Слайд 2

СПОСОБЫ ЗАЩИТЫ ПРИЛОЖЕНИЙ
Упаковка / шифрование всего файла
Обфускация отдельных строк / машинного
кода
Виртуализация кода
Обнаружение отладчиков/эмуляторов/песочниц/виртуалок
Слайд 3

Слайд 4
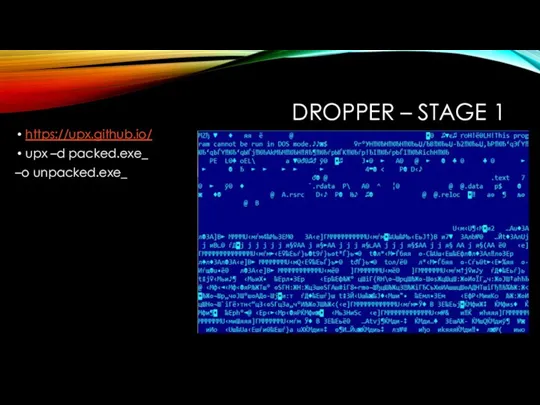
DROPPER – STAGE 1
https://upx.github.io/
upx –d packed.exe_
–o unpacked.exe_
Слайд 5
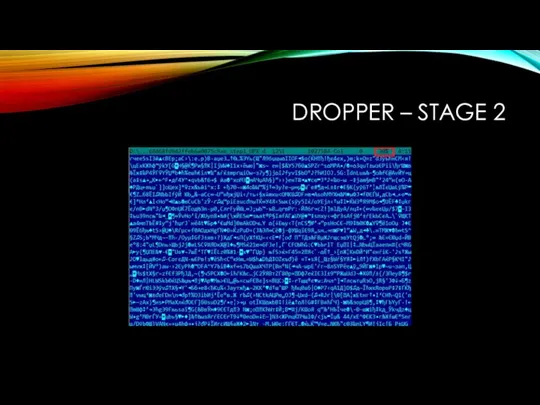
Слайд 6
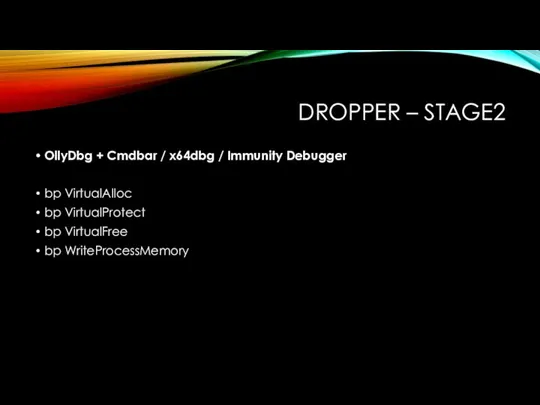
DROPPER – STAGE2
OllyDbg + Cmdbar / x64dbg / Immunity Debugger
bp VirtualAlloc
bp
VirtualProtect
bp VirtualFree
