Содержание
- 2. Some common firewall properties: Firewalls are resistant to network attacks. All traffic flows through the firewall.
- 3. Packet filtering (Stateless) firewalls - usually part of a router firewall, which permits or denies traffic
- 4. Usually part of a router firewall, which permits or denies traffic based on Layer 3 and
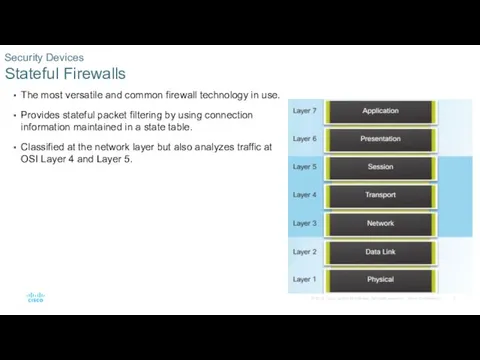
- 5. The most versatile and common firewall technology in use. Provides stateful packet filtering by using connection
- 6. Provide standard firewall capabilities like stateful inspection. Contain integrated intrusion prevention. Use application awareness and control
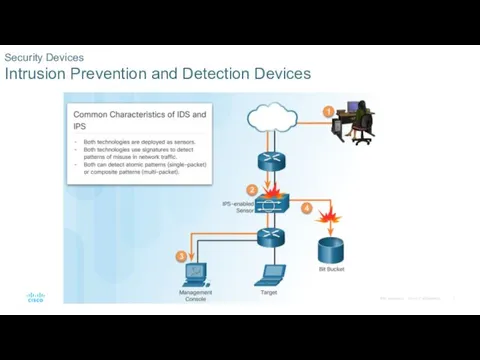
- 7. Security Devices Intrusion Prevention and Detection Devices
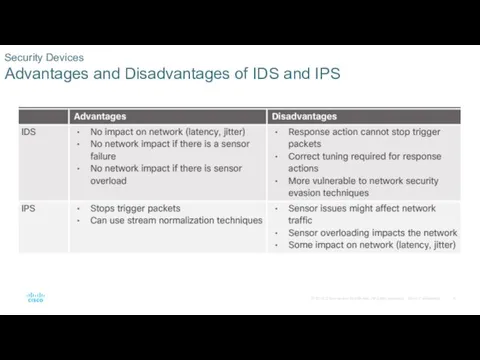
- 8. Security Devices Advantages and Disadvantages of IDS and IPS
- 9. Host-based IPS (HIPS): Software installed on a single host to monitor and analyze suspicious activity. Monitor
- 10. Cisco Advanced Malware Protection (AMP): Is enterprise-class advanced malware analysis and protection solution. Provides comprehensive malware
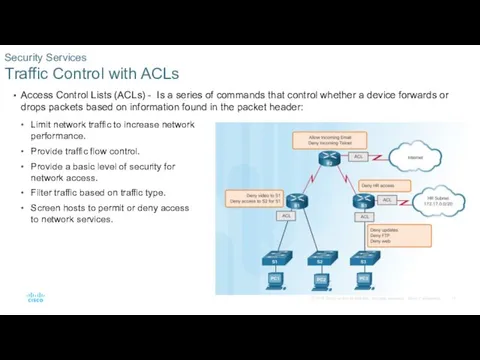
- 11. Access Control Lists (ACLs) - Is a series of commands that control whether a device forwards
- 12. The two types of Cisco IPv4 ACLs are standard and extended. Standard ACLs can be used
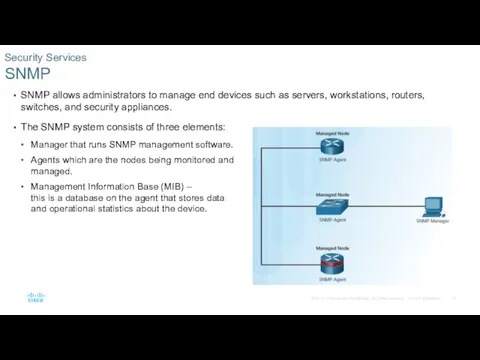
- 13. SNMP allows administrators to manage end devices such as servers, workstations, routers, switches, and security appliances.
