Содержание
- 2. Transport layer: roadmap Transport-layer services Multiplexing and demultiplexing Connectionless transport: UDP Principles of reliable data transfer
- 3. Transport services and protocols provide logical communication between application processes running on different hosts mobile network
- 4. Transport vs. network layer services and protocols Transport Layer: 3-
- 5. Transport vs. network layer services and protocols network layer: logical communication between hosts transport layer: logical
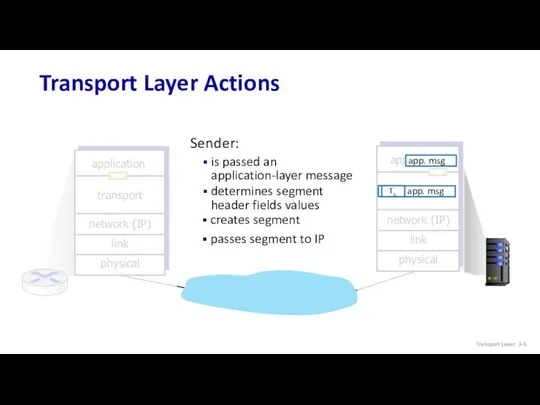
- 6. transport Transport Layer Actions Sender: is passed an application-layer message determines segment header fields values creates
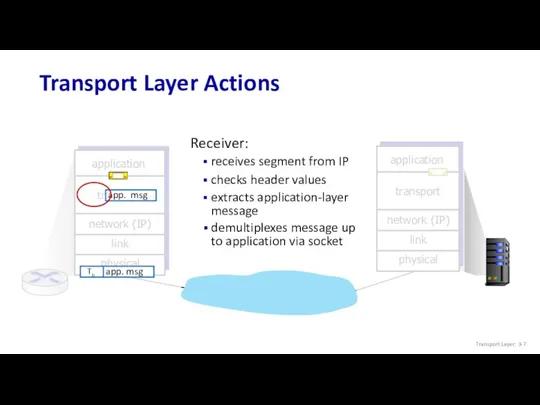
- 7. transport Transport Layer Actions transport Receiver: extracts application-layer message checks header values receives segment from IP
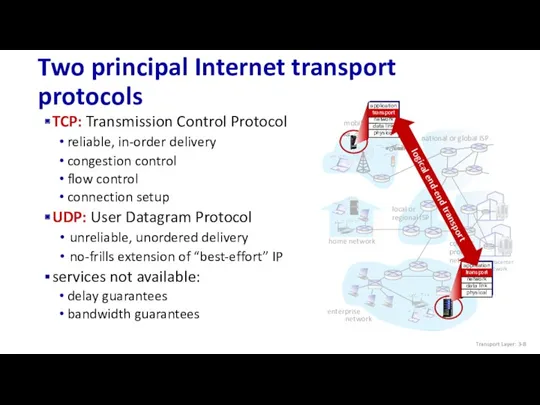
- 8. Two principal Internet transport protocols mobile network home network enterprise network national or global ISP local
- 9. Topic 3: roadmap Transport-layer services Multiplexing and demultiplexing Connectionless transport: UDP Principles of reliable data transfer
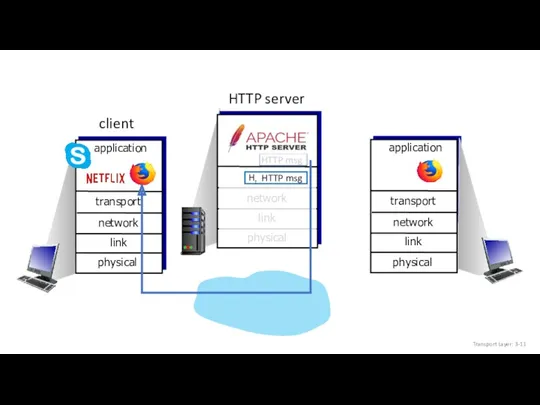
- 10. HTTP msg Transport Layer: 3-
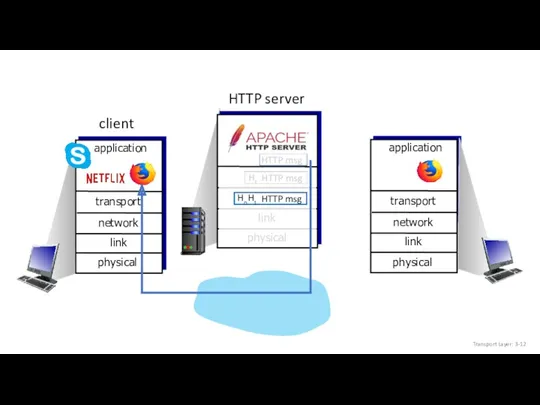
- 11. HTTP msg Transport Layer: 3-
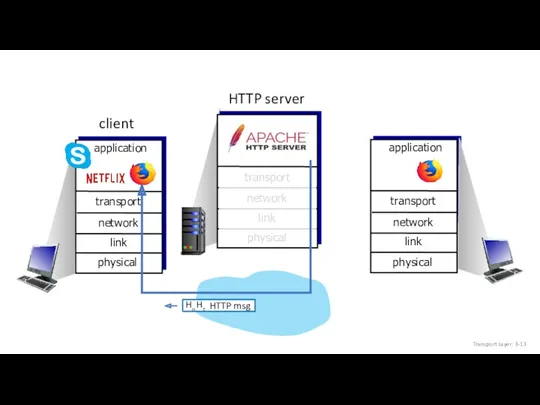
- 12. HTTP msg Transport Layer: 3-
- 13. Transport Layer: 3-
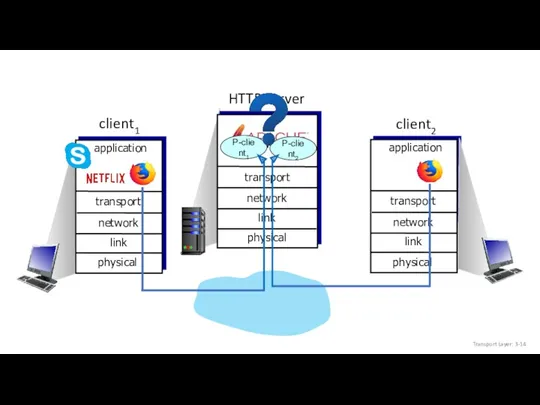
- 14. P-client1 P-client2 Transport Layer: 3-
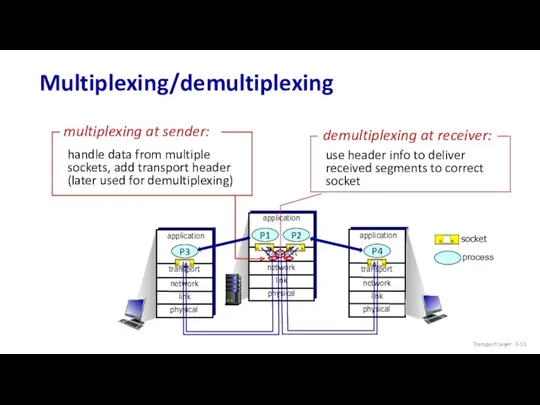
- 15. Multiplexing/demultiplexing process socket transport application physical link network P2 P1 transport application physical link network P4
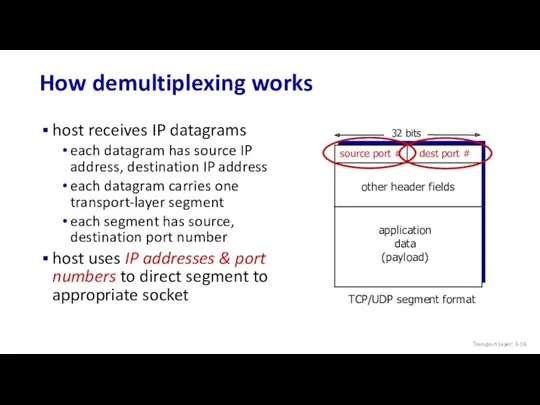
- 16. How demultiplexing works host receives IP datagrams each datagram has source IP address, destination IP address
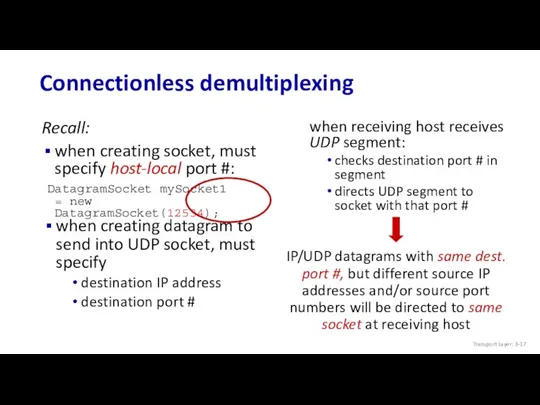
- 17. Connectionless demultiplexing Recall: when creating socket, must specify host-local port #: DatagramSocket mySocket1 = new DatagramSocket(12534);
