Содержание
- 2. Who am I? Roberto Suggi Liverani Security Consultant, CISSP - Security-Assessment.com 4+ years in information security,
- 3. Agenda Web Spam Introduction Black Hat SEO / White Hat SEO Web Spam Business Aggressive Black
- 4. Web Spam - Introduction Web Spam Definition: The practice of manipulating web pages in order to
- 5. Web Spam – White Hat and Black Hat SEO Different techniques to manipulate search engine page
- 6. The Web Spam Business The top-10 results page is the SEO business SEO businesses: Increase visibility/positioning
- 7. Web Spam – Aggressive Black Hat SEO However, there are instances where black hat SEO is
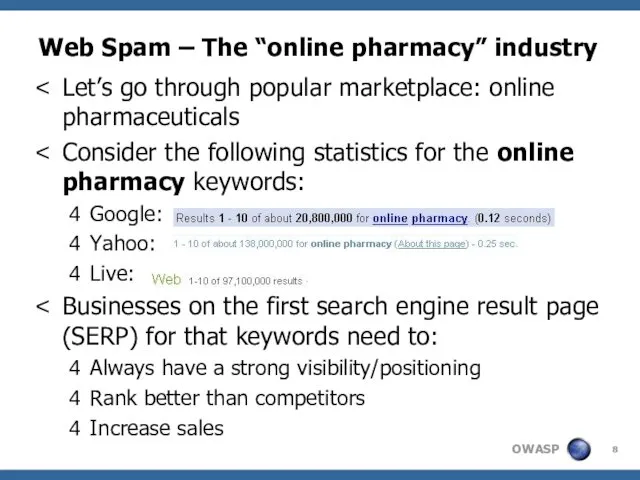
- 8. Web Spam – The “online pharmacy” industry Let’s go through popular marketplace: online pharmaceuticals Consider the
- 9. Web Spam – Affiliate/Associate Programs Businesses in these industries prefer to not spam directly because: Do