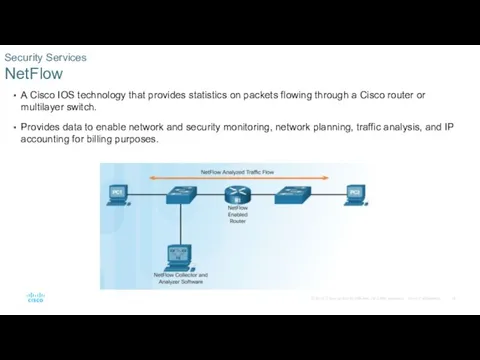
- 14. A Cisco IOS technology that provides statistics on packets flowing through a Cisco router or multilayer
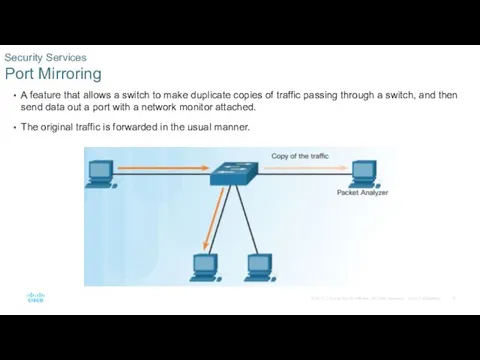
- 15. A feature that allows a switch to make duplicate copies of traffic passing through a switch,
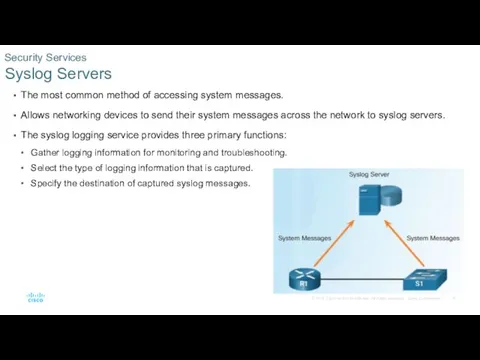
- 16. The most common method of accessing system messages. Allows networking devices to send their system messages
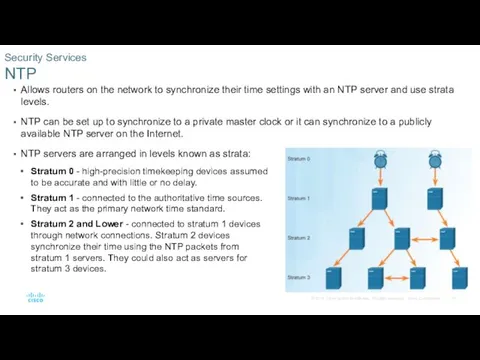
- 17. Allows routers on the network to synchronize their time settings with an NTP server and use
- 18. AAA Services is a set of three independent security functions: Authentication, Authorization, and Accounting/auditing. Authentication -
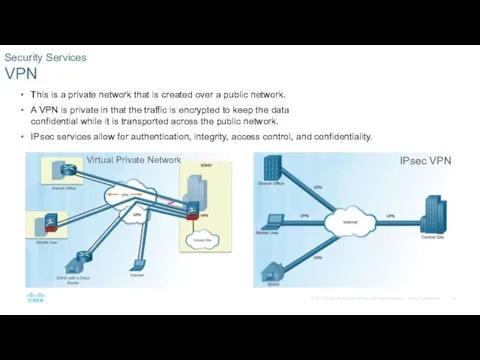
- 19. This is a private network that is created over a public network. A VPN is private
- 20. Network Representations
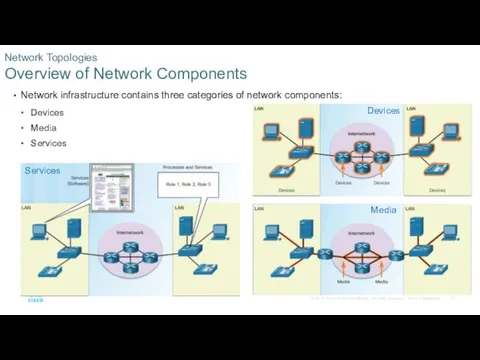
- 21. Network infrastructure contains three categories of network components: Devices Media Services Network Topologies Overview of Network
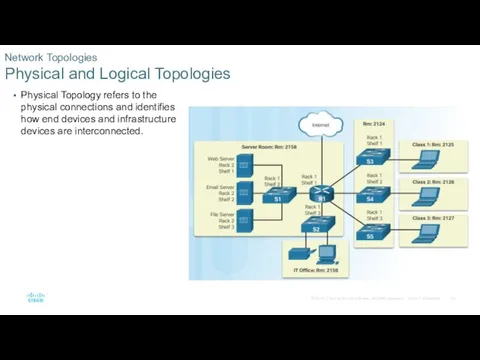
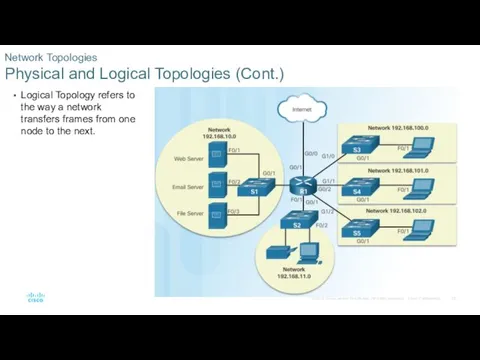
- 22. Physical Topology refers to the physical connections and identifies how end devices and infrastructure devices are
- 23. Logical Topology refers to the way a network transfers frames from one node to the next.
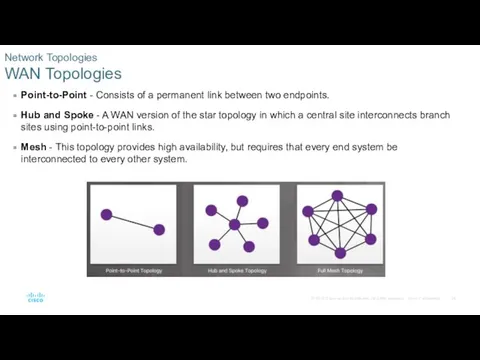
- 24. Network Topologies WAN Topologies Point-to-Point - Consists of a permanent link between two endpoints. Hub and
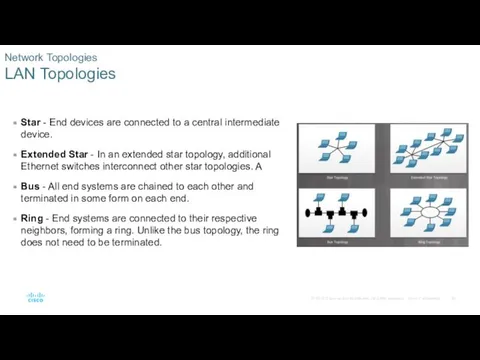
- 25. Network Topologies LAN Topologies Star - End devices are connected to a central intermediate device. Extended
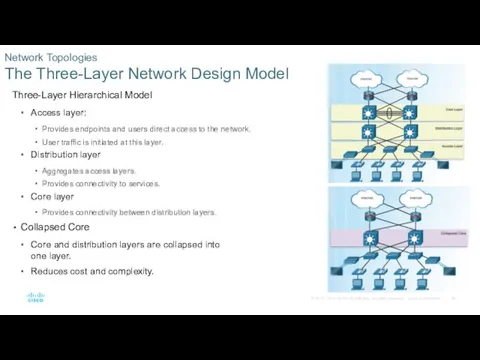
