Содержание
- 2. Objectives: Identify what Malicious code is Know the categories of Malicious code Introduce you to the
- 3. A broad category of software threats to your network and systems Modifies or destroys data Steals
- 4. AKA: Programmed Threats A Computer Program is designed to achieve a particular function Malicious when the
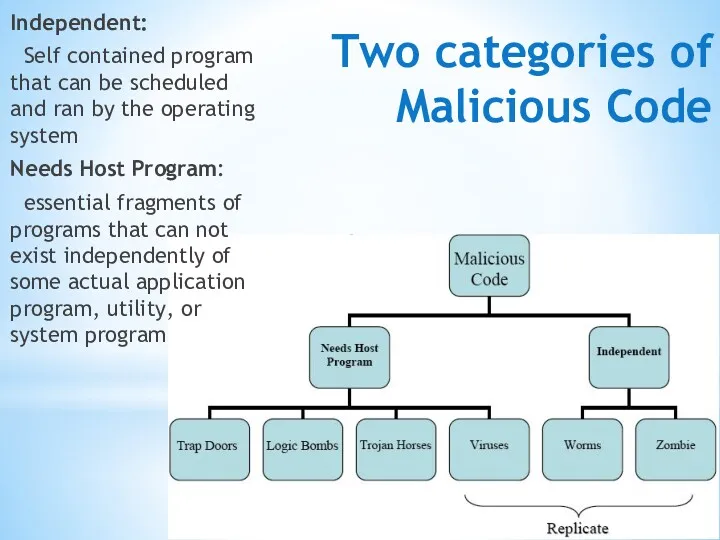
- 5. Two categories of Malicious Code Independent: Self contained program that can be scheduled and ran by
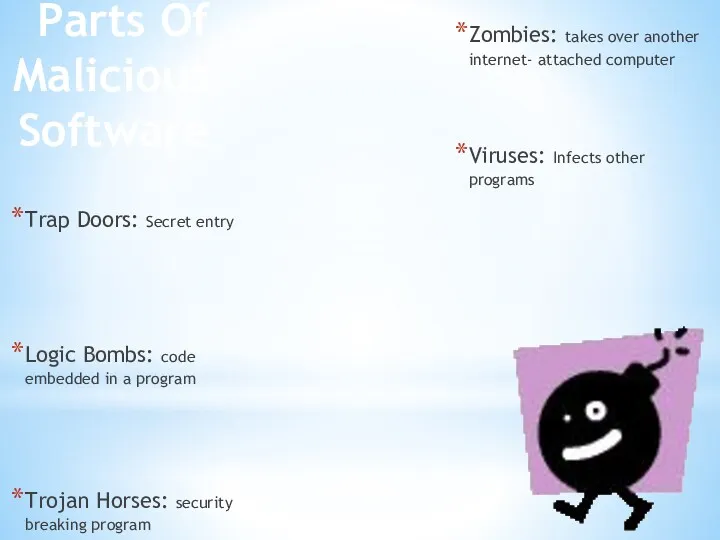
- 6. Parts Of Malicious Software Trap Doors: Secret entry Logic Bombs: code embedded in a program Trojan
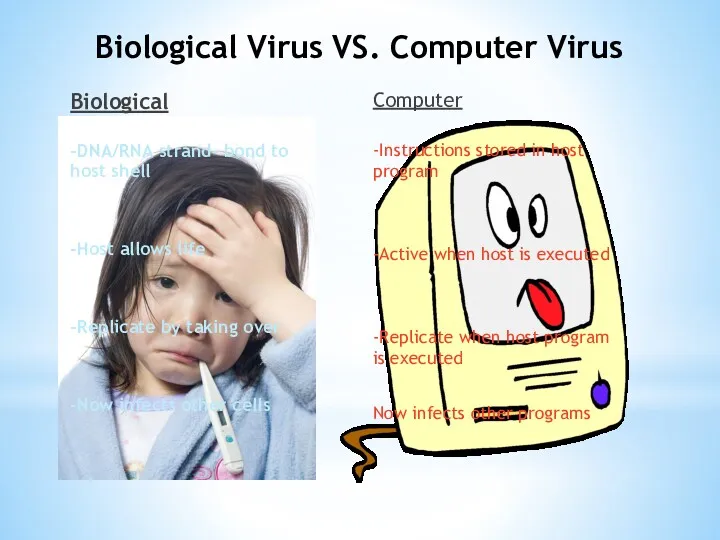
- 7. Biological Virus VS. Computer Virus Biological -DNA/RNA strand- bond to host shell -Host allows life -Replicate
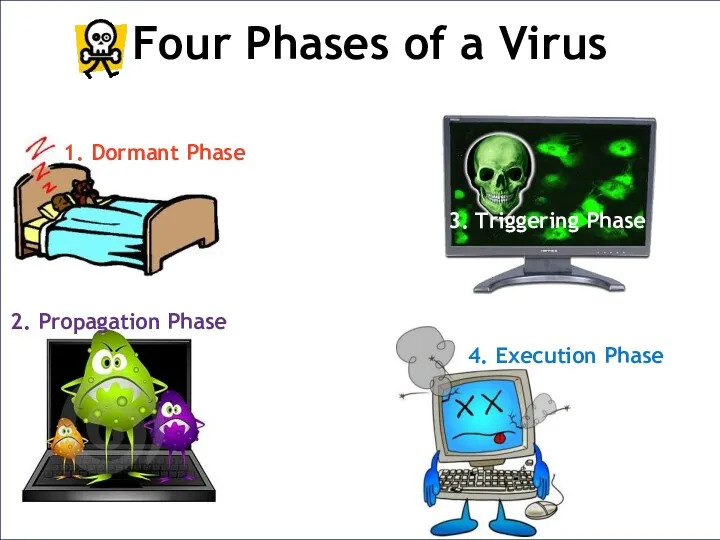
- 8. Four Phases of a Virus 1. Dormant Phase 3. Triggering Phase 2. Propagation Phase 4. Execution
- 10. Скачать презентацию

 Технологии работы с информацией и знаниями
Технологии работы с информацией и знаниями Обзор информационной системы КАСАНТ/КАСАТ
Обзор информационной системы КАСАНТ/КАСАТ Онтологические модели представления знаний
Онтологические модели представления знаний Console Input / Output Reading and Writing to the Console
Console Input / Output Reading and Writing to the Console Создание и использование ЦОР на уроках информатики с целью формирования у учащихся информационно-коммуникационной компетентности
Создание и использование ЦОР на уроках информатики с целью формирования у учащихся информационно-коммуникационной компетентности Информационное общество. Требования к уровням компьютерной грамотности. Стандарты оформления научных работ
Информационное общество. Требования к уровням компьютерной грамотности. Стандарты оформления научных работ Основи растрової графіки. Використання фото та кліпартів. Растрова анімація
