Содержание
- 2. $WHOAMI Penetration Tester @ SynerComm Bug Bounty Hunter on HackerOne Python enthusiast @Rhynorater @Rhynorater jgardner@synercomm.com
- 3. 5 ROUTES TO DA … and how to protect your administrators
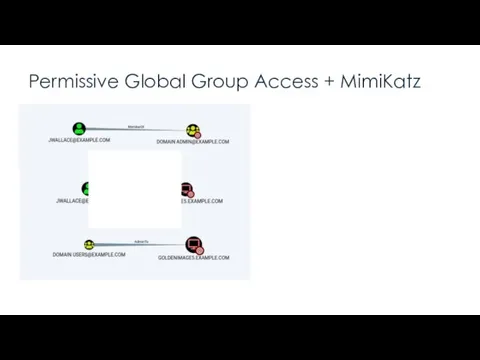
- 4. PERMISSIVE GLOBAL GROUP ACCESS + MIMIKATZ Solution: Apply the principle of least privilege
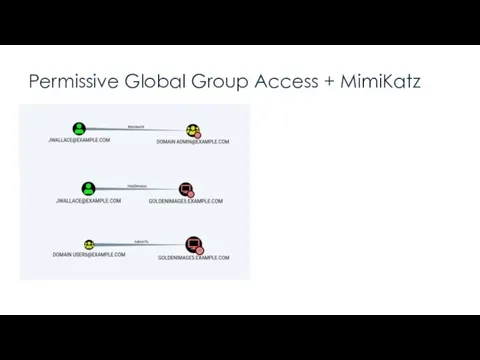
- 5. Permissive Global Group Access + MimiKatz Takeaway:
- 6. Permissive Global Group Access + MimiKatz “A local admin can extract from memory the cleartext password
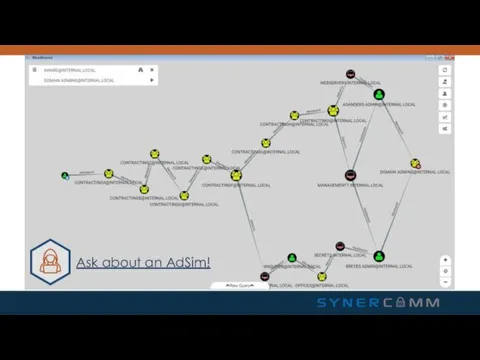
- 7. BloodHound Available on GitHub @BloodhoundAD 10 minute setup Queries DC and domain computer for session and
- 8. Ask about an AdSim!
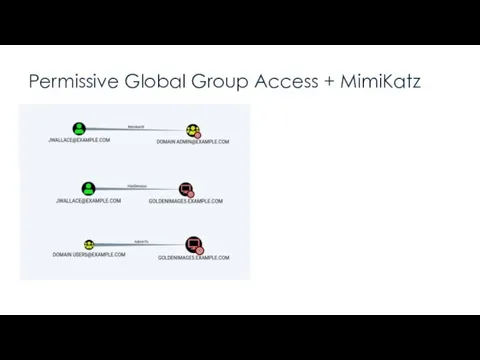
- 9. Permissive Global Group Access + MimiKatz “A local admin can extract from memory the cleartext password
- 10. Permissive Global Group Access + MimiKatz “A local admin can extract from memory the cleartext password
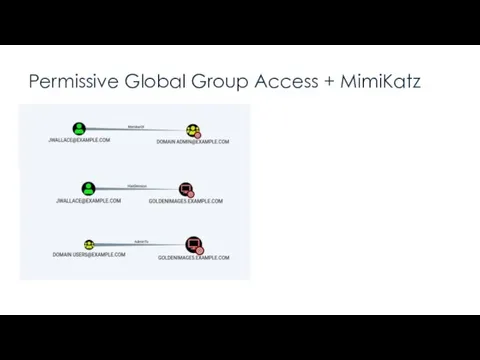
- 11. Permissive Global Group Access + MimiKatz “A local admin can extract from memory the cleartext password
- 12. LLMNR & NBT-NS POISONING Solution: Turn them off.
