Содержание
- 2. Agenda Demo and Vulnerability Theory Goals Using the SPIKE API Useful samples included with SPIKE Questions
- 3. Demo of SPIKE in Action
- 4. Theory SPIKE is a GPL'd API and set of tools that allows you to quickly create
- 5. The Goals of SPIKE Find new vulnerabilities by Making it easy to quickly reproduce a complex
- 6. How the SPIKE API works Unique SPIKE data structure supports lengths and blocks s_block_start(), s_block_end(), s_blocksize_halfword_bigendian();
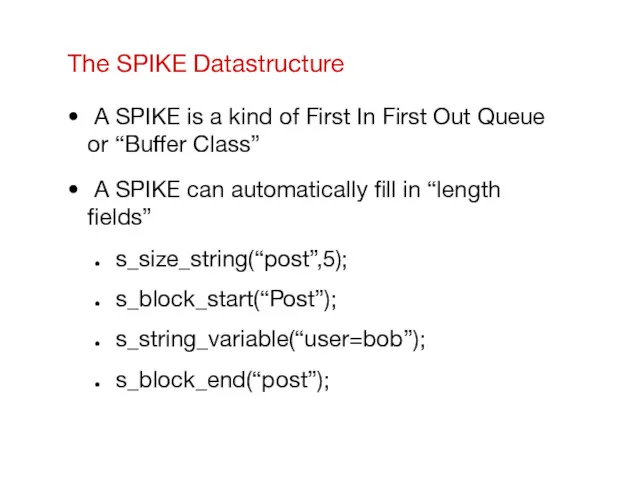
- 7. The SPIKE Datastructure A SPIKE is a kind of First In First Out Queue or “Buffer
- 8. Length Fields Length fields come in many varieties Word/halfword/string Big endian, little endian More than one
- 9. A few basic calls The main call is s_push(buffer,size) underneath everything Currently, there is no s_pop();
- 10. Setting up/destroying a SPIKE Global variables you have to deal with: set_current_spike(*struct spike); spike_clear(); Malloc fun
- 11. Network SPIKE calls Basic TCP connectivity spike_tcp_connect(host,port); spike_send(); spike_close_tcp(); Basic UDP Connectivity spike_udp_connect(host,port); spike_send();
- 12. Fuzzing Framework SPIKE calls s_string_variable(“”); s_string_repeat(“A”,5000); Equivalent to s_push("perl -e 'print “A” x 5000’”) While loop
- 13. Advantages to using SPIKE’s fuzzing framework over a perl script Size values will automatically get updated
- 14. The Process of Using SPIKE on an unknown protocol Use Ethereal to cut and paste the
- 15. The SPIKE scripting language ...is C. s_parse(“filename.spk”); Loads the file line by line and does limited
- 16. Current Demo SPIKEs Web Focused MSRPC protocol support Miscellaneous other demos
- 17. SPIKE Programs for non Web Apps msrpcfuzz Citrixfuzz Quake,halflife (UDP demos)
- 18. Quickstart: msrpcfuzz First use DCEDUMP (basically rpcinfo against Windows) Then chose a program and port to
- 19. SPIKE Programs for Web Apps ntlm2/ntlm_brute webmitm makewebfuzz.pl webfuzz.c closed_source_web_server_fuzzer generic_web_server_fuzz
- 20. ntlm_brute and ntlm2 Tries to do a dictionary attack on NTLM authenticating web servers Somewhat slow
- 21. Webmitm (SPIKE version, not dsniff Version) Transparent proxy (originally from dsniff) Used to generate http_request files
- 22. Makewebfuzz.pl Creates webfuzz.c files from http_request files Superceeded by SPIKE Console wizardry and generic .spk scripts,
- 23. Webfuzz Sends the valid request, but incrementally goes through each variable in the request and checks
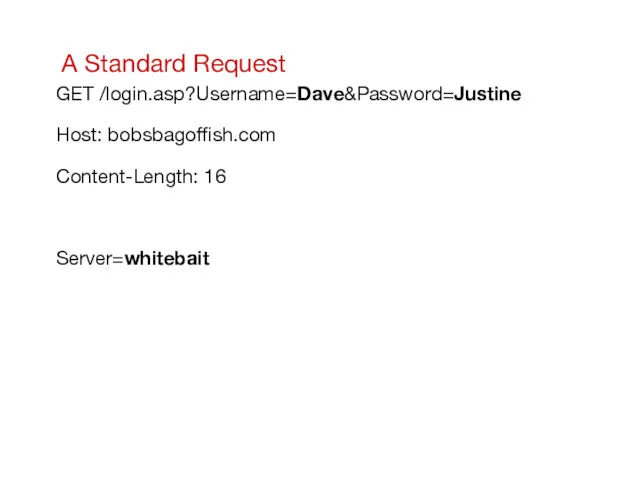
- 24. A Standard Request GET /login.asp?Username=Dave&Password=Justine Host: bobsbagoffish.com Content-Length: 16 Server=whitebait
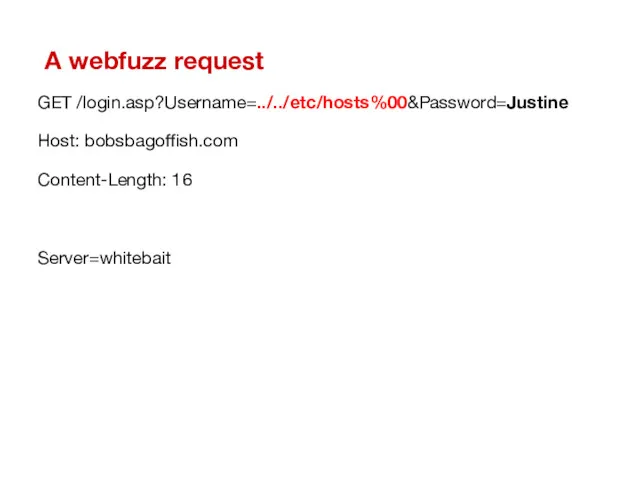
- 25. A webfuzz request GET /login.asp?Username=../../etc/hosts%00&Password=Justine Host: bobsbagoffish.com Content-Length: 16 Server=whitebait