- 10. Web Spam – Affiliate/Associate Programs Some affiliate/associate programs directly/indirectly allow spam. How? Some of these affiliate/associate
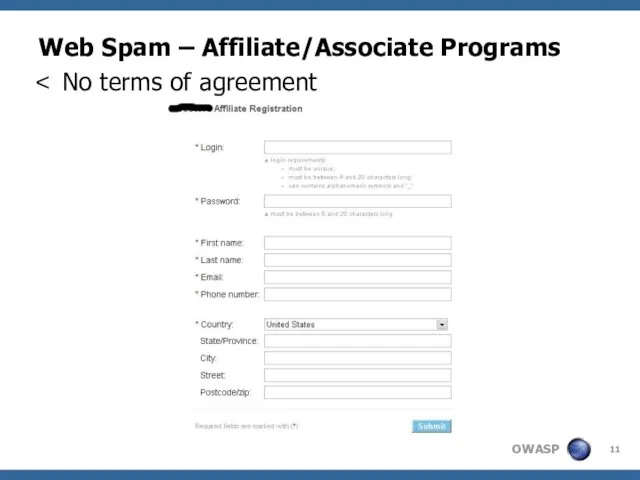
- 11. Web Spam – Affiliate/Associate Programs No terms of agreement
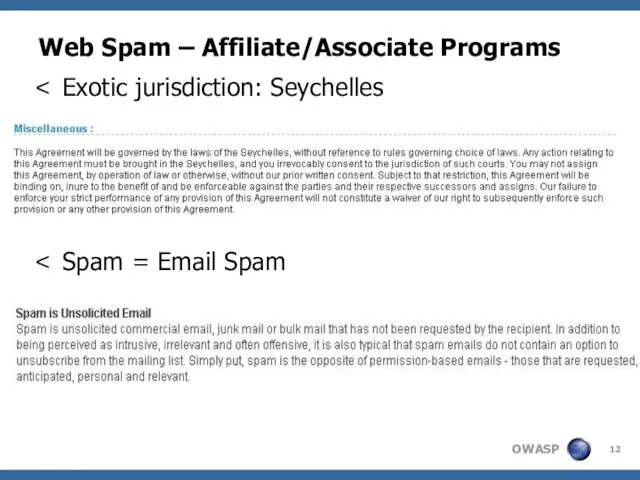
- 12. Web Spam – Affiliate/Associate Programs Exotic jurisdiction: Seychelles Spam = Email Spam
- 13. Web Spam – So how does it work? Affiliates use aggressive black hat SEO to spam
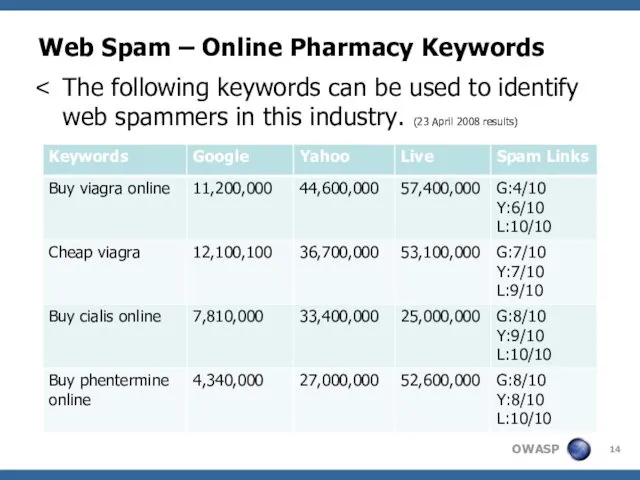
- 14. Web Spam – Online Pharmacy Keywords The following keywords can be used to identify web spammers
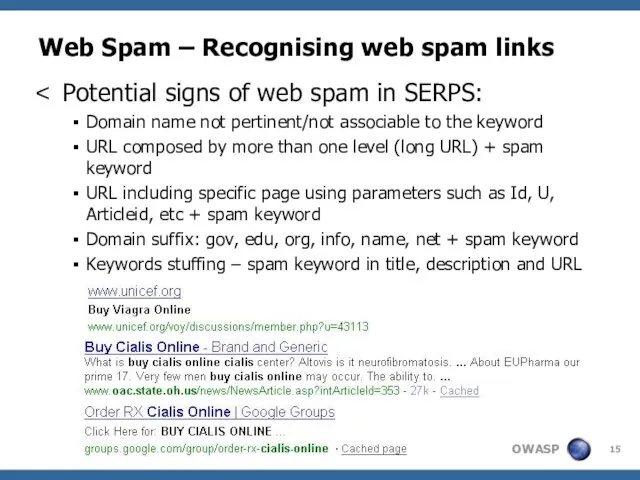
- 15. Potential signs of web spam in SERPS: Domain name not pertinent/not associable to the keyword URL
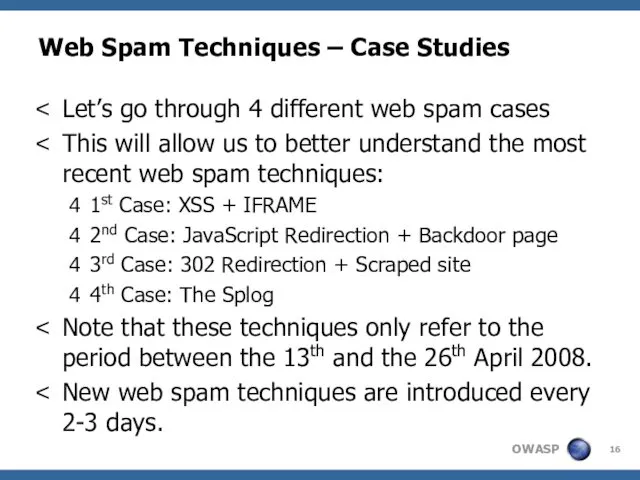
- 16. Web Spam Techniques – Case Studies Let’s go through 4 different web spam cases This will
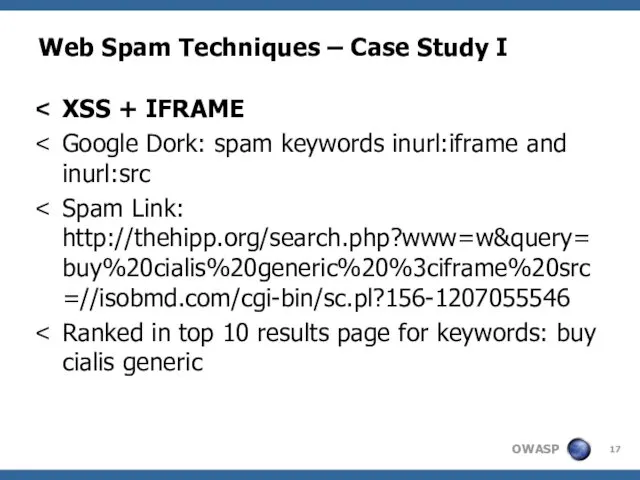
- 17. Web Spam Techniques – Case Study I XSS + IFRAME Google Dork: spam keywords inurl:iframe and
