Содержание
- 2. Introduction to Microsoft RPC Reverse engineering of Microsoft RPC services dmidl (reverse midl) fa (reverse c)
- 3. Introduction to Microsoft RPC It's 106 miles to Chicago, we've got a full tank of gas,
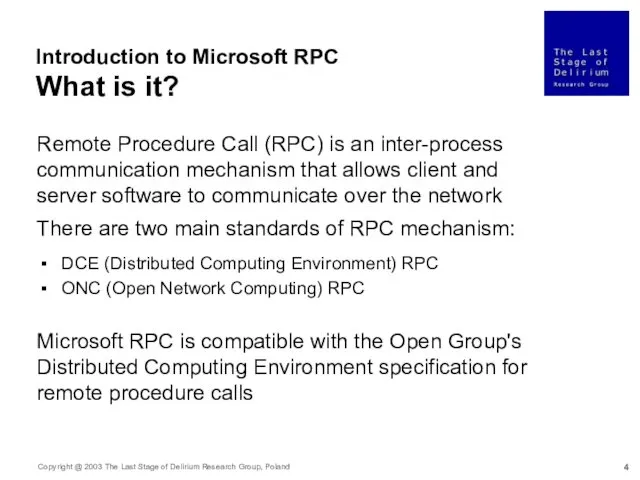
- 4. Remote Procedure Call (RPC) is an inter-process communication mechanism that allows client and server software to
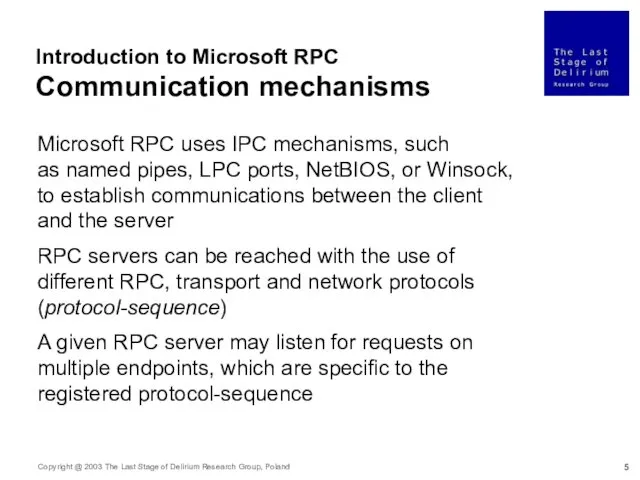
- 5. Introduction to Microsoft RPC Communication mechanisms Microsoft RPC uses IPC mechanisms, such as named pipes, LPC
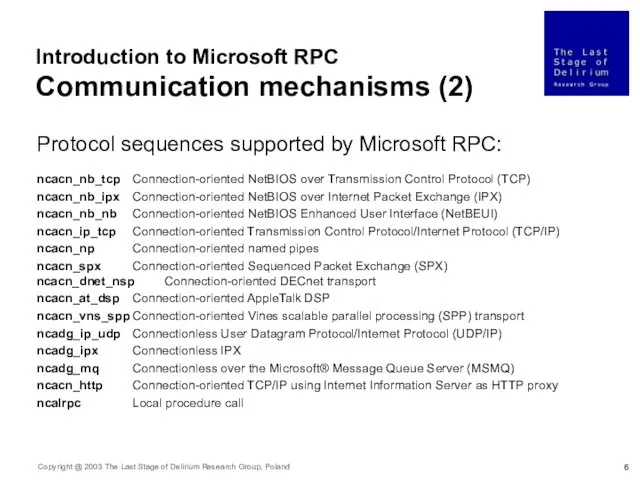
- 6. Introduction to Microsoft RPC Communication mechanisms (2) Protocol sequences supported by Microsoft RPC: ncacn_nb_tcp Connection-oriented NetBIOS
- 7. Introduction to Microsoft RPC RPC client/server architecture Specific functionality of a given RPC server is exposed
- 8. Introduction to Microsoft RPC Why it is so important ? Microsoft RPC has been a backbone
- 9. Introduction to Microsoft RPC RPC interfaces (Windows 2000) RPC interfaces that can be by default reached
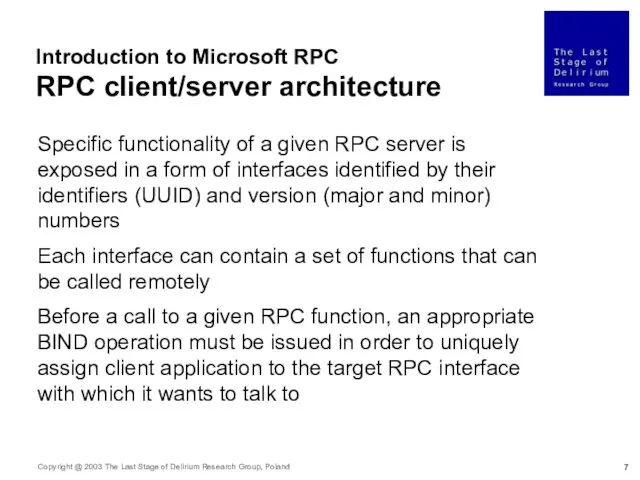
- 10. Introduction to Microsoft RPC RPC interfaces (Windows 2000) cont. RPC interfaces that can be by default
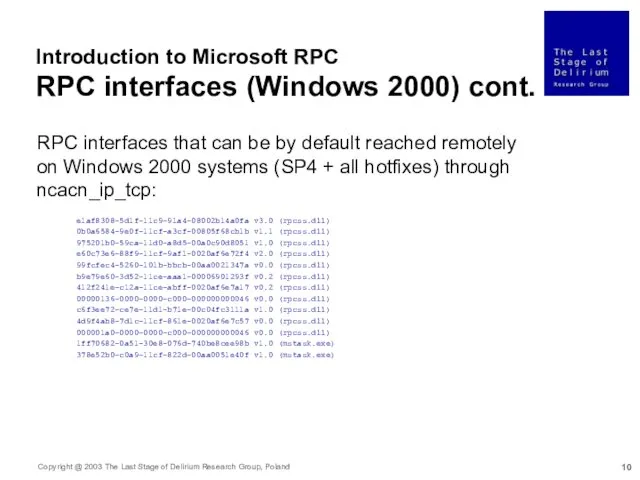
- 11. Introduction to Microsoft RPC RPC interfaces (Windows XP) RPC interfaces that can be by default reached
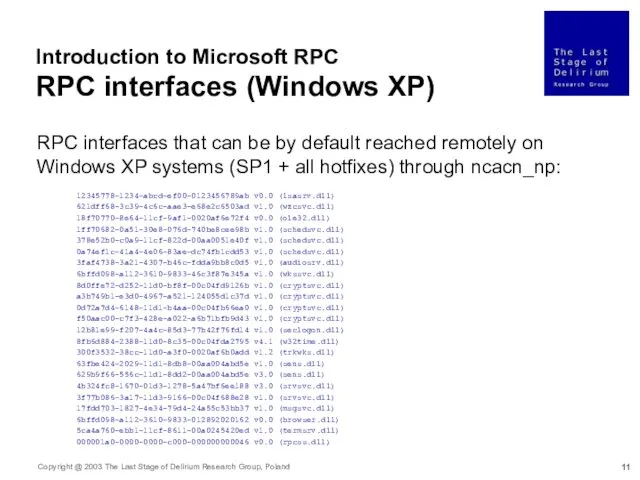
- 12. Introduction to Microsoft RPC RPC interfaces (Windows XP) cont. RPC interfaces that can be by default
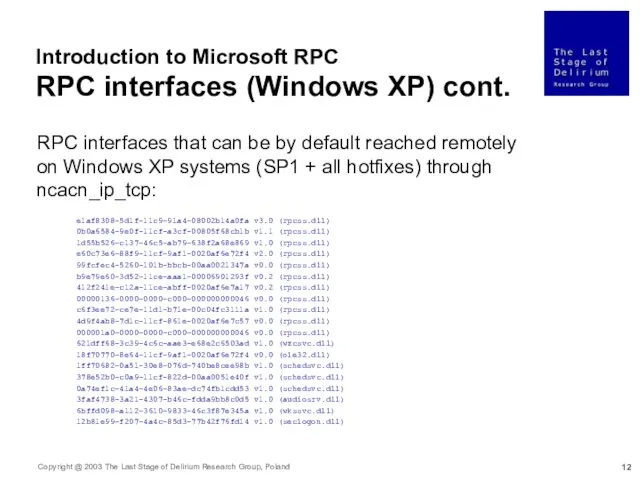
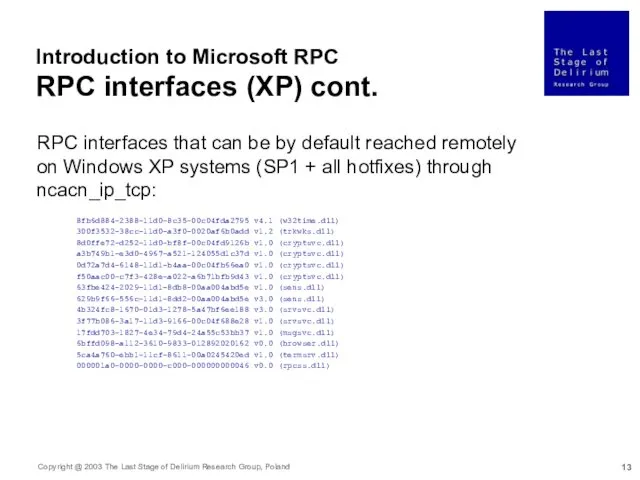
- 13. Introduction to Microsoft RPC RPC interfaces (XP) cont. RPC interfaces that can be by default reached
