Содержание
- 2. What is database A database is a collection of structured data. A database captures an abstract
- 3. What is DBMS A DBMS is a (usually complex) piece of software that sits in front
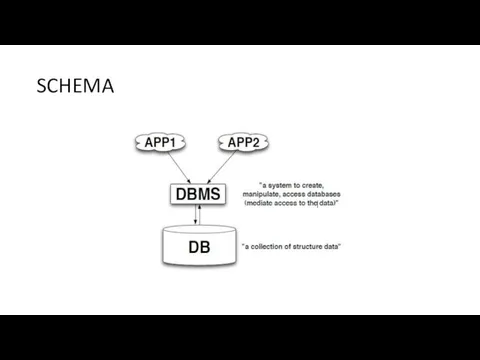
- 4. SCHEMA
- 5. Brief History The first general-purpose DBMS designed by Charles Bachman at General Electric in the early
- 6. Types of Databases Hierarchical database Network database Relational database Object-oriented database NoSQL Graph Oriented Database -
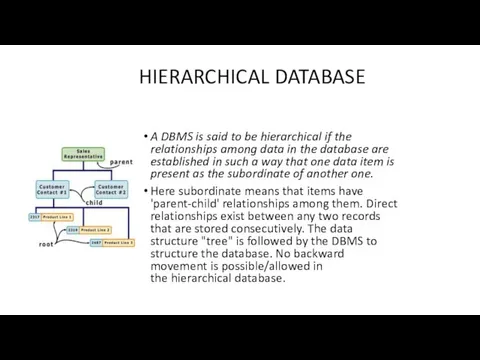
- 7. HIERARCHICAL DATABASE A DBMS is said to be hierarchical if the relationships among data in the
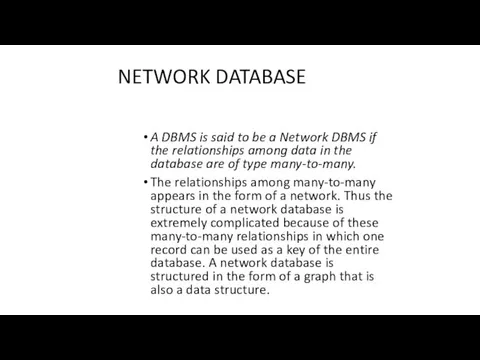
- 8. NETWORK DATABASE A DBMS is said to be a Network DBMS if the relationships among data
- 9. RELATIONAL DATABASE A DBMS is said to be a Relational DBMS or RDBMS if the database
- 10. OBJECT-ORIENTED DATABASE Object-oriented databases use small, reusable chunks of software called objects. The objects themselves are
- 11. FILE SYSTEMS VERSUS A DBMS Data independence – physical storage system is hidden from the final
- 12. LEVELS OF ABSTRACTION Conceptual Entities and Relations between Them Physical File organization, storage selection for different
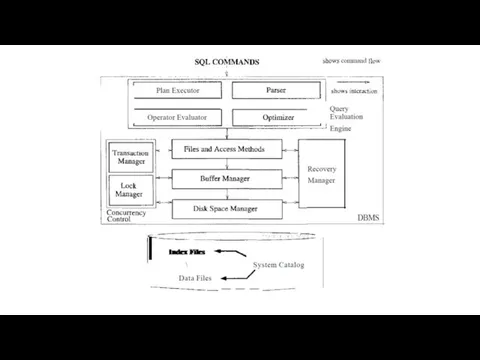
- 13. Queries in a DBMS A very attractive feature of the relational model is that it supports
- 14. TRANSACTION MANAGEMENT Airline reservations when one travel agent looks up Flight 100 on some given day
- 15. Concurrency, Control and Recovery Every object that is read or written by a transaction is first
- 17. TWO CONCEPTUAL USERS OF DBMS Application programmers Database Administrators where administrators responsibilities are often next: Design
- 18. Questions What are the main benefits of using a DBMS to manage data in applications involving
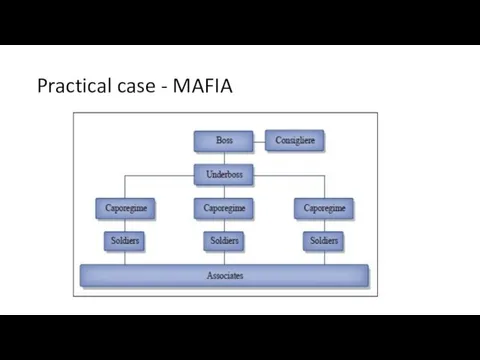
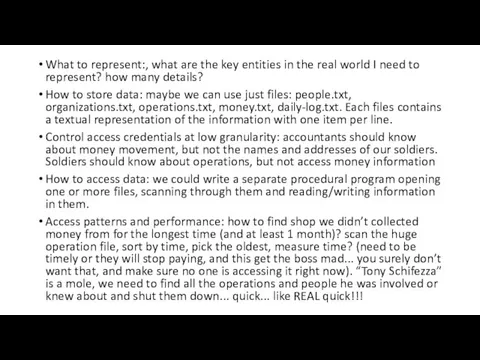
- 21. Practical case - MAFIA
- 22. I need to store information about people that work for me (soldiers, caporegime, etc..) organizations I
- 23. I will need to share some of this information with external organizations I work with, protecting
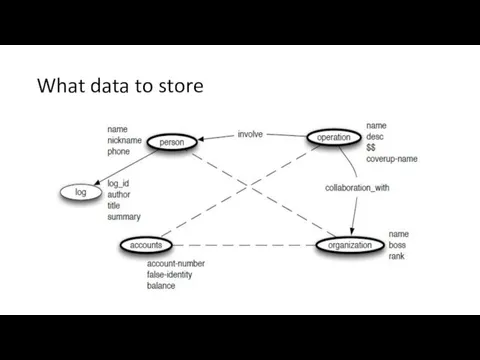
- 24. What data to store
- 25. What to Consider
- 26. What to represent:, what are the key entities in the real world I need to represent?
- 28. Скачать презентацию
