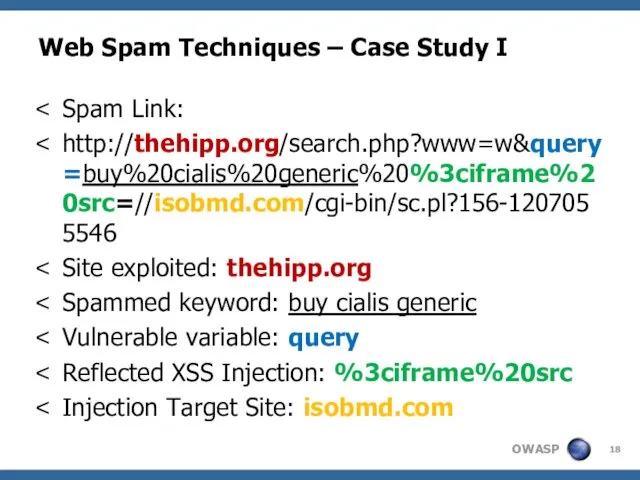
- 18. Web Spam Techniques – Case Study I Spam Link: http://thehipp.org/search.php?www=w&query=buy%20cialis%20generic%20%3ciframe%20src=//isobmd.com/cgi-bin/sc.pl?156-1207055546 Site exploited: thehipp.org Spammed keyword: buy
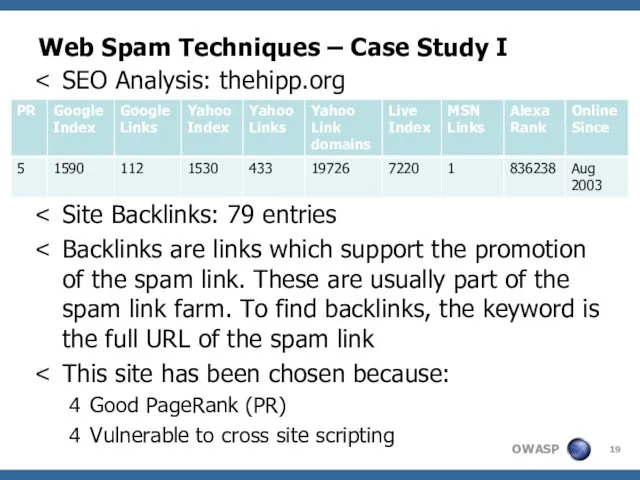
- 19. Web Spam Techniques – Case Study I SEO Analysis: thehipp.org PR: 5 Site Backlinks: 79 entries
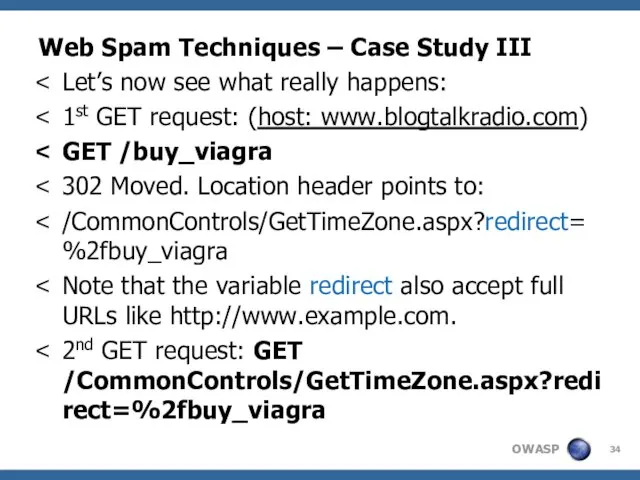
- 20. Web Spam Techniques – Case Study I Let’s now see what really happens: 1st GET request:
- 21. Web Spam Techniques – Case Study I 2nd GET request: (host: isobdm.com) GET /cgi-bin/sc.pl?156-1207055546' Server returns
- 22. Web Spam Techniques – Case Study I 3rd GET request: (host: www.finance-leaders.com) GET /feed3.php?keyword=156&feed=8&ref=http%3A//thehipp.org/search.php%3Fwww%3Dw%26query%3Dbuy%2520cialis%2520generic%2520%253ciframe%2520src%3D//isobmd.com/cgi-bin/sc.pl%3F156-1207055546 200 OK.