- 14. Introduction to Microsoft RPC Other RPC interfaces There are many more RPC interfaces in Windows 2000/XP
- 15. Introduction to Microsoft RPC Authentication issues Presented Windows interfaces can be reached from the network through
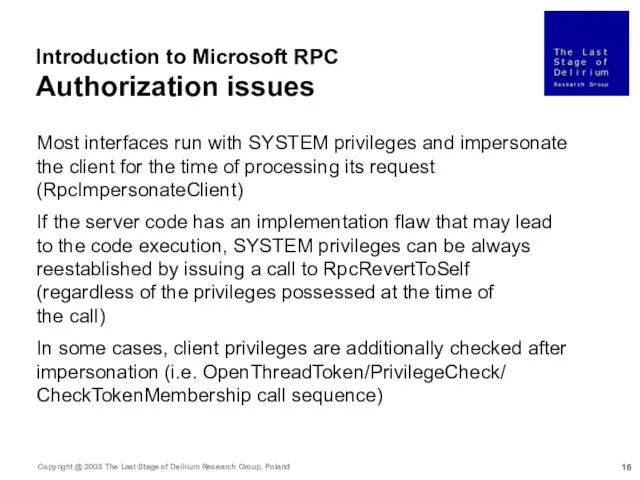
- 16. Introduction to Microsoft RPC Authorization issues Most interfaces run with SYSTEM privileges and impersonate the client
- 17. Introduction to Microsoft RPC RPC runtime security issues If there are multiple RPC interfaces registered in
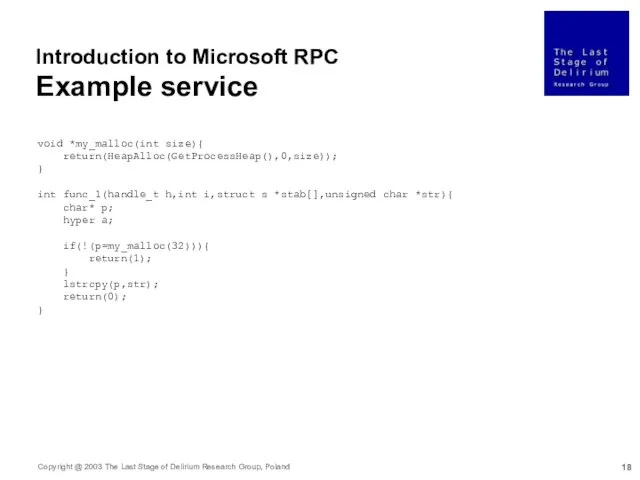
- 18. void *my_malloc(int size){ return(HeapAlloc(GetProcessHeap(),0,size)); } int func_1(handle_t h,int i,struct s *stab[],unsigned char *str){ char* p; hyper
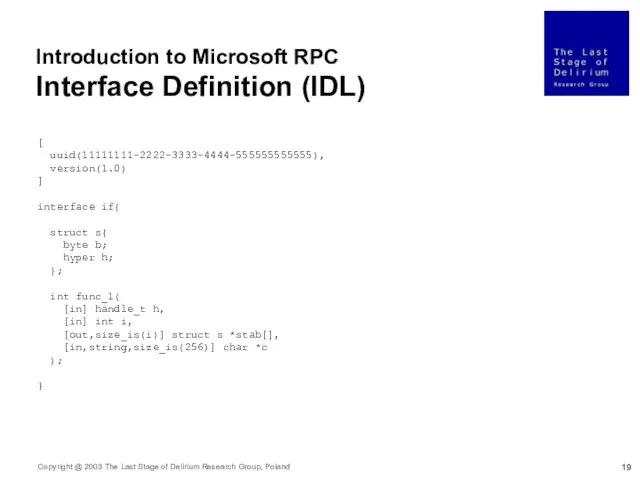
- 19. Introduction to Microsoft RPC Interface Definition (IDL) [ uuid(11111111-2222-3333-4444-555555555555), version(1.0) ] interface if{ struct s{ byte
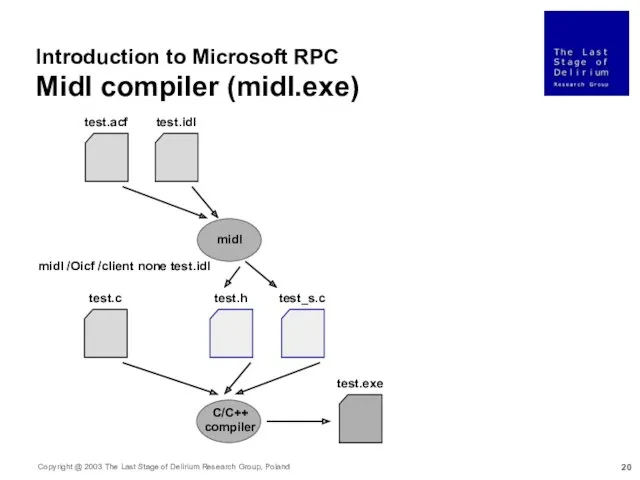
- 20. Introduction to Microsoft RPC Midl compiler (midl.exe) test.acf test.c midl midl /Oicf /client none test.idl test.idl
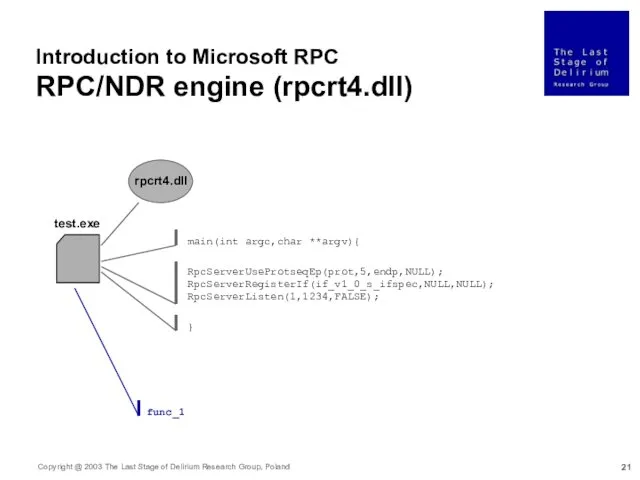
- 21. Introduction to Microsoft RPC RPC/NDR engine (rpcrt4.dll) test.exe rpcrt4.dll RpcServerUseProtseqEp(prot,5,endp,NULL); RpcServerRegisterIf(if_v1_0_s_ifspec,NULL,NULL); RpcServerListen(1,1234,FALSE); main(int argc,char **argv){ }
- 22. Reverse engineering of Microsoft RPC Basic research is when I'm doing what I don't know what
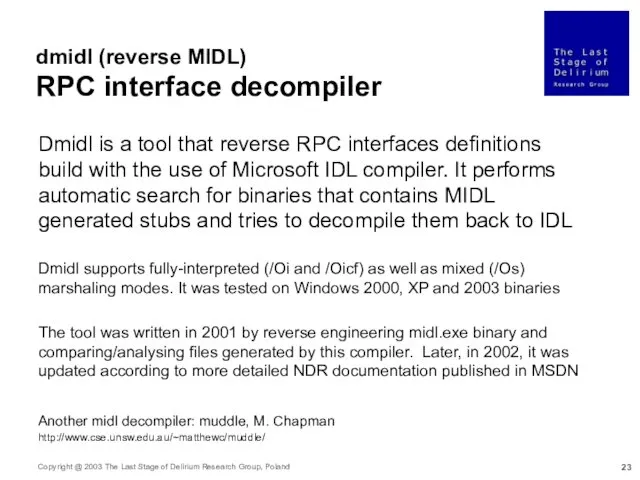
- 23. dmidl (reverse MIDL) RPC interface decompiler Dmidl is a tool that reverse RPC interfaces definitions build
