Содержание
- 2. Service Master Key Root – Top Level Key – symmetric key One Service Master key per
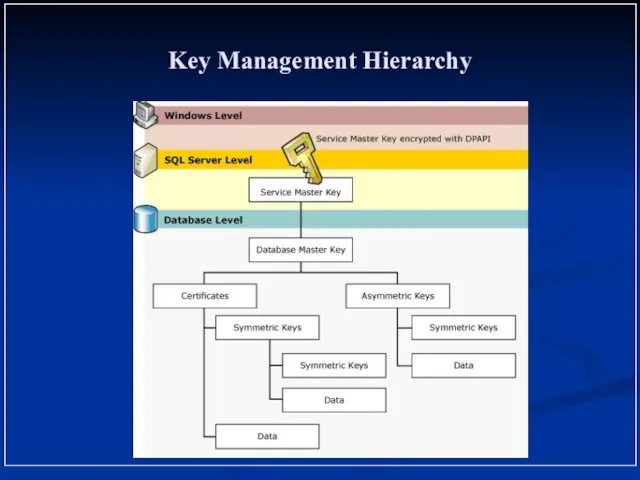
- 3. Key Management Hierarchy Key Management Hierarchy Database Master Keys Symmetric key One Database Master key per
- 4. Key Management Hierarchy
- 5. MS SQL Server Protecting Password Avoid storing passwords if possible Use LDAP or Active Directory is
- 6. MS SQL Server Checklist Use either the AES192 or AES256 algorithm Use randomly generated keys and
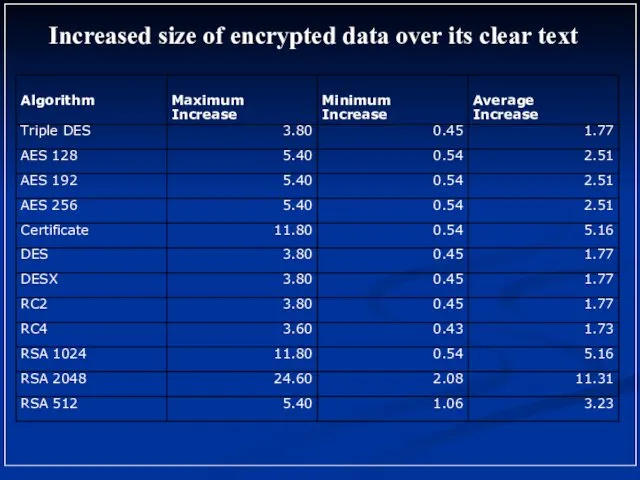
- 7. Increased size of encrypted data over its clear text
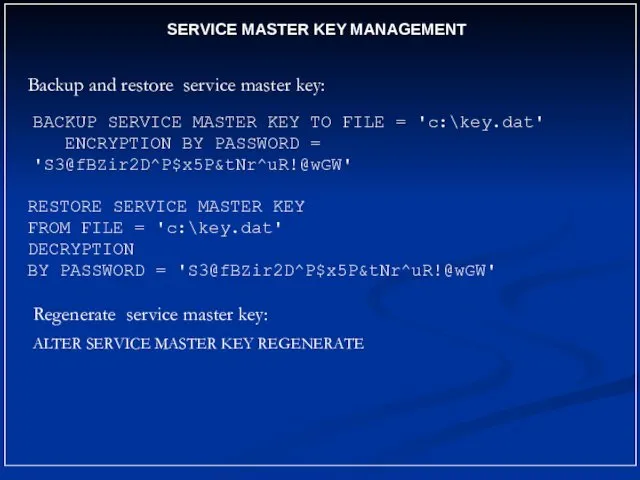
- 8. SERVICE MASTER KEY MANAGEMENT Backup and restore service master key: BACKUP SERVICE MASTER KEY TO FILE
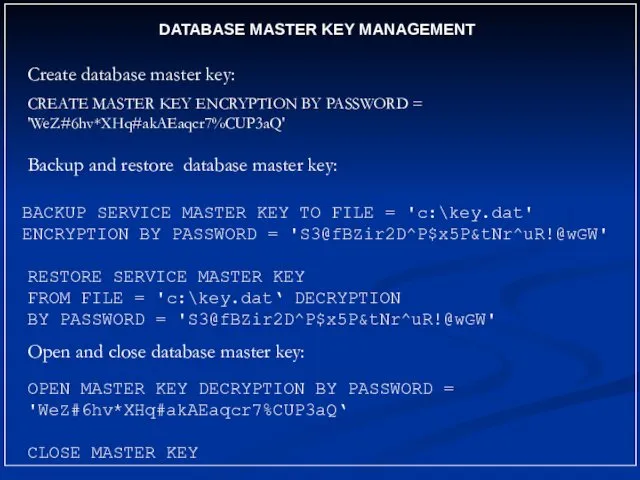
- 9. DATABASE MASTER KEY MANAGEMENT Backup and restore database master key: BACKUP SERVICE MASTER KEY TO FILE
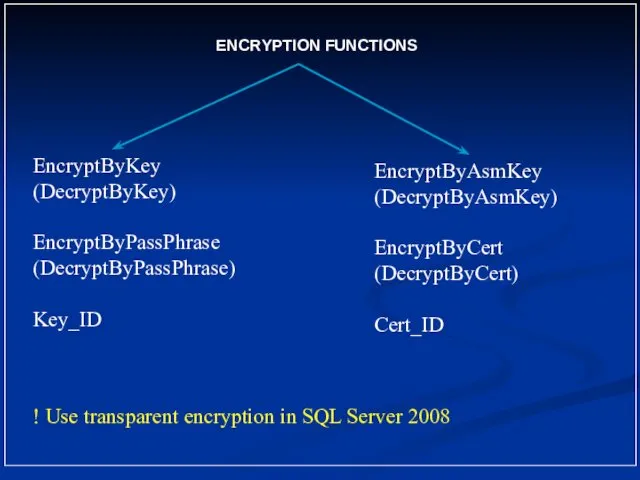
- 10. ENCRYPTION FUNCTIONS EncryptByKey (DecryptByKey) EncryptByPassPhrase (DecryptByPassPhrase) Key_ID EncryptByAsmKey (DecryptByAsmKey) EncryptByCert (DecryptByCert) Cert_ID ! Use transparent encryption
