Содержание
- 2. Outline Symmetric encryption Block encryption algorithms Stream ciphers Cipher Block Modes
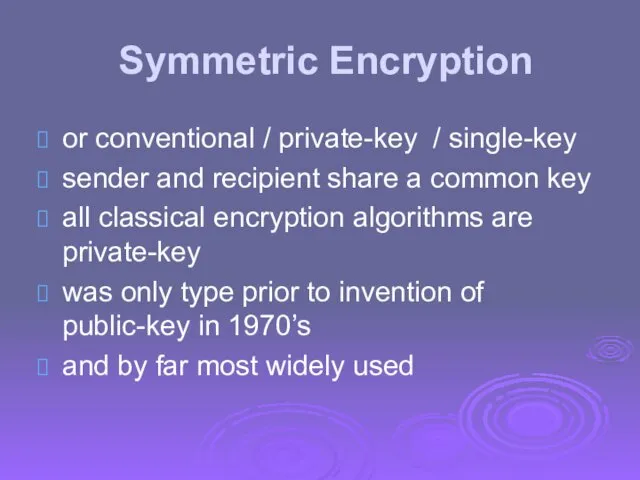
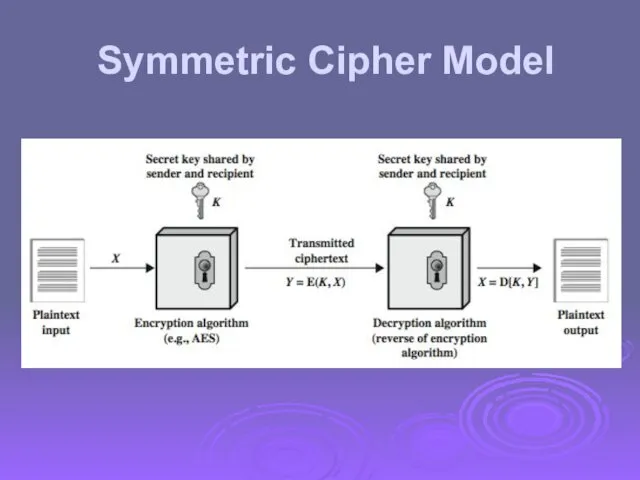
- 3. Symmetric Encryption or conventional / private-key / single-key sender and recipient share a common key all
- 4. Crypto Cryptology ⎯ The art and science of making and breaking “secret codes” Cryptography ⎯ making
- 5. Some Basic Terminology plaintext - original message ciphertext - coded message cipher - algorithm for transforming
- 6. Simple Substitution Plaintext: fourscoreandsevenyearsago Key: Ciphertext: IRXUVFRUHDAGVHYHABHDUVDIR Shift by 3 is “Caesar’s cipher” Plaintext Ciphertext
- 7. Ceasar’s Cipher Decryption Plaintext: spongebobsquarepants Plaintext Ciphertext Suppose we know a Ceasar’s cipher is being used
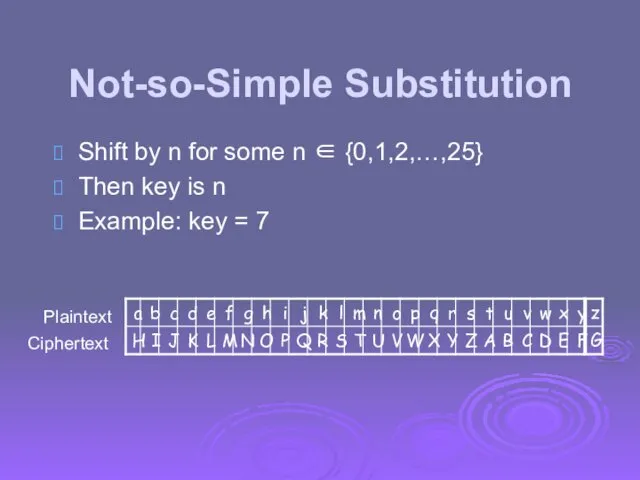
- 8. Not-so-Simple Substitution Shift by n for some n ∈ {0,1,2,…,25} Then key is n Example: key
- 9. Cryptanalysis I: Try Them All A simple substitution (shift by n) is used But the key
- 10. Even-less-Simple Substitution Key is some permutation of letters Need not be a shift For example Plaintext