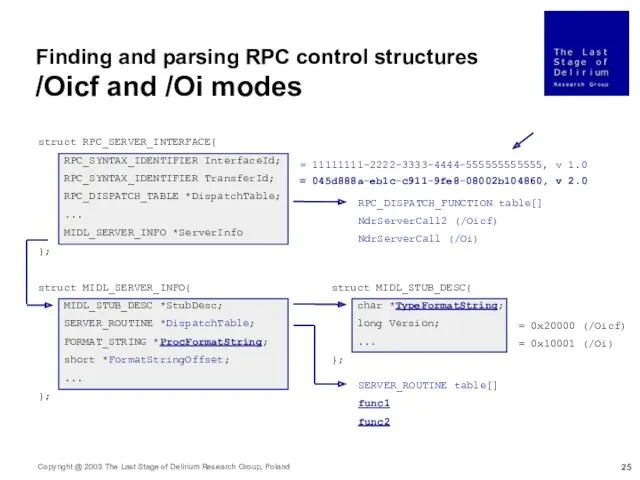
- 24. Finding and parsing RPC control structures Reversing procedure format strings Reversing type format strings Combining parameter
- 25. struct RPC_SERVER_INTERFACE{ RPC_SYNTAX_IDENTIFIER InterfaceId; RPC_SYNTAX_IDENTIFIER TransferId; RPC_DISPATCH_TABLE *DispatchTable; ... MIDL_SERVER_INFO *ServerInfo }; = 045d888a-eb1c-c911-9fe8-08002b104860, v 2.0
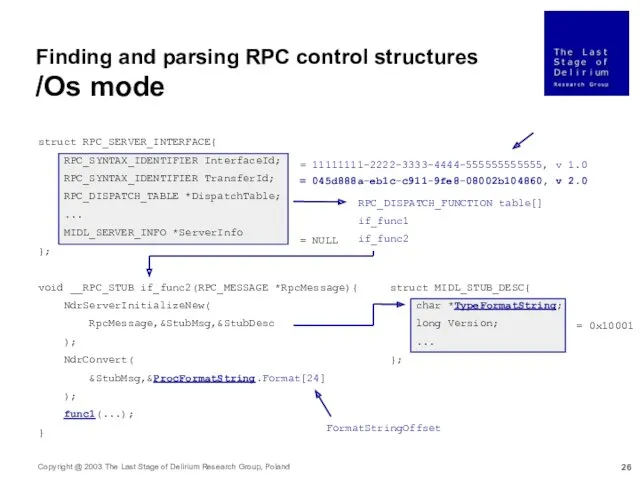
- 26. Finding and parsing RPC control structures /Os mode struct RPC_SERVER_INTERFACE{ RPC_SYNTAX_IDENTIFIER InterfaceId; RPC_SYNTAX_IDENTIFIER TransferId; RPC_DISPATCH_TABLE *DispatchTable;
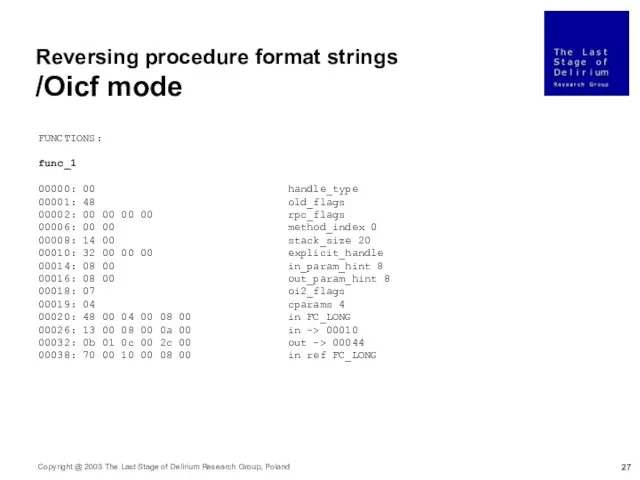
- 27. Reversing procedure format strings /Oicf mode FUNCTIONS: func_1 00000: 00 handle_type 00001: 48 old_flags 00002: 00
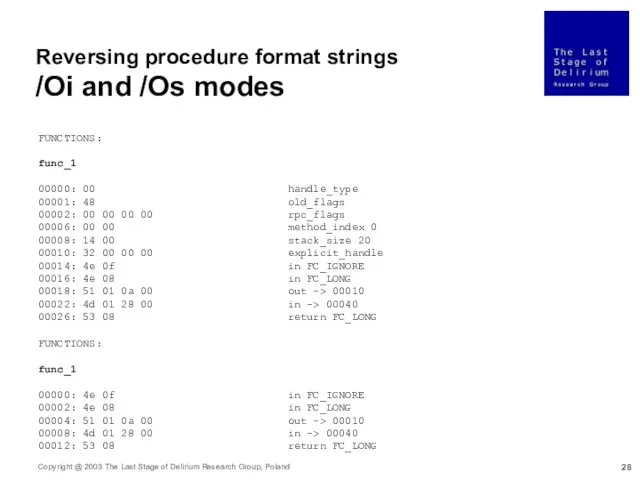
- 28. FUNCTIONS: func_1 00000: 00 handle_type 00001: 48 old_flags 00002: 00 00 00 00 rpc_flags 00006: 00
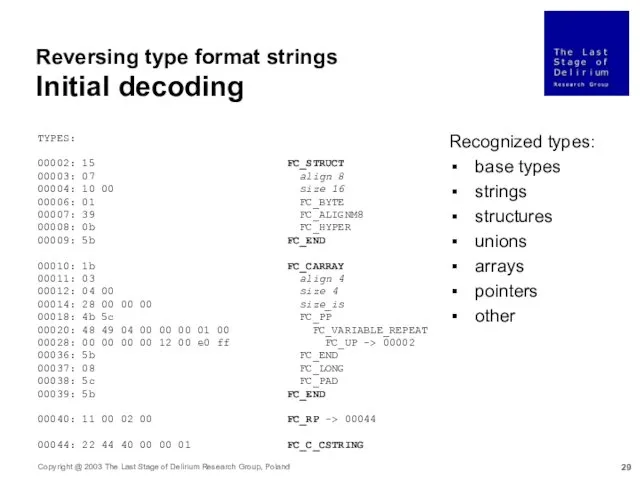
- 29. Reversing type format strings Initial decoding TYPES: 00002: 15 FC_STRUCT 00003: 07 align 8 00004: 10
- 30. Combining parameter and type information Complex types Enumerate implicit/explicit handles and contexts Follow embedded types and
- 31. [ uuid(11111111-2222-3333-4444-555555555555), version(1.0) ] interface if{ /* TYPES */ struct _2{ byte _1; hyper _2; };
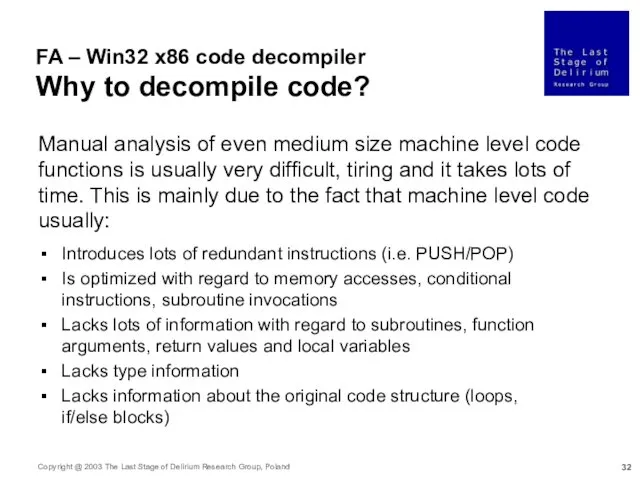
- 32. FA – Win32 x86 code decompiler Why to decompile code? Manual analysis of even medium size
- 33. FA – Win32 x86 code decompiler Why to decompile code? (2) The process of code decompilation
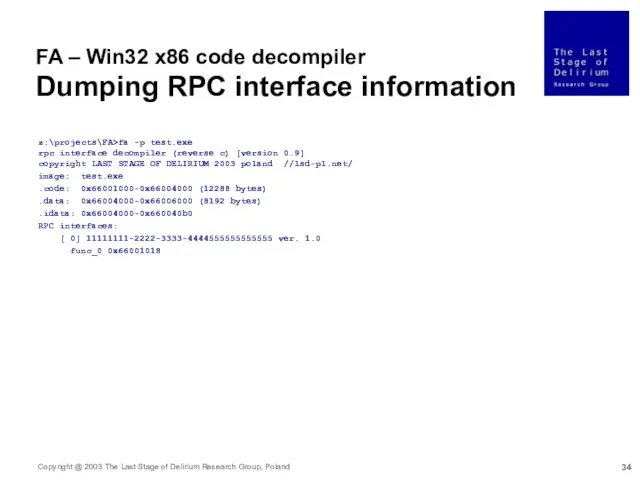