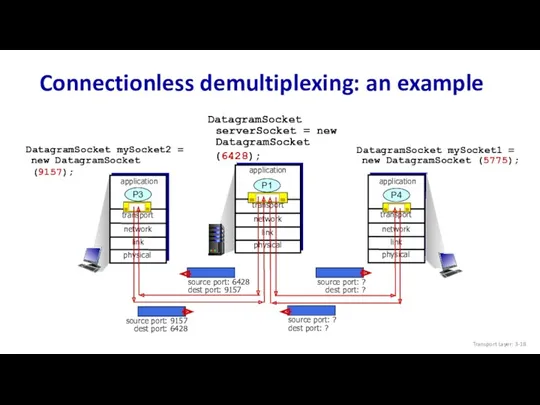
- 18. Connectionless demultiplexing: an example DatagramSocket serverSocket = new DatagramSocket (6428); transport application physical link network P3
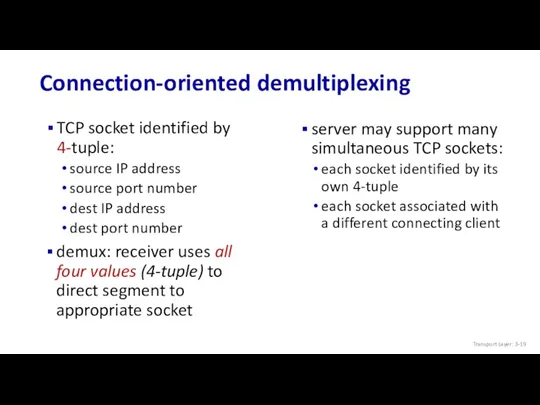
- 19. Connection-oriented demultiplexing TCP socket identified by 4-tuple: source IP address source port number dest IP address
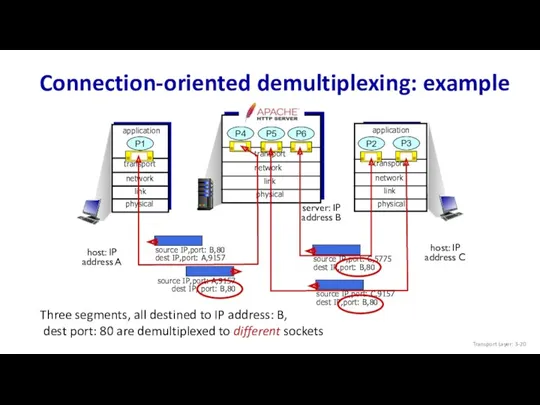
- 20. Connection-oriented demultiplexing: example transport application physical link network P1 transport application physical link P4 transport application
- 21. Summary Multiplexing, demultiplexing: based on segment, datagram header field values UDP: demultiplexing using destination port number
- 22. Topic 3: roadmap Transport-layer services Multiplexing and demultiplexing Connectionless transport: UDP Principles of reliable data transfer
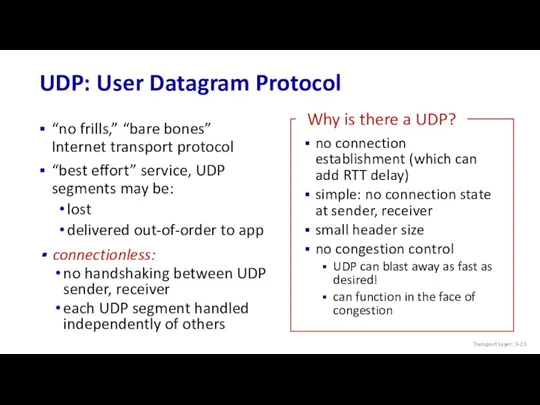
- 23. UDP: User Datagram Protocol “no frills,” “bare bones” Internet transport protocol “best effort” service, UDP segments
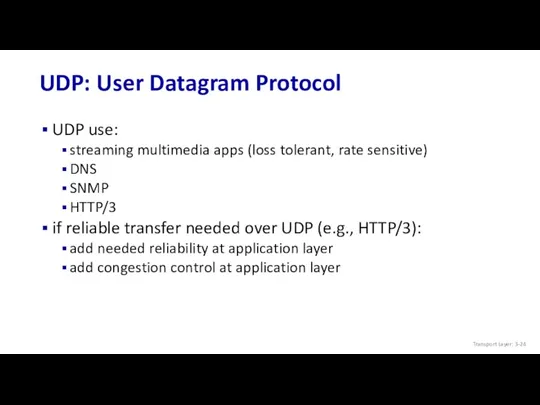
- 24. UDP: User Datagram Protocol UDP use: streaming multimedia apps (loss tolerant, rate sensitive) DNS SNMP HTTP/3
- 25. UDP: User Datagram Protocol [RFC 768] Transport Layer: 3-
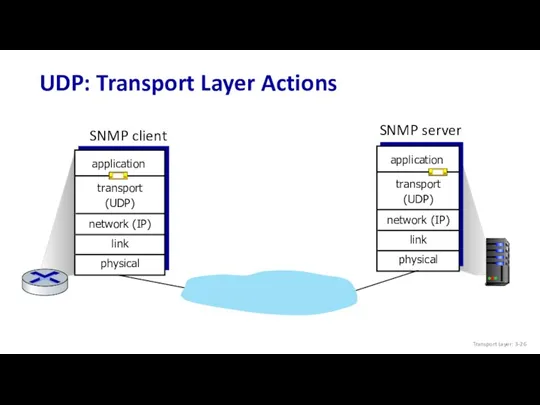
- 26. SNMP server SNMP client UDP: Transport Layer Actions Transport Layer: 3-
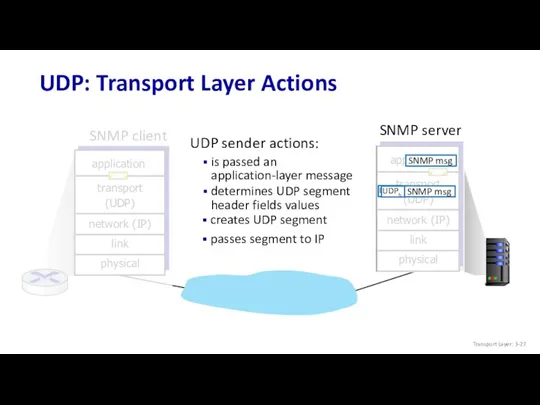
- 27. SNMP server SNMP client UDP: Transport Layer Actions UDP sender actions: is passed an application-layer message
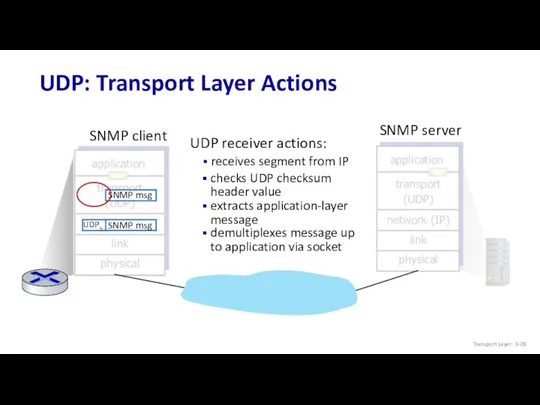
- 28. SNMP server SNMP client UDP: Transport Layer Actions UDP receiver actions: extracts application-layer message checks UDP
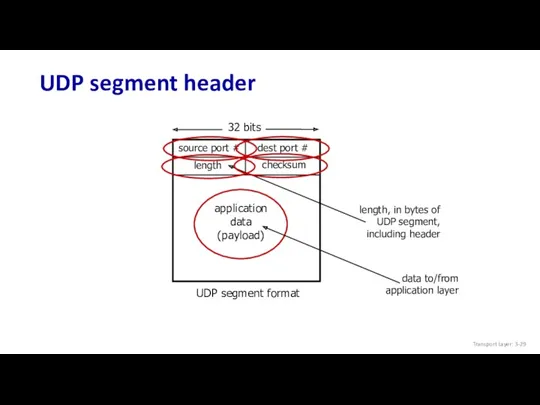
- 29. UDP segment header source port # dest port # 32 bits application data (payload) UDP segment
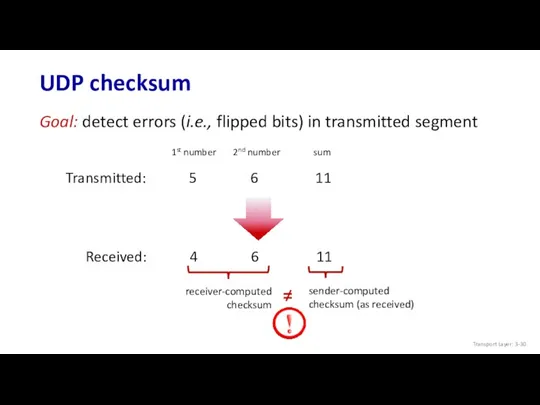
- 30. UDP checksum Transmitted: 5 6 11 Goal: detect errors (i.e., flipped bits) in transmitted segment Received:
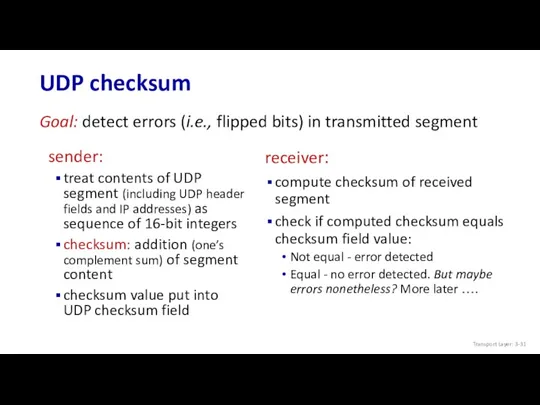