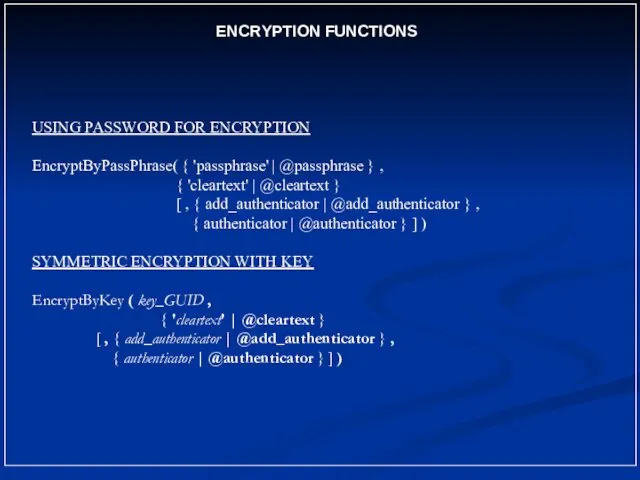
- 11. ENCRYPTION FUNCTIONS USING PASSWORD FOR ENCRYPTION EncryptByPassPhrase( { 'passphrase' | @passphrase } , { 'cleartext' |
- 12. Encryption for Oracle 8i-11g Oracle DBMS Obfuscation Toolkit (DOTK) (Only option for older Oracle 8g &
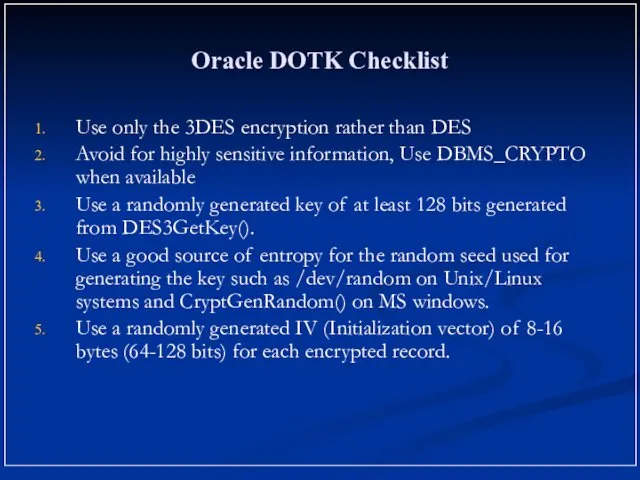
- 13. Oracle DOTK Checklist Use only the 3DES encryption rather than DES Avoid for highly sensitive information,
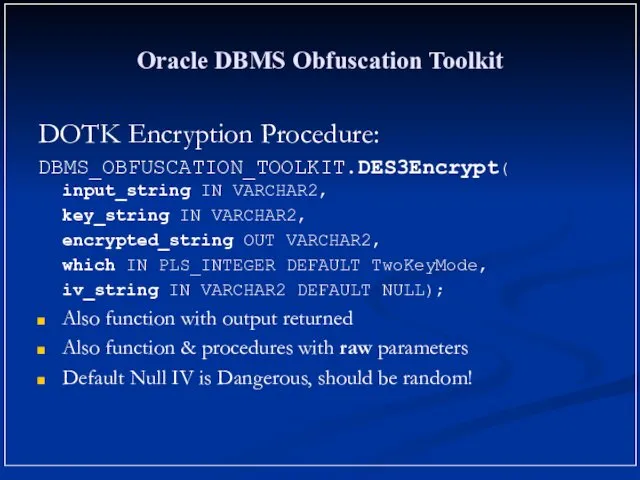
- 14. Oracle DBMS Obfuscation Toolkit DOTK Encryption Procedure: DBMS_OBFUSCATION_TOOLKIT.DES3Encrypt( input_string IN VARCHAR2, key_string IN VARCHAR2, encrypted_string OUT
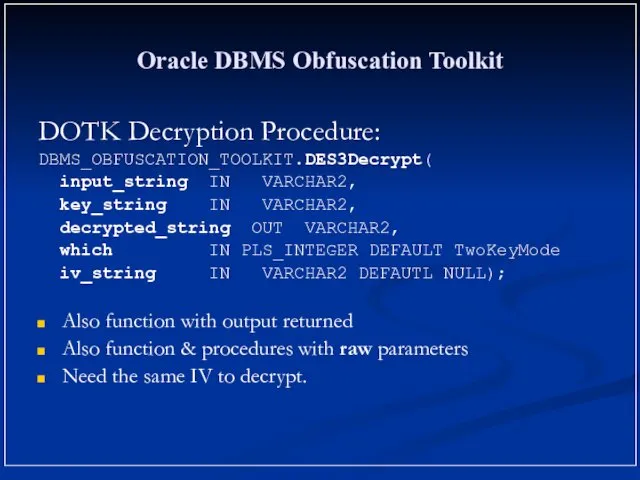
- 15. Oracle DBMS Obfuscation Toolkit DOTK Decryption Procedure: DBMS_OBFUSCATION_TOOLKIT.DES3Decrypt( input_string IN VARCHAR2, key_string IN VARCHAR2, decrypted_string OUT
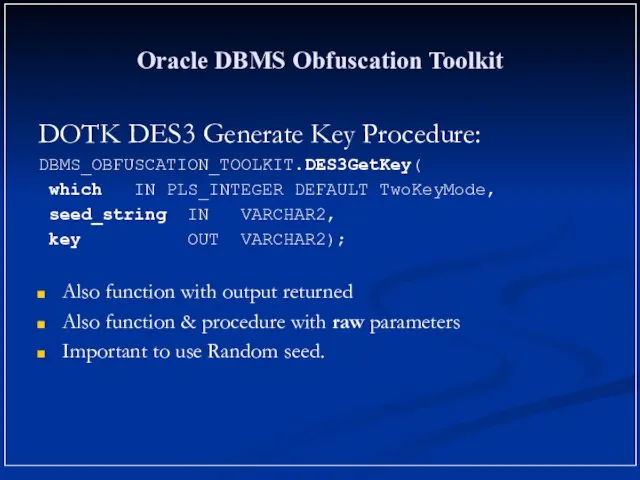
- 16. Oracle DBMS Obfuscation Toolkit DOTK DES3 Generate Key Procedure: DBMS_OBFUSCATION_TOOLKIT.DES3GetKey( which IN PLS_INTEGER DEFAULT TwoKeyMode, seed_string