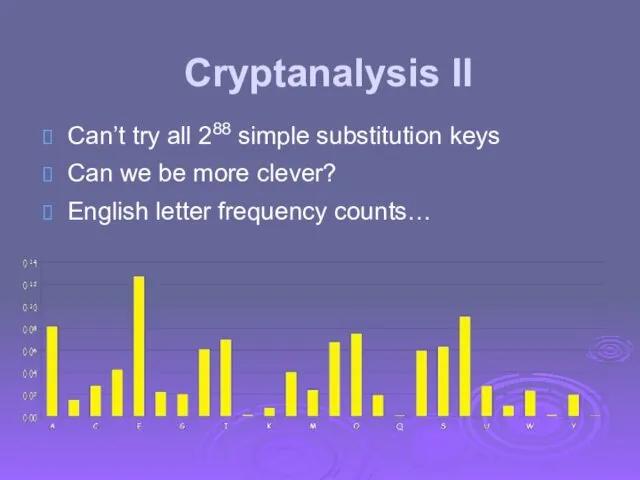
- 11. Cryptanalysis II: Be Clever We know that a simple substitution is used But not necessarily a
- 12. Cryptanalysis II Can’t try all 288 simple substitution keys Can we be more clever? English letter
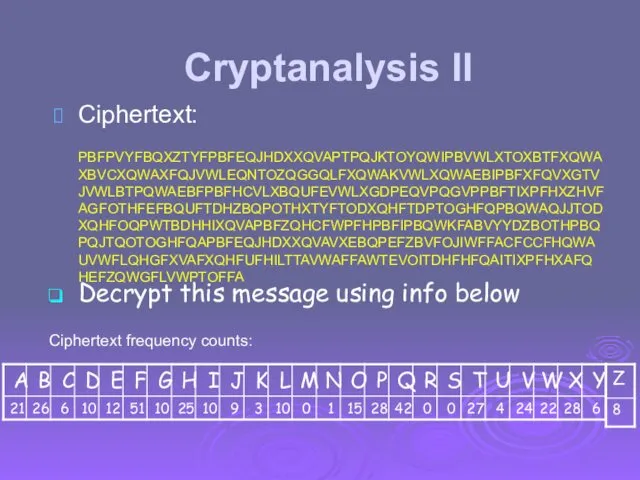
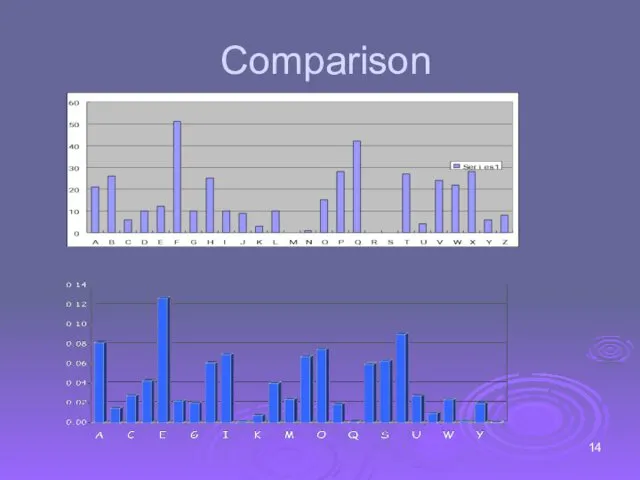
- 13. Cryptanalysis II Ciphertext: PBFPVYFBQXZTYFPBFEQJHDXXQVAPTPQJKTOYQWIPBVWLXTOXBTFXQWAXBVCXQWAXFQJVWLEQNTOZQGGQLFXQWAKVWLXQWAEBIPBFXFQVXGTVJVWLBTPQWAEBFPBFHCVLXBQUFEVWLXGDPEQVPQGVPPBFTIXPFHXZHVFAGFOTHFEFBQUFTDHZBQPOTHXTYFTODXQHFTDPTOGHFQPBQWAQJJTODXQHFOQPWTBDHHIXQVAPBFZQHCFWPFHPBFIPBQWKFABVYYDZBOTHPBQPQJTQOTOGHFQAPBFEQJHDXXQVAVXEBQPEFZBVFOJIWFFACFCCFHQWAUVWFLQHGFXVAFXQHFUFHILTTAVWAFFAWTEVOITDHFHFQAITIXPFHXAFQHEFZQWGFLVWPTOFFA Ciphertext frequency counts: Decrypt this message using info below
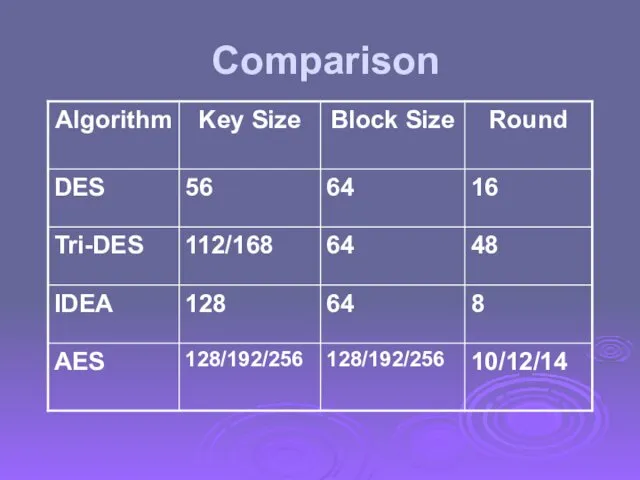
- 14. Comparison
- 15. Symmetric Cipher Model
- 16. Requirements two requirements for secure use of symmetric encryption: a strong encryption algorithm a secret key
- 17. Cryptography can characterize cryptographic system by: type of encryption operations used substitution transposition product number of