- 31. UDP checksum sender: treat contents of UDP segment (including UDP header fields and IP addresses) as
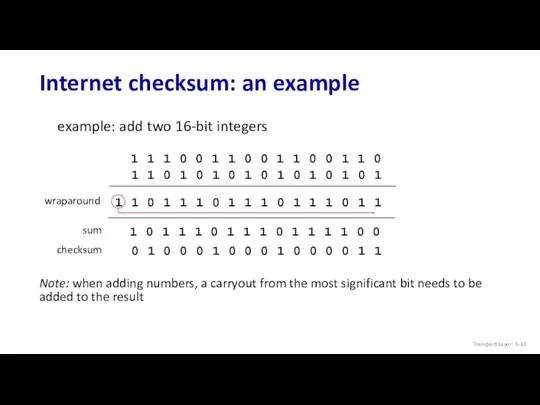
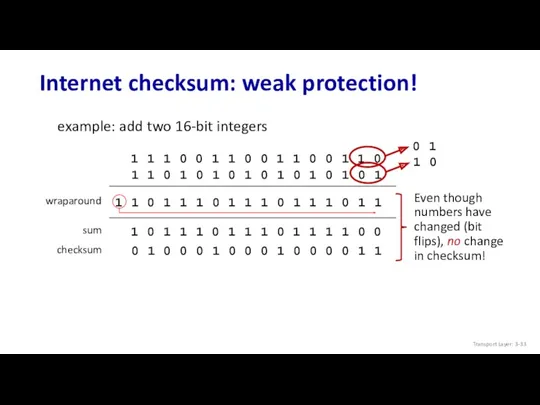
- 32. Internet checksum: an example example: add two 16-bit integers sum checksum Note: when adding numbers, a
- 33. Internet checksum: weak protection! example: add two 16-bit integers sum checksum 1 1 1 0 0
- 34. Summary: UDP “no frills” protocol: segments may be lost, delivered out of order best effort service:
- 35. Topic 3: roadmap Transport-layer services Multiplexing and demultiplexing Connectionless transport: UDP Principles of reliable data transfer
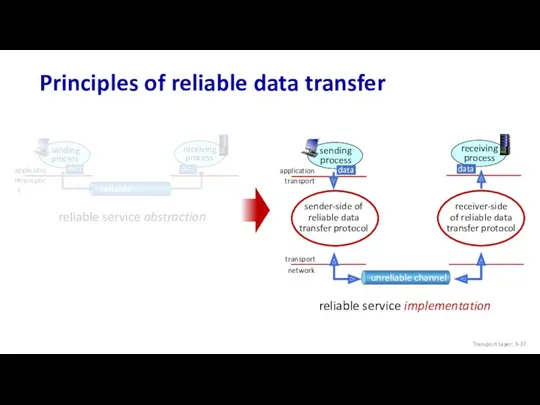
- 36. Principles of reliable data transfer Transport Layer: 3-
- 37. Principles of reliable data transfer Transport Layer: 3-
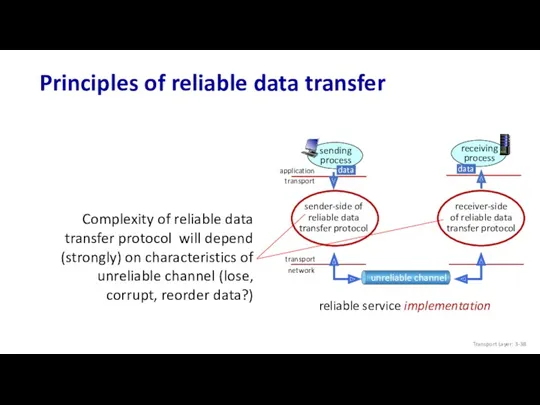
- 38. Principles of reliable data transfer Transport Layer: 3-
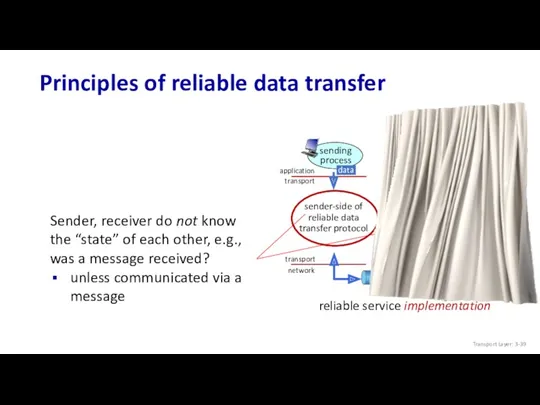
- 39. Principles of reliable data transfer Transport Layer: 3-
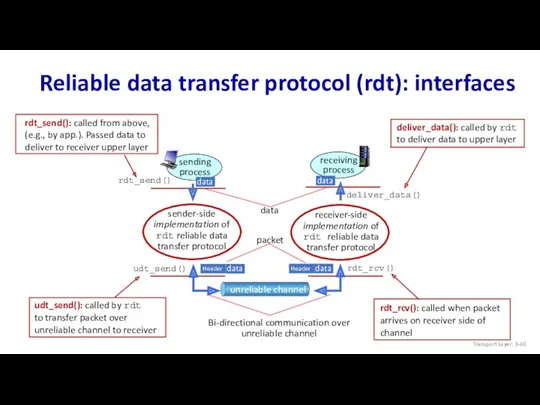
- 40. Reliable data transfer protocol (rdt): interfaces Transport Layer: 3-
- 41. Reliable data transfer: getting started We will: incrementally develop sender, receiver sides of reliable data transfer
- 42. rdt1.0: reliable transfer over a reliable channel underlying channel perfectly reliable no bit errors no loss
- 43. rdt2.0: channel with bit errors underlying channel may flip bits in packet checksum (e.g., Internet checksum)
- 44. rdt2.0: channel with bit errors underlying channel may flip bits in packet checksum to detect bit
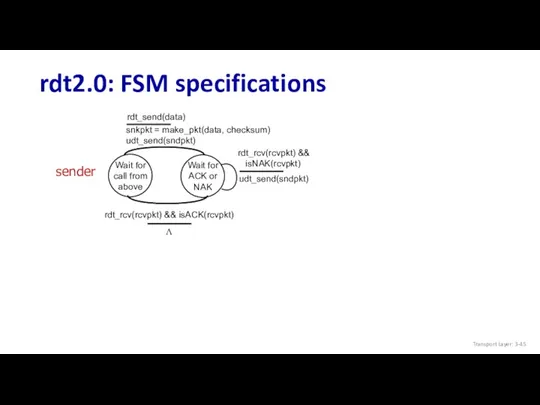
- 45. rdt2.0: FSM specifications Wait for call from above Wait for call from below sender receiver rdt_rcv(rcvpkt)
- 46. rdt2.0: FSM specification Wait for call from above Wait for call from below sender receiver Note:
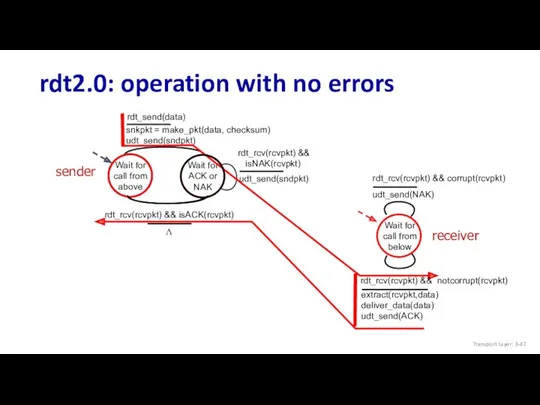
- 47. rdt2.0: operation with no errors Wait for call from above snkpkt = make_pkt(data, checksum) udt_send(sndpkt) udt_send(sndpkt)
