Type of access attack that attempts to manipulate individuals into performing
actions or divulging confidential information needed to access a network.
Examples of social engineering attacks include:
Pretexting - Calls an individual and lies to them in an attempt to gain access to privileged data. Pretends to need personal or financial data in order to confirm the identity of the recipient.
Spam - Use spam email to trick a user into clicking an infected link, or downloading an infected file.
Phishing - Common version is the threat actor sends enticing custom-targeted spam email to individuals with the hope the target user clicks on a link or downloads malicious code.
Something for Something (Quid pro quo) - Requests personal information from a party in exchange for something like a free gift.
Tailgating - Follows an authorized person with a corporate badge into a badge-secure location.
Baiting - Threat actor leaves a malware-infected physical device, such as a USB flash drive in a public location such as a corporate washroom. The finder finds the device and inserts it into their computer.
Visual hacking – Physically observes the victim entering credentials such as a workstation login, an ATM PIN, or the combination on a physical lock. Also known as “shoulder surfing”.
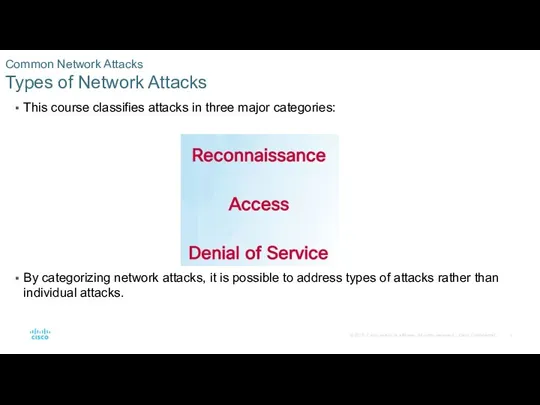
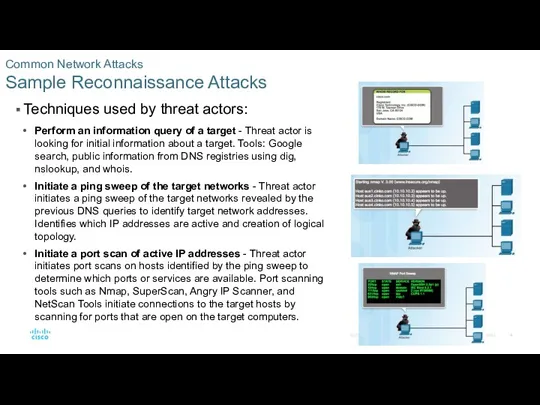
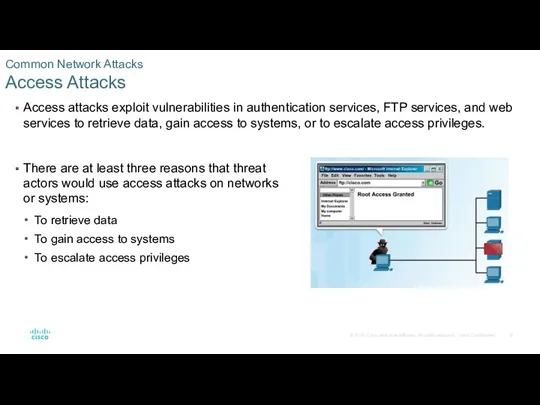
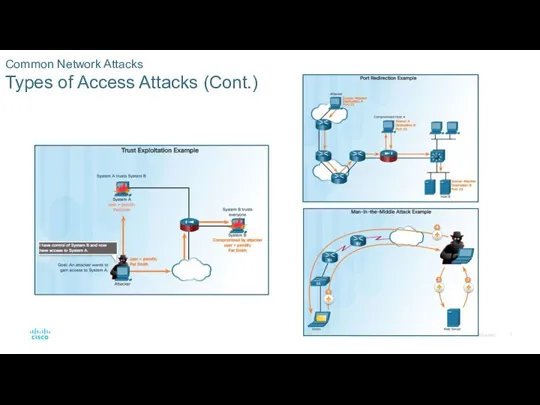
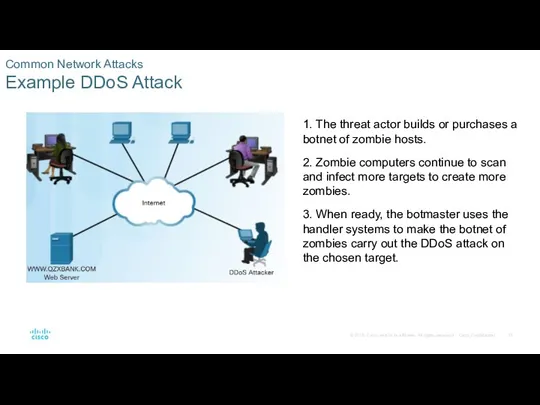
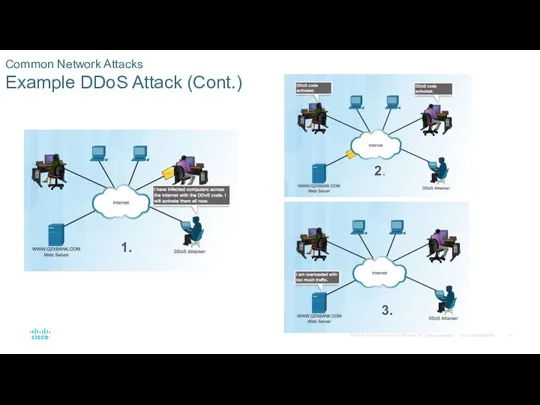
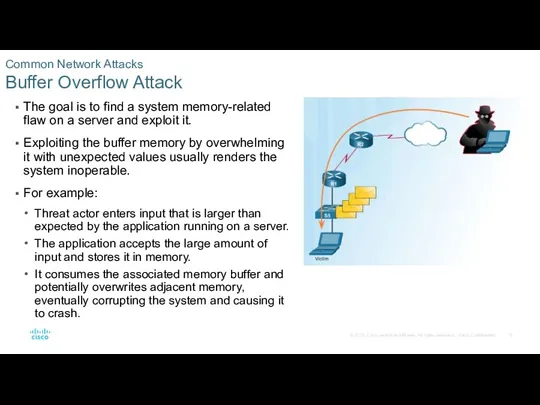
Common Network Attacks
Social Engineering Attacks







 Режимы и способы обработки данных
Режимы и способы обработки данных Компьютер – исполнитель алгоритмов
Компьютер – исполнитель алгоритмов Арифметические операции в позиционных системах счисления (4). 8 класс
Арифметические операции в позиционных системах счисления (4). 8 класс Теория формальных языков и трансляций. Магазинные автоматы. Глава 5
Теория формальных языков и трансляций. Магазинные автоматы. Глава 5 Работа с формулами. Организация вычислений в электронных таблицах
Работа с формулами. Организация вычислений в электронных таблицах Введение в ОС_7cf4f868-0df6-48ba-816e-1789eba5764d
