Содержание
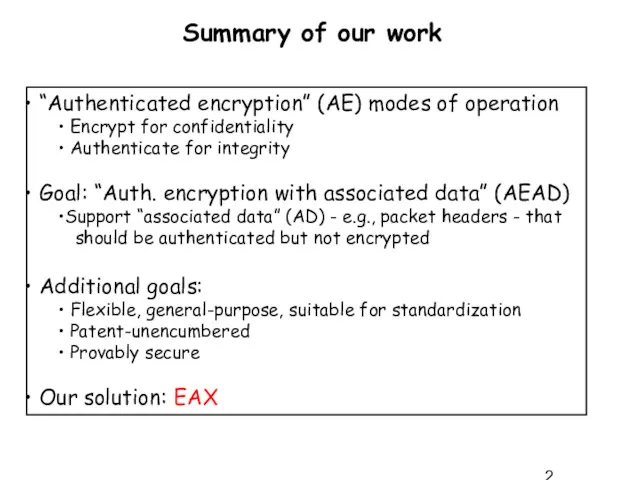
- 2. “Authenticated encryption” (AE) modes of operation Encrypt for confidentiality Authenticate for integrity Goal: “Auth. encryption with
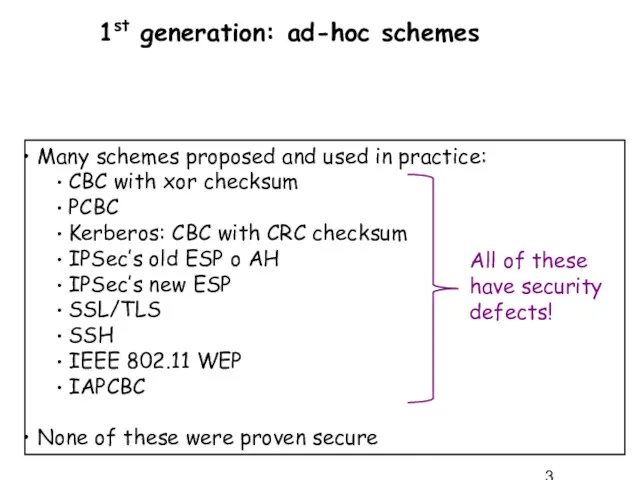
- 3. 1st generation: ad-hoc schemes Many schemes proposed and used in practice: CBC with xor checksum PCBC
- 4. 2nd generation: provable security Generic-composition: encrypt-then-authenticate Advantages: + Provably secure [Bellare,Namprempre] [Krawczyk] + Supports associated data:
- 5. 3rd generation: One-pass provably secure AE(AD) IAPM [Jutla], OCB [Rogaway], XCBC [Gligor, Donescu] Advantages: + Encrypt
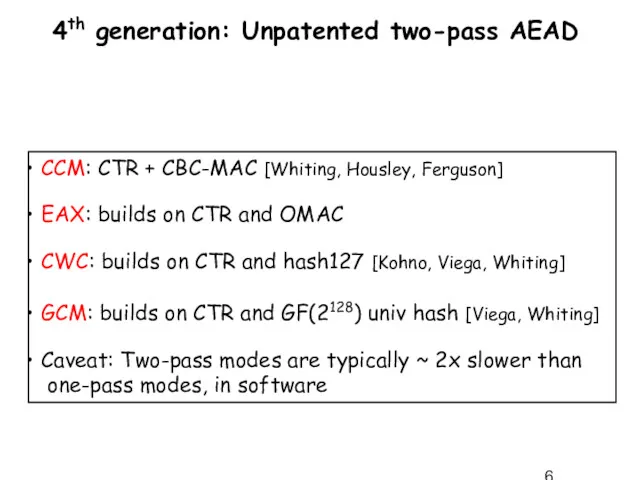
- 6. 4th generation: Unpatented two-pass AEAD CCM: CTR + CBC-MAC [Whiting, Housley, Ferguson] EAX: builds on CTR
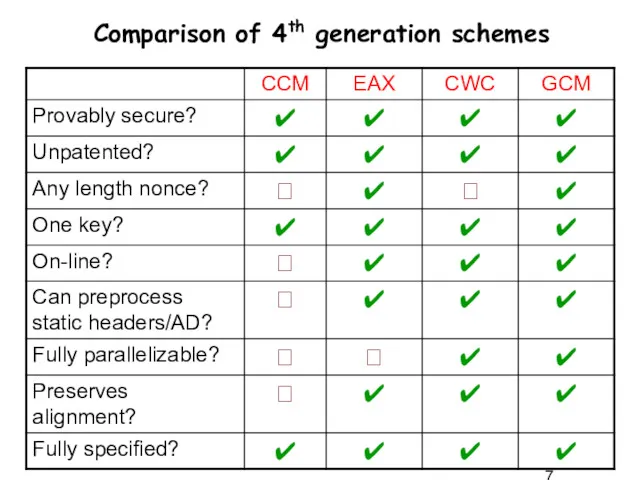
- 7. Comparison of 4th generation schemes
- 8. OMAC [Iwata, Kurosawa] L = π (0n) 2L = msb(L)? L L 4L = 2(2L) “Tweaked”
- 9. Security of OMAC∙ Theorem [slight improvement of [IK]] Suppose there is an adversary A that attacks
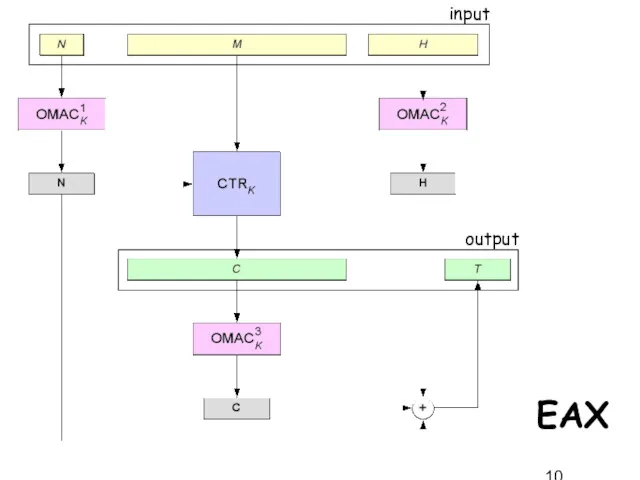
- 10. EAX input output
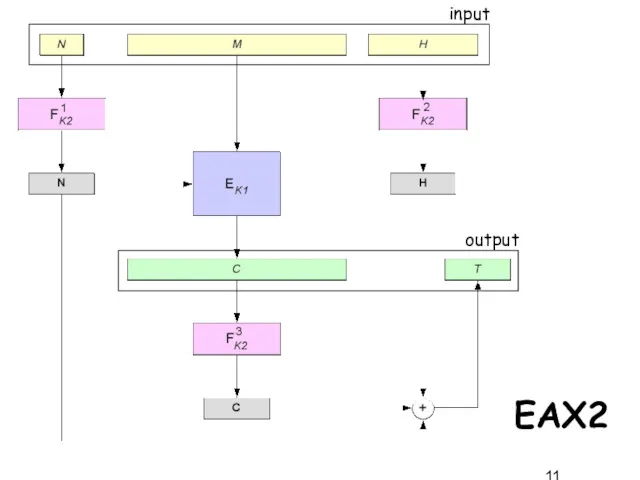
- 11. EAX2 input output
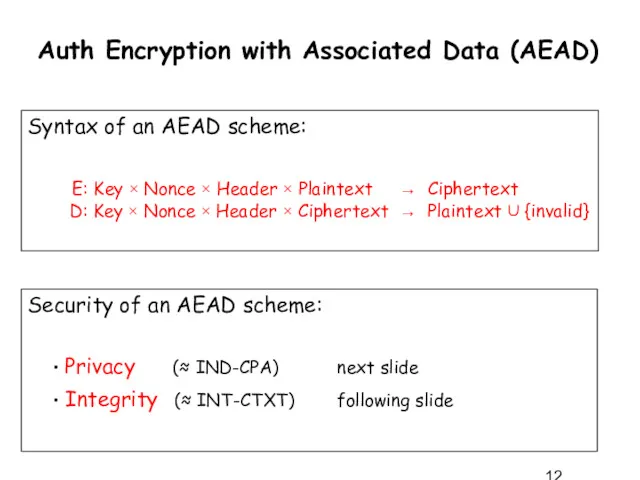
- 12. Auth Encryption with Associated Data (AEAD) Syntax of an AEAD scheme: E: Key × Nonce ×
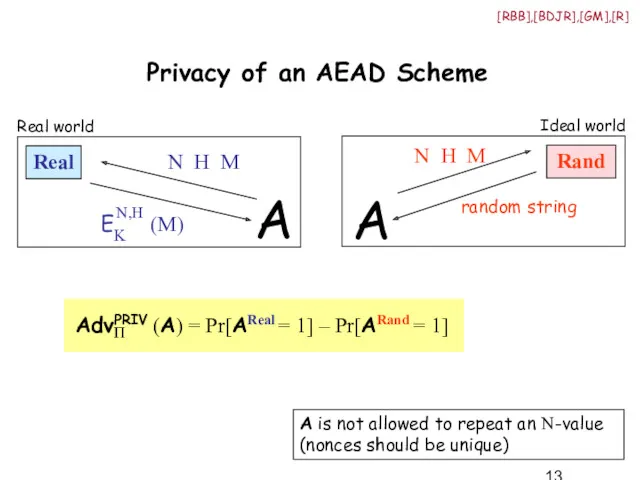
- 13. Privacy of an AEAD Scheme A is not allowed to repeat an N-value (nonces should be