- 23. Web Spam Techniques – Case Study I 4th GET request: (host: genericpillsworld.com) GET /product/61/ 200 OK.
- 24. Web Spam Techniques – Case Study II JavaScript Redirection + Backdoor page Russian backdoor Google Dork:
- 25. Web Spam Techniques – Case Study II Spam Link: www.daemen.edu/academics/festival/management2007/downloads/thumbs/?item=678 Site exploited: daemen.edu Spammed keyword: official
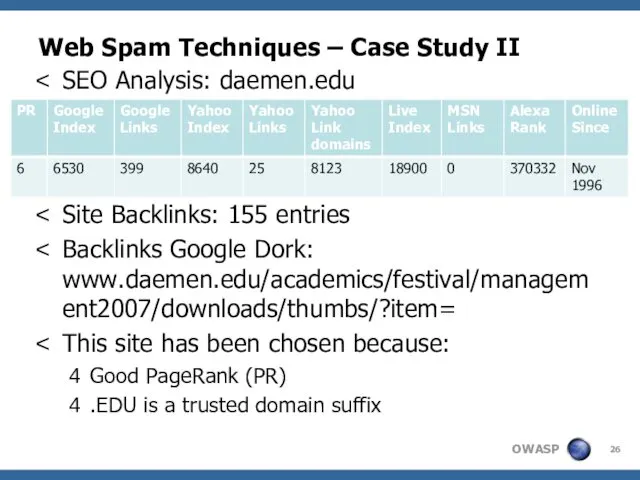
- 26. Web Spam Techniques – Case Study II SEO Analysis: daemen.edu PR: 5 Site Backlinks: 155 entries
- 27. Web Spam Techniques – Case Study II Let’s now see what really happens: 1st GET request:
- 28. Web Spam Techniques – Case Study II JavaScript disabled. Content extract: “you is find hearing medical
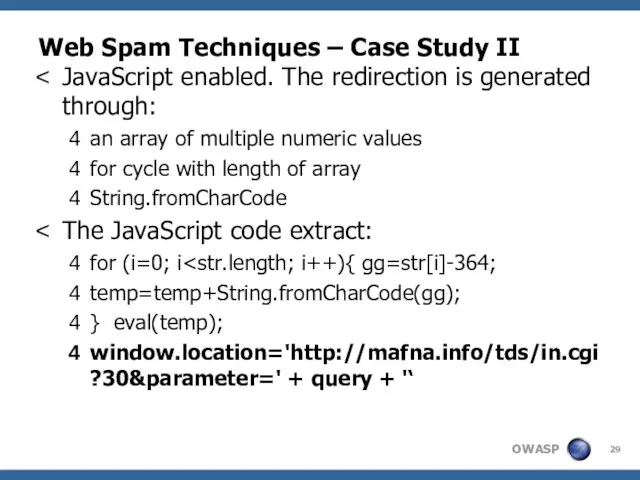
- 29. Web Spam Techniques – Case Study II JavaScript enabled. The redirection is generated through: an array
- 30. Web Spam Techniques – Case Study II Bad JavaScript is hosted on the site itself. Web
- 31. Web Spam Techniques – Case Study III 302 Redirection + Scraped site Google Dork: blogtalkradio.com/buy_viagra any
- 32. Web Spam Techniques – Case Study III Spam Link: http://www.blogtalkradio.com/buy_viagra Site exploited: blogtalkradio.com Spammed keyword: buy
- 33. Web Spam Techniques – Case Study III SEO Analysis: blogtalkradio.com PR: 5 Site Backlinks: 27100 entries
- 34. Web Spam Techniques – Case Study III Let’s now see what really happens: 1st GET request:
- 35. Web Spam Techniques – Case Study III Some considerations: Spammer uses 302 redirection for an internal
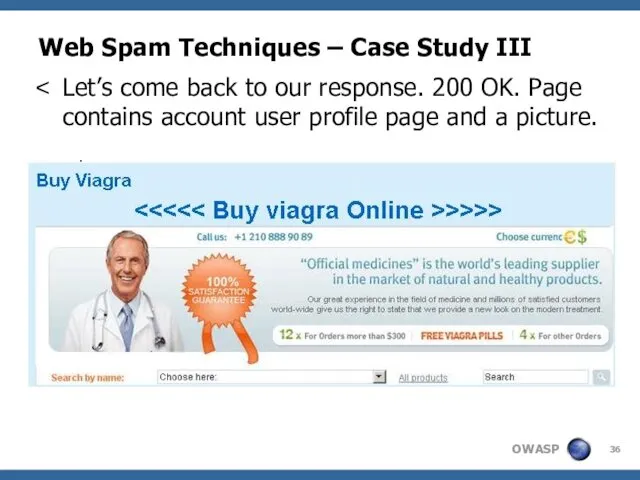
