Содержание
- 2. Introduction What is SQL Injection? Real World Examples Important SQL Syntax Example Website Prevention
- 3. What is SQL Injection? Code Injection Technique Exploits Security Vulnerability Targets User Input Handlers
- 4. Real World Examples On August 17, 2009, the United States Justice Department charged an American citizen
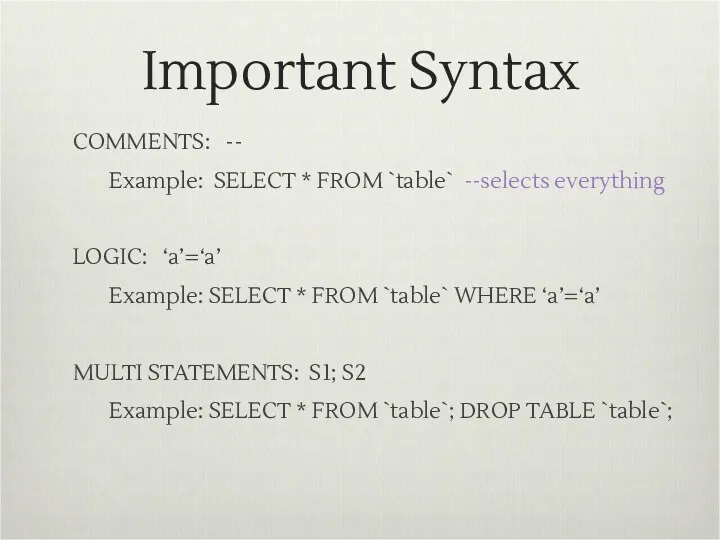