- 17. Oracle DBMS Crypto Checklist Use either the AES192 or AES256 algorithm Use DBMS_CRYPTO.RANDOMBYTES() to generate random
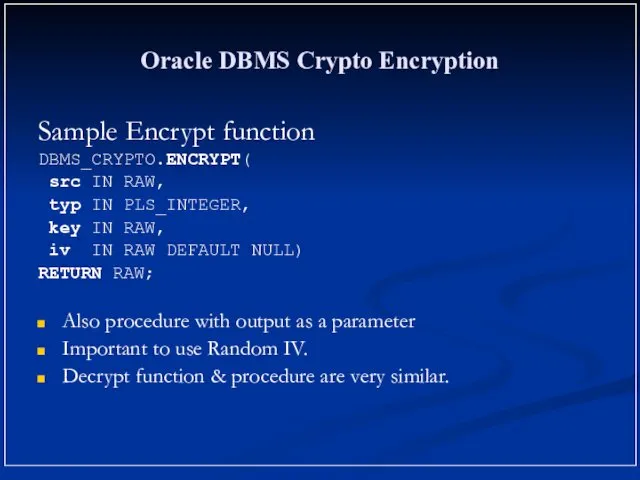
- 18. Oracle DBMS Crypto Encryption Sample Encrypt function DBMS_CRYPTO.ENCRYPT( src IN RAW, typ IN PLS_INTEGER, key IN
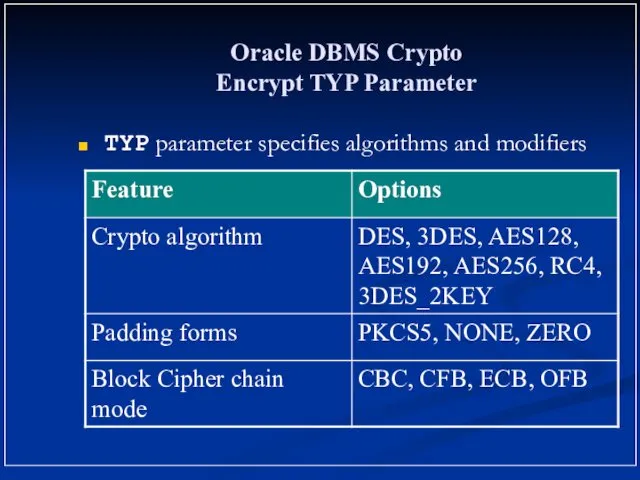
- 19. Oracle DBMS Crypto Encrypt TYP Parameter TYP parameter specifies algorithms and modifiers
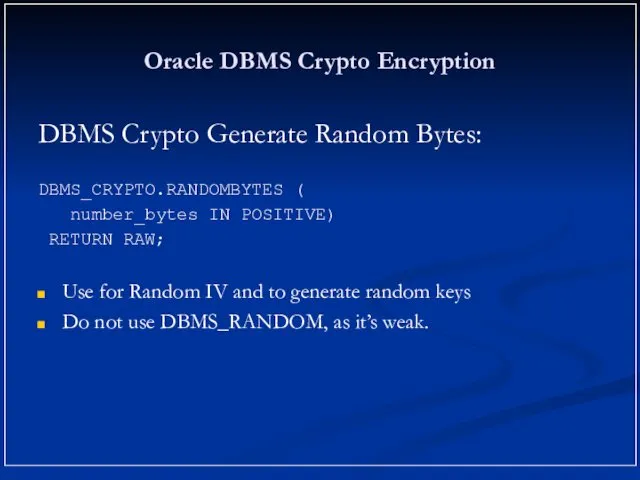
- 20. Oracle DBMS Crypto Encryption DBMS Crypto Generate Random Bytes: DBMS_CRYPTO.RANDOMBYTES ( number_bytes IN POSITIVE) RETURN RAW;
- 22. Скачать презентацию






 12 апреля. День космонавтики.
12 апреля. День космонавтики. Financier - is a specialist managing money
Financier - is a specialist managing money Аппликация кораблик. Поэтапное изготовление
Аппликация кораблик. Поэтапное изготовление Проходження практики на підприємстві Оризон-Навігація
Проходження практики на підприємстві Оризон-Навігація Взаимное расположение прямой и окружности на плоскости
