Содержание
- 2. 1 Understanding Defense Explain approaches to network security defense. Explain how the defense-in-depth strategy is used
- 3. Understanding Defense
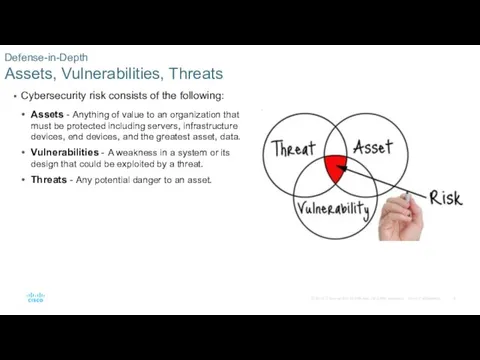
- 4. Cybersecurity risk consists of the following: Assets - Anything of value to an organization that must
- 5. Many organizations only have a general idea of the assets that need to be protected. All
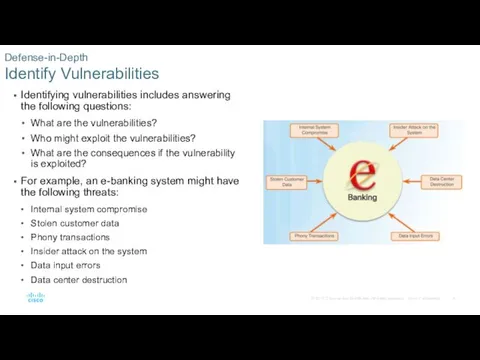
- 6. Identifying vulnerabilities includes answering the following questions: What are the vulnerabilities? Who might exploit the vulnerabilities?
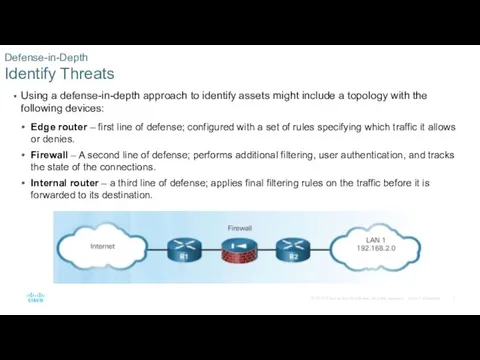
- 7. Using a defense-in-depth approach to identify assets might include a topology with the following devices: Edge
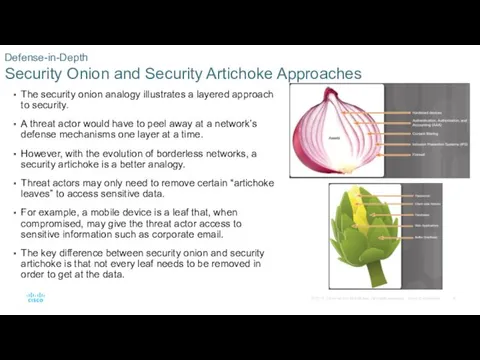
- 8. The security onion analogy illustrates a layered approach to security. A threat actor would have to
- 9. Policies provide the foundation for network security by defining what is acceptable. Business policies are the
- 10. A comprehensive security policy has a number of benefits: Demonstrates an organization’s commitment to security. Sets
- 11. Many organizations support Bring Your Own Device (BYOD), which enables employees to use their own mobile
- 12. The following BYOD security best practices help mitigate BYOD risks: Password protected access for each device
- 13. Compliance regulations and standards define what organizations are responsible for providing, and the liability if they
- 14. Access Control
- 15. Access Control Concepts Communications Security: CIA Information security deals with protecting information and information systems from
- 16. Access Control Concepts Access Control Models Basic access control models include the following: Mandatory access control
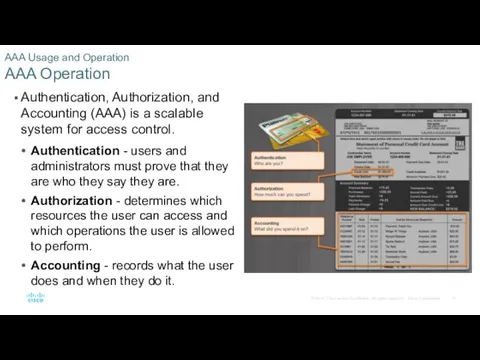
- 17. AAA Usage and Operation AAA Operation Authentication, Authorization, and Accounting (AAA) is a scalable system for
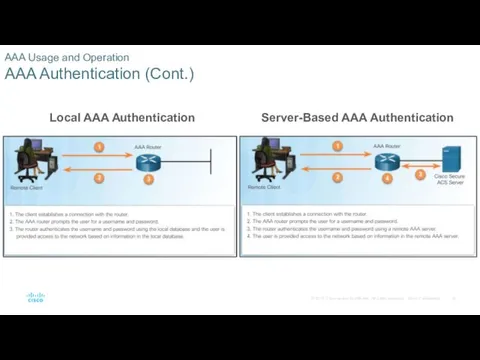
- 18. AAA Usage and Operation AAA Authentication Two common AAA authentication methods include: Local AAA Authentication -
- 19. AAA Usage and Operation AAA Authentication (Cont.) Local AAA Authentication Server-Based AAA Authentication
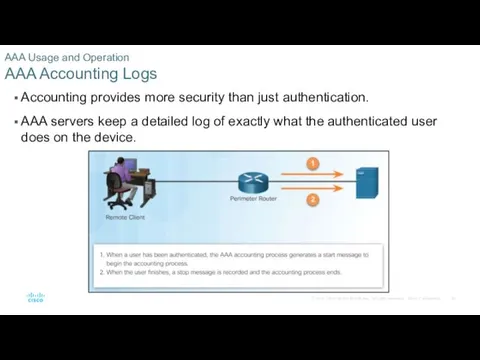
- 20. AAA Usage and Operation AAA Accounting Logs Accounting provides more security than just authentication. AAA servers
- 21. AAA Usage and Operation AAA Accounting Logs (Cont.) The various types of accounting information that can
- 22. Threat Intelligence
- 23. Information Sources Network Intelligence Communities Threat intelligence organizations such as CERT, SANS, and MITRE offer detailed
- 24. Information Sources Cisco Cybersecurity Reports Cisco offers their Cybersecurity Report annually, which provides an update on
- 25. Information Sources Security Blogs and Podcasts Security blogs and podcasts help cybersecurity professionals understand and mitigate
- 26. Threat Intelligence Services Cisco Talos Threat intelligence services allow the exchange of threat information such as
- 27. Threat Intelligence Services FireEye FireEye is another security company that offers services to help enterprises secure
- 28. Threat Intelligence Services Automated Indicator Sharing Automated Indicator Sharing (AIS) is program which allows the U.S.