- 36. Web Spam Techniques – Case Study III Let’s come back to our response. 200 OK. Page
- 37. Web Spam Techniques – Case Study III Picture link points to: http://vip-side.com/in.cgi?16¶metr=Viagra 3rd GET request to
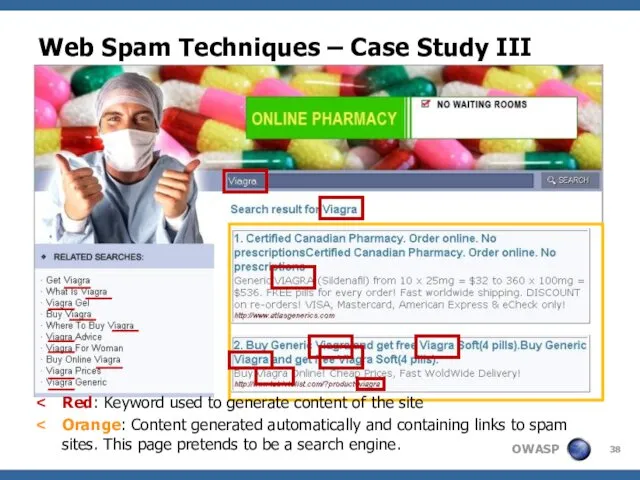
- 38. Web Spam Techniques – Case Study III Red: Keyword used to generate content of the site
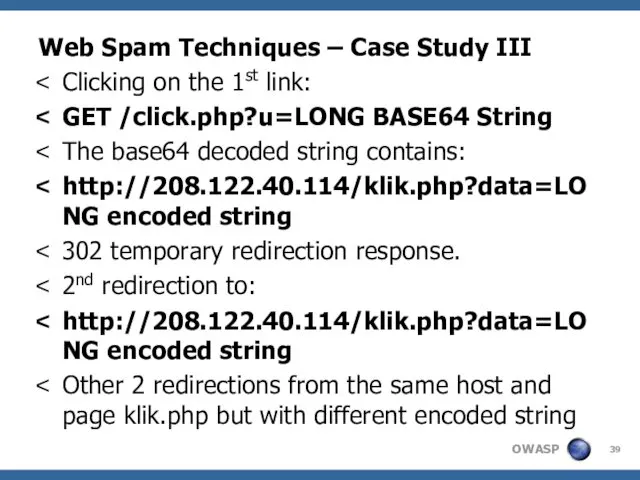
- 39. Web Spam Techniques – Case Study III Clicking on the 1st link: GET /click.php?u=LONG BASE64 String
- 40. Web Spam Techniques – Case Study III And finally we land here: http://www.tabletslist.com/?product=viagra 200 OK. Pharmacy
- 41. Web Spam Techniques – Case Study IV The Splog (Blog Spam = Splog) Google Dorks: inurl:certified
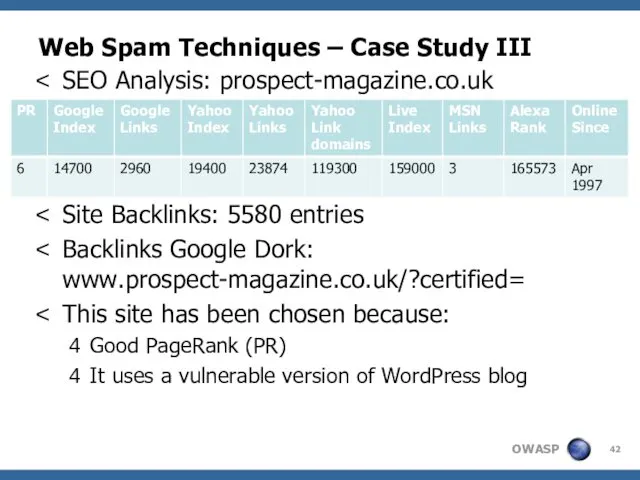
- 42. Web Spam Techniques – Case Study III SEO Analysis: prospect-magazine.co.uk PR: 5 Site Backlinks: 5580 entries
- 43. Web Spam Techniques – Case Study IV Let’s now see what really happens: 1st GET request:
- 44. Web Spam Techniques – Case Study IV Page includes JavaScript which checks: URL for the following
- 45. Web Spam Techniques – Case Study IV JavaScript Extract: document.URL.indexOf("?certified=")!=-1 || document.URL.indexOf("?discount=")!=-1 || document.URL.indexOf("?fda-approved=")!=-1) && ((q=r.indexOf("?"+t+"="))!=-1||(q=r.indexOf("&"+t+"="))!=-1)){window.location="http://sevensearch.net/delta/search.php?q="+r.substring(q+2+t.length).split("&")[0];}
- 46. Web Spam Techniques – Case Study IV Back to our redirection – 2nd GET request: (host:
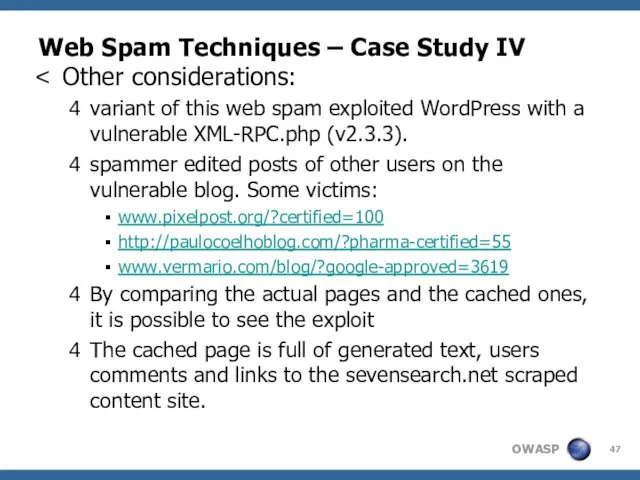
- 47. Web Spam Techniques – Case Study IV Other considerations: variant of this web spam exploited WordPress
