосистем Хочу всё знать. Интеллектуальная игра для дошкольников
Хочу всё знать. Интеллектуальная игра для дошкольников Презентация к методическому семинару
Презентация к методическому семинару Правонарушение. Юридическая ответственность и её виды
Правонарушение. Юридическая ответственность и её виды Сучасні програмні продукти моделювання та симуляції електронних схем
Сучасні програмні продукти моделювання та симуляції електронних схем Базовые конкурентные стратегии по Майклу Портеру
Базовые конкурентные стратегии по Майклу Портеру Разработка открытого урока, данный в ходе всероссийского конкурса- Учитель года-2014 по теме Реки.
Разработка открытого урока, данный в ходе всероссийского конкурса- Учитель года-2014 по теме Реки. Как не стать жертвой наркомании
Как не стать жертвой наркомании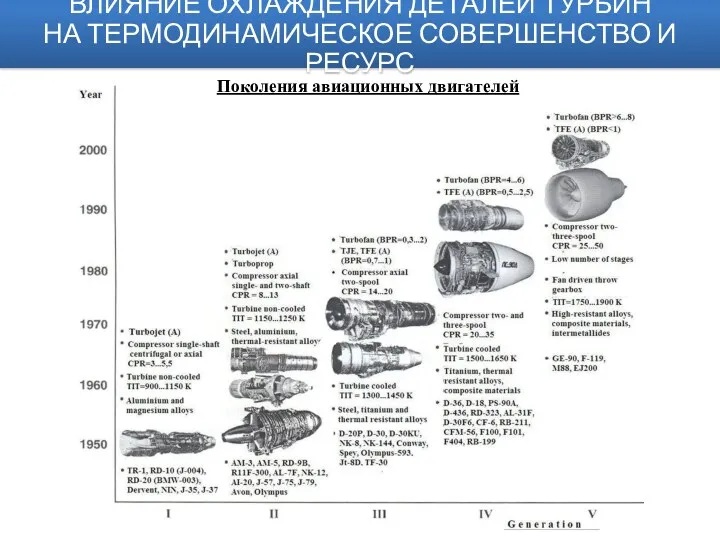 Авиационные двигатели. Влияние охлаждения деталей турбин на термодинамическое совершенство и ресурс прочности лопаток
Авиационные двигатели. Влияние охлаждения деталей турбин на термодинамическое совершенство и ресурс прочности лопаток Мембранные покрытия
Мембранные покрытия Коррекция речевых нарушений у старших дошкольников в условиях логопедического пункта в ДОУ
Коррекция речевых нарушений у старших дошкольников в условиях логопедического пункта в ДОУ Аппаратная часть компьютерной системы
Аппаратная часть компьютерной системы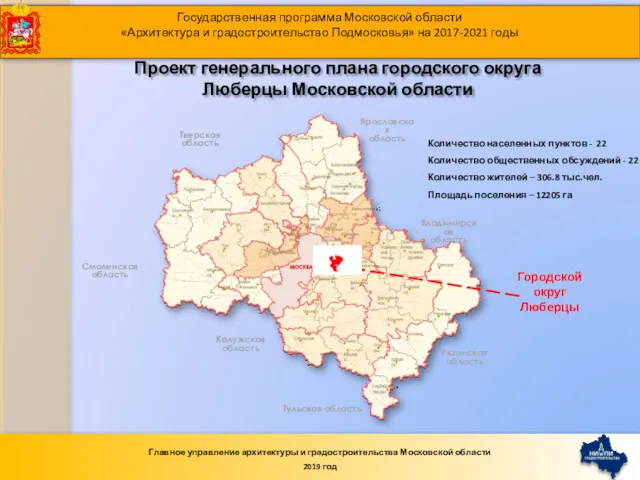 Проект генерального плана городского округа Люберцы Московской области
Проект генерального плана городского округа Люберцы Московской области Классный час Откуда берутся грязнули
Классный час Откуда берутся грязнули Винсент Ван Гог 1853-1890 (37 лет)
Винсент Ван Гог 1853-1890 (37 лет) Зимний подарок Презентация
Зимний подарок Презентация Презентация Живи, память, живи!
Презентация Живи, память, живи! Презентация Курить - здоровью вредить.
Презентация Курить - здоровью вредить.