- 34. FA – Win32 x86 code decompiler Dumping RPC interface information z:\projects\FA>fa -p test.exe rpc interface decompiler
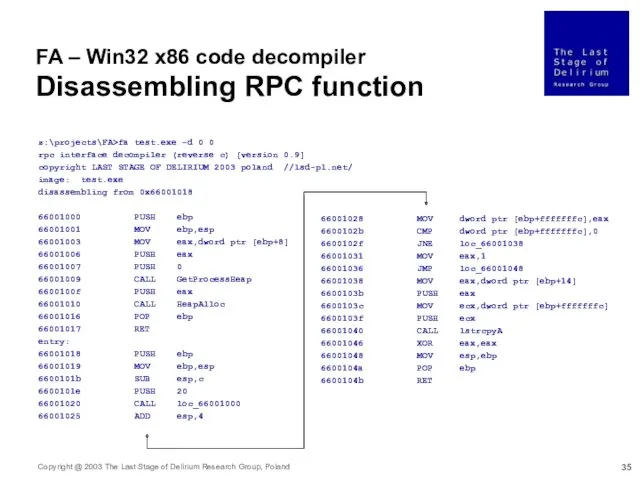
- 35. z:\projects\FA>fa test.exe –d 0 0 rpc interface decompiler (reverse c) [version 0.9] copyright LAST STAGE OF
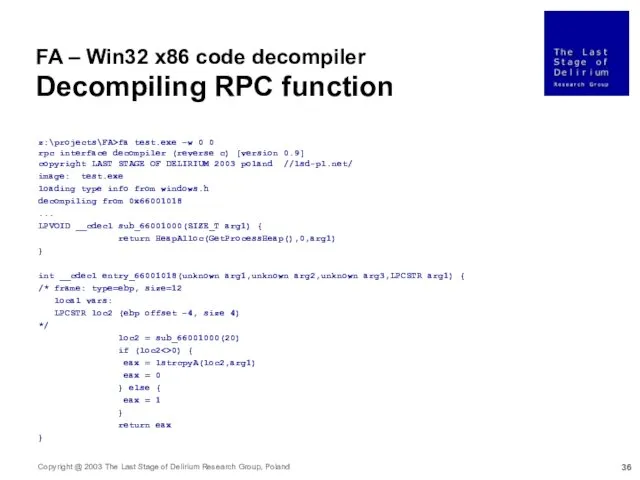
- 36. FA – Win32 x86 code decompiler Decompiling RPC function z:\projects\FA>fa test.exe –w 0 0 rpc interface
- 37. FA – Win32 x86 code decompiler Decompiler operation In general, the process of FA operation is
- 38. FA – Win32 x86 code decompiler Decompiler features Convert machine level code into a set of
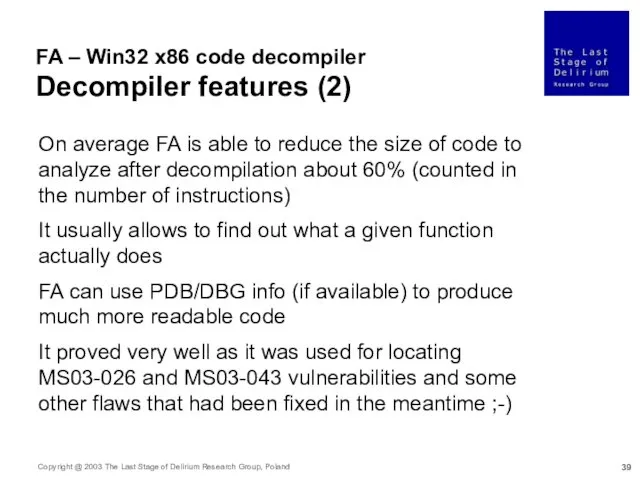
- 39. FA – Win32 x86 code decompiler Decompiler features (2) On average FA is able to reduce
- 40. Exploitation techniques for RPC vulnerabilities Part 3: If I had only known, I would have been
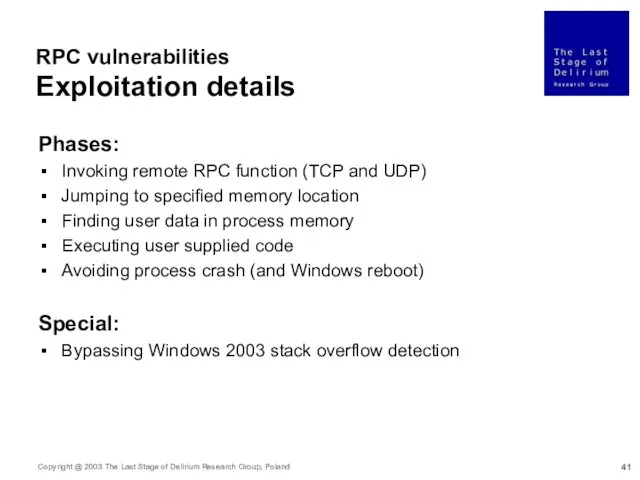
- 41. RPC vulnerabilities Exploitation details Phases: Invoking remote RPC function (TCP and UDP) Jumping to specified memory
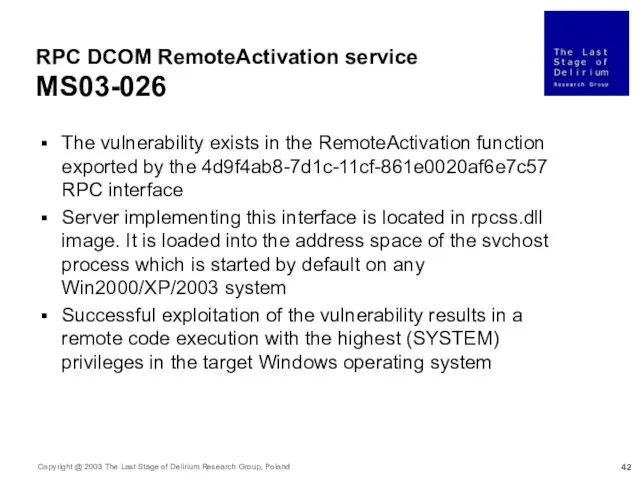
- 42. RPC DCOM RemoteActivation service MS03-026 The vulnerability exists in the RemoteActivation function exported by the 4d9f4ab8-7d1c-11cf-861e0020af6e7c57
- 43. Invoking remote RPC function (TCP) RemoteActivation() error_status_t RemoteActivation( [in] handle_t _1, [in,ref] struct _110 *_2, [out,ref]
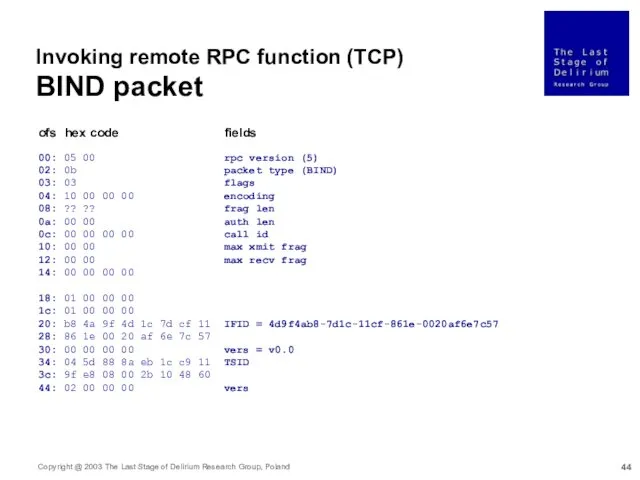
- 44. 00: 05 00 rpc version (5) 02: 0b packet type (BIND) 03: 03 flags 04: 10
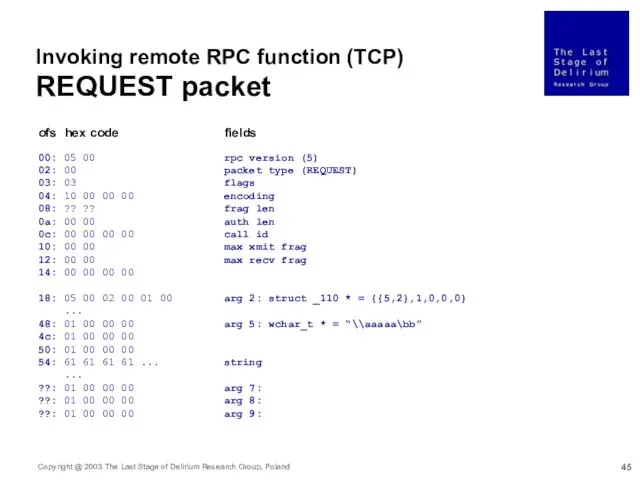
- 45. Invoking remote RPC function (TCP) REQUEST packet 00: 05 00 rpc version (5) 02: 00 packet
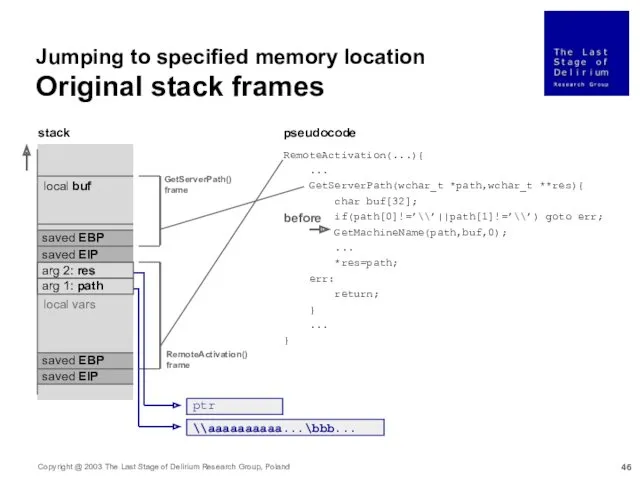
