Содержание
- 2. Cybersecurity
- 3. Internet crime The internet provides a wide variety of opportunities for communication and development, but it
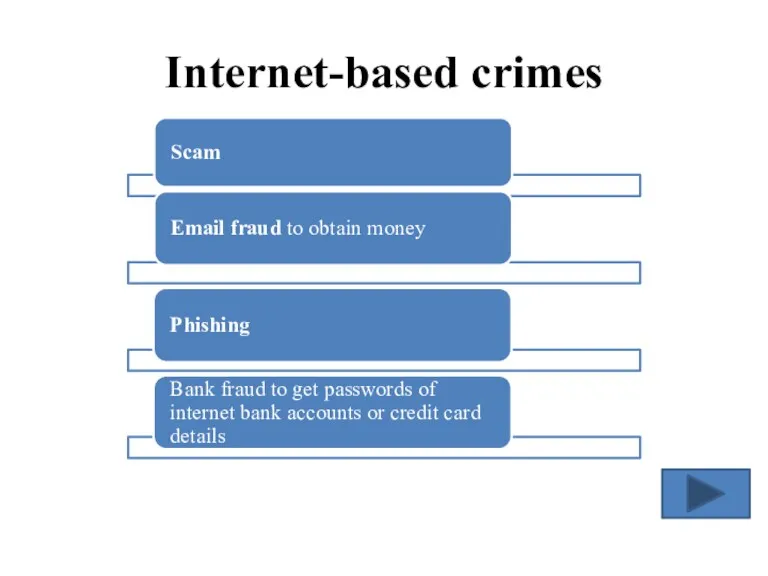
- 4. Internet-based crimes
- 5. Other examples of internet crime Cyberstalking Online harassment or abuse mainly in chat rooms Piracy
- 6. Malware Malicious software created to damage or alter the computer data or its operations.
- 7. Types of malware Viruses are programs that spread by attaching themselves to executable files or documents.
- 8. Trojan horses are malicious programs disguised as innocent-looking files or embedded within legitimate software. They may
- 9. Preventative tips Don’t open email attachments from unknown people, take note of the file extensions; Run
- 10. Identify the internet crime Crackers try to find a way to copy the latest game; Half
- 11. You and computers Answer questions about you Do the quiz and find out your result. What
- 12. More information Think of the following statements. Are they true or false? 1. Keeping information locked
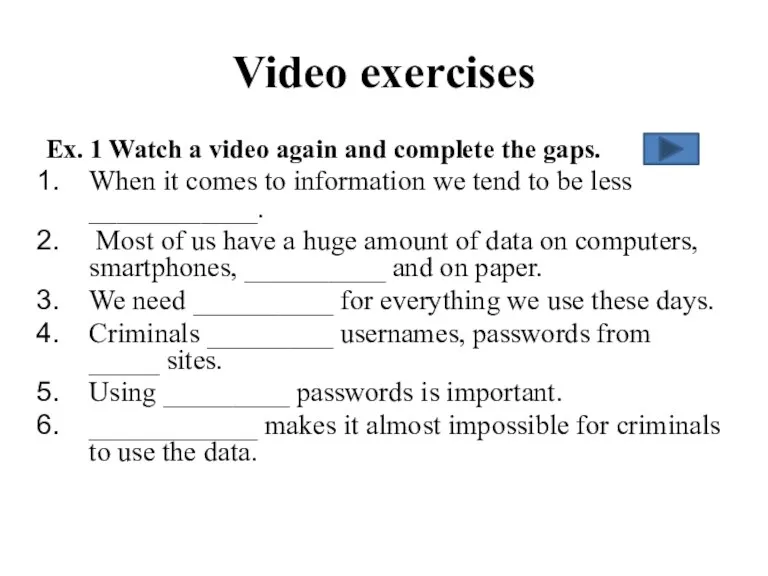
- 13. Video exercises Ex. 1 Watch a video again and complete the gaps. When it comes to
- 14. Video exercises Ex. 2 Watch a video and answer the questions. What kind of address do
- 16. Скачать презентацию








 Базовый семинар: основы контекстной рекламы
Базовый семинар: основы контекстной рекламы Розроблення модуля Управління бізнес-процесами оренди автомобілів на основі Web-технологій
Розроблення модуля Управління бізнес-процесами оренди автомобілів на основі Web-технологій Документирование программного обеспечения
Документирование программного обеспечения Основы комбинаторики, размещения, перестановки, сочетания
Основы комбинаторики, размещения, перестановки, сочетания Работа с файлами в Pascal