- 5. Important Syntax COMMENTS: -- Example: SELECT * FROM `table` --selects everything LOGIC: ‘a’=‘a’ Example: SELECT *
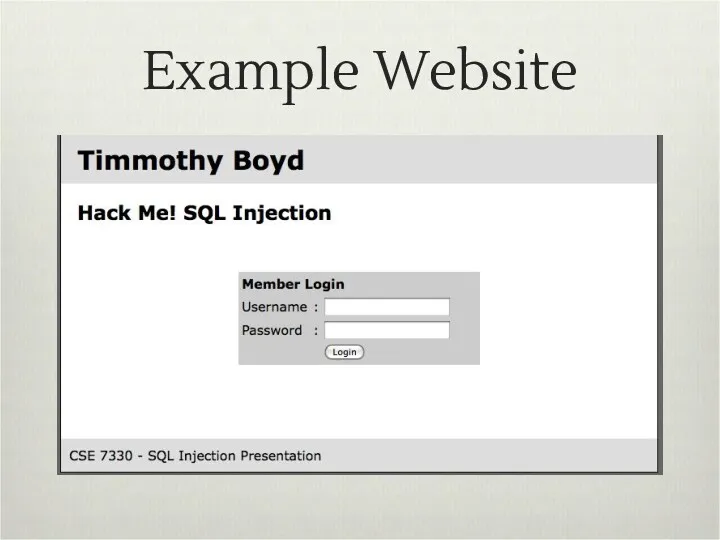
- 6. Example Website
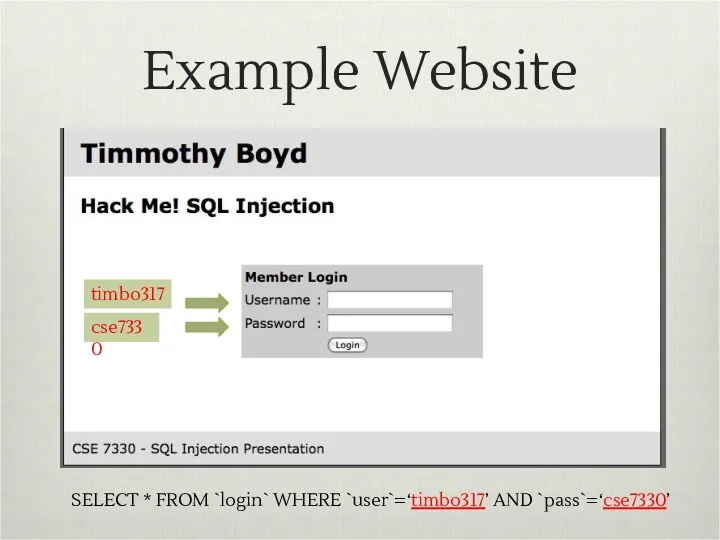
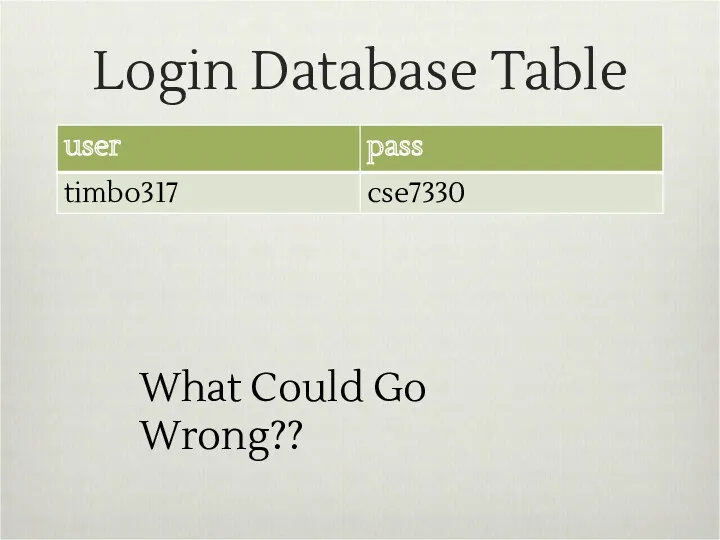
- 8. Example Website timbo317 cse7330 SELECT * FROM `login` WHERE `user`=‘timbo317’ AND `pass`=‘cse7330’
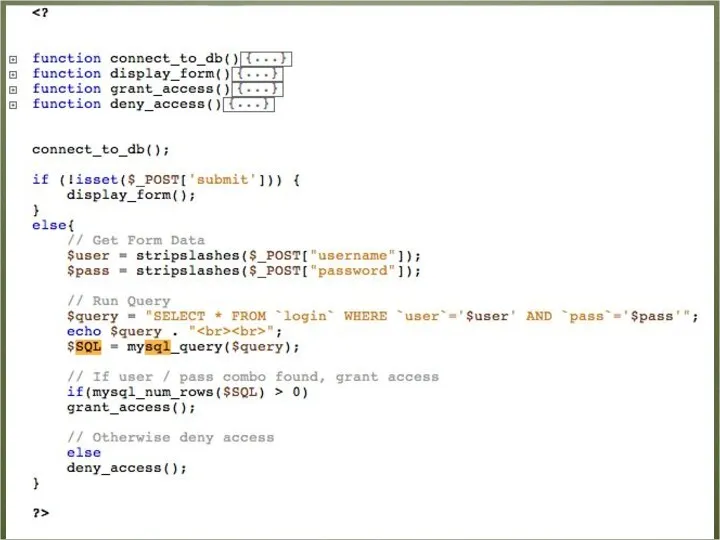
- 9. Login Database Table What Could Go Wrong??