bp WriteProcessMemory
Слайд 7
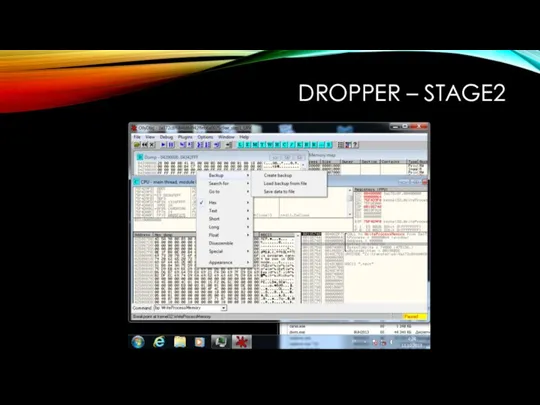
Слайд 8
Слайд 9
Слайд 10
Слайд 11
Слайд 12
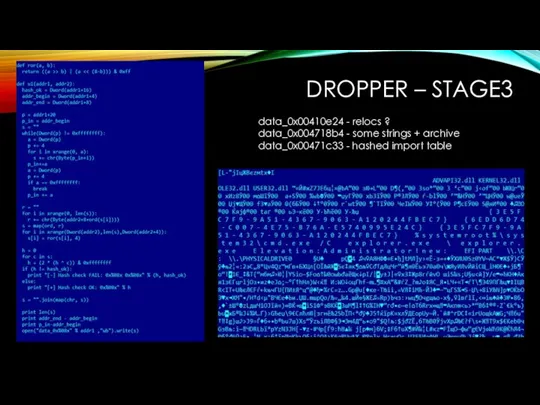
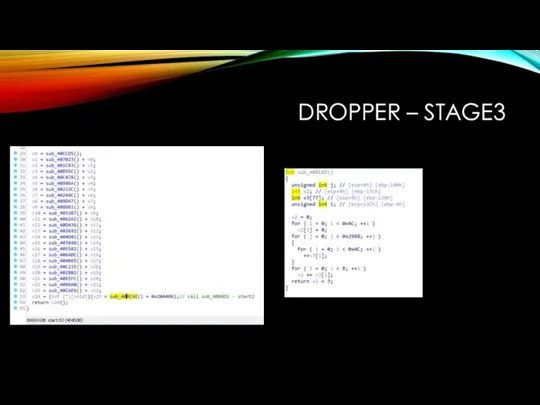
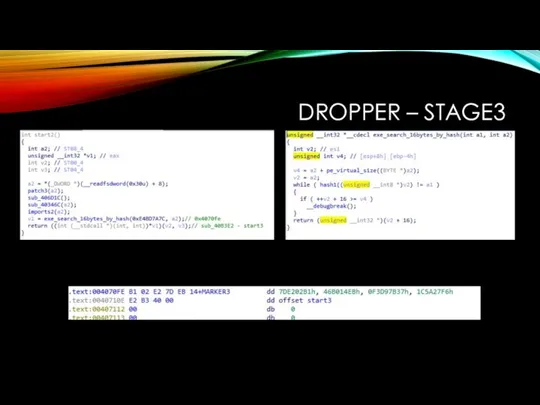
DROPPER – STAGE3
data_0x00410e24 - relocs ?
data_0x004718b4 - some strings + archive
data_0x00471c33
- hashed import table
Слайд 13
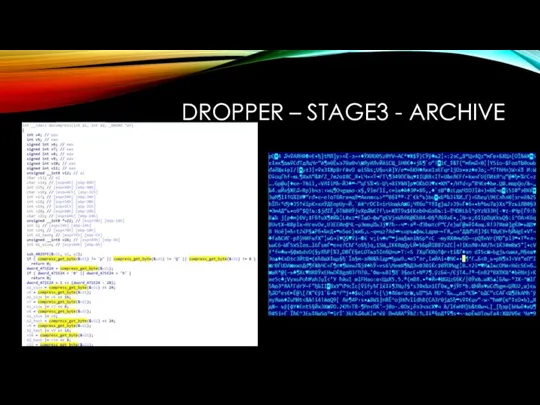
DROPPER – STAGE3 - ARCHIVE
Слайд 14
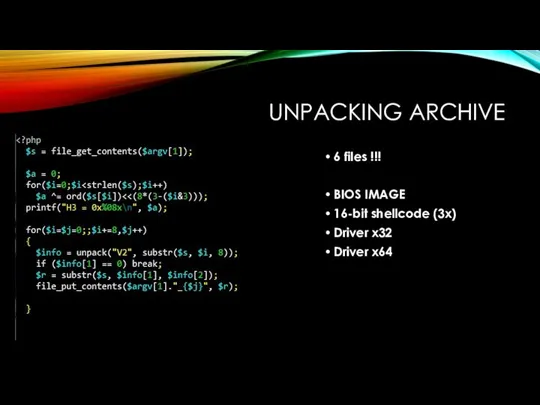
UNPACKING ARCHIVE
6 files !!!