- 18. Cryptanalysis objective to recover key not just message general approaches: cryptanalytic attack brute-force attack if either
- 19. Cryptanalytic Attacks ciphertext only only know algorithm & ciphertext, is statistical, know or can identify plaintext
- 20. An encryption scheme: computationally secure if The cost of breaking the cipher exceeds the value of
- 21. Brute Force Search always possible to simply try every key most basic attack, proportional to key
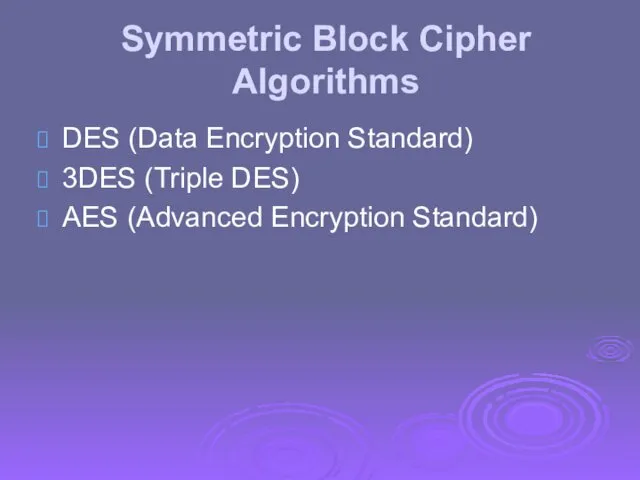
- 22. Symmetric Block Cipher Algorithms DES (Data Encryption Standard) 3DES (Triple DES) AES (Advanced Encryption Standard)
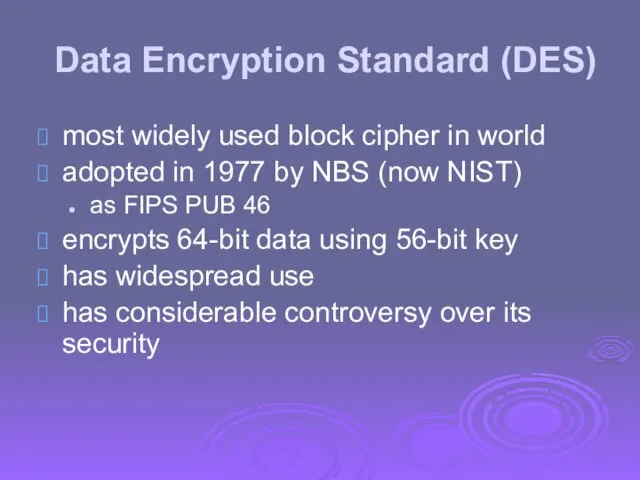
- 23. Data Encryption Standard (DES) most widely used block cipher in world adopted in 1977 by NBS
- 24. DES History IBM developed Lucifer cipher by team led by Feistel in late 60’s used 64-bit
- 25. DES Design Controversy although DES standard is public, considerable controversy over design in choice of 56-bit
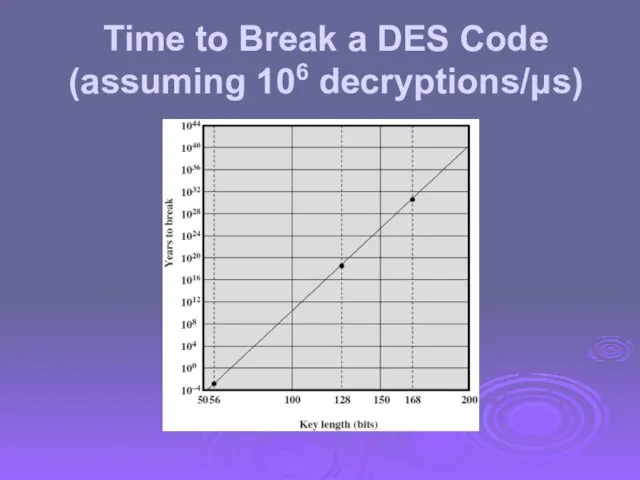
- 26. Time to Break a DES Code (assuming 106 decryptions/μs)
- 27. Multiple Encryption & DES clear a replacement for DES was needed theoretical attacks that can break
