Слайд 2

Cyber crime
In the start of 21 century, the new era started.
The era of technologies.
However, with technologies, new types of crime developed.
Слайд 3

Hacking
Nowadays, a major concern that has emerged among computer or smartphone
users is the threat of hacking. Hackers can easily hack the security systems, bank systems, any program and earn a lot of money.
Слайд 4

Hacking
For example, hacking mobile phones has become a real business in
Russia, Asia, and other places where pre-paid phone calls are common. Analytics estimated that criminals, hackers who target mobile phones earn from $1000 to $5000 per day per person.
Слайд 5

Hacking
There are four forms of attacks commonly used against computers and
networks, according to Aaron Turpen, in his article ‘Hacker Prevention Techniques.’
Слайд 6
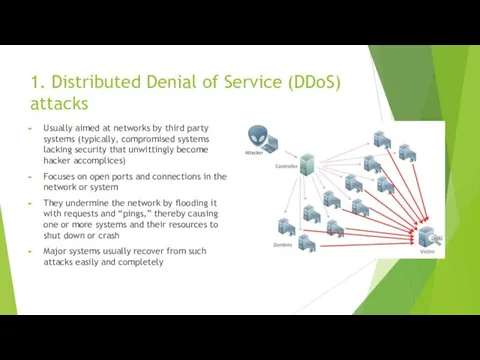
1. Distributed Denial of Service (DDoS) attacks
Usually aimed at networks by
third party systems (typically, compromised systems lacking security that unwittingly become hacker accomplices)
Focuses on open ports and connections in the network or system
They undermine the network by flooding it with requests and “pings,” thereby causing one or more systems and their resources to shut down or crash
Major systems usually recover from such attacks easily and completely
Слайд 7

2. Trojan Horse
Software disguised as something else (typically useful shareware or
freeware) and so are installed in your system consciously
It either contains
- a “back door,” (which allows others to enter your system, and do what they want with it, while you’re using the software), or
- a “trigger,” (sets itself off when triggered, either by a date or a time or a series of events, etc., and cause your system to shut down or attack other computers; can be part of a DDoS attack
Difficult to detect
Слайд 8

3. Virus
Most common
Primary concern is to replicate and spread itself, and
then destroy or attempt an attack on the host system
Слайд 9

4.Worm
A combination of a DDoS and a virus attack
Usually reproduces as
often as possible to spread as widely as they can
Commonly aimed at larger systems (mainframes, corporate networks, etc.); some are built to “consume” data and filter it back out to unauthorized users (i.e. corporate spies)
It consumes resources (quietly) until the system finally becomes overloaded and ceases to function
Слайд 10
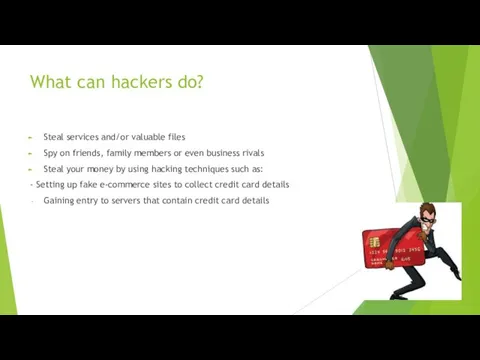
What can hackers do?
Steal services and/or valuable files
Spy on friends, family
members or even business rivals
Steal your money by using hacking techniques such as:
- Setting up fake e-commerce sites to collect credit card details
Gaining entry to servers that contain credit card details
Слайд 11











 Числовая последовательность
Числовая последовательность Сальвадор Дали
Сальвадор Дали От Пионерии до Города Мастеров. Летопись районной пионерской организации
От Пионерии до Города Мастеров. Летопись районной пионерской организации Электроизмерительные приборы. 8 класс
Электроизмерительные приборы. 8 класс Самообразование Развитие творческих способностей у детей 4-5 лет
Самообразование Развитие творческих способностей у детей 4-5 лет Открытый банк заданий ЕГЭ по математике
Открытый банк заданий ЕГЭ по математике Технология приготовления напитков
Технология приготовления напитков Презентация Откуда берется хлеб
Презентация Откуда берется хлеб Виды транспорта
Виды транспорта Система оценки планируемых образовательных результатов в условиях реализации ФГОС НОО.
Система оценки планируемых образовательных результатов в условиях реализации ФГОС НОО. Музыкальная физкультминутка Веселая зарядка для 1 - 4 классов
Музыкальная физкультминутка Веселая зарядка для 1 - 4 классов Промышленная теплоэнергетика. Классификация и основные показатели тепловых электрических станций. (Занятие 15)
Промышленная теплоэнергетика. Классификация и основные показатели тепловых электрических станций. (Занятие 15) Биостимуляторы. Гиполипидемические средства
Биостимуляторы. Гиполипидемические средства Теоретические основы электротехники
Теоретические основы электротехники Работа с пластилином
Работа с пластилином Презентация к уроку Фосфор
Презентация к уроку Фосфор Взаимосвязь между величинами: цена, количество, стоимость
Взаимосвязь между величинами: цена, количество, стоимость Сборник материалов для родителей Школа заботливых родителей
Сборник материалов для родителей Школа заботливых родителей Презентация дополнительной образовательной программы хореографического коллектива Сияние
Презентация дополнительной образовательной программы хореографического коллектива Сияние Securitization and credit crises
Securitization and credit crises 20231119_signalnye_kartochki_5_uproshchenie
20231119_signalnye_kartochki_5_uproshchenie Житие Сергия Радонежского
Житие Сергия Радонежского Входные устройства РПУ
Входные устройства РПУ Физкультминутки, как элемент здоровьесберегающих технологий в начальной школе.
Физкультминутки, как элемент здоровьесберегающих технологий в начальной школе. ''Инновационные технологии в формировании познавательной активности младших школьников в рамках ФГОС''
''Инновационные технологии в формировании познавательной активности младших школьников в рамках ФГОС'' Активные методы обучения персонала
Активные методы обучения персонала М.Ю.Лермонтова Мцыри. Контрольная работа по поэме
М.Ю.Лермонтова Мцыри. Контрольная работа по поэме презентация для самообразования учителей о Кембриджской Программе внедрения семи модулей, как Новых подходах в воспитании и обучении детей.
презентация для самообразования учителей о Кембриджской Программе внедрения семи модулей, как Новых подходах в воспитании и обучении детей.