Содержание
- 2. Test questions 1 1. Definition and purpose of transactions. 2. Transaction properties. 3. Describe transaction concurrency
- 3. Contents: The concept of transaction Transaction properties and commands Transaction mix and launch schedule Transaction Concurrency
- 4. The concept of transaction • Transaction is an indivisible sequence of data manipulation operations in terms
- 5. Roll back: Transactions are units of data recovery after failures - during recovery, the system eliminates
- 6. 2. Transaction properties and commands ACID Properties: (A) Atomicity . A transaction is done as an
- 7. Base integrity violation example Inserting a new employee into the table does not can be performed
- 8. Transactions and SQL The transaction starts automatically from the moment the user joins the database and
- 9. Transaction mix A transaction is considered as a sequence of elementary atomic operations. The atomicity of
- 10. Definition 1. A set of several transactions whose elementary operations alternate with each other is called
- 11. 4. Transaction Concurrency Issues How can transactions of different users interfere with each other? There are
- 12. Designations Consider two transactions A and B, starting in accordance with some schedules. Let transactions work
- 13. Lost update problem Two transactions take turns writing some data on the same row and committing
- 14. Uncommitted dependency (dirty reading) Transaction B modifies the data in the row. After that, transaction A
- 15. Uncommitted dependency (dirty reading) Result. Transaction A in its work used data that is not in
- 16. The problem of incompatible analysis Unrepeatable reading. Fictitious elements (phantoms). Actually incompatible analysis.
- 17. Unrepeatable reading Transaction A reads the same row twice. Between these readings, transaction B wedges in,
- 18. Unrepeatable reading Transaction A knows nothing about the existence of transaction B, and since it does
- 19. Fictitious elements (phantoms) Transaction A selects rows with the same conditions twice. Transaction B wedges between
- 20. Actually incompatible analysis The mixture contains two transactions - one long, the other short. A long
- 21. Actually incompatible analysis Result. Although transaction B did everything right - the money was transferred without
- 22. Competing transactions An analysis of the problems of concurrency shows that if no special measures are
- 23. Conflicts between transactions As a result of competition for data between transactions, there is a Access
- 24. Test questions1 1. Definition and purpose of transactions. 2. Transaction properties. 3. Describe transaction concurrency issues:
- 25. Test questions2 1. Describe ways to solve transaction concurrency issues using locks. 2. Describe the algorithm
- 26. METHODS FOR SOLVING TRANSACTION CONCURRENCY ISSUES
- 27. How to resolve competition Since transactions do not interfere with each other if they access different
- 28. Locks There are two types of locks: Exclusive locks (X-locks) - locks without mutual access (write
- 29. Data access protocol Before reading an object, a transaction must impose an S-lock on this object.
- 30. Solving transaction concurrency issues Loss update problem Two transactions take turns writing some data on the
- 31. Uncommitted dependency problem (dirty reading) Transaction B modifies the data in the row. After that, transaction
- 32. Unrepeatable reading Transaction A reads the same row twice. Between these readings, transaction B wedges in,
- 33. The problem of incompatible analysis Fictitious elements (phantoms) Transaction A selects rows with the same conditions
- 34. Actually incompatible analysis The effect of the incompatible aalysis itself is also different from previous examples
- 35. Actually incompatible analysis Result. Both transactions are waiting for each other and cannot continue. There was
- 36. Problem analysis Loss update problem - There was a deadlock situation. Uncommitted dependency problem (dirty reading)
- 37. Because there is no normal way out of the deadlock situation, then such a situation needs
- 38. Two approaches for choosing a victim The DBMS does not monitor the occurrence of deadlocks. Transactions
- 39. Two-phase transaction confirmation In distributed systems, committing transactions may require the interaction of several processes on
- 40. TRANSACTIONS AND DATA RECOVERY
- 41. After the system fails, the subsequent launch analyzes the transactions that were performed before the transaction
- 42. Data durability The requirement of data durability (one of the properties of transactions) is that the
- 43. Types of failures Individual transaction rollback. It can be initiated either by the transaction itself using
- 44. Transaction log In all three cases, the basis of recovery is the redundancy of data provided
- 45. Logging Database pages whose contents in the buffer (in RAM) are different from the contents on
- 46. Save checkpoint Additional condition for pushing buffers: Each successfully completed transaction must be actually saved in
- 47. Individual transaction rollback In order to be able to perform an individual rollback of a transaction
- 48. Individual transaction rollback (algorithm) 1. A list of records made by a given transaction in the
- 49. Recovering from a mild failure After a mild failure, not all physical database pages contain changed
- 51. Recovering from a mild failure The last checkpoint was taken at time tc. A mild system
- 52. Recovering from a mild failure T4. The transaction started after the adoption of the checkpoint and
- 53. Recovering from a hard system failure If a hard failure occurs, the database on the disk
- 54. Test questions2 1. Describe ways to solve transaction concurrency issues using locks. 2. Describe the algorithm
- 56. Скачать презентацию
 Анықталған интегралдың қолданылуы
Анықталған интегралдың қолданылуы Основные понятия в области метрологии. Метрология в прошлом и настоящем (урок 01.06)
Основные понятия в области метрологии. Метрология в прошлом и настоящем (урок 01.06) Знакомство с задачей.