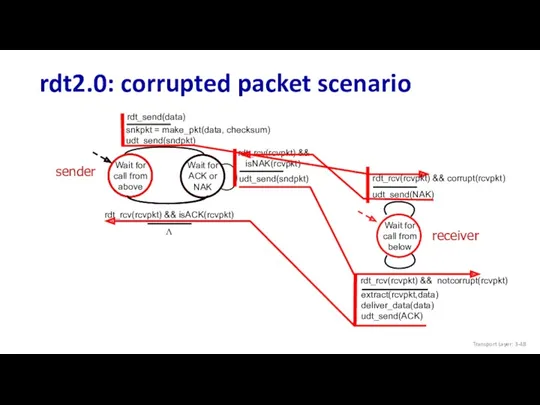
- 48. rdt2.0: corrupted packet scenario Wait for call from above snkpkt = make_pkt(data, checksum) udt_send(sndpkt) udt_send(sndpkt) rdt_rcv(rcvpkt)
- 49. rdt2.0 has a fatal flaw! what happens if ACK/NAK corrupted? sender doesn’t know what happened at
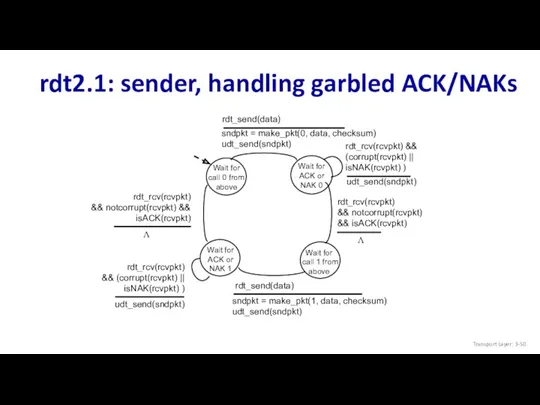
- 50. rdt2.1: sender, handling garbled ACK/NAKs Wait for call 0 from above Transport Layer: 3-
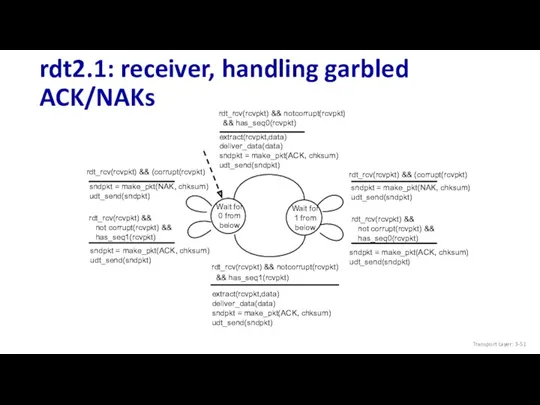
- 51. rdt2.1: receiver, handling garbled ACK/NAKs Transport Layer: 3-
- 52. rdt2.1: discussion sender: seq # added to pkt two seq. #s (0,1) will suffice. Why? must
- 53. rdt2.2: a NAK-free protocol same functionality as rdt2.1, using ACKs only instead of NAK, receiver sends
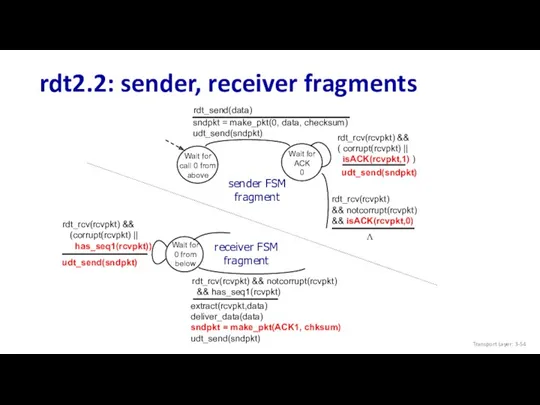
- 54. rdt2.2: sender, receiver fragments Transport Layer: 3-
- 55. rdt3.0: channels with errors and loss New channel assumption: underlying channel can also lose packets (data,
- 56. rdt3.0: channels with errors and loss Approach: sender waits “reasonable” amount of time for ACK retransmits
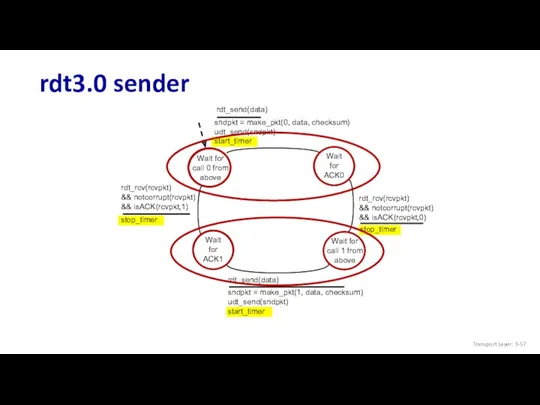
- 57. rdt3.0 sender Transport Layer: 3-
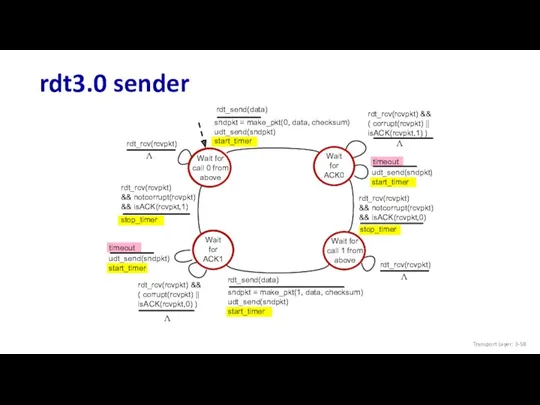
- 58. rdt3.0 sender Transport Layer: 3-
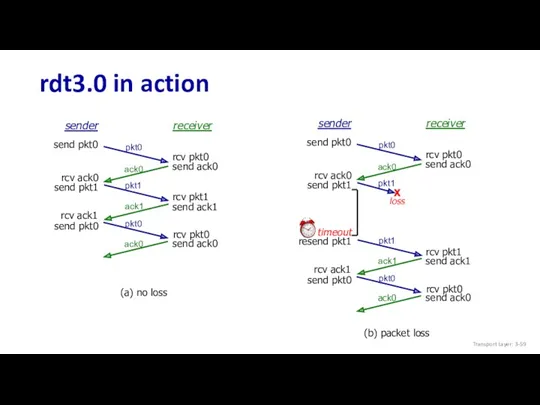
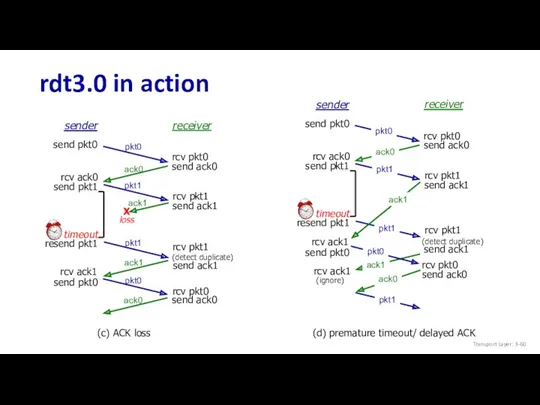
- 59. rdt3.0 in action sender receiver rcv pkt1 rcv pkt0 send ack0 send ack1 send ack0 rcv
- 60. rdt3.0 in action rcv pkt1 send ack1 (detect duplicate) sender receiver rcv pkt1 rcv pkt0 send
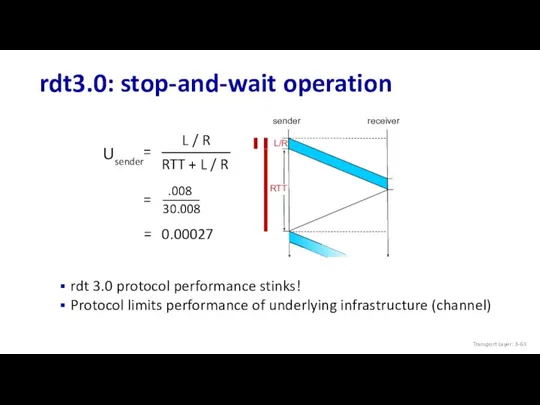
- 61. Performance of rdt3.0 (stop-and-wait) example: 1 Gbps link, 15 ms prop. delay, 8000 bit packet U
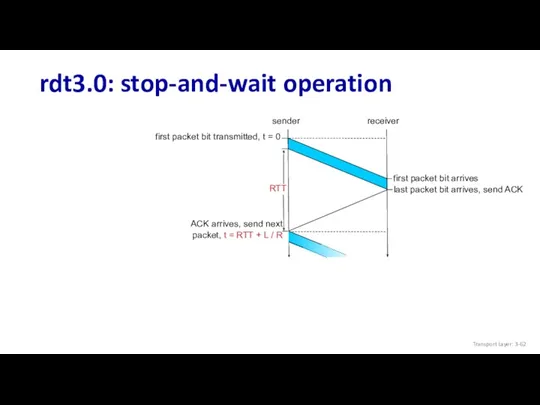
- 62. rdt3.0: stop-and-wait operation Transport Layer: 3-
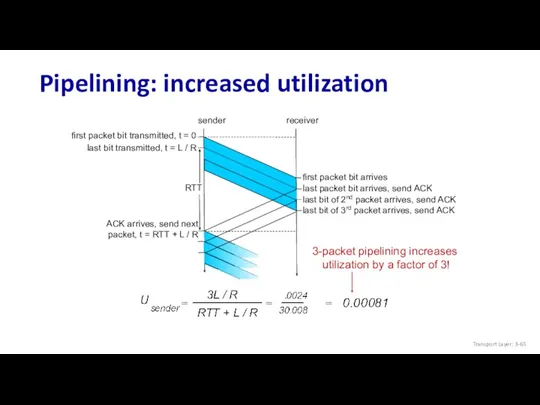
- 63. rdt3.0: stop-and-wait operation sender receiver L / R RTT + L / R rdt 3.0 protocol
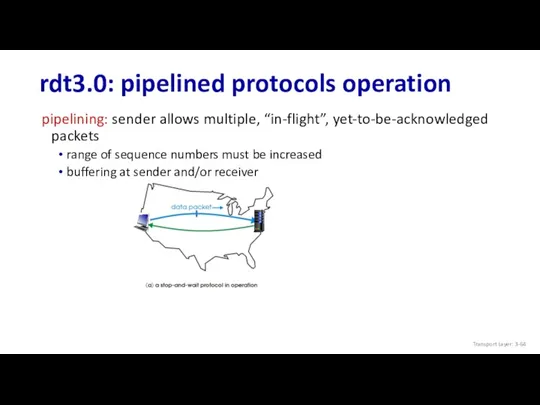
- 64. rdt3.0: pipelined protocols operation pipelining: sender allows multiple, “in-flight”, yet-to-be-acknowledged packets range of sequence numbers must