- 48. Web Spam – Security Considerations Web application vulnerabilities can be used for other purposes as well:
- 49. Web Spam – Security Recommendations Beside the standard security recommendations for any web application, it is
- 50. Web Spam Techniques – Questions? Thanks!!!! And if u notice some nice web spam techniques, please
- 51. Web Spam Techniques - Disclaimer All SEO results and statistics have been taken during the following
- 52. Web Spam Techniques - References Web Spam, Propaganda and Trust http://airweb.cse.lehigh.edu/2005/metaxas.pdf Detecting Spam Web Pages through
- 54. Скачать презентацию


























![Web Spam Techniques – Case Study IV JavaScript Extract: document.URL.indexOf("?certified=")!=-1 || document.URL.indexOf("?discount=")!=-1 || document.URL.indexOf("?fda-approved=")!=-1) && ((q=r.indexOf("?"+t+"="))!=-1||(q=r.indexOf("&"+t+"="))!=-1)){window.location="http://sevensearch.net/delta/search.php?q="+r.substring(q+2+t.length).split("&")[0];}](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/93693/slide-44.jpg)





 Компьютерная графика (Autodesk 3ds max). Создание и работа с примитивами. Управление объектами. (Лекция 2.1)
Компьютерная графика (Autodesk 3ds max). Создание и работа с примитивами. Управление объектами. (Лекция 2.1) СМИ нового формата. Журналисты современной информации
СМИ нового формата. Журналисты современной информации Моделирование и его разновидности
Моделирование и его разновидности Развитие детей с помощью курсов робототехники
Развитие детей с помощью курсов робототехники Пользовательские хуки
Пользовательские хуки Электронный учебник по информатике