- 13. LLMNR & NBT-NS Poisoning “Turn off LLMNR. Turn off NBT-NS. Monitor for these requests.” Takeaway: Graphic
- 14. LLMNR & NBT-NS Poisoning “Turn off LLMNR. Turn off NBT-NS. Monitor for these requests.” Takeaway: Responder.py
- 15. LLMNR & NBT-NS Poisoning “Turn off LLMNR. Turn off NBT-NS. Monitor for these requests.” Takeaway: Inveigh.ps1
- 16. LLMNR & NBT-NS Poisoning “Turn off LLMNR. Turn off NBT-NS. Monitor for these requests.” Takeaway: The
- 17. LLMNR & NBT-NS Poisoning “Turn on SMB Signing” Quick Takeaway: Bonus: SMB Relay Attacks
- 18. SYSVOL PASSWORDS + LEAKED AES KEYS Solution: Delete the XML files. Just delete them.
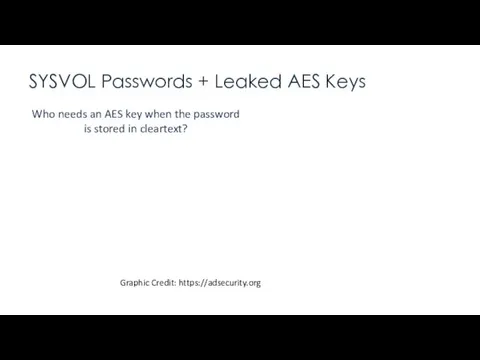
- 19. SYSVOL Passwords + Leaked AES Keys “Apply the patch, delete the XML files, and don’t put
- 20. SYSVOL Passwords + Leaked AES Keys “Apply the patch, delete the XML files, and don’t put
- 21. SYSVOL Passwords + Leaked AES Keys “Apply the patch, delete the XML files, and don’t put
- 22. SYSVOL Passwords + Leaked AES Keys “Apply the patch, delete the XML files, and don’t put
- 23. KERBEROASTING Solution: Long Service Account Passwords
- 24. KerberRoasting “Domain accounts used to run services should have long and complex passwords” Takeaway: Account used
- 25. KerberRoasting “Domain accounts used to run services should have long and complex passwords” Takeaway: Audit your
- 26. DC BACKUPS Solution: Ensure no one but Domain Admins can access your DC backups
- 27. DC Backups “Only Domain Admins should have access to DC Backups” Takeaway: User with access to
- 28. Takeaways A local admin can extract from memory the cleartext password of any authenticated user Turn
- 29. DA101 - Kit https://www.SHELLNTELL.com/blog/da-101 Question or Help? Justin Gardner – jgardner@synercomm.com
- 31. Скачать презентацию














 Компьютерные сети. Топология сетей
Компьютерные сети. Топология сетей Научно-техническая информация
Научно-техническая информация Логические выражения и операции
Логические выражения и операции Функции и повторное использование кода
Функции и повторное использование кода Программы Microsoft Office: PowerPoint 2010, Word 2010
Программы Microsoft Office: PowerPoint 2010, Word 2010 Дополнительные типы данных в Python. Множества, кортежи, словари