- 65. Pipelining: increased utilization Transport Layer: 3-
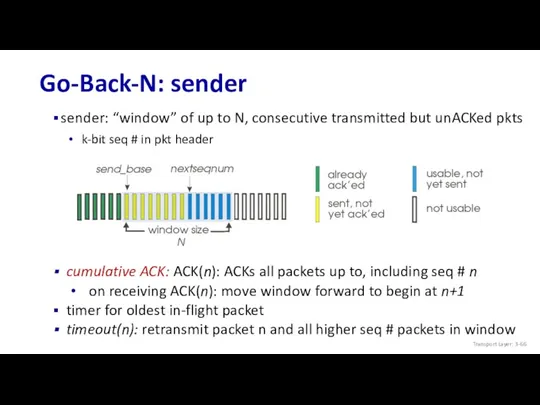
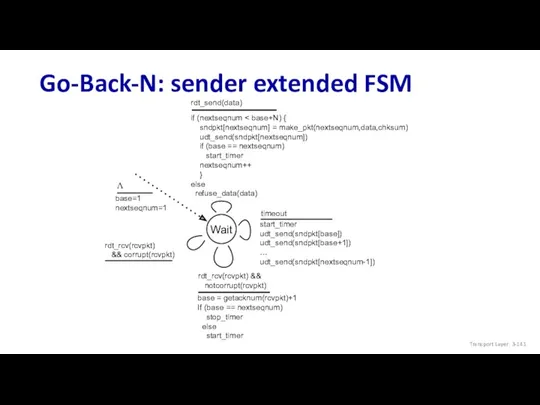
- 66. Go-Back-N: sender sender: “window” of up to N, consecutive transmitted but unACKed pkts k-bit seq #
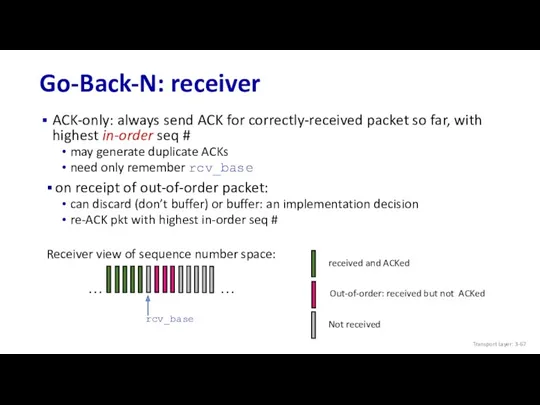
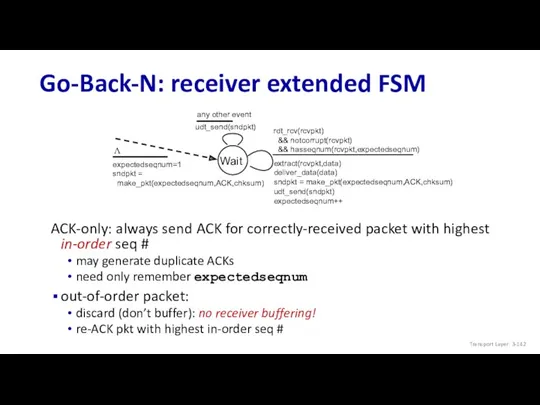
- 67. Go-Back-N: receiver ACK-only: always send ACK for correctly-received packet so far, with highest in-order seq #
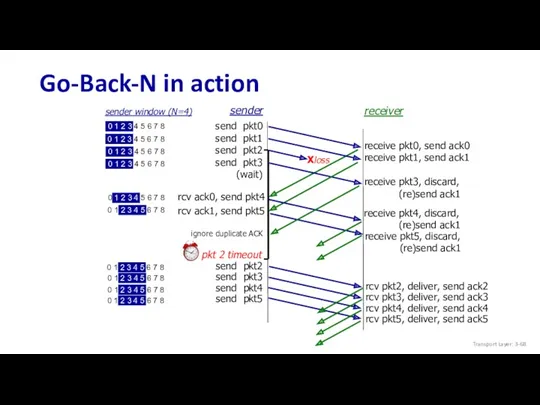
- 68. Go-Back-N in action send pkt0 send pkt1 send pkt2 send pkt3 (wait) sender receiver receive pkt0,
- 69. Selective repeat receiver individually acknowledges all correctly received packets buffers packets, as needed, for eventual in-order
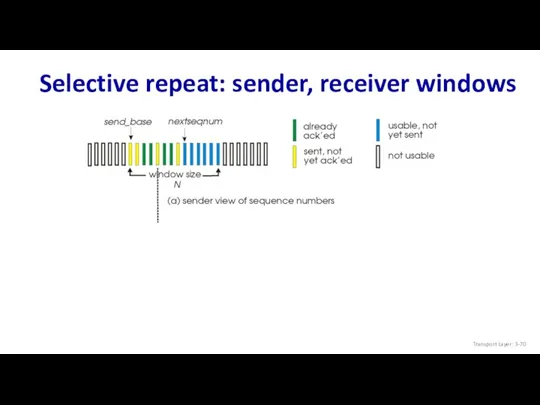
- 70. Selective repeat: sender, receiver windows Transport Layer: 3-
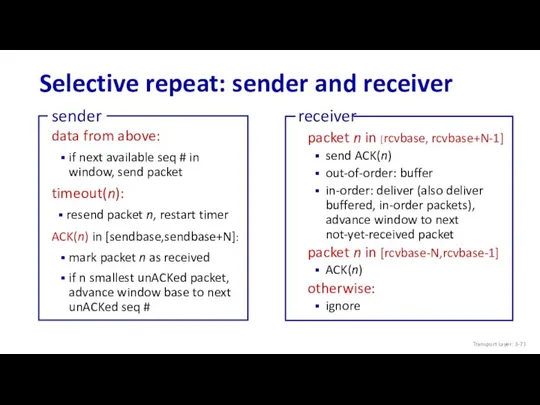
- 71. Selective repeat: sender and receiver data from above: if next available seq # in window, send
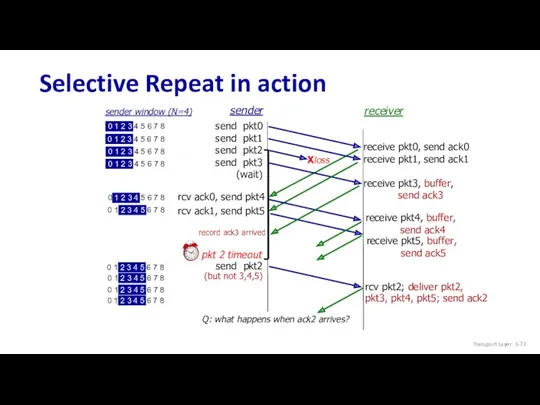
- 72. Selective Repeat in action send pkt0 send pkt1 send pkt2 send pkt3 (wait) sender receiver send
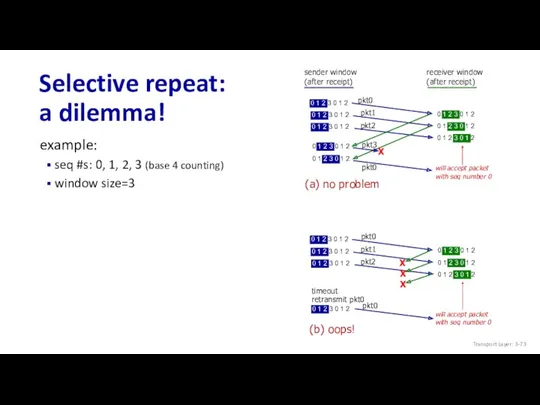
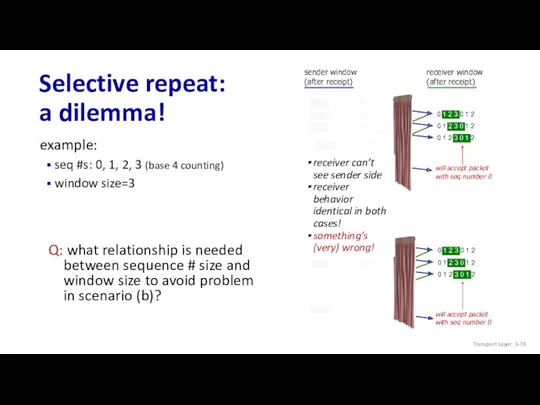
- 73. Selective repeat: a dilemma! (b) oops! (a) no problem example: seq #s: 0, 1, 2, 3
- 74. Selective repeat: a dilemma! Q: what relationship is needed between sequence # size and window size
- 75. Topic 3: roadmap Transport-layer services Multiplexing and demultiplexing Connectionless transport: UDP Principles of reliable data transfer
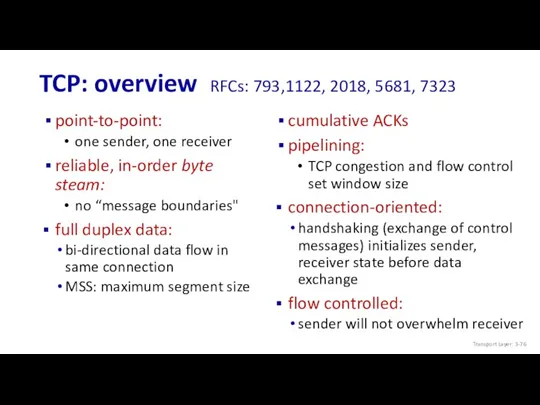
- 76. TCP: overview RFCs: 793,1122, 2018, 5681, 7323 cumulative ACKs pipelining: TCP congestion and flow control set
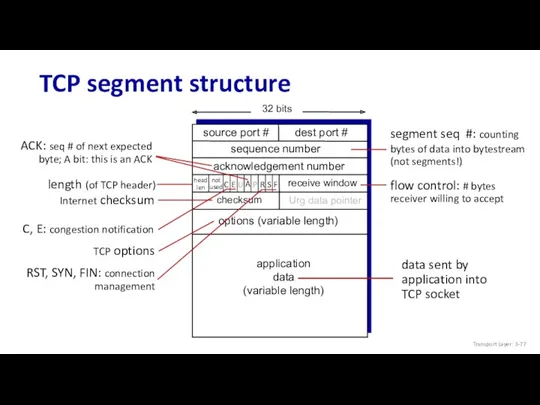
- 77. TCP segment structure not used Transport Layer: 3-
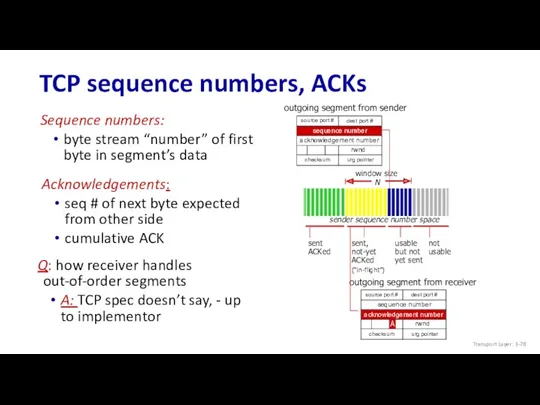
- 78. TCP sequence numbers, ACKs Sequence numbers: byte stream “number” of first byte in segment’s data sent