- 26. Three-Layer Hierarchical Model Access layer: Provides endpoints and users direct access to the network. User traffic
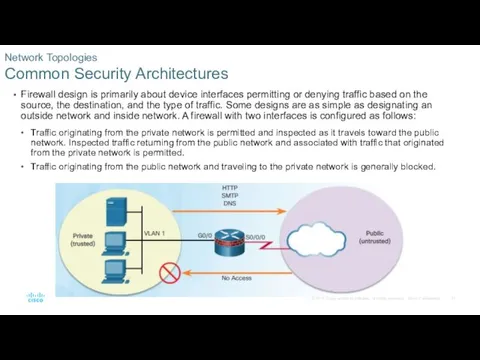
- 27. Firewall design is primarily about device interfaces permitting or denying traffic based on the source, the
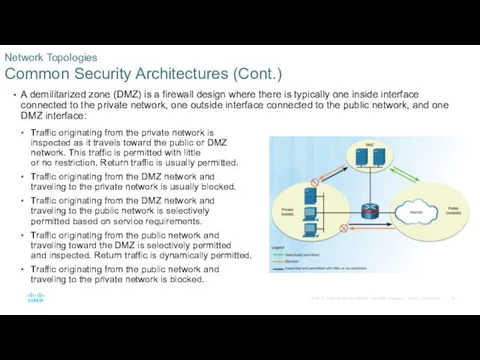
- 28. A demilitarized zone (DMZ) is a firewall design where there is typically one inside interface connected
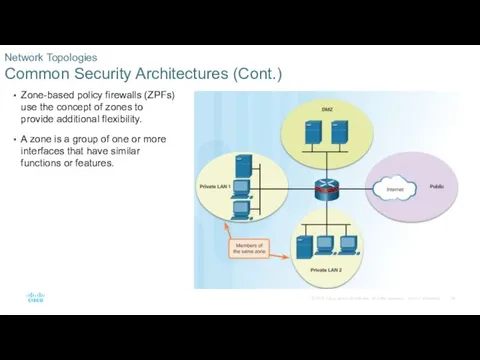
- 29. Zone-based policy firewalls (ZPFs) use the concept of zones to provide additional flexibility. A zone is
- 30. Summary
- 31. There are many different types of firewalls: packet filtering (stateless) firewall, stateful firewall, application gateway firewall
- 32. Deciding which implementation of IDS and IPS to use is based on the security goals of
- 33. NetFlow provides data to enable network and security monitoring, network planning, traffic analysis to include identification
- 34. The network infrastructure contains three categories of network components: devices, media, and services. LAN and Wide
- 35. New Terms and Commands
- 37. Скачать презентацию















 Элективное занятие по информатике в 9 классе
Элективное занятие по информатике в 9 классе О браузерах в интернете
О браузерах в интернете SimCorp APL
SimCorp APL Социальная сеть, как основа современной культуры
Социальная сеть, как основа современной культуры Типология современных радиостанций
Типология современных радиостанций Об'єктно-орієнтований аналіз
Об'єктно-орієнтований аналіз Формулы в электронных таблицах. Тест
Формулы в электронных таблицах. Тест RAM, ROM and Virtual memory
RAM, ROM and Virtual memory Четыре основных типа запросов данных в SQL
Четыре основных типа запросов данных в SQL Тема: Базы данных