- 46. Jumping to specified memory location Original stack frames RemoteActivation(...){ ... GetServerPath(wchar_t *path,wchar_t **res){ char buf[32]; if(path[0]!=’\\’||path[1]!=’\\’)
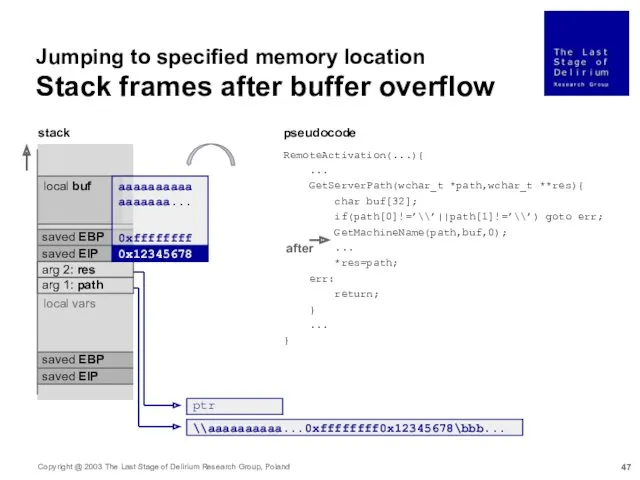
- 47. Jumping to specified memory location Stack frames after buffer overflow stack local buf saved EBP arg
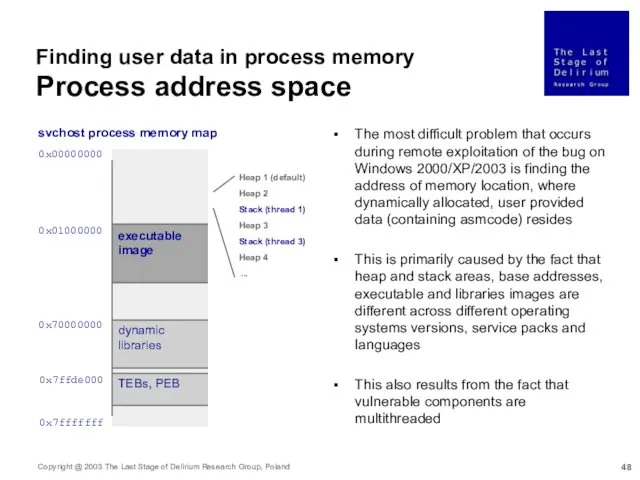
- 48. Finding user data in process memory Process address space 0x00000000 0x01000000 0x70000000 0x7ffde000 0x7fffffff svchost process
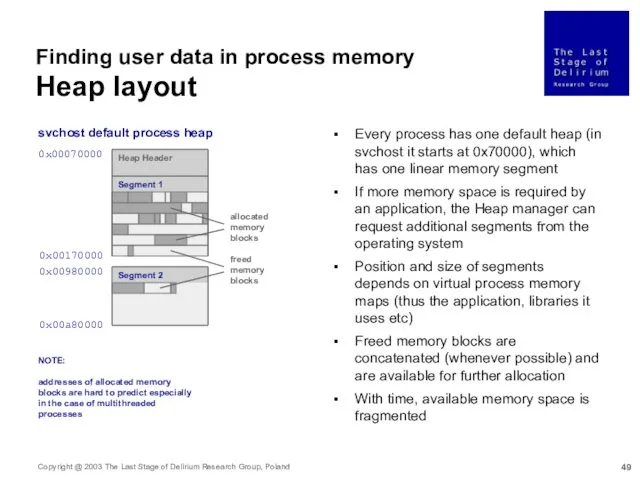
- 49. Finding user data in process memory Heap layout 0x00070000 0x00980000 0x00170000 0x00a80000 svchost default process heap
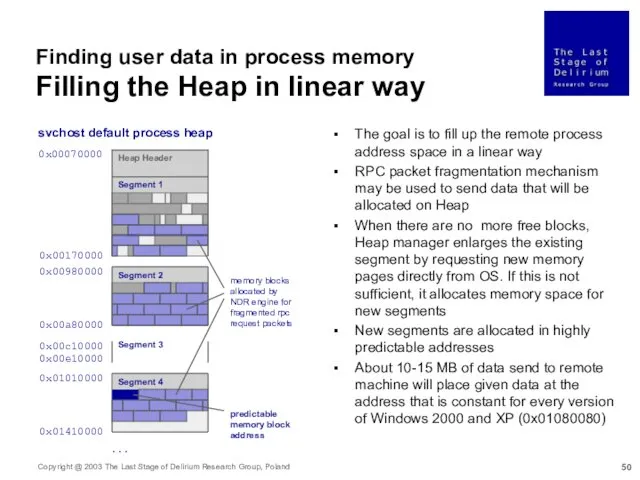
- 50. Finding user data in process memory Filling the Heap in linear way 0x00070000 0x00980000 0x00170000 0x00a80000
- 51. Finding user data in process memory OTHER METHODS Relative jump through call ebx instruction stored in
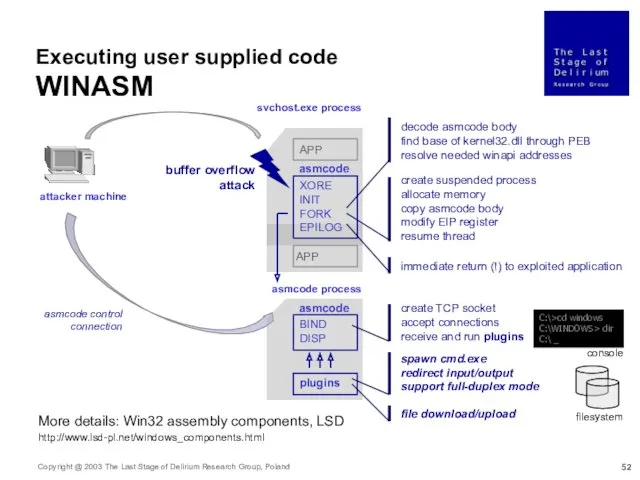
- 52. attacker machine svchost.exe process buffer overflow attack asmcode process XORE INIT FORK EPILOG APP APP create
- 53. svchost process is very critical for Windows operating system and cannot be terminated or stopped, as
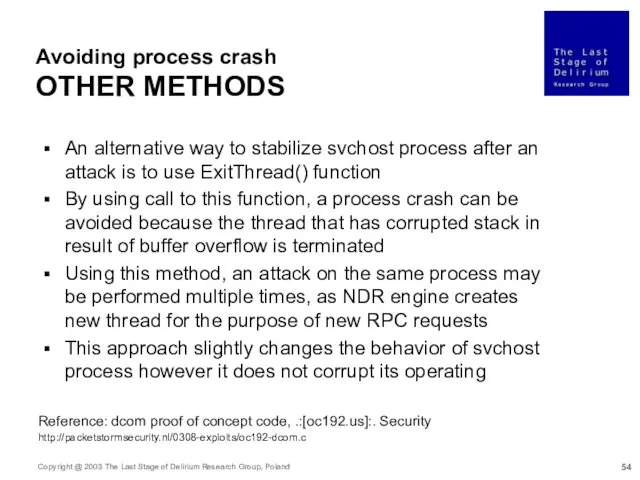
- 54. Avoiding process crash OTHER METHODS An alternative way to stabilize svchost process after an attack is
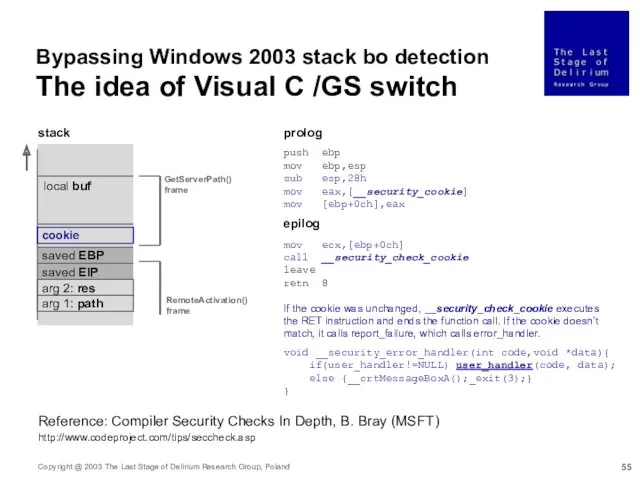
- 55. Bypassing Windows 2003 stack bo detection The idea of Visual C /GS switch Reference: Compiler Security
- 56. Bypassing Windows 2003 stack guard protection Overwriting user_handler Reference: Microsoft Compiler Flaw Technical Note, C. Ren,
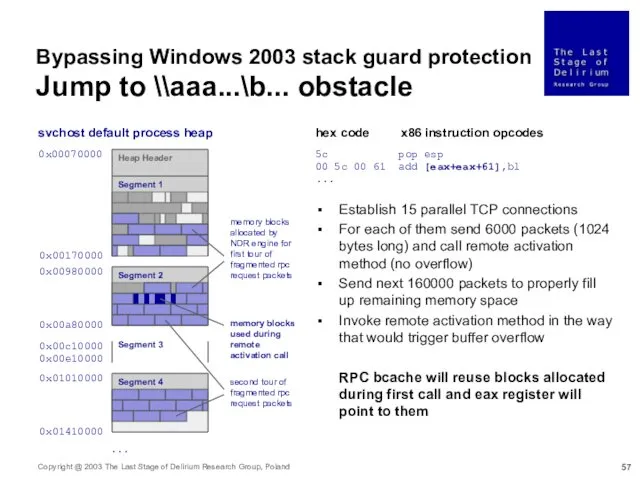