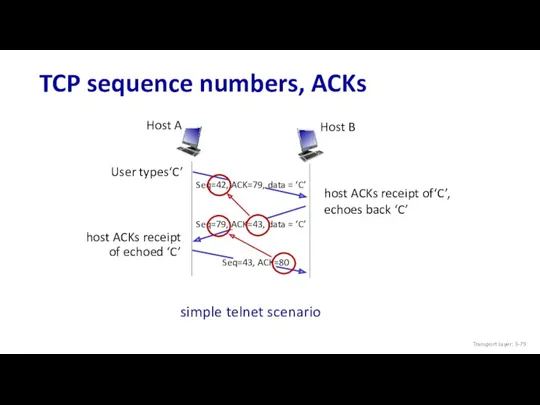
- 79. TCP sequence numbers, ACKs host ACKs receipt of echoed ‘C’ host ACKs receipt of‘C’, echoes back
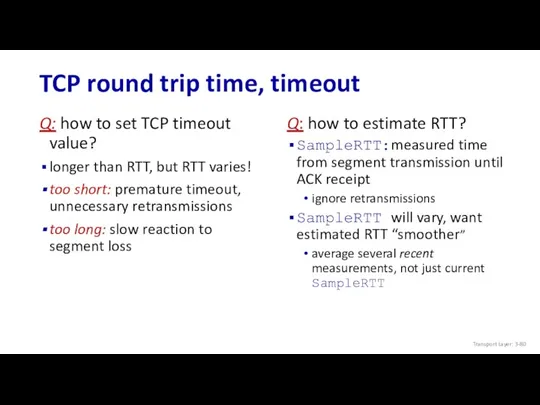
- 80. TCP round trip time, timeout Q: how to set TCP timeout value? longer than RTT, but
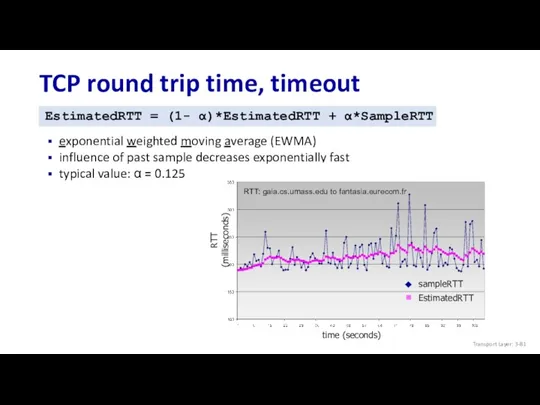
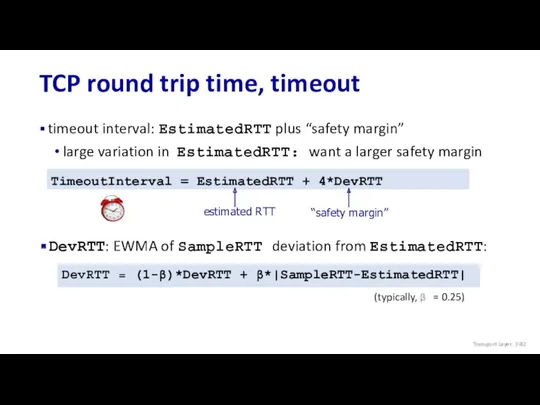
- 81. TCP round trip time, timeout EstimatedRTT = (1- α)*EstimatedRTT + α*SampleRTT exponential weighted moving average (EWMA)
- 82. TCP round trip time, timeout timeout interval: EstimatedRTT plus “safety margin” large variation in EstimatedRTT: want
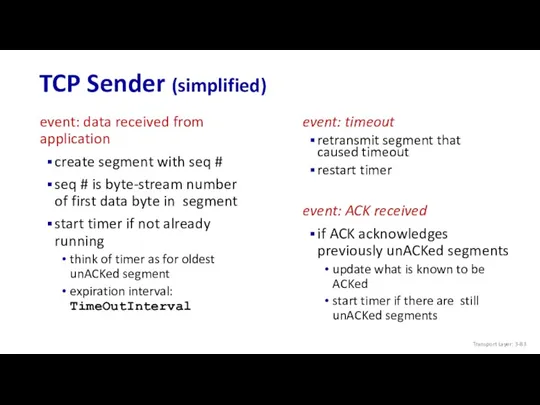
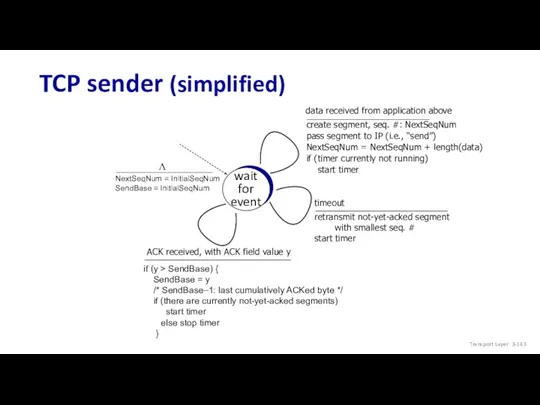
- 83. TCP Sender (simplified) event: data received from application create segment with seq # seq # is
- 84. TCP Receiver: ACK generation [RFC 5681] Event at receiver arrival of in-order segment with expected seq
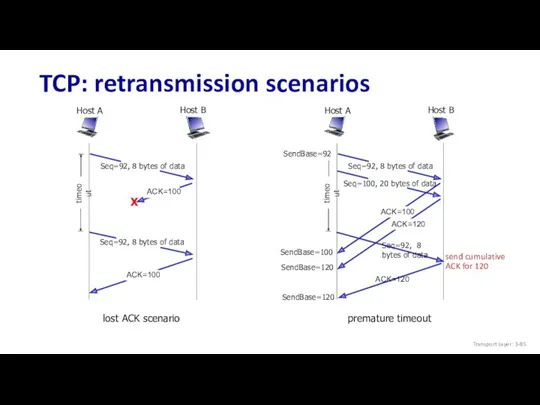
- 85. TCP: retransmission scenarios lost ACK scenario Host B Host A premature timeout Host B Host A
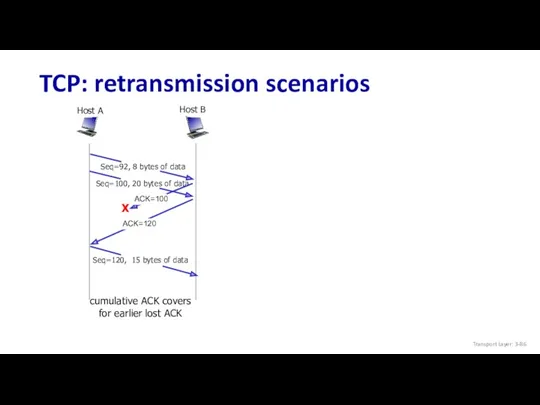
- 86. TCP: retransmission scenarios cumulative ACK covers for earlier lost ACK Host B Host A Seq=92, 8
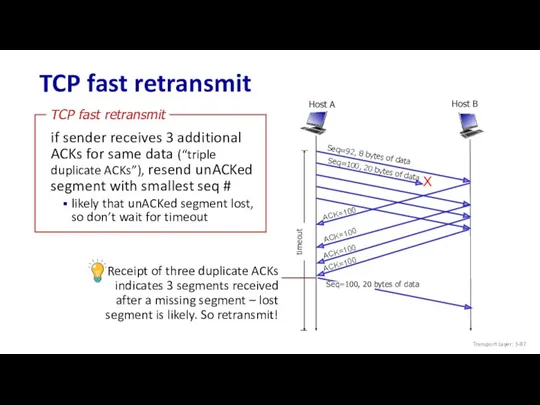
- 87. TCP fast retransmit Host B Host A Transport Layer: 3-
- 88. Topic 3: roadmap Transport-layer services Multiplexing and demultiplexing Connectionless transport: UDP Principles of reliable data transfer
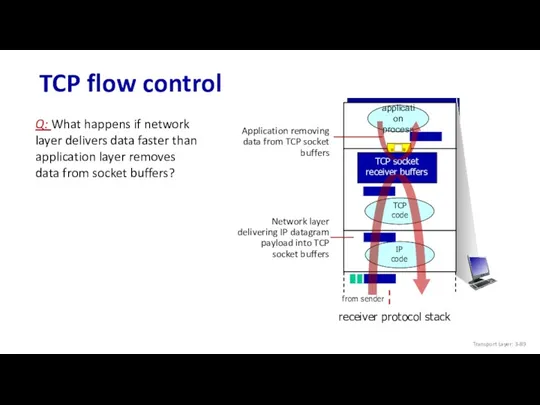
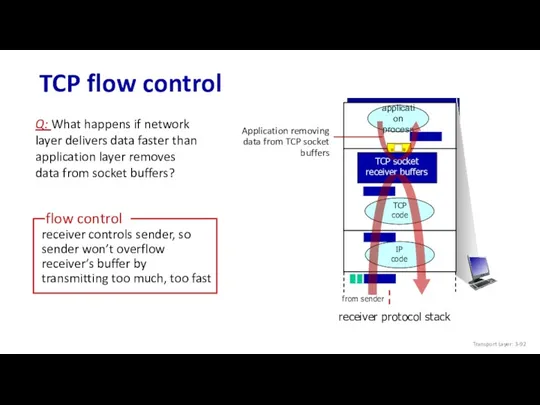
- 89. TCP flow control application process TCP code IP code receiver protocol stack Q: What happens if
- 90. TCP flow control application process TCP code IP code receiver protocol stack Q: What happens if
- 91. TCP flow control application process TCP code IP code receiver protocol stack Q: What happens if
- 92. TCP flow control application process TCP code IP code receiver protocol stack Q: What happens if
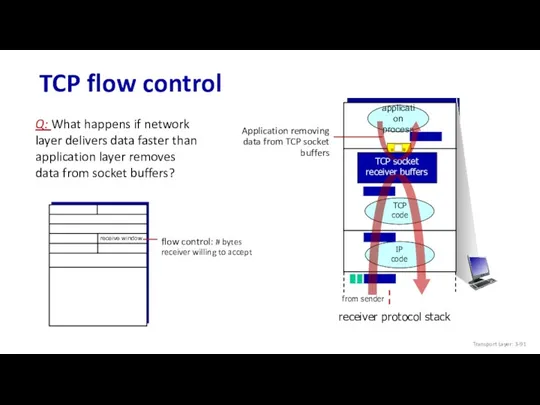
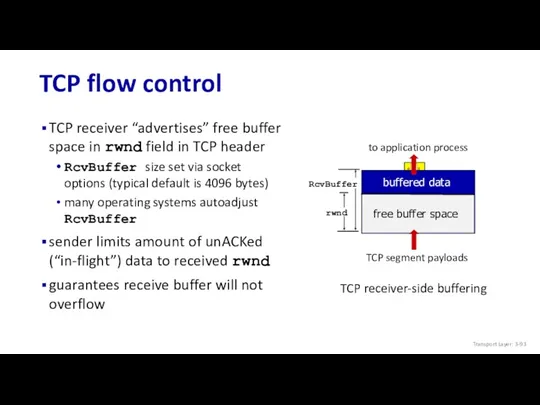
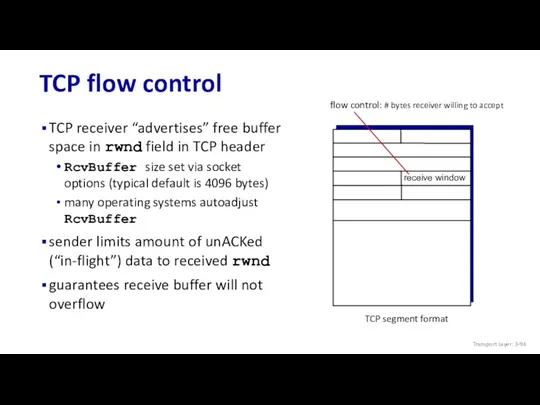