Электронный учебник по информатике Операционные системы. Введение, основные понятия и термины. (Лекция 1)
Операционные системы. Введение, основные понятия и термины. (Лекция 1) Логические элементы компьютера
Логические элементы компьютера Robots
Robots Introduction to informational and communication technologies
Introduction to informational and communication technologies Операционные системы
Операционные системы Викторина по информатике Инфознайка. 6 класс
Викторина по информатике Инфознайка. 6 класс Игра Удивительный мир информатики
Игра Удивительный мир информатики Структура Web приложений
Структура Web приложений Стандартные функции языка CLIPS. Стандартные арифметические функции
Стандартные функции языка CLIPS. Стандартные арифметические функции Игра Самый умный. Информатика
Игра Самый умный. Информатика Информационные процессы и системы в правовой сфере
Информационные процессы и системы в правовой сфере Основы 3D-моделирования машиностроительных объектов
Основы 3D-моделирования машиностроительных объектов Обзор программных продуктов дистрибутива Линукс Юниор
Обзор программных продуктов дистрибутива Линукс Юниор Применение ИКТ на уроках естествознания
Применение ИКТ на уроках естествознания Час кода в России
Час кода в России Subversion
Subversion Проектирование ПО ИС. Лекция 7
Проектирование ПО ИС. Лекция 7 Computer graphics
Computer graphics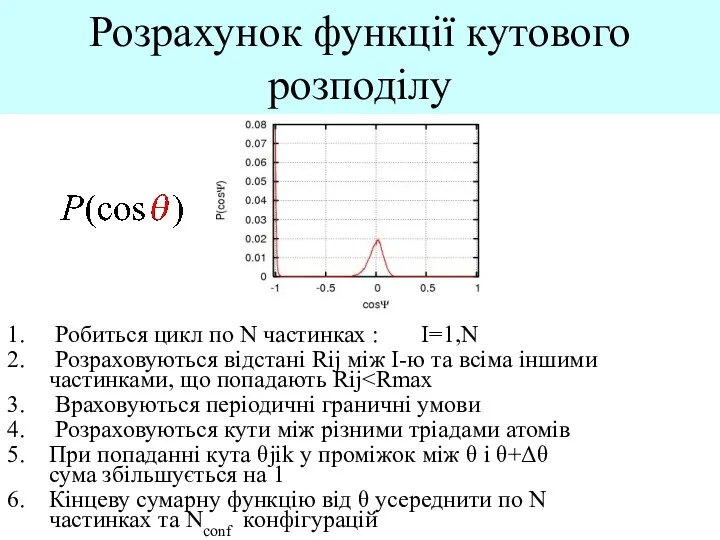 Розрахунок функції кутового розподілу
Розрахунок функції кутового розподілу Изучение графического редактора PAINT
Изучение графического редактора PAINT Презентация Ребусы
Презентация Ребусы Declaring PL/SQL Variables. (Lecture 2)
Declaring PL/SQL Variables. (Lecture 2)