Содержание
- 2. Malware “A program that is inserted into a system, usually covertly, with the intent of compromising
- 3. Malicious software Programs exploiting system vulnerabilities Known as malicious software or malware program fragments that need
- 4. Malware Terminology Payload: actions of the malware Virus: attaches itself to a program Worm: propagates copies
- 5. Viruses Piece of software that infects programs modifying them to include a copy of the virus
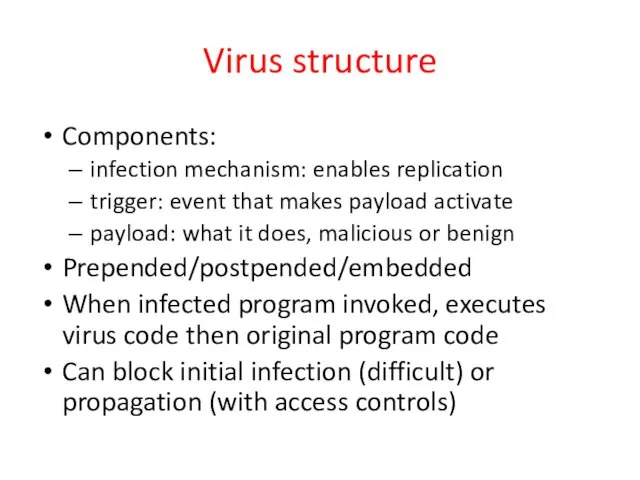
- 6. Virus structure Components: infection mechanism: enables replication trigger: event that makes payload activate payload: what it
- 7. Virus structure
- 8. A virus such as the one just described is easily detected because an infected version of
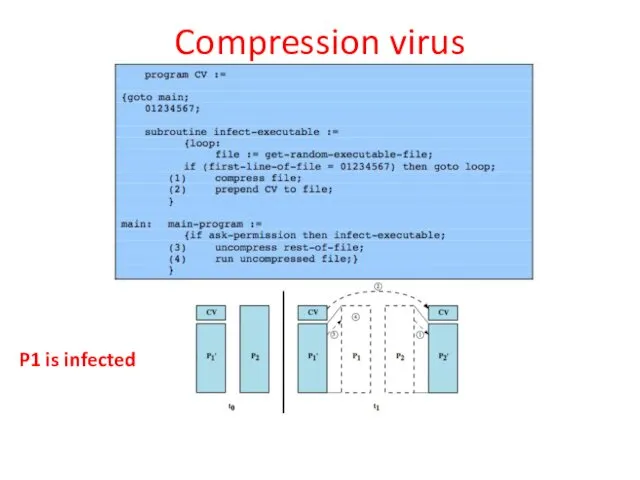
- 9. Compression virus P1 is infected
- 10. Virus classification By target boot sector: infect a master boot record file infector: infects executable OS
- 11. Macro and scripting viruses Became very common in mid-1990s since platform independent infect documents easily spread
- 12. E-Mail Viruses More recent development Melissa exploits MS Word macro in attached doc if attachment opened,
- 13. Virus countermeasures Prevention: ideal solution but difficult Realistically need: detection: determine what occurred identification: identify the
- 14. Anti-virus evolution Virus & antivirus tech have both evolved Early viruses simple code, easily removed As
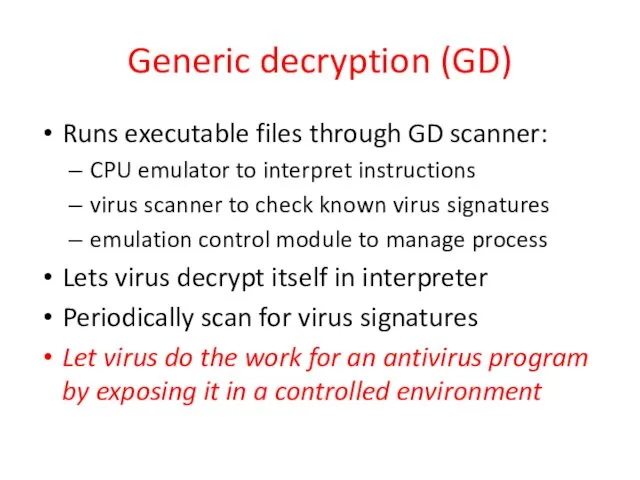
- 15. Generic decryption (GD) Runs executable files through GD scanner: CPU emulator to interpret instructions virus scanner
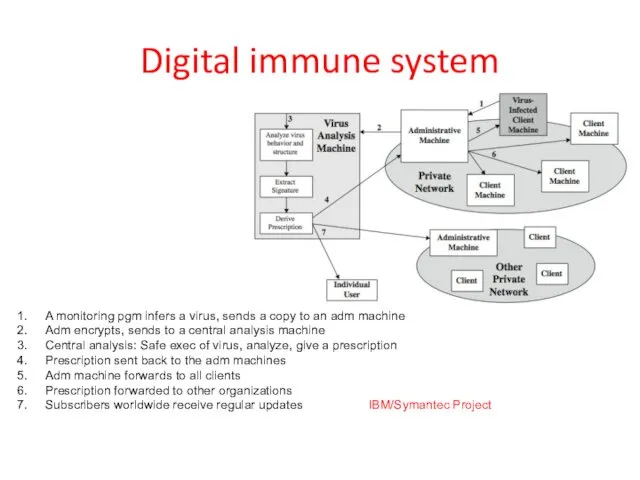
- 16. Digital immune system A monitoring pgm infers a virus, sends a copy to an adm machine
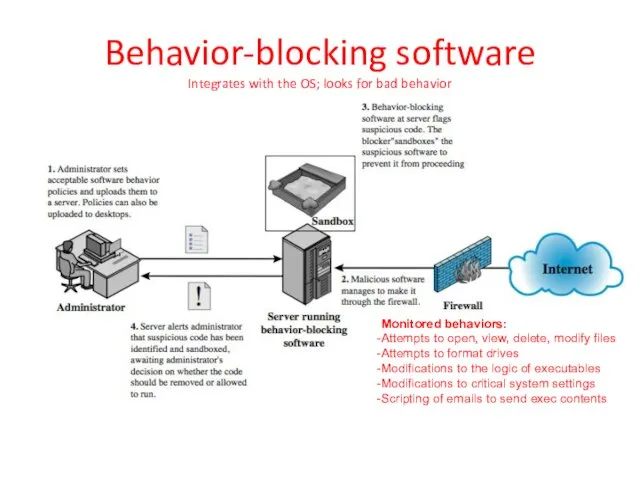
- 17. Behavior-blocking software Integrates with the OS; looks for bad behavior Monitored behaviors: Attempts to open, view,
- 18. Worms Replicating program that propagates over net using email, remote exec, remote login Has phases like
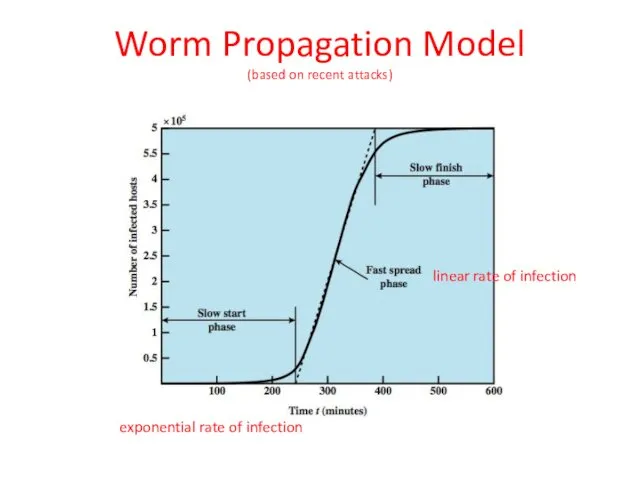
- 19. Worm Propagation Model (based on recent attacks) exponential rate of infection linear rate of infection
- 20. Morris worm One of best known worms Released by Robert Morris in 1988 Affected 6,000 computers;
