Содержание
- 2. Learning Objective Explore the history and current state of hacking and penetration testing, including their ethical
- 3. Key Concepts Birth and evolution of hacking 1960s: individuals of technology enthusiasts, motivated by intellectual curiosity
- 4. Types of Hackers Script kiddies are beginners and possess basic skills. Black hats break into computer
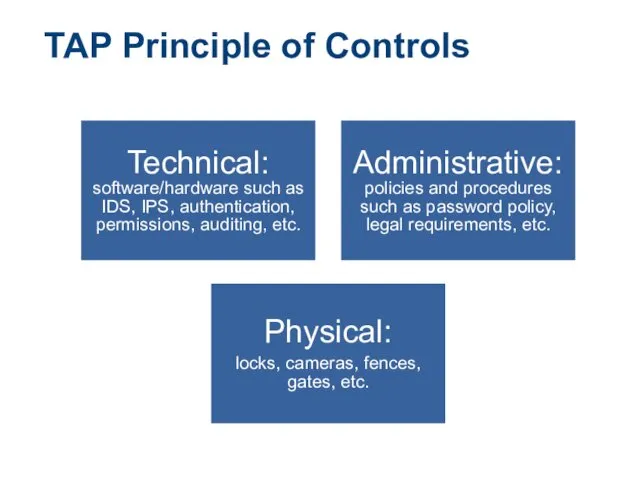
- 5. TAP Principle of Controls Technical: software/hardware such as IDS, IPS, authentication, permissions, auditing, etc. Administrative: policies
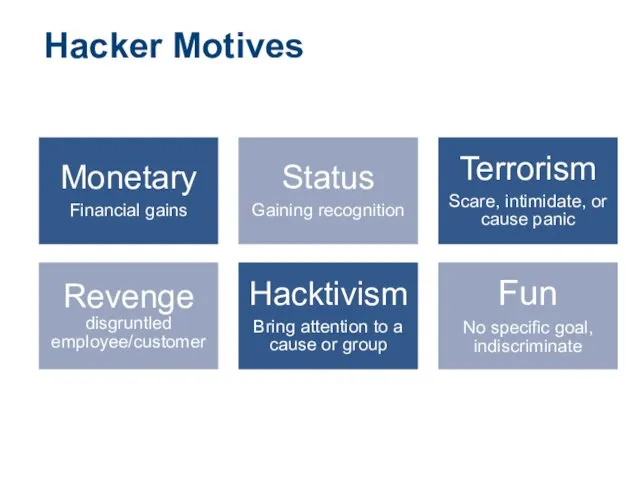
- 6. Hacker Motives Monetary Financial gains Status Gaining recognition Terrorism Scare, intimidate, or cause panic Revenge disgruntled
- 7. Common Attacks (1) Theft of access: stealing passwords, subverting access mechanisms to bypass normal authentication Network
- 8. Common Attacks (2) Dumpster diving: gathering discarded materials Malicious coding: software written to cause damage, destruction,
- 9. Hacking as skillful modification of systems Early Viruses, Phone Phreaking First Hacker Groups, Bulletin Boards First
- 10. Famous Hacks over Time 1988 Robert T. Morris: the first Internet worm 1999 David L. Smith:
- 11. Famous Hackers and Groups Individual Hackers: Kevin Poulsen, Frank Abagnale, Kevin Mitnick Groups: Black Hats: The
- 12. Modern Hacking and Cybercriminals Transformation of hobbyist hacking to cybercrime Cybercriminals seeking profits by aiming at
- 13. Ethical Hacking and Penetration Testing Ethical hackers require permission to engage in penetration testing Penetration testing
- 14. Key Points about Ethical Hacking It requires explicit permission of “victim” Participants use the same tactics
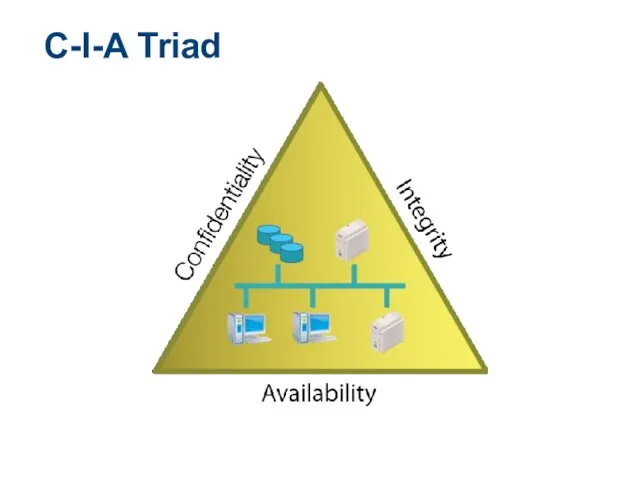
- 15. C-I-A Triad
- 16. C-I-A Triad Confidentiality: safeguarding information or services against disclosure to unauthorized parties Integrity: ensuring that information
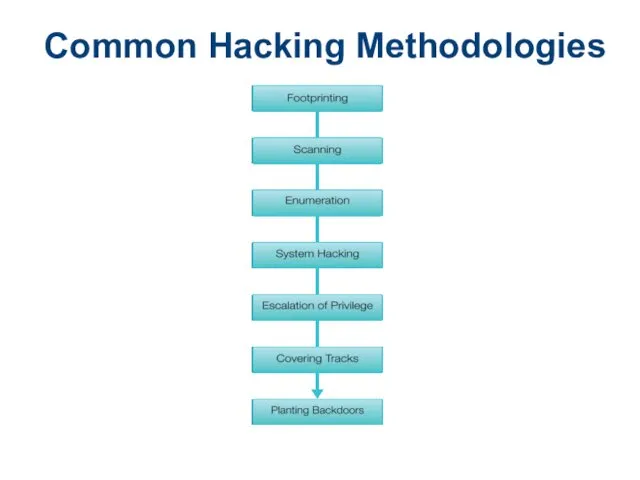
- 17. Common Hacking Methodologies
- 18. Hacking Methodologies Footprinting: An attacker passively acquires information about the intended victim’s system Scanning: actively acquire
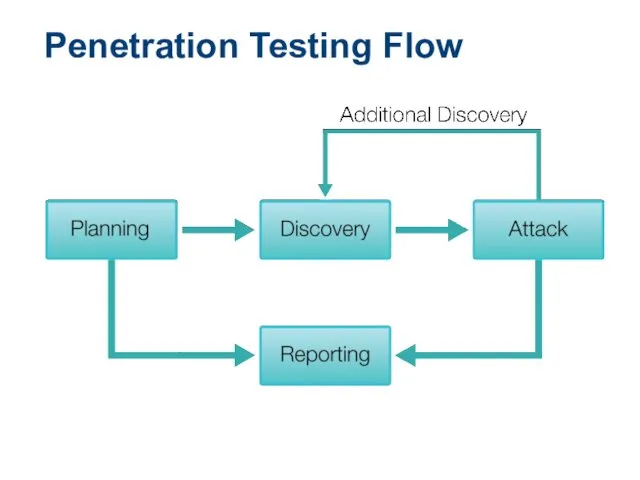
- 19. Penetration Testing Flow
- 20. Performing a Penetration Test Next logical step beyond ethical hacking Require rules to be agreed upon
- 21. Laws and Ethical Standards Ethical hackers should exercise proper care not to violate the rules of