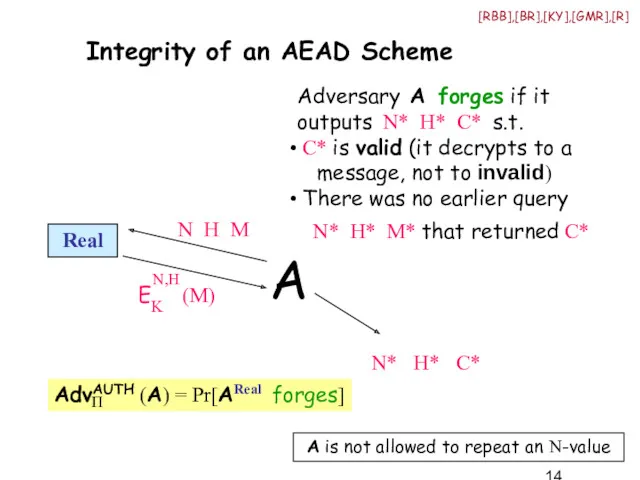
- 14. Integrity of an AEAD Scheme A N H M Real AdvAUTH (A) = Pr[AReal forges] N*
- 15. Security of EAX Theorem Suppose there is an adversary A that attacks EAX[E] using time t
- 16. Why use EAX? EAX is secure Provably secure, if underlying block cipher is secure Single API
- 18. Скачать презентацию

![3rd generation: One-pass provably secure AE(AD) IAPM [Jutla], OCB [Rogaway],](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/142409/slide-4.jpg)
![OMAC [Iwata, Kurosawa] L = π (0n) 2L = msb(L)?](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/142409/slide-7.jpg)
![Security of OMAC∙ Theorem [slight improvement of [IK]] Suppose there](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/142409/slide-8.jpg)


 role in key sectors of development of society. Standards in the field of ICT
role in key sectors of development of society. Standards in the field of ICT ICT the workplace
ICT the workplace История развития компьютерной техники
История развития компьютерной техники Моделі кольору
Моделі кольору Пошук файлів та папок (урок 12, 6 клас)
Пошук файлів та папок (урок 12, 6 клас) Смешарики : война, эпизод 1
Смешарики : война, эпизод 1 Решение логических задач
Решение логических задач Языки программирования C++
Языки программирования C++ Форматы графических файлов
Форматы графических файлов Оформление презентаций (основные принципы)