Введение в ОС_7cf4f868-0df6-48ba-816e-1789eba5764d Понятие, как форма мышления
Понятие, как форма мышления Module 1: Introducing Siebel Applications
Module 1: Introducing Siebel Applications Хранимые процедуры
Хранимые процедуры Fyi letters
Fyi letters Компьютерные вирусы. Обзор и классификация компьютерных вирусов. Средства защиты от компьютерных вирусов
Компьютерные вирусы. Обзор и классификация компьютерных вирусов. Средства защиты от компьютерных вирусов Git (гит) - распределенная система управления версиями Think Results
Git (гит) - распределенная система управления версиями Think Results ИКТ – компетентность участников образовательного процесса
ИКТ – компетентность участников образовательного процесса Представление чисел в компьютере
Представление чисел в компьютере Структурирование информации и информационные модели. Подготовка к ЕГЭ
Структурирование информации и информационные модели. Подготовка к ЕГЭ Вступ до С. Перша проста програма
Вступ до С. Перша проста програма Class diagram на диаграмме UML
Class diagram на диаграмме UML Пример поиска информации на государственных образовательных порталах. Поисковые системы
Пример поиска информации на государственных образовательных порталах. Поисковые системы Presentation
Presentation Эффективное применение ИКТ на уроках и во внеурочной деятельности
Эффективное применение ИКТ на уроках и во внеурочной деятельности Блочная верстка сайта. Урок 16
Блочная верстка сайта. Урок 16 дискретное представление графической информации
дискретное представление графической информации Сети и защита информации
Сети и защита информации Привет, Алиса… или как оперативно помочь клиенту. Фирма 1С
Привет, Алиса… или как оперативно помочь клиенту. Фирма 1С Технология создания и преобразования информационных объектов-1
Технология создания и преобразования информационных объектов-1 Десятичная (децимальная) классификация Дьюи (ДКД)
Десятичная (децимальная) классификация Дьюи (ДКД) Проектирование и реализация информационной системы Трамвайно-троллейбусное управление
Проектирование и реализация информационной системы Трамвайно-троллейбусное управление Реализация пользовательского приложения Калькулятор средствами языка программирования C#
Реализация пользовательского приложения Калькулятор средствами языка программирования C#