- 23. Скачать презентацию














 Экономическая информатика. Microsoft Excel
Экономическая информатика. Microsoft Excel CSS-стили. Основы работы с хостингом
CSS-стили. Основы работы с хостингом Булевий пошук. Лекція 1
Булевий пошук. Лекція 1 СППР, хранилища и витрины данных, интеллектуальный анализ данных
СППР, хранилища и витрины данных, интеллектуальный анализ данных LOGO! программирование
LOGO! программирование Компьютерные вирусы
Компьютерные вирусы Что же такое информатика
Что же такое информатика Информация и информационные процессы
Информация и информационные процессы Виртуальные машины
Виртуальные машины Разбор 3 задания (базы данных) из ЕГЭ по информатике
Разбор 3 задания (базы данных) из ЕГЭ по информатике ASP.NET MVC 5. Part 1. Overview. Controllers. Views
ASP.NET MVC 5. Part 1. Overview. Controllers. Views Информационные жанры в СМИ
Информационные жанры в СМИ Понятие алгоритма, свойства, виды (типы). Формы записи. Исходные и выходные данные алгоритмов, примеры (Лекция 3)
Понятие алгоритма, свойства, виды (типы). Формы записи. Исходные и выходные данные алгоритмов, примеры (Лекция 3) Измерение информации Алфавитный подход
Измерение информации Алфавитный подход Перевод чисел в позиционных системах счисления
Перевод чисел в позиционных системах счисления Архитектура ЭВМ
Архитектура ЭВМ Робототехника Ev3. 5-8 классы
Робототехника Ev3. 5-8 классы Использование редактора блок-схем при решении математических задач на Паскале
Использование редактора блок-схем при решении математических задач на Паскале Информационные системы как средство реализации информационных технологий. Определения. Стандарты
Информационные системы как средство реализации информационных технологий. Определения. Стандарты Настройки для банни-хоппинга [rus]
Настройки для банни-хоппинга [rus] ВКР: Разработка информационной системы загородной базы отдыха
ВКР: Разработка информационной системы загородной базы отдыха Трассировка лучей в играх
Трассировка лучей в играх Оренбургский областной музей изобразительных искусств. Мобильный аудиогид по музею Maugry
Оренбургский областной музей изобразительных искусств. Мобильный аудиогид по музею Maugry Технології штучного інтелекту в готельноресторанних комплексах
Технології штучного інтелекту в готельноресторанних комплексах Электронный документооборот
Электронный документооборот Разработка приложений для ОС Android
Разработка приложений для ОС Android AVL trees. (Lecture 8)
AVL trees. (Lecture 8) 1С и Telegram
1С и Telegram