Содержание
- 2. David Strom - ASME 1/9/08 Webinar outline What about my desktops? Liability for personal data leaks
- 3. David Strom - ASME 1/9/08 My background IT trade magazine and Web site editor for 20
- 4. David Strom - ASME 1/9/08 Security is hard More blended threats to your networks More guest
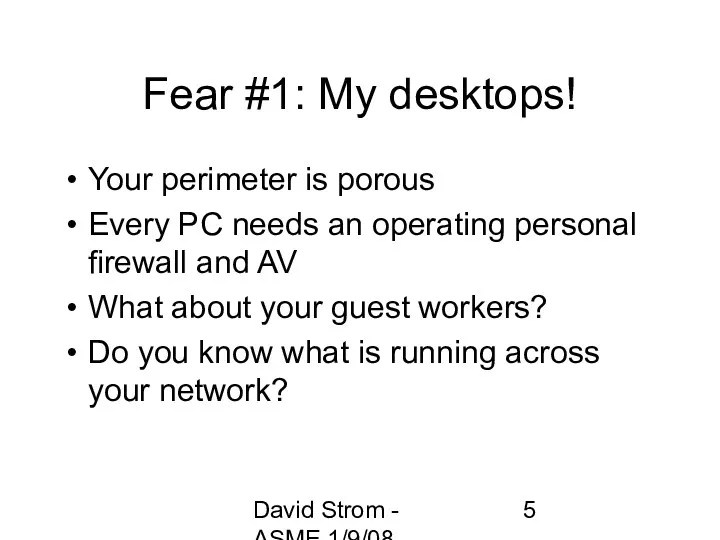
- 5. David Strom - ASME 1/9/08 Fear #1: My desktops! Your perimeter is porous Every PC needs
- 6. David Strom - ASME 1/9/08 It is so easy to secure XP – NOT! -install latest
- 7. David Strom - ASME 1/9/08 And Vista isn’t much better Disable User Account Control Disable Driver
- 8. David Strom - ASME 1/9/08 Fear #2: I am liable for any data leaks HIPAA: Identify
- 9. David Strom - ASME 1/9/08 Fear #3: How can I learn from my mistakes Buy the
- 10. David Strom - ASME 1/9/08 What happened? Hacker stole data Some systems were compromised, or had
- 11. David Strom - ASME 1/9/08 Do a vulnerability analysis Look at desktops, servers, and networks as
- 12. David Strom - ASME 1/9/08 Hindsight is an incredible tool Create chains of custody and business
- 13. David Strom - ASME 1/9/08 Fear #4: I can’t log everything First, understand that logs fall
- 14. David Strom - ASME 1/9/08 Log managers vs. Security Info Managers SIMs: Event correlation and analysis
- 15. David Strom - ASME 1/9/08 You need a common, enterprise-wide log repository One place where all
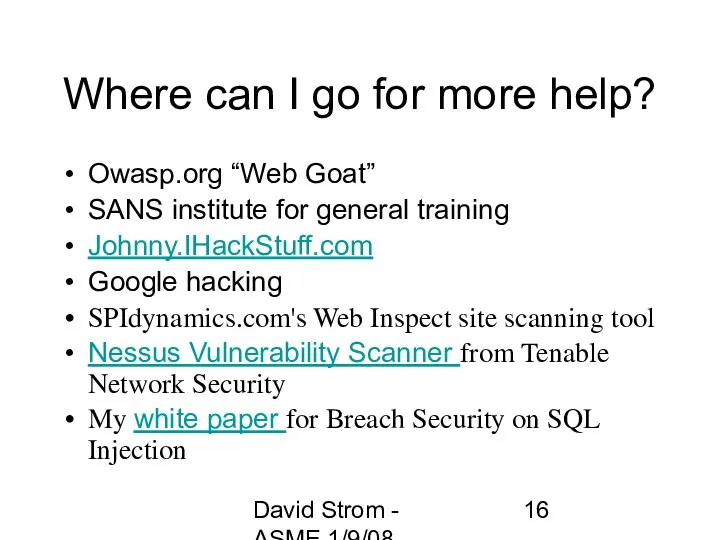
- 16. David Strom - ASME 1/9/08 Where can I go for more help? Owasp.org “Web Goat” SANS
- 17. David Strom - ASME 1/9/08 Wise words to end Don’t treat security as Yet Another IT
- 19. Скачать презентацию














 Нормативно-Правовые Акты
Нормативно-Правовые Акты Арбитражное процессуальное право. Доказательства и доказывание в арбитражном процессе
Арбитражное процессуальное право. Доказательства и доказывание в арбитражном процессе Брак, условия его заключения
Брак, условия его заключения Делопроизводство в системе государственного управления
Делопроизводство в системе государственного управления Преступления против свободы, чести и достоинства личности
Преступления против свободы, чести и достоинства личности Актуальные вопросы технологического присоединения
Актуальные вопросы технологического присоединения Законодательство в области авторского права и интеллектуальной собственности
Законодательство в области авторского права и интеллектуальной собственности Актуальные вопросы расчета пособий по обязательному социальному страхованию на случай временной нетрудоспособности
Актуальные вопросы расчета пособий по обязательному социальному страхованию на случай временной нетрудоспособности Регулирование численности безнадзорных домашних животных в Тюменской области
Регулирование численности безнадзорных домашних животных в Тюменской области Принципы, аксиомы и презумпции права. (Тема 3-4)
Принципы, аксиомы и презумпции права. (Тема 3-4) Федеральный закон О техническом регулировании от 27.12.2002 N 184-ФЗ
Федеральный закон О техническом регулировании от 27.12.2002 N 184-ФЗ Избирательное право и избирательные системы
Избирательное право и избирательные системы Инструктаж по заполнению журнала учета работы педагога
Инструктаж по заполнению журнала учета работы педагога Мемлекет, құқық және мемлекеттік-құқықтық құбылыстар туралы негізгі ұғымдар
Мемлекет, құқық және мемлекеттік-құқықтық құбылыстар туралы негізгі ұғымдар Судопроизводство. Взыскание алиментов
Судопроизводство. Взыскание алиментов Державна митна служба України: положення про діяльність
Державна митна служба України: положення про діяльність Жерге орналастыру ғылымының дамуы
Жерге орналастыру ғылымының дамуы Договор подряда
Договор подряда Стойкая нетрудоспособность
Стойкая нетрудоспособность О внесении изменений в Статьи 155 и 162 ЖК РФ
О внесении изменений в Статьи 155 и 162 ЖК РФ Азақстан республикасының. Тұтынушыларының құқығын қорғау комитетінің құқықтары, міндеттері және функциялары
Азақстан республикасының. Тұтынушыларының құқығын қорғау комитетінің құқықтары, міндеттері және функциялары Правовые взгляды представителей исторической школы права
Правовые взгляды представителей исторической школы права Государство в политической системе общества
Государство в политической системе общества Трудовые правоотношения
Трудовые правоотношения Правовой статус иностранных граждан и лиц без гражданства на территории Российской Федерации
Правовой статус иностранных граждан и лиц без гражданства на территории Российской Федерации Основні етапи європейських співтовариств і ЄС формування
Основні етапи європейських співтовариств і ЄС формування Патентная классификация
Патентная классификация