Взаимное расположение прямой и окружности на плоскости Меланин түзуші ұлпаның,жүйке ұлпасының ісіктері,күрделі ісіктер
Меланин түзуші ұлпаның,жүйке ұлпасының ісіктері,күрделі ісіктер Урок по Географии Алтайского края 8 класс тема: Растительность Алтайского края
Урок по Географии Алтайского края 8 класс тема: Растительность Алтайского края Презентация к родительскому собранию Агрессия. Игры на снижение агрессии.
Презентация к родительскому собранию Агрессия. Игры на снижение агрессии. Объемные изображение в скульптуре
Объемные изображение в скульптуре Монтаж строительных конструкций
Монтаж строительных конструкций Вены большого круга кровообращения
Вены большого круга кровообращения Состояние травматизма в организациях Лысьвенского городского округа
Состояние травматизма в организациях Лысьвенского городского округа Исторические аспекты коррупции в России. Тема 2
Исторические аспекты коррупции в России. Тема 2 Автоматизация звука Ж (1-2 класс).
Автоматизация звука Ж (1-2 класс). Закупочная логистика. Сущность и задачи закупочной логистики
Закупочная логистика. Сущность и задачи закупочной логистики Трехфазные цепи переменного синусоидального тока
Трехфазные цепи переменного синусоидального тока Наиболее типичные заболевания и травмы в игровых видах спорта. Методика массажа
Наиболее типичные заболевания и травмы в игровых видах спорта. Методика массажа Выращивание кристаллов в домашних условиях
Выращивание кристаллов в домашних условиях Основные средства предприятия
Основные средства предприятия Баскетбол
Баскетбол Экономическая точность обработки. Методология разработки технологических процессов
Экономическая точность обработки. Методология разработки технологических процессов Презентация 38 1 группа
Презентация 38 1 группа Event-менеджмент
Event-менеджмент Биосфера Земли. Тест
Биосфера Земли. Тест Проектная деятельность в ДОУ
Проектная деятельность в ДОУ Презентация Здравствуй, лето! (Загадки)
Презентация Здравствуй, лето! (Загадки) Тренинг Искусство быть счастливой
Тренинг Искусство быть счастливой Основные понятия химии высокомолекулярных соединений (ВМС)
Основные понятия химии высокомолекулярных соединений (ВМС)