Работа с файлами в Pascal Основные методы внедрения и анализа функционирования программного обеспечения и компьютерной системы
Основные методы внедрения и анализа функционирования программного обеспечения и компьютерной системы Конспект урока с презентацией
Конспект урока с презентацией Запись числа в различных системах счисления. ОГЭ - 4 (N10)
Запись числа в различных системах счисления. ОГЭ - 4 (N10) Курсовая работа
Курсовая работа The Internet
The Internet Вебинар 1
Вебинар 1 Графический редактор Adobe Photoshop. История создания
Графический редактор Adobe Photoshop. История создания Информационная культура
Информационная культура 1С:Предприятие 8. Такси и аренда автомобилей
1С:Предприятие 8. Такси и аренда автомобилей World Wide Web. История создания и современность
World Wide Web. История создания и современность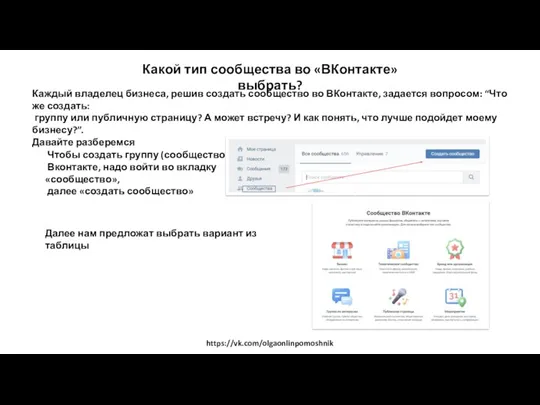 Сообщества во ВКонтакте
Сообщества во ВКонтакте Сортування та фільтрація даних
Сортування та фільтрація даних GSIS Инструкция пользователя (Для сервисного центра)
GSIS Инструкция пользователя (Для сервисного центра) Система счисления
Система счисления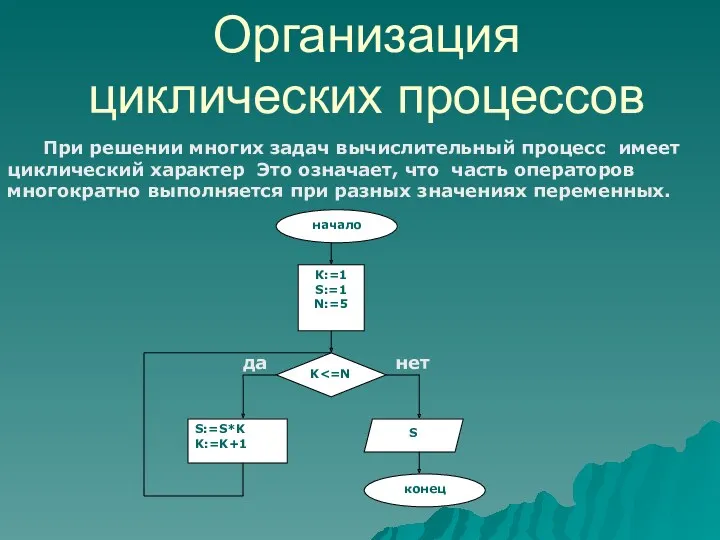 Урок по теме Организация циклических процессов
Урок по теме Организация циклических процессов Напрямки та інструменти веб-дизайну
Напрямки та інструменти веб-дизайну Ассистенты или чат - боты
Ассистенты или чат - боты Telegram. Характеристика
Telegram. Характеристика Cloud Computing For Everyone. Module 2. School Schedules
Cloud Computing For Everyone. Module 2. School Schedules Вводная презентация проекта Сердце - пламенный мотор
Вводная презентация проекта Сердце - пламенный мотор Регистр
Регистр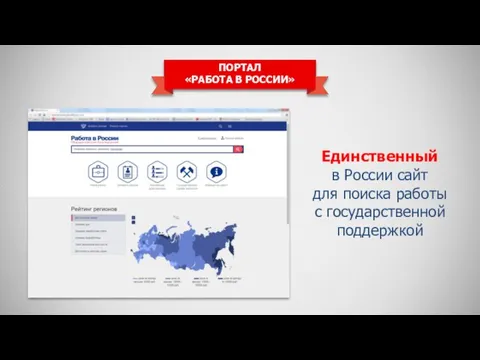 Портал Работа в России
Портал Работа в России Архитектура ПК
Архитектура ПК