BIOS IMAGE
16-bit shellcode (3x)
Driver x32
Driver x64
Слайд 15
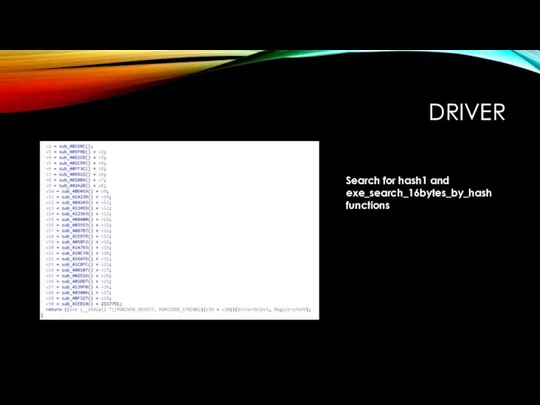
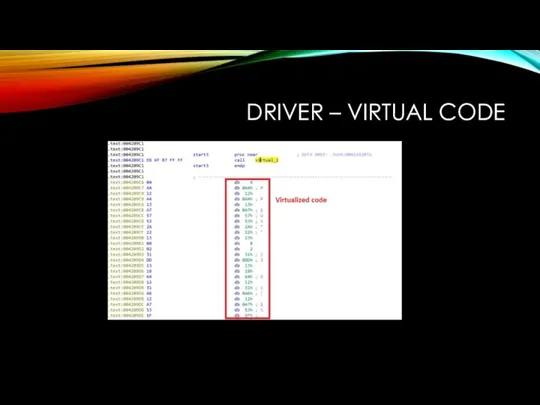
DRIVER
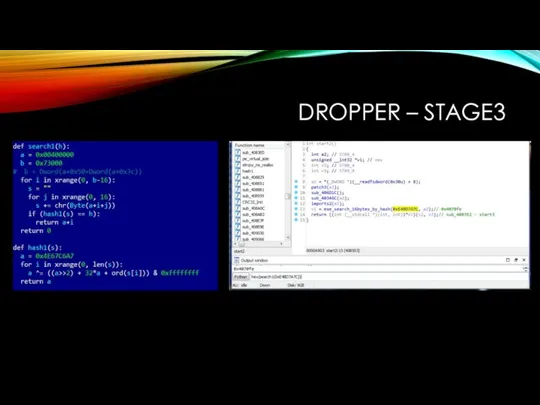
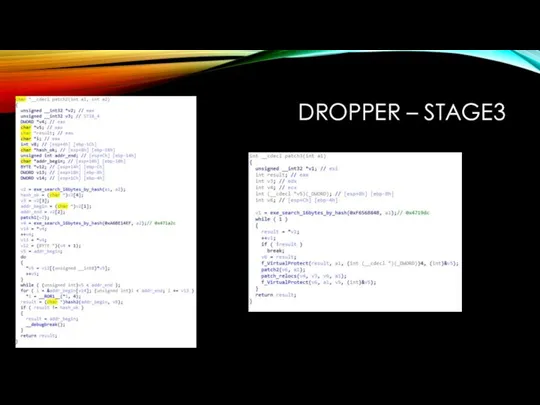
Search for hash1 and exe_search_16bytes_by_hash functions
Слайд 16
Слайд 17
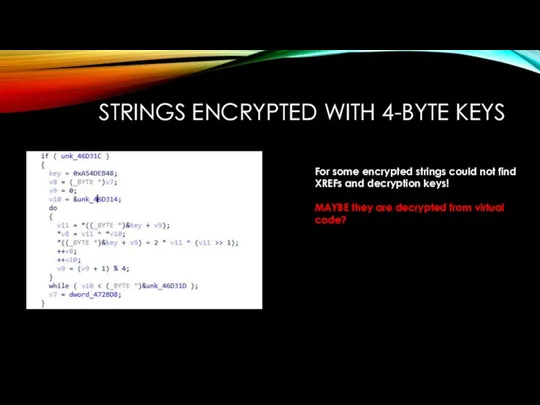
STRINGS ENCRYPTED WITH 4-BYTE KEYS
For some encrypted strings could not find
XREFs and decryption keys!
MAYBE they are decrypted from virtual code?