- 93. TCP flow control TCP receiver “advertises” free buffer space in rwnd field in TCP header RcvBuffer
- 94. TCP flow control TCP receiver “advertises” free buffer space in rwnd field in TCP header RcvBuffer
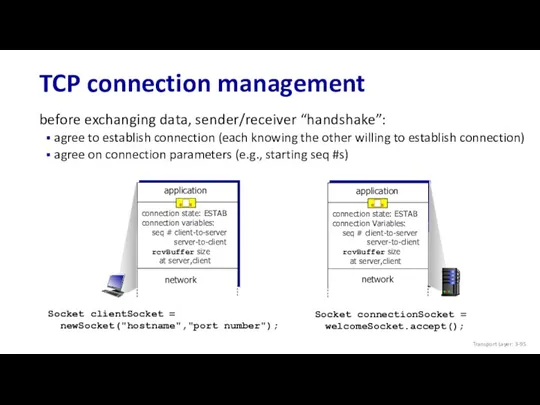
- 95. TCP connection management before exchanging data, sender/receiver “handshake”: agree to establish connection (each knowing the other
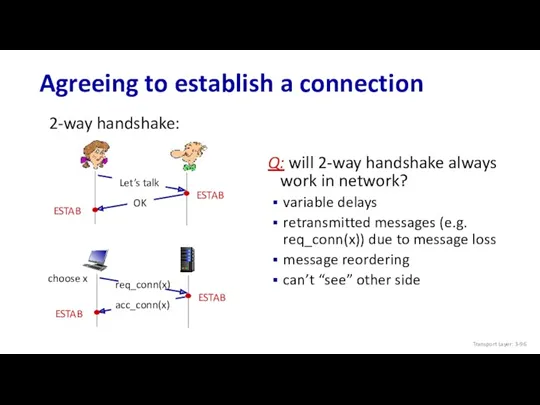
- 96. Agreeing to establish a connection Q: will 2-way handshake always work in network? variable delays retransmitted
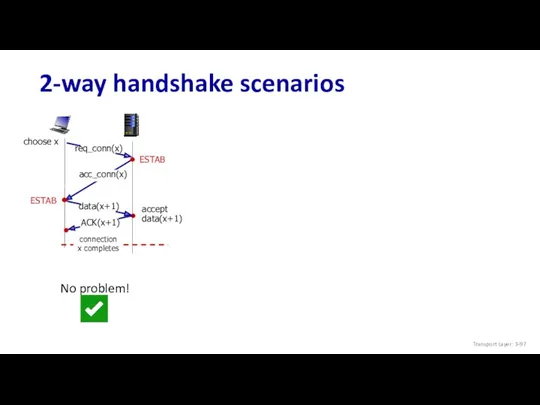
- 97. 2-way handshake scenarios Transport Layer: 3-
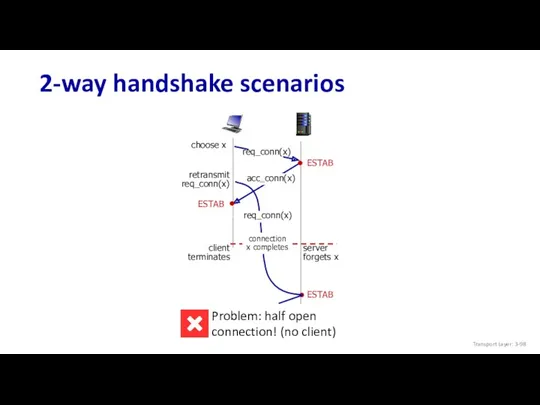
- 98. 2-way handshake scenarios Transport Layer: 3-
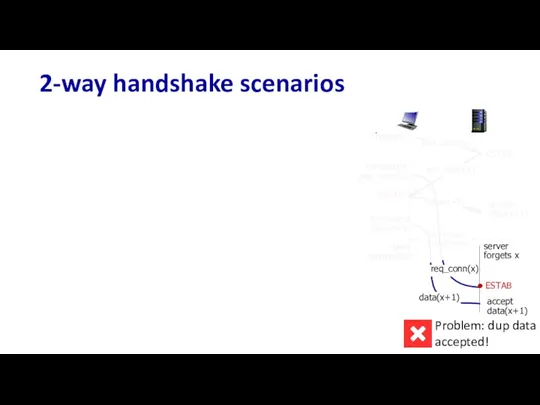
- 99. 2-way handshake scenarios
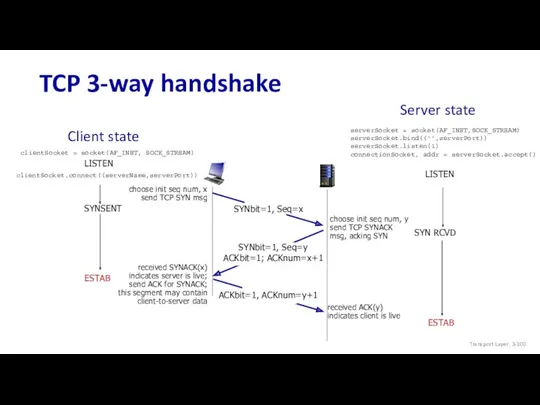
- 100. TCP 3-way handshake ESTAB Client state LISTEN Server state LISTEN clientSocket = socket(AF_INET, SOCK_STREAM) serverSocket =
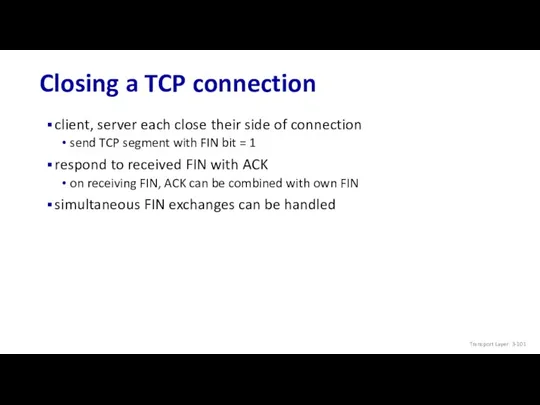
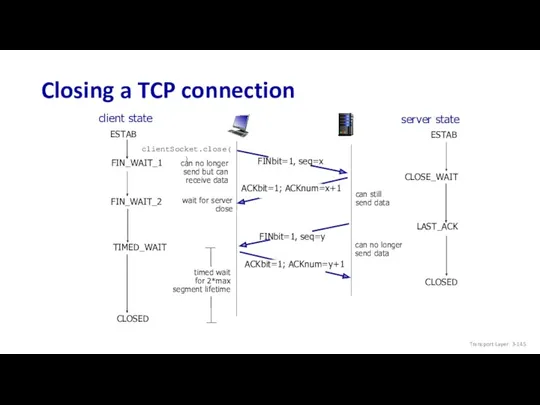
- 101. Closing a TCP connection client, server each close their side of connection send TCP segment with
- 102. Topic 3: roadmap Transport-layer services Multiplexing and demultiplexing Connectionless transport: UDP Principles of reliable data transfer
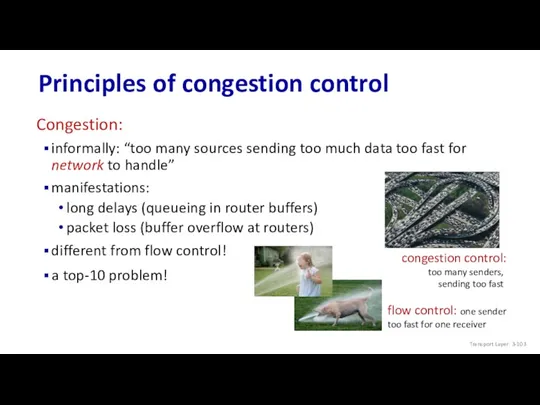
- 103. Congestion: informally: “too many sources sending too much data too fast for network to handle” manifestations:
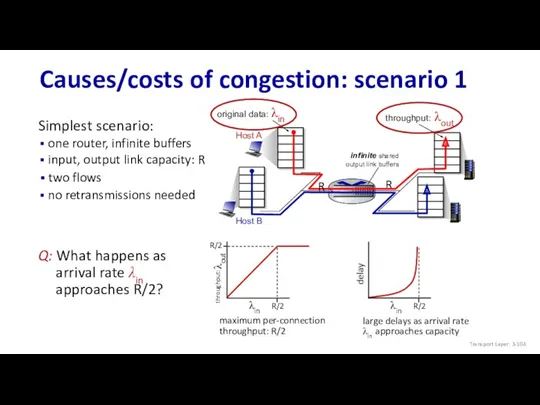
- 104. Causes/costs of congestion: scenario 1 Simplest scenario: maximum per-connection throughput: R/2 Host A Host B large
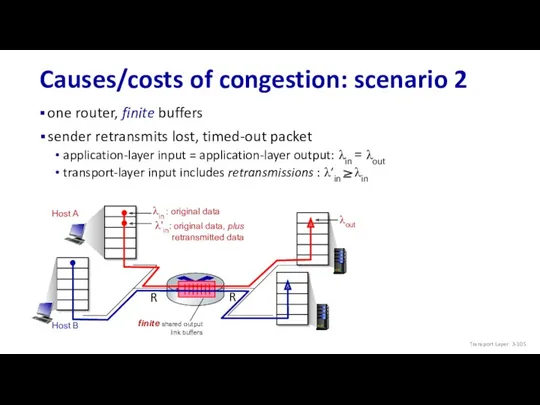
- 105. Causes/costs of congestion: scenario 2 one router, finite buffers Host A Host B Transport Layer: 3-
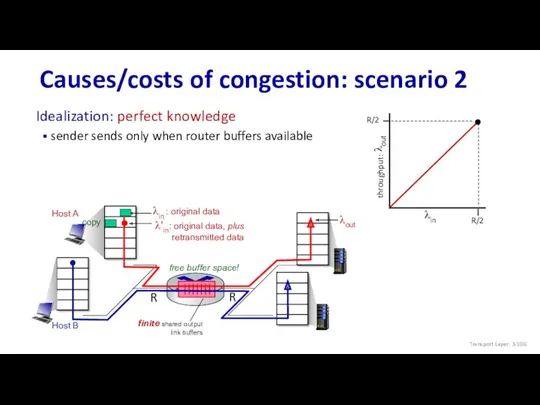
- 106. Host A Host B Causes/costs of congestion: scenario 2 copy free buffer space! Idealization: perfect knowledge
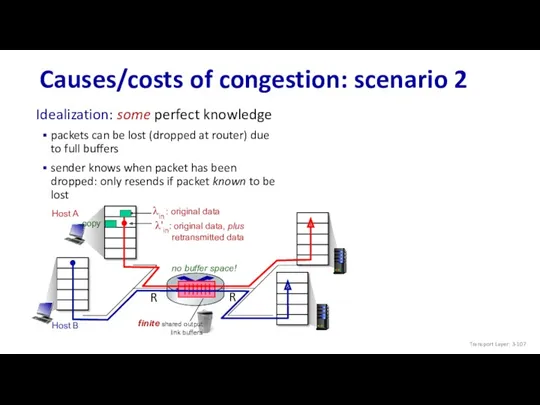