- 21. More recent worm attacks Melissa 1998: exploiting Microsoft Word macro embedded in an attachment. 1999: could
- 22. State of worm technology Multiplatform: not limited to Windows Multi-exploit: Web servers, emails, file sharing …
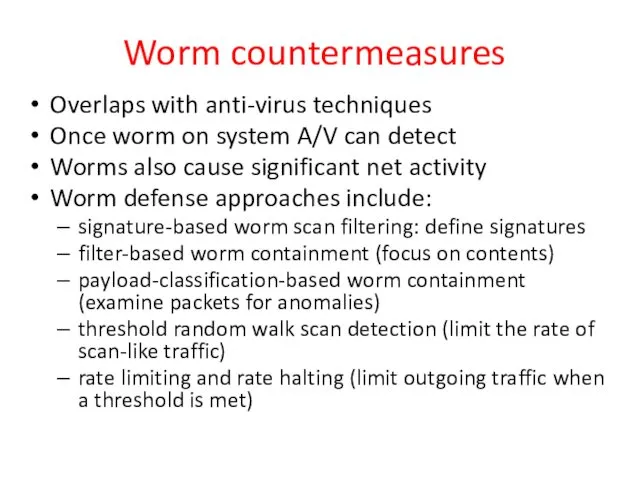
- 23. Worm countermeasures Overlaps with anti-virus techniques Once worm on system A/V can detect Worms also cause
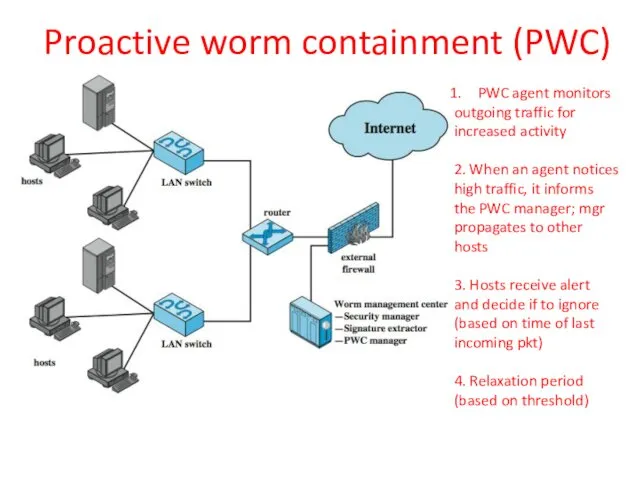
- 24. Proactive worm containment (PWC) PWC agent monitors outgoing traffic for increased activity 2. When an agent
- 25. Mobile code Scripts, macros or other portable instructions Popular ones: JavaScript, ActiveX, VBScript Heterogeneous platforms From
- 26. Client-side vulnerabilities Drive-by-downloads: common in recent attacks Exploits browser vulnerabilities (when a user visits a website
- 27. Social engineering, spam, email, Trojans “Tricking” users to assist in the compromise of their own systems
- 28. Payload What actions a malware will take on the system? Data destruction, theft Data encryption (ransomware)
- 29. Payload attack agents: bots (zombie/drone) Program taking over other computers and launch attacks hard to trace
- 30. Uses of bots DDoS Spamming Sniffing traffic Keylogging Spreading malware Installing advertisement Manipulating games and polls
- 31. Payload: information theft Credential theft, key loggers, spyware Phishing identify theft Spear phishing (act as a
- 32. A backdoor is a secret entry point into a program to gain access without going through
- 33. Payload: backdoor and rootkits A rootkit is a set of programs installed for admin access It
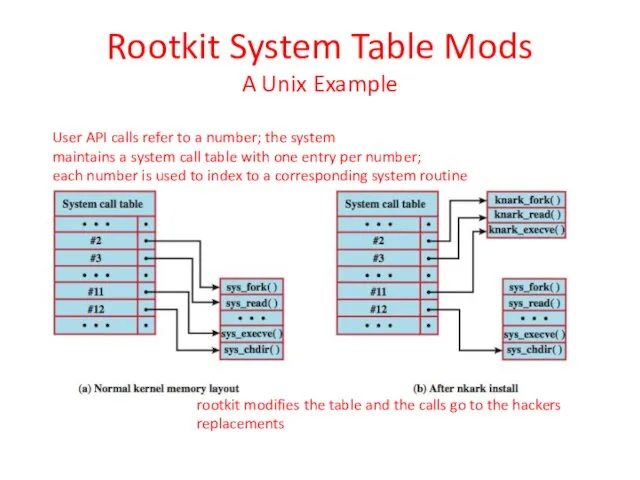
- 34. Rootkit System Table Mods A Unix Example User API calls refer to a number; the system
- 35. Countermeasures for Malware Prevention: Ensure all systems are as current as possible, with all patches applied
- 36. Countermeasures for Malware If prevention fails, use technical mechanisms to support the following threat mitigation options:
- 38. Скачать презентацию
























 Арифметические операции в позиционных системах счисления
Арифметические операции в позиционных системах счисления Введення й редагування тексту