 Модели качества процессов конструирования ПО
Модели качества процессов конструирования ПО Модели и моделирование. Системный подход в моделировании. Этапы моделирования. Математические модели в биологии
Модели и моделирование. Системный подход в моделировании. Этапы моделирования. Математические модели в биологии Системи управління базами даних. Звіти. Призначення та режими роботи зі звітами. Створення звітів
Системи управління базами даних. Звіти. Призначення та режими роботи зі звітами. Створення звітів Информационное обеспечение САПР
Информационное обеспечение САПР Файл и файловая система. Презентация к уроку. 8 класс.
Файл и файловая система. Презентация к уроку. 8 класс. KLM Royal Dutch Airlines. Отчет по странице бренда в ВКОНТАКТЕ
KLM Royal Dutch Airlines. Отчет по странице бренда в ВКОНТАКТЕ Oracle 12с. Встроенные функции (PL/SQL, лекция 11)
Oracle 12с. Встроенные функции (PL/SQL, лекция 11) Спойлеры в Повер Поинт
Спойлеры в Повер Поинт Where can I get a copy of XPG PRIME software
Where can I get a copy of XPG PRIME software Структурные типы данных (Delphi / Pascal, глава 3)
Структурные типы данных (Delphi / Pascal, глава 3) Apps for smartphones
Apps for smartphones Базы данных
Базы данных Цифровое видео
Цифровое видео Game Des
Game Des Основные понятия базы данных
Основные понятия базы данных Алгебра высказываний. Логические выражения
Алгебра высказываний. Логические выражения Своя игра по информатике
Своя игра по информатике Файлы и файловая система
Файлы и файловая система Хмарні технології
Хмарні технології Instructions for use
Instructions for use ГПБ Ипотека SC. Инструкция
ГПБ Ипотека SC. Инструкция КБИС. Основы криптографии. Симметричные алгоритмы шифрования. (Лекция 6)
КБИС. Основы криптографии. Симметричные алгоритмы шифрования. (Лекция 6) Презентация и разработка урока информатики во 2 классе Техника безопасности в компьютерном классе
Презентация и разработка урока информатики во 2 классе Техника безопасности в компьютерном классе Основы Visual Basic
Основы Visual Basic Построение диаграмм и графиков
Построение диаграмм и графиков Безопасность информационных технологий
Безопасность информационных технологий Информационное общество. Теория и реальность
Информационное общество. Теория и реальность База данных - основа информационной системы
База данных - основа информационной системы