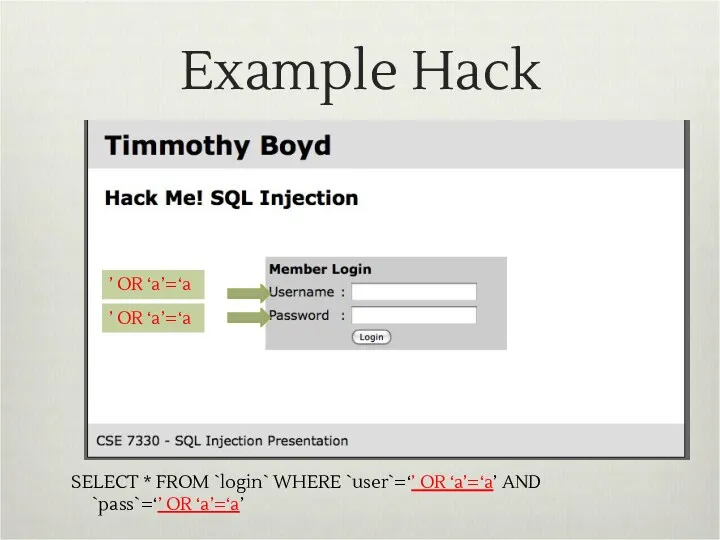
- 10. Example Hack ’ OR ‘a’=‘a ’ OR ‘a’=‘a SELECT * FROM `login` WHERE `user`=‘’ OR ‘a’=‘a’
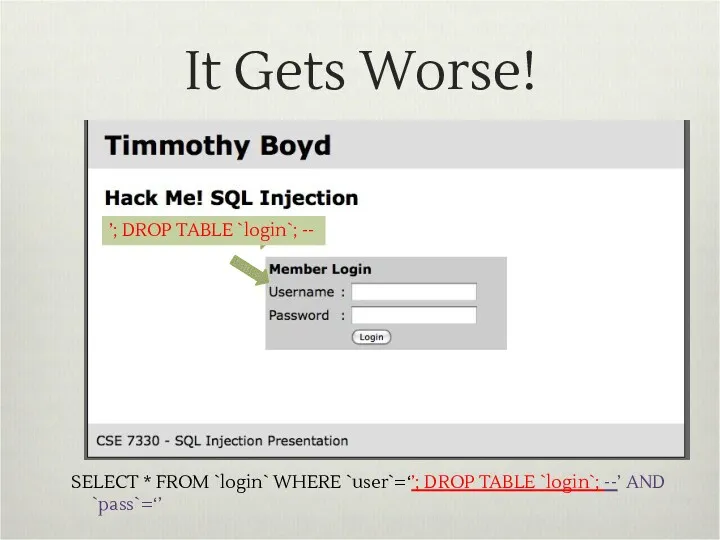
- 11. It Gets Worse! ’; DROP TABLE `login`; -- SELECT * FROM `login` WHERE `user`=‘’; DROP TABLE
- 12. All Queries are Possible SELECT * FROM `login` WHERE `user`=‘’; INSERT INTO `login` ('user','pass') VALUES ('haxor','whatever');--’
- 13. Live Demonstration http://www.timmothyboyd.com/cse7330 How Can You Prevent This??
- 14. Prevention Logic to allow only numbers / letters in username and password. How should you enforce
- 16. Скачать презентацию





 Основы алгоритмизации и программирования
Основы алгоритмизации и программирования Третий-лишний. Назовите лишнее высказывание
Третий-лишний. Назовите лишнее высказывание Устройство компьютерной сети. (Лекция 1)
Устройство компьютерной сети. (Лекция 1) Microsoft Paint - Windows жүйесінің стандартты программалар тобына кіретін қарапайым нүктелік графикалық редактор
Microsoft Paint - Windows жүйесінің стандартты программалар тобына кіретін қарапайым нүктелік графикалық редактор Текстовые редакторы
Текстовые редакторы Классификация информационных систем
Классификация информационных систем Тест по теме Количество информации
Тест по теме Количество информации Робототехніка на основі Arduino
Робототехніка на основі Arduino Затенение и тонирование
Затенение и тонирование Системы счисления
Системы счисления Python
Python ООП простыми словами. (Лекция 2)
ООП простыми словами. (Лекция 2) Обеспечение целостности БД
Обеспечение целостности БД Беспроводные сети
Беспроводные сети Создание и обработка графической информации. Практическое занятие № 5
Создание и обработка графической информации. Практическое занятие № 5 HTML5. Семантика
HTML5. Семантика Организация учета доступа к сети Интернет
Организация учета доступа к сети Интернет Следуя командам
Следуя командам Алгоритмы. Линейный алгоритм
Алгоритмы. Линейный алгоритм Простейшая программа на С
Простейшая программа на С Библиографическое описание для составления списка литературы
Библиографическое описание для составления списка литературы Алгоритмы поиска. Поиск в линейных структурах
Алгоритмы поиска. Поиск в линейных структурах Суперкомпьютеры Intel
Суперкомпьютеры Intel Графічний інтерфейс ОС Windows
Графічний інтерфейс ОС Windows Понятия истина и ложь. 2 класс
Понятия истина и ложь. 2 класс Разработка базы данных Магазин
Разработка базы данных Магазин 1С:ERP Управление предприятием 2.0. Оптимизация обновления информационной базы
1С:ERP Управление предприятием 2.0. Оптимизация обновления информационной базы Управление файловой системой
Управление файловой системой