- 57. Bypassing Windows 2003 stack guard protection Jump to \\aaa...\b... obstacle 5c pop esp 00 5c 00
- 58. Bypassing Windows 2003 stack guard protection OTHER METHODS Structure Exception Handling mechanism may be used The
- 59. RPC messenger service MS03-43 The vulnerability exists in the NetrSendMessage function exported by the 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc RPC
- 60. Invoking remote RPC function NetrSendMessage() error_status_t NetrSendMessage( [in,ref,string] char *_1, [in,ref,string] char *_2, [in,ref,string] char *_3
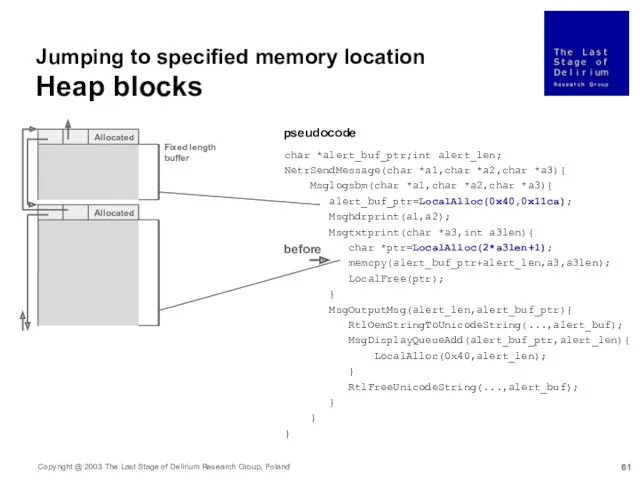
- 61. char *alert_buf_ptr;int alert_len; NetrSendMessage(char *a1,char *a2,char *a3){ Msglogsbm(char *a1,char *a2,char *a3){ alert_buf_ptr=LocalAlloc(0x40,0x11ca); Msghdrprint(a1,a2); Msgtxtprint(char *a3,int a3len){
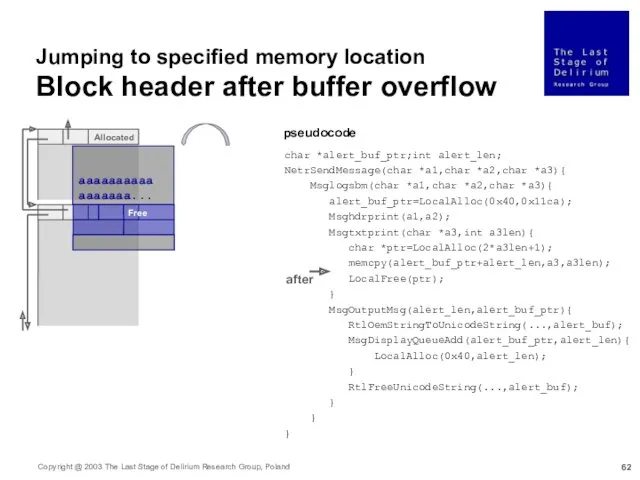
- 62. aaaaaaaaaaaaaaaaa... Allocated Free Jumping to specified memory location Block header after buffer overflow char *alert_buf_ptr;int alert_len;
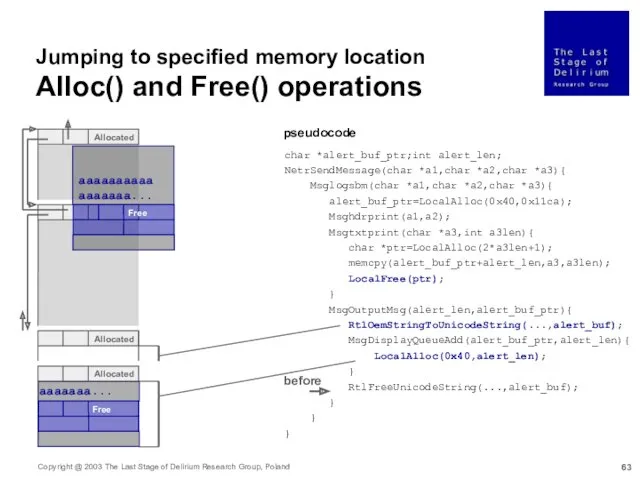
- 63. aaaaaaaaaaaaaaaaa... Allocated Allocated Allocated Free aaaaaaa... Free Jumping to specified memory location Alloc() and Free() operations
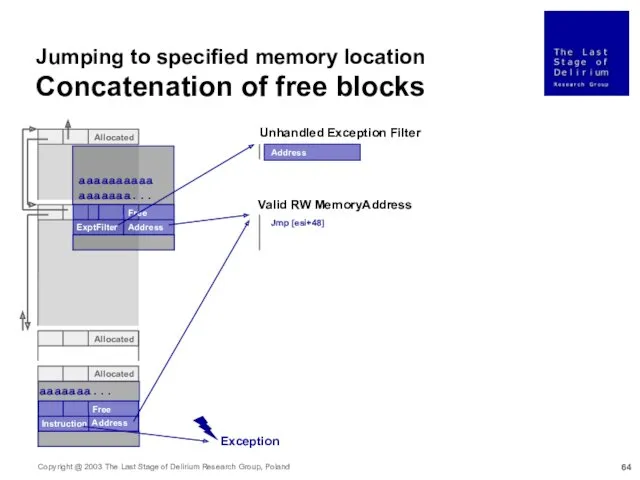
- 64. aaaaaaaaaaaaaaaaa... Allocated Allocated Allocated Free aaaaaaa... Free Unhandled Exception Filter Valid RW MemoryAddress ExptFilter Address Address
- 65. The same method as for resuming svchost process state may be used for a process that
- 66. Summary RPC mechanism is a great example of complex technological component in the context of security
- 68. Скачать презентацию