Тема: Базы данных Сведения о языке программирования Паскаль
Сведения о языке программирования Паскаль Курс по основам программирования на Python. Функции
Курс по основам программирования на Python. Функции Фриланс, как форма занятности
Фриланс, как форма занятности Представление графической информации. Виды графики
Представление графической информации. Виды графики Защита информации в базах данных
Защита информации в базах данных Виды профессиональной информационной деятельности человека с использованием технических средств и информационных ресурсов
Виды профессиональной информационной деятельности человека с использованием технических средств и информационных ресурсов Техзадание к сайту
Техзадание к сайту Формализация понятия алгоритма
Формализация понятия алгоритма Компьютерная графика. Борьба с шумом изображений. (Лекция 5)
Компьютерная графика. Борьба с шумом изображений. (Лекция 5) Безопасный интернет
Безопасный интернет Браузер. Кем и когда создан
Браузер. Кем и когда создан Етапи побудови інформаційної моделі. Побудова інформаційних моделей. 7 клас
Етапи побудови інформаційної моделі. Побудова інформаційних моделей. 7 клас Deployment techniques for LabVIEW™ Applications
Deployment techniques for LabVIEW™ Applications The Great Alone Audiobook for Free Download
The Great Alone Audiobook for Free Download Разработка программного средства Портфолио студента
Разработка программного средства Портфолио студента Презентация Основы работы в векторном редакторе Corel Draw 11. Графические эффекты.
Презентация Основы работы в векторном редакторе Corel Draw 11. Графические эффекты. Introduction to spring framework and dependency injection
Introduction to spring framework and dependency injection Безопасность в Интернете
Безопасность в Интернете