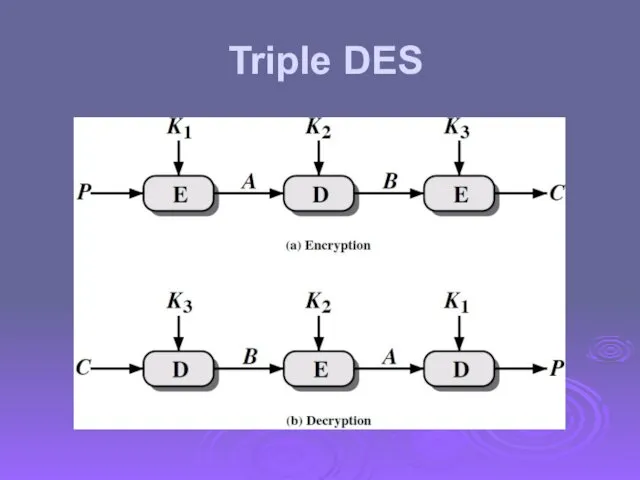
- 28. Triple DES
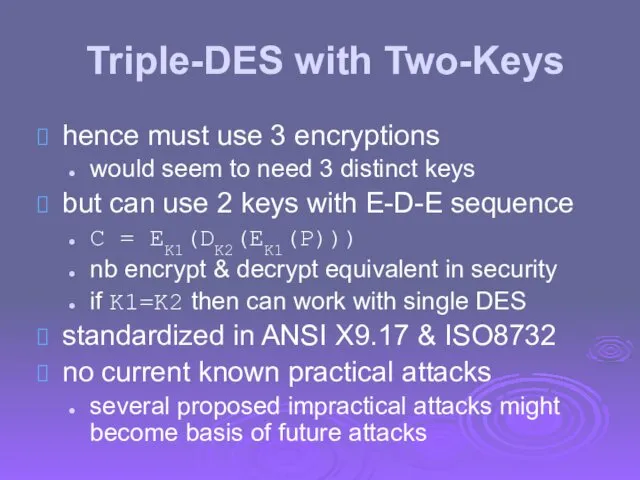
- 29. Triple-DES with Two-Keys hence must use 3 encryptions would seem to need 3 distinct keys but
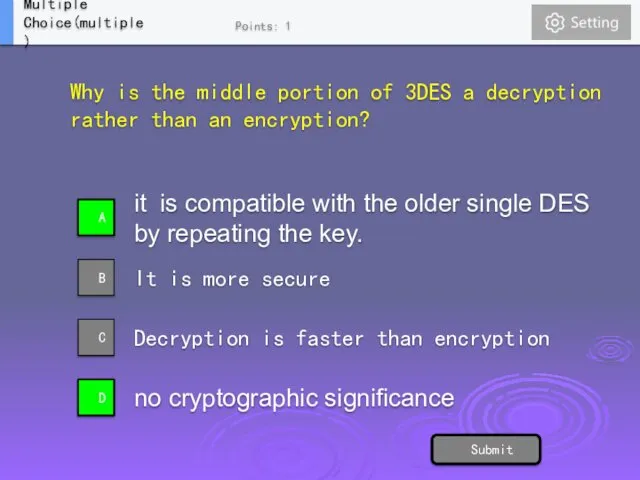
- 30. Why is the middle portion of 3DES a decryption rather than an encryption? it is compatible
- 31. Triple-DES with Three-Keys although no practical attacks on two-key Triple-DES have some concerns Two-key: key length
- 32. Origins clearly a replacement for DES was needed have theoretical attacks that can break it have
- 33. The AES Cipher - Rijndael designed by Rijmen-Daemen in Belgium has 128/192/256 bit keys, 128 bit
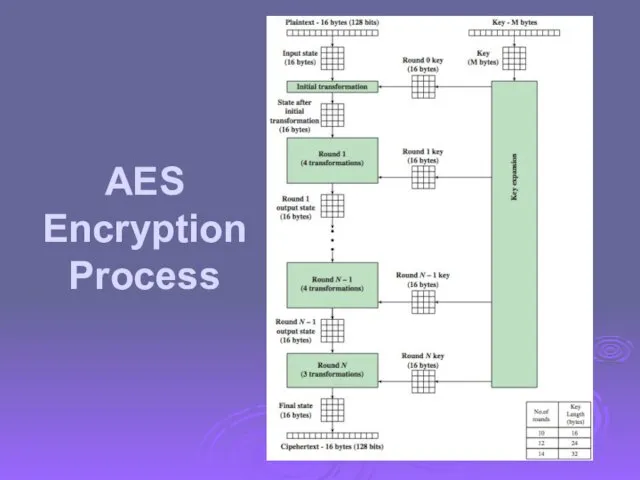
- 34. AES Encryption Process
- 35. Comparison
- 36. Random Numbers many uses of random numbers in cryptography nonces in authentication protocols to prevent replay
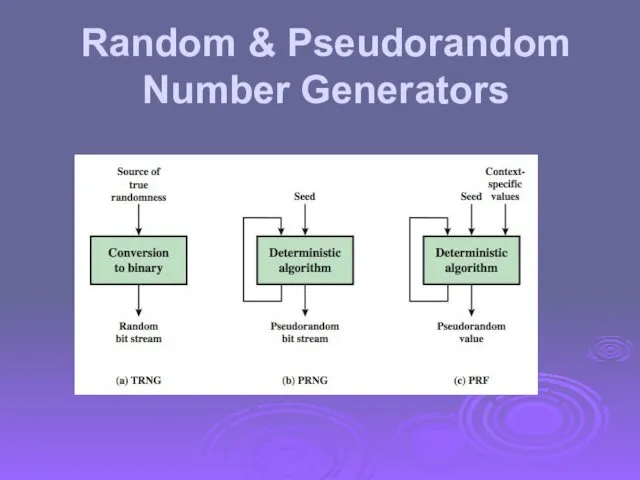
- 37. Pseudorandom Number Generators (PRNGs) often use deterministic algorithmic techniques to create “random numbers” although are not
- 38. Random & Pseudorandom Number Generators
- 39. PRNG Algorithm Design Purpose-built algorithms E.g. RC4 Algorithms based on existing cryptographic algorithms Symmetric block ciphers