![[ uuid(11111111-2222-3333-4444-555555555555), version(1.0) ] interface if{ /* TYPES */ struct](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/39419/slide-30.jpg)




![Invoking remote RPC function (TCP) RemoteActivation() error_status_t RemoteActivation( [in] handle_t](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/39419/slide-42.jpg)





![Invoking remote RPC function NetrSendMessage() error_status_t NetrSendMessage( [in,ref,string] char *_1,](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/39419/slide-59.jpg)

 Prezentatsia
Prezentatsia Образовательная ситуация с использованием информационно-коммуникационных технологий В гостях у сказки для детей средней группы.
Образовательная ситуация с использованием информационно-коммуникационных технологий В гостях у сказки для детей средней группы. Родительный, дательный, творительный и предложный падежи имен прилагательных женского рода
Родительный, дательный, творительный и предложный падежи имен прилагательных женского рода Процессуальные теории мотивации
Процессуальные теории мотивации Шаблоны для изготовления презнтаций на зимнюют тематику.
Шаблоны для изготовления презнтаций на зимнюют тематику. Проект: Этих дней не смолкнет слава
Проект: Этих дней не смолкнет слава Бизнес-план. Индивидуальное предприятие
Бизнес-план. Индивидуальное предприятие Қаймақ технологиясы оларды нормалау және гомогенизациялау
Қаймақ технологиясы оларды нормалау және гомогенизациялау Операция Зёрнышко (презентация)
Операция Зёрнышко (презентация) Принцип действия и схема рт-252 рт-253 рт-255
Принцип действия и схема рт-252 рт-253 рт-255 Лист. Общие понятия о листе, его развитие, анатомическое строение, видоизменения, морфология и классификация