Слайд 18
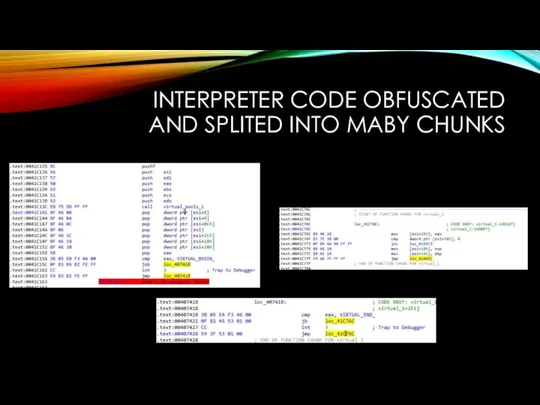
INTERPRETER CODE OBFUSCATED AND SPLITED INTO MABY CHUNKS
Слайд 19
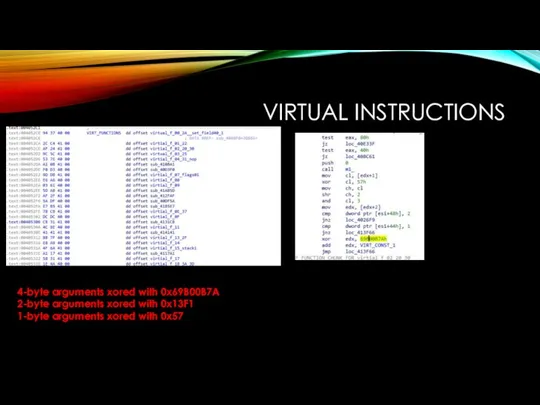
VIRTUAL INSTRUCTIONS
4-byte arguments xored with 0x69B00B7A
2-byte arguments xored with 0x13F1
1-byte arguments
xored with 0x57
Слайд 20
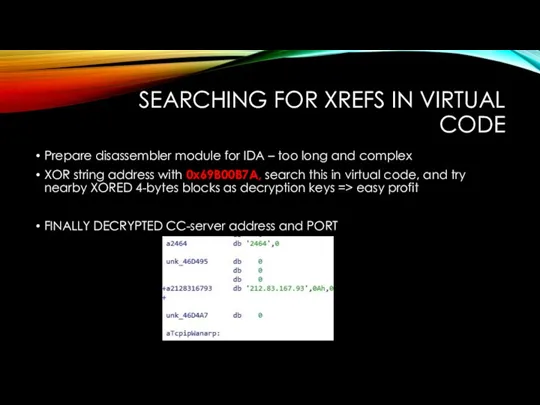
SEARCHING FOR XREFS IN VIRTUAL CODE
Prepare disassembler module for IDA –
too long and complex
XOR string address with 0x69B00B7A, search this in virtual code, and try nearby XORED 4-bytes blocks as decryption keys => easy profit
FINALLY DECRYPTED CC-server address and PORT
Слайд 21

DGA ALGORITHM
SEEMS DGA ALROTITHM ALSO EXISTS
NO XREFS FROM NATIVE CODE TO
DGA strings
TODO – time to make IDA PRO processor module




















 Управление IT-отделом 8
Управление IT-отделом 8 Global Regulatory Reporting
Global Regulatory Reporting Компьютерные сети их классификация. Работа в локальной сети. Топологии локальных сетей. Обмен данными
Компьютерные сети их классификация. Работа в локальной сети. Топологии локальных сетей. Обмен данными Электронды үкімет
Электронды үкімет Влияние социальных сетей на грамматность речи
Влияние социальных сетей на грамматность речи Урок информатики в 7 классе Мультимедийные интерактивные презентации
Урок информатики в 7 классе Мультимедийные интерактивные презентации Измерение информации. 10 класс
Измерение информации. 10 класс How to create site?
How to create site? Алгоритмы и контейнеры данных (C++)
Алгоритмы и контейнеры данных (C++) Системи управління базами даних: основи побудови та моделі організації
Системи управління базами даних: основи побудови та моделі організації Создание простых механизмов с помощью конструктора LegoWeDo
Создание простых механизмов с помощью конструктора LegoWeDo Урок В мире кодов
Урок В мире кодов The Essence of C++ with examples in C++84, C++98, C++11, and C++14
The Essence of C++ with examples in C++84, C++98, C++11, and C++14 Формирование и анализ требований к ИС
Формирование и анализ требований к ИС Лекции по программированию на ассемблере
Лекции по программированию на ассемблере Поиск информации
Поиск информации Классификация информационных систем
Классификация информационных систем Работа с большими документами
Работа с большими документами Создание приложения с использованием С++ и Оpengl
Создание приложения с использованием С++ и Оpengl Электронная коммерция и реклама в сети Internet
Электронная коммерция и реклама в сети Internet 9 класс. Урок на тему: Условия выбора и сложные логические выражения
9 класс. Урок на тему: Условия выбора и сложные логические выражения Информационная безопасность
Информационная безопасность Информация и информационные процессы
Информация и информационные процессы Основы алгоритмизации и объектно-ориентированного программирования
Основы алгоритмизации и объектно-ориентированного программирования ЛицеИСт – лицейская информационная система
ЛицеИСт – лицейская информационная система San berlenleriň görnüşlerini özgertmek
San berlenleriň görnüşlerini özgertmek Поняття про мову гіпертекстової розмітки. Урок 31
Поняття про мову гіпертекстової розмітки. Урок 31 Проект-дослідження Мобілочка
Проект-дослідження Мобілочка