- 40. Outline Symmetric encryption Block encryption algorithms Stream ciphers Cipher Block Modes
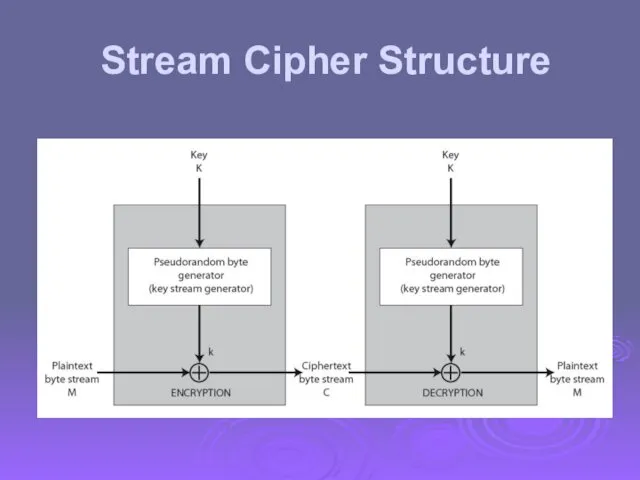
- 41. Stream Cipher Structure
- 42. Stream Cipher Properties some design considerations are: long period with no repetitions statistically random depends on
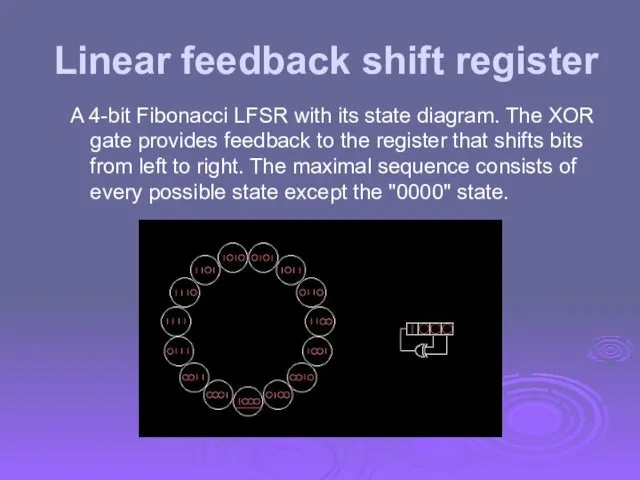
- 43. Linear feedback shift register A 4-bit Fibonacci LFSR with its state diagram. The XOR gate provides
- 45. RC4 a proprietary cipher owned by RSA DSI another Ron Rivest design, simple but effective variable
- 46. RC4 Security claimed secure against known attacks have some analyses, none practical result is very non-linear
- 47. Outline Symmetric encryption Block encryption algorithms Stream ciphers Cipher Block Modes
- 48. The Most Important Modes Electronic Codebook Mode (ECB) Cipher Block Chaining Mode (CBC) Cipher Feedback Mode
- 49. Electronic Codebook Book (ECB) message is broken into independent blocks which are encrypted each block is
- 50. 2021/3/4 Zimmerman Telegram februar 13605 fest 13732 finanzielle 13850 folgender 13918 frieden 17142 friedenschluss 17149