Лист. Общие понятия о листе, его развитие, анатомическое строение, видоизменения, морфология и классификация Викторина История Олимпийских игр
Викторина История Олимпийских игр Обобщение опыта по теме Психология общения
Обобщение опыта по теме Психология общения Доклад на РМО воспитателей разновозрастных групп по теме: Система мониторинга реализации ООП ДОУ
Доклад на РМО воспитателей разновозрастных групп по теме: Система мониторинга реализации ООП ДОУ Технические каналы утечки информации
Технические каналы утечки информации Участие медсестры в подготовке к инструментальным методам исследования
Участие медсестры в подготовке к инструментальным методам исследования Резцы. Классификация резцов
Резцы. Классификация резцов Умная теплица
Умная теплица Зимняя олимпиада 2014
Зимняя олимпиада 2014 День Святой Троицы (Пятидесятница)
День Святой Троицы (Пятидесятница) Драматургия танца
Драматургия танца Когерентность. Монохроматические волны
Когерентность. Монохроматические волны Современное климатическое оборудование
Современное климатическое оборудование Мои ученики
Мои ученики Конспект интегрированного занятия по развитию речи для детей младшего дошкольного возраста с использованием мнемотехники и ИКТ
Конспект интегрированного занятия по развитию речи для детей младшего дошкольного возраста с использованием мнемотехники и ИКТ Методическая разработка Презентация ко Дню Победы Поклонимся великим тем годам... Диск Диск Диск Диск
Методическая разработка Презентация ко Дню Победы Поклонимся великим тем годам... Диск Диск Диск Диск Кім ақылды кім шапшаң кім тапқыр. Таныстыру
Кім ақылды кім шапшаң кім тапқыр. Таныстыру Антон Павлович Чехов
Антон Павлович Чехов