Введення й редагування тексту Информатика. Часть 1. Лекции по Microsoft Excel
Информатика. Часть 1. Лекции по Microsoft Excel CCNA Security
CCNA Security Носители информации
Носители информации Засоби автоматизації процесу створення документа
Засоби автоматизації процесу створення документа Методы искусственного интеллекта
Методы искусственного интеллекта Методы и модели описания систем. Количественные методы
Методы и модели описания систем. Количественные методы Синтез линейной системы управления
Синтез линейной системы управления Методы поиска областей открытия и закрытия в видео и способы их улучшения
Методы поиска областей открытия и закрытия в видео и способы их улучшения Алгоритмы. Определение и способы записи алгоритмов
Алгоритмы. Определение и способы записи алгоритмов Дослідження та проектування Mondex середовище
Дослідження та проектування Mondex середовище Компьютерные сети. Виды компьютерных сетей
Компьютерные сети. Виды компьютерных сетей Пример создания базы данных шаг за шагом
Пример создания базы данных шаг за шагом Система защиты от DDoS атак на основе анализа логов
Система защиты от DDoS атак на основе анализа логов Презентации к уроку информатики в 3 классе по теме Объект
Презентации к уроку информатики в 3 классе по теме Объект Тестовая документация Лекция 7
Тестовая документация Лекция 7 Лекция 3 по архитектуре компьютеров. Архитектура системы команд
Лекция 3 по архитектуре компьютеров. Архитектура системы команд Среда разработки MATLAB. Раздел 1
Среда разработки MATLAB. Раздел 1 Утиліти для роботи з дисками. 9 клас
Утиліти для роботи з дисками. 9 клас Безпека в інтернеті
Безпека в інтернеті Основні сервіси Internet
Основні сервіси Internet Анализ требований и определение спецификаций программного обеспечения при объектном подходе
Анализ требований и определение спецификаций программного обеспечения при объектном подходе Компьютерные сети. Основы компьютерных сетей. Технология Ethernet. Часть 2
Компьютерные сети. Основы компьютерных сетей. Технология Ethernet. Часть 2 Программирование на Basic
Программирование на Basic Инструкция по использованию ЛК
Инструкция по использованию ЛК Модель сутність-зв’язок
Модель сутність-зв’язок Презентация Текстовый редактор
Презентация Текстовый редактор