Дополнительные типы данных в Python. Множества, кортежи, словари Территориальная информационная медицинская система
Территориальная информационная медицинская система Типология баз данных
Типология баз данных Файлы и файловая система. Программное обеспечение
Файлы и файловая система. Программное обеспечение Способы увеличения производительности ПК
Способы увеличения производительности ПК Внеклассное мероприятие по информатике Игра воображения
Внеклассное мероприятие по информатике Игра воображения Кестелер арасындағы қатынастарды басқару. Мәліметтер схемасымен жұмыс жасау
Кестелер арасындағы қатынастарды басқару. Мәліметтер схемасымен жұмыс жасау Понятие о мультимедиа технологиях. Создание компьютерной презентации
Понятие о мультимедиа технологиях. Создание компьютерной презентации Совершенствование организации проектирования уникальных зданий на основе строительно-информационного моделирования
Совершенствование организации проектирования уникальных зданий на основе строительно-информационного моделирования Новые свойства и возможности Windows Vista
Новые свойства и возможности Windows Vista Технологии локальных сетей. (Тема 3)
Технологии локальных сетей. (Тема 3) Команды ARP и PING
Команды ARP и PING Что такое CIDR и какие задачи позволяет решить? Администрирование вычислительных сетей. Лекция 7
Что такое CIDR и какие задачи позволяет решить? Администрирование вычислительных сетей. Лекция 7 Методика подготовки школьников к участию в олимпиадах по информатике
Методика подготовки школьников к участию в олимпиадах по информатике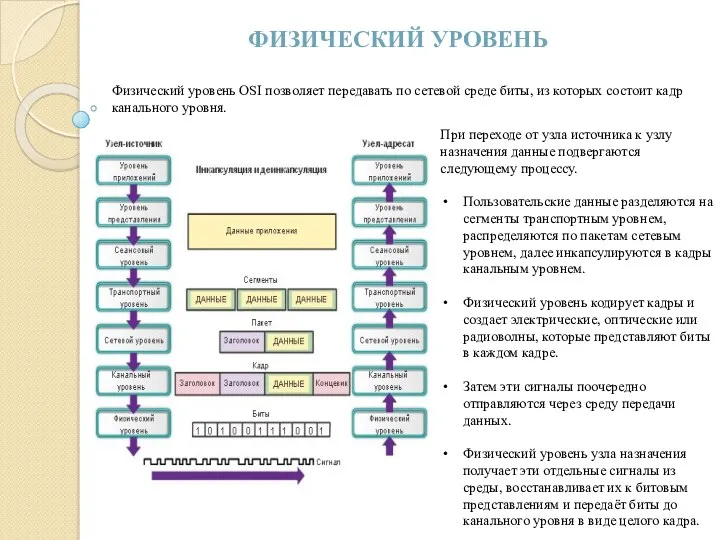 Физический уровень OSI
Физический уровень OSI Changing template colours in PowerPoint 2007
Changing template colours in PowerPoint 2007 DOM-манипуляции
DOM-манипуляции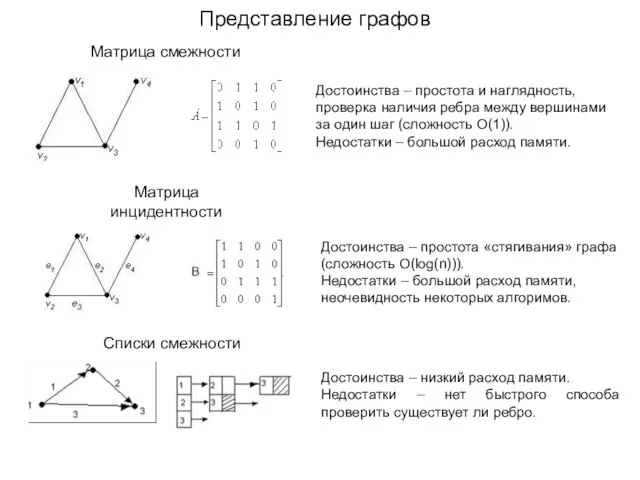 Представление графов
Представление графов Виды программного обеспечения
Виды программного обеспечения Информационное общество
Информационное общество Nissan Visteon USB Reflash Procedure
Nissan Visteon USB Reflash Procedure Открытый урок по информатике Компьютер - мой лучший друг
Открытый урок по информатике Компьютер - мой лучший друг Информация и информационные процессы в неживой природе
Информация и информационные процессы в неживой природе