- 51. 2021/3/4 Zimmerman Decryption UK decrypt part of the telegraphy
- 52. Advantages and Limitations of ECB message repetitions may show in ciphertext if aligned with message block
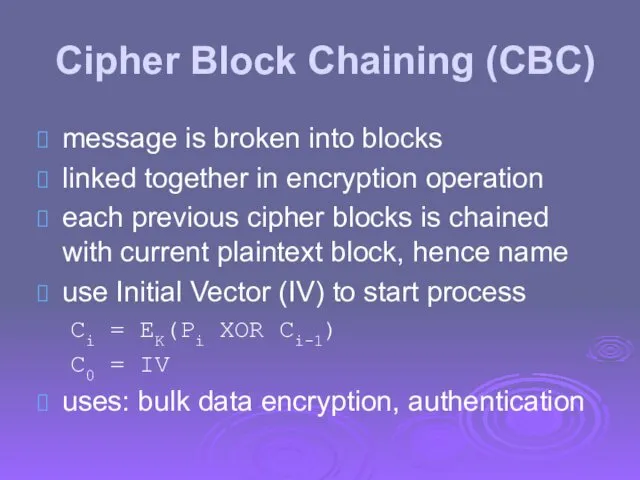
- 53. Cipher Block Chaining (CBC) message is broken into blocks linked together in encryption operation each previous
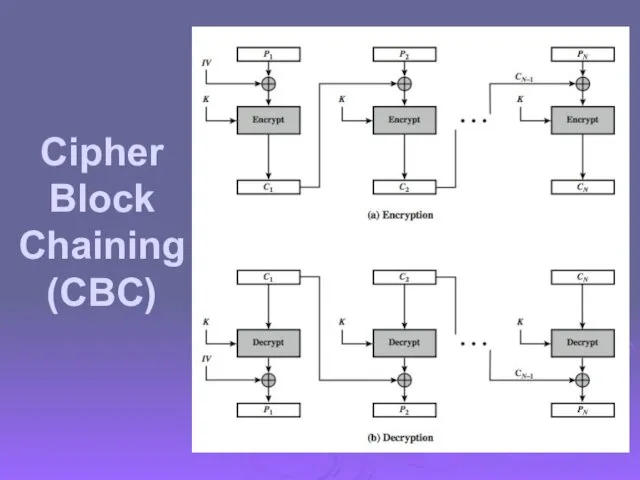
- 54. Cipher Block Chaining (CBC)
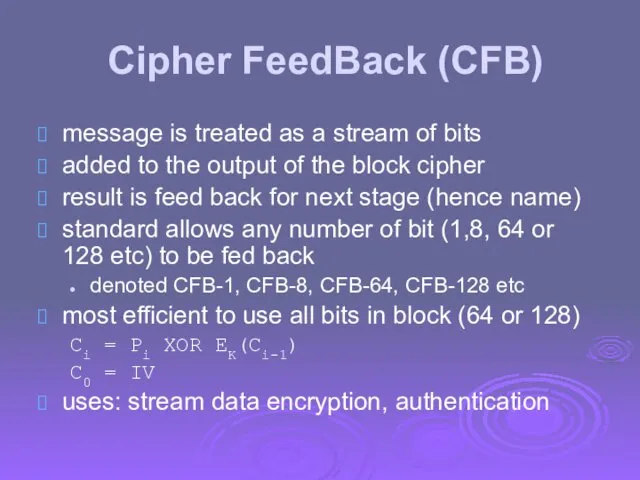
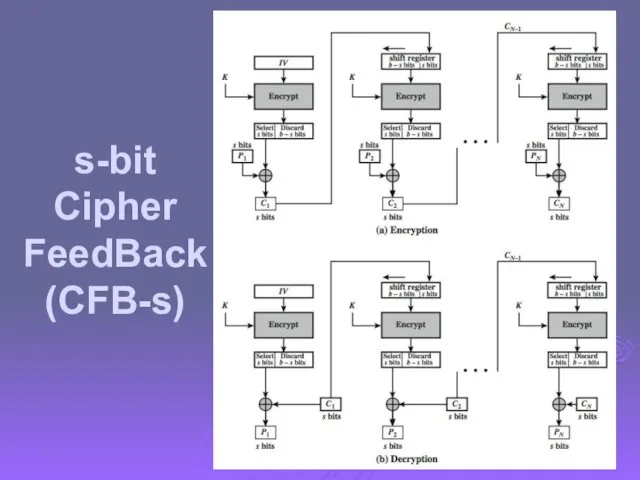
- 55. Cipher FeedBack (CFB) message is treated as a stream of bits added to the output of
- 56. s-bit Cipher FeedBack (CFB-s)
- 57. Advantages and Limitations of CFB appropriate when data arrives in bits/bytes most common stream mode Limitation:
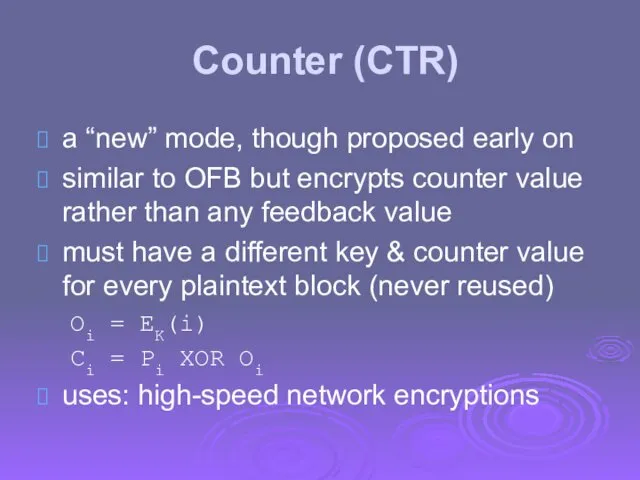
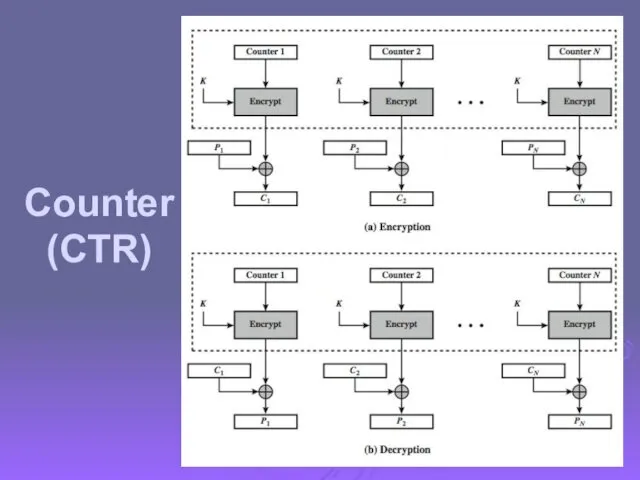
- 58. Counter (CTR) a “new” mode, though proposed early on similar to OFB but encrypts counter value
- 59. Counter (CTR)
- 60. Advantages and Limitations of CTR efficiency can do parallel encryptions in h/w or s/w can preprocess
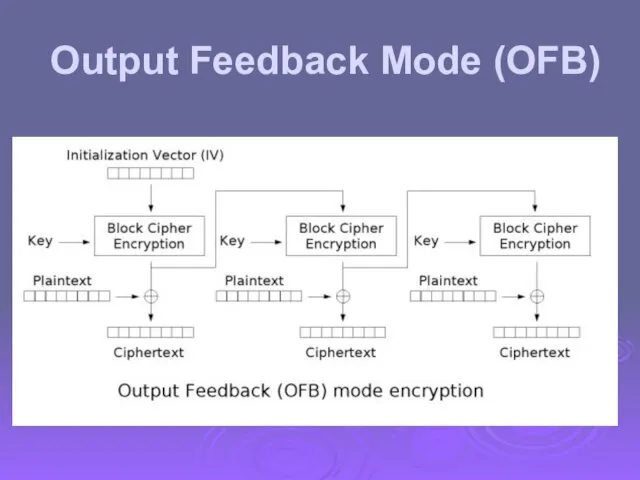
- 61. Output Feedback Mode (OFB)
- 63. Скачать презентацию



