Знакомство с задачей. Стереометрия. Аксиомы стереометрии
Стереометрия. Аксиомы стереометрии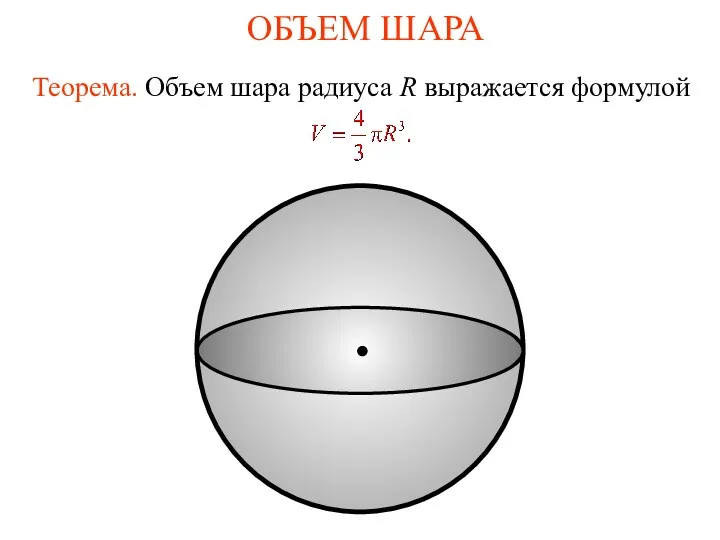 Объем шара
Объем шара Сложение чисел с помощью координатной прямой. Демонстрационный материал. 6 класс
Сложение чисел с помощью координатной прямой. Демонстрационный материал. 6 класс Виды углов
Виды углов Winston p. 313
Winston p. 313 Что узнали и чему научились. Математика, 4 класс
Что узнали и чему научились. Математика, 4 класс Развивающее занятие Геометрические фигуры
Развивающее занятие Геометрические фигуры Урок с применением ИКТ
Урок с применением ИКТ Главные направления линии второго порядка
Главные направления линии второго порядка Арифметическая прогрессия
Арифметическая прогрессия Тела вращения. Цилиндр и конус
Тела вращения. Цилиндр и конус Абсолютные и относительные статистические величины
Абсолютные и относительные статистические величины Интегрированный урок: математика + биология. Простые и сложные листья
Интегрированный урок: математика + биология. Простые и сложные листья Занимательная математика
Занимательная математика Учимся писать цифры от 0 до 9
Учимся писать цифры от 0 до 9 Логарифмик тигезләмәләр һәм тигезсезлекләр чишү юллары. БДИга әзерлек
Логарифмик тигезләмәләр һәм тигезсезлекләр чишү юллары. БДИга әзерлек Задачи на разрезание фигур
Задачи на разрезание фигур Вычитание однозначного числа из круглого десятка.
Вычитание однозначного числа из круглого десятка. Метод алгебраического сложения. Алгебра 7 класс
Метод алгебраического сложения. Алгебра 7 класс Показатели вариации, для изучения величины отклонений
Показатели вариации, для изучения величины отклонений Изменение величин
Изменение величин Линейная функция и её график
Линейная функция и её график Вписанные и описанные тела
Вписанные и описанные тела Презентация к уроку математики (2 класс) Тема урока - Деление.
Презентация к уроку математики (2 класс) Тема урока - Деление. Формулы сокращенного умножения
Формулы сокращенного умножения