Оформление презентаций (основные принципы) Основы web. Протокол НTТР
Основы web. Протокол НTТР Функции и функциональные блоки
Функции и функциональные блоки Поиск инфомации в сети
Поиск инфомации в сети Растровая и векторная графика
Растровая и векторная графика Инструкция по работе с веб-сайтом программного обеспечения Corel
Инструкция по работе с веб-сайтом программного обеспечения Corel Obliczenia w Matlabie. Tablice
Obliczenia w Matlabie. Tablice Writing research articles. IMRD. Format. Overview
Writing research articles. IMRD. Format. Overview Beta Career
Beta Career 5 класс Презентации к учебнику Босова Л.Л.
5 класс Презентации к учебнику Босова Л.Л. Алфавитный подход к измерению количества информации.
Алфавитный подход к измерению количества информации. Автоматизация прикладного решения в системе 1С
Автоматизация прикладного решения в системе 1С Информационные технологии, их развитие и классификация
Информационные технологии, их развитие и классификация Информационные системы и технологии с элементами искусственного интеллекта. Лекция 8
Информационные системы и технологии с элементами искусственного интеллекта. Лекция 8 Керування безпекою комп’ютера
Керування безпекою комп’ютера Браузер и поисковая система
Браузер и поисковая система Нейронные сети
Нейронные сети Сертификация программного обеспечения
Сертификация программного обеспечения Усадьба Прекрасные зори
Усадьба Прекрасные зори