 Экономическая психология
Экономическая психология Планирование работы по коррекции различных форм дисграфии
Планирование работы по коррекции различных форм дисграфии Метеовеличины. Атмосферное давление
Метеовеличины. Атмосферное давление Применение производной для решения задач
Применение производной для решения задач Охраняемые животные Крыма
Охраняемые животные Крыма Е. Благинина Кукушка и Котёнок
Е. Благинина Кукушка и Котёнок Учебно-методические комплексы для начальной школы
Учебно-методические комплексы для начальной школы Добро и зло
Добро и зло Ипотека для молодых учителей
Ипотека для молодых учителей Урок-проект: Прямое плетение из бумаги
Урок-проект: Прямое плетение из бумаги Объект уголовного правонарушения
Объект уголовного правонарушения От героев былых времен... Презентация для классного часа
От героев былых времен... Презентация для классного часа Дзержинский Феликс Эдмундович
Дзержинский Феликс Эдмундович Презентация к 200 юбилею М.Ю. Лермонтова
Презентация к 200 юбилею М.Ю. Лермонтова Технологии разработки Internet-приложений
Технологии разработки Internet-приложений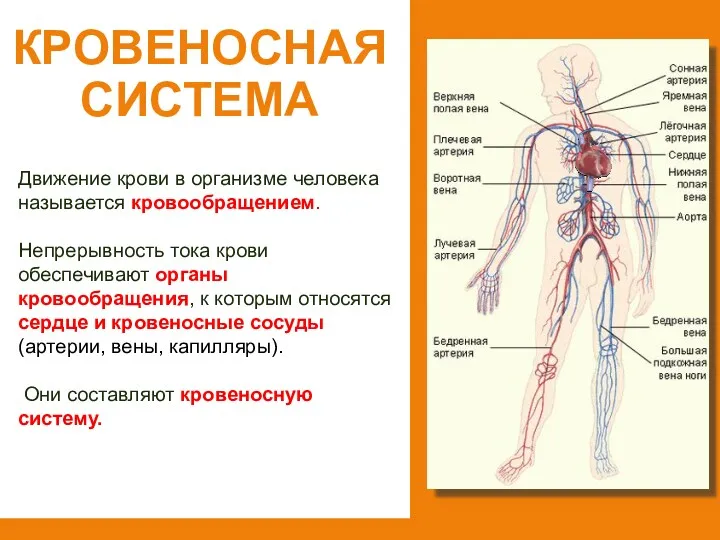 Кровеносная система
Кровеносная система Киберпреступность
Киберпреступность Тушение пожаров на железнодорожном транспорте
Тушение пожаров на железнодорожном транспорте Реклама и PR в комплексе интегрированных коммуникаций
Реклама и PR в комплексе интегрированных коммуникаций Моделирование процессов разработки нефтяного месторождения
Моделирование процессов разработки нефтяного месторождения Механизм поддержания равновесия в модели IS–LM посредством мостиков, связывающих рынки товаров и денег
Механизм поддержания равновесия в модели IS–LM посредством мостиков, связывающих рынки товаров и денег Кл.час с использованием проектной деятельности Тема: Люблю березку русскую
Кл.час с использованием проектной деятельности Тема: Люблю березку русскую Технология 3D - MID
Технология 3D - MID Измерение углов. Транспортир.
Измерение углов. Транспортир. Презентация проекта Моя семья - моя радость!
Презентация проекта Моя семья - моя радость! Из истории пионерской организации Красноэховской школы
Из истории пионерской организации Красноэховской школы Нейроэндокринные опухоли поджелудочной железы
Нейроэндокринные опухоли поджелудочной железы Система счисления
Система счисления