- 29. Threat Intelligence Services Common Vulnerabilities and Exposures Database Common Vulnerabilities and Exposures (CVE) is a database
- 30. Threat Intelligence Services Threat Intelligence Communication Standards Cyber Threat Intelligence (CTI) standards such as STIX and
- 31. Summary
- 32. Summary Cybersecurity risk consists of assets, vulnerabilities, and threats. Assets constitute the attack surface that threat
- 33. Summary (Cont.) A BYOD policy, which enables employees to use their own mobile devices to access
- 34. Summary (Cont.) AAA access control includes the authentication, authorization, and accounting. Two common authentication methods are
- 35. Summary (Cont.) Threat intelligence organizations such as CERT, SANS, and MITRE offer detailed threat information that
- 37. Скачать презентацию
























 Реферирование. Виды аналитико-синтетической переработки информации. (Лекция 1)
Реферирование. Виды аналитико-синтетической переработки информации. (Лекция 1) Применение программного обеспечения компьютера в подготовке фрагментов уроков по предмету Технология.
Применение программного обеспечения компьютера в подготовке фрагментов уроков по предмету Технология. Информация и информационные процессы
Информация и информационные процессы Деловая графика
Деловая графика Изображение
Изображение Алгоритм и его свойства
Алгоритм и его свойства Руководство пользователя DiagSmart
Руководство пользователя DiagSmart Input device
Input device Наукометричні міжнародні бази даних
Наукометричні міжнародні бази даних Программирование на языке Python. §54. Алгоритм и его свойства
Программирование на языке Python. §54. Алгоритм и его свойства Компьютерные сети. Адресация. Тема 6
Компьютерные сети. Адресация. Тема 6 Программирование на языке C++
Программирование на языке C++ Overview of apps and web sites for language learning
Overview of apps and web sites for language learning Data Modeling and Databases II
Data Modeling and Databases II Представление числовой информации с помощью систем счисления
Представление числовой информации с помощью систем счисления Основные виды обеспечения вычислительной системы
Основные виды обеспечения вычислительной системы Глобальная компьютерная сеть
Глобальная компьютерная сеть IP – адреса и маски подсети
IP – адреса и маски подсети Циклы For и While
Циклы For и While Заседание комиссии при Правительстве Оренбургской области: использование информационных технологий в деятельности органов власти
Заседание комиссии при Правительстве Оренбургской области: использование информационных технологий в деятельности органов власти Интернет и дети
Интернет и дети Информация и её свойства. Информация и информационные процессы. Информатика. 7 класс
Информация и её свойства. Информация и информационные процессы. Информатика. 7 класс Инструменты анализа данных. Табличный процессор. Основные сведения
Инструменты анализа данных. Табличный процессор. Основные сведения Polimorfizm
Polimorfizm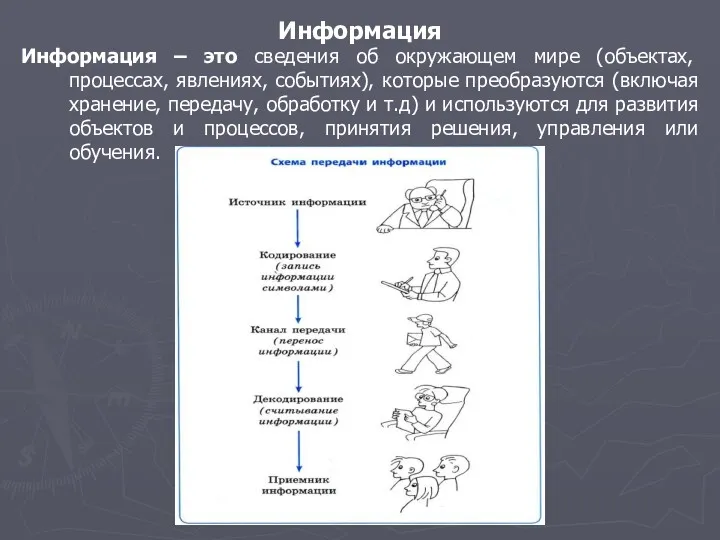 Системы счисления и кодирование информации
Системы счисления и кодирование информации Код Хэмминга. Пример работы алгоритма
Код Хэмминга. Пример работы алгоритма Моделирование систем. Лекция 2
Моделирование систем. Лекция 2 Управление в логистических информационных системах (Информационные системы планирования и управления ресурсами предприятия)
Управление в логистических информационных системах (Информационные системы планирования и управления ресурсами предприятия)