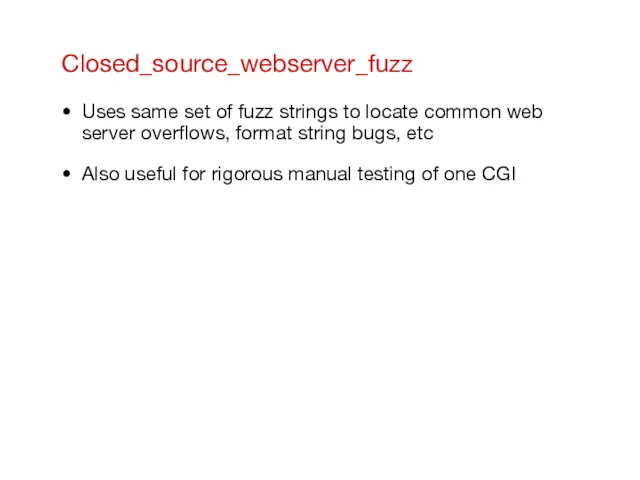
- 26. Closed_source_webserver_fuzz Uses same set of fuzz strings to locate common web server overflows, format string bugs,
- 27. Automating the process of finding SQL injection bugs odbcwebfuzz.sh Make a directory of captured http_requests using
- 28. When Automation Fails This is an exponential problem! Unlike commercial alternatives to SPIKE every part of
- 29. Examples where automation fails User Registration that requires a sequence of pages to be hit use
- 30. The SPIKE Console wxPython cross platform pretty Wizards enable quick utilization of SPIKE's capabilities Currently beta,
- 31. The Future of SPIKE SPIKE Console Improvements Additional SPIKE protocol demos and updates
- 33. Скачать презентацию




















 Оператор цикла с предусловием
Оператор цикла с предусловием Другие нейросети. Урок 4.3
Другие нейросети. Урок 4.3 Методы сортировок массивов
Методы сортировок массивов Динамикалық SQL
Динамикалық SQL Программирование на Паскале - первый уровень. Простые (линейные) программы
Программирование на Паскале - первый уровень. Простые (линейные) программы Основы алгебры логики. Логические основы компьютера
Основы алгебры логики. Логические основы компьютера Числовые данные 2 класс
Числовые данные 2 класс Структура и функции MS DOS
Структура и функции MS DOS Организация труда в конвергентной редакции мультимедийного СМИ
Организация труда в конвергентной редакции мультимедийного СМИ Массивы
Массивы Quicksort
Quicksort Основные понятия и принципы математического моделирования
Основные понятия и принципы математического моделирования География сферы услуг (инфографика)
География сферы услуг (инфографика) Разработка клиентских веб-приложений
Разработка клиентских веб-приложений Кодирование графической информации
Кодирование графической информации Этапы проектирования базы данных
Этапы проектирования базы данных Информационное общество
Информационное общество MobileTrans. Поддержка 3000 + телефонов и различных сетей
MobileTrans. Поддержка 3000 + телефонов и различных сетей Общие сведения о языке программирования Паскаль
Общие сведения о языке программирования Паскаль Умовні і циклічні конструкції JavaScript
Умовні і циклічні конструкції JavaScript Зачем нужна информатика
Зачем нужна информатика Параллельные и последовательные интерфейсы. ААС 05
Параллельные и последовательные интерфейсы. ААС 05 MS Excel в курсовой работе
MS Excel в курсовой работе Электронное пособие для оказания профориентационной поддержки школьникам
Электронное пособие для оказания профориентационной поддержки школьникам Основы логики.
Основы логики. Основы алгоритмизации и программирования
Основы алгоритмизации и программирования Website redesign
Website redesign ВКР: Совершенствование системы управления персоналом сервисного предприятия
ВКР: Совершенствование системы управления персоналом сервисного предприятия