Основи растрової графіки. Використання фото та кліпартів. Растрова анімація Устройство компьютера. Аналогия между компьютером и человеком
Устройство компьютера. Аналогия между компьютером и человеком Науковедение, наукометрия, библиометрия
Науковедение, наукометрия, библиометрия Основы работы в CorelDRAW X7. Компьютерная графика
Основы работы в CorelDRAW X7. Компьютерная графика Логическое программирование
Логическое программирование Автоматизированные системы обработки информации
Автоматизированные системы обработки информации Информационные ресурсы интернета
Информационные ресурсы интернета Виды базы данных
Виды базы данных Своя игра
Своя игра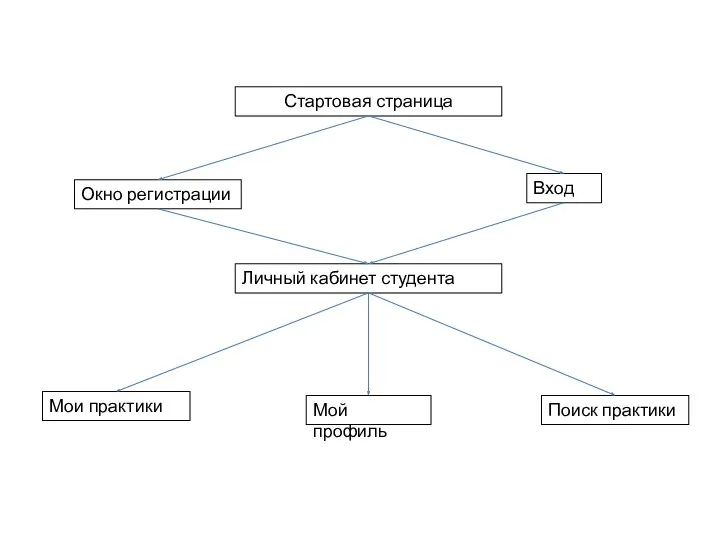 Стартовая страница
Стартовая страница Мультимедийная разработка урока изобразительного искусства (5 класс)
Мультимедийная разработка урока изобразительного искусства (5 класс) Основы сетевого администрирования
Основы сетевого администрирования Understanding CSS. Essentials: layouts, managing text flow, managing the graphical interface
Understanding CSS. Essentials: layouts, managing text flow, managing the graphical interface Паттерны проектирования
Паттерны проектирования Информационные технологии и системы. Автоматизированные информационные системы (АИС)
Информационные технологии и системы. Автоматизированные информационные системы (АИС) Хранение информации. 10 лекция
Хранение информации. 10 лекция Кодирование информации
Кодирование информации Программирование (Python)
Программирование (Python) Bitcoin. Как это работает — предпосылки
Bitcoin. Как это работает — предпосылки Analysis and Design of Data Systems. Enhanced ER (EER) Mode. (Lecture 11)
Analysis and Design of Data Systems. Enhanced ER (EER) Mode. (Lecture 11) Адресация компьютера в сети
Адресация компьютера в сети Управление файловой системой. Основные понятия. (Лекция 13)
Управление файловой системой. Основные понятия. (Лекция 13)