- 107. Host A Host B Causes/costs of congestion: scenario 2 copy no buffer space! Idealization: some perfect
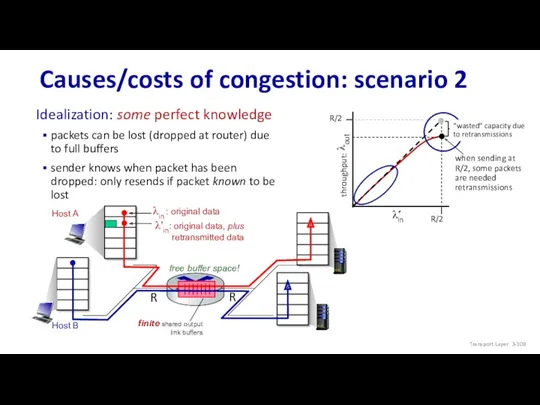
- 108. Host A Host B Causes/costs of congestion: scenario 2 free buffer space! Idealization: some perfect knowledge
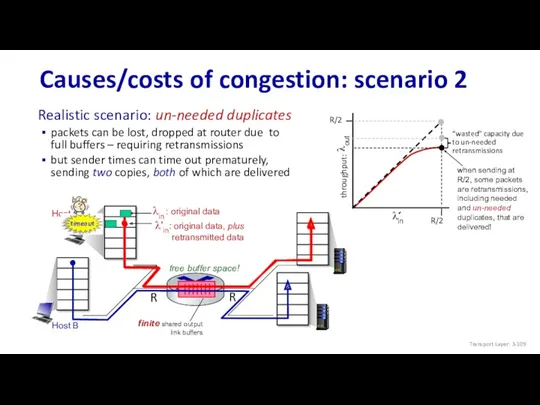
- 109. Host A Host B Causes/costs of congestion: scenario 2 copy Realistic scenario: un-needed duplicates packets can
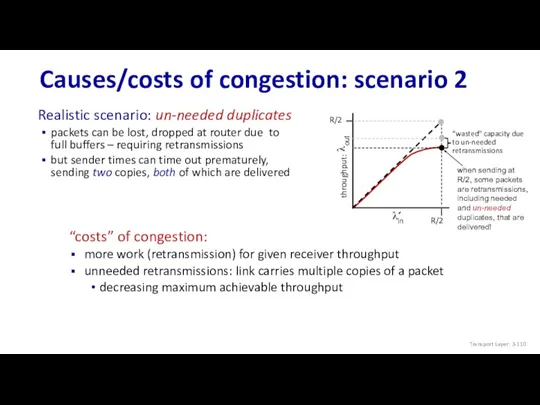
- 110. Causes/costs of congestion: scenario 2 “costs” of congestion: more work (retransmission) for given receiver throughput unneeded
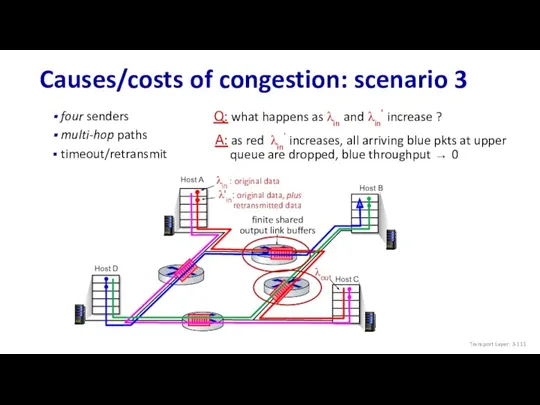
- 111. Causes/costs of congestion: scenario 3 four senders multi-hop paths timeout/retransmit Q: what happens as λin and
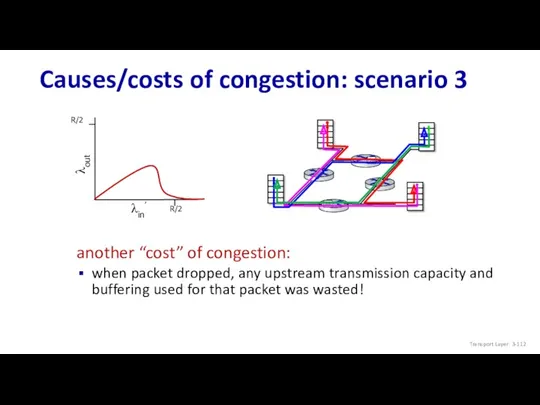
- 112. Causes/costs of congestion: scenario 3 another “cost” of congestion: when packet dropped, any upstream transmission capacity
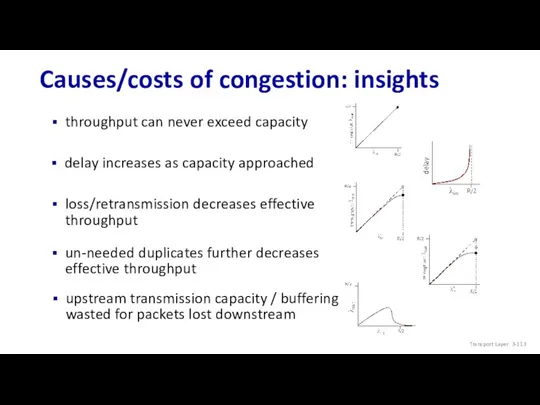
- 113. Causes/costs of congestion: insights Transport Layer: 3-
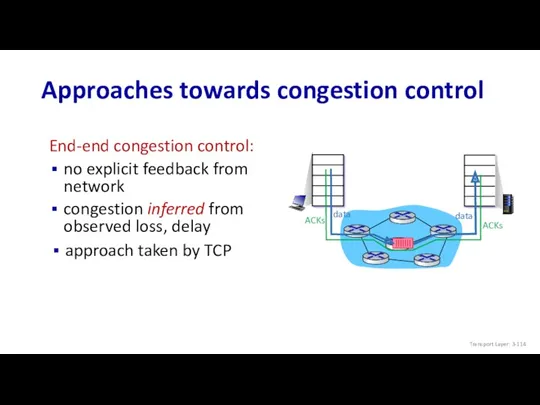
- 114. End-end congestion control: no explicit feedback from network congestion inferred from observed loss, delay Approaches towards
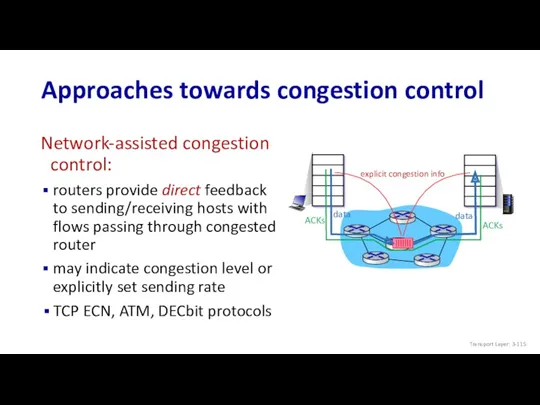
- 115. TCP ECN, ATM, DECbit protocols Approaches towards congestion control explicit congestion info Network-assisted congestion control: routers
- 116. Topic 3: roadmap Transport-layer services Multiplexing and demultiplexing Connectionless transport: UDP Principles of reliable data transfer
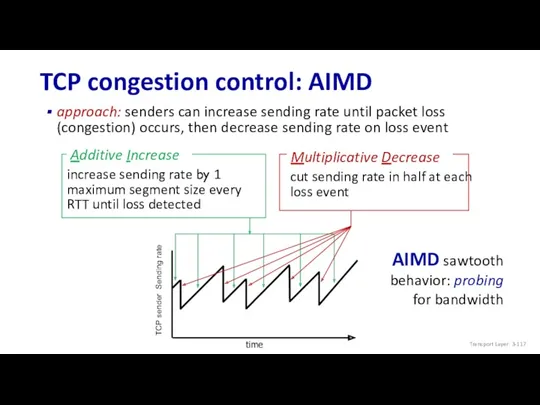
- 117. TCP congestion control: AIMD approach: senders can increase sending rate until packet loss (congestion) occurs, then
- 118. TCP AIMD: more Multiplicative decrease detail: sending rate is Cut in half on loss detected by
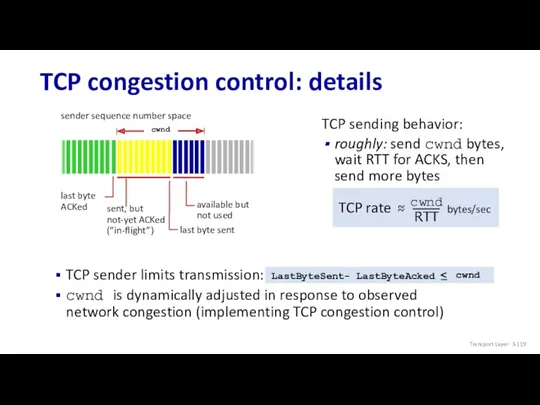
- 119. TCP congestion control: details Transport Layer: 3-
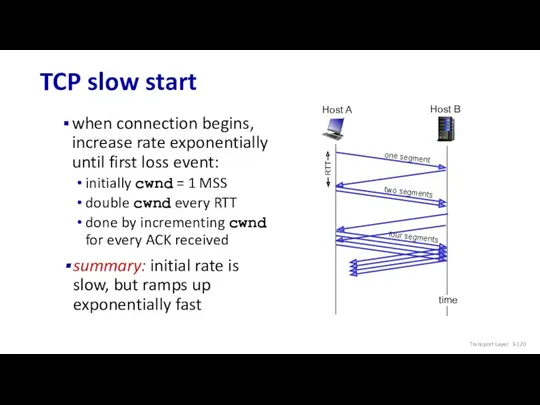
- 120. TCP slow start when connection begins, increase rate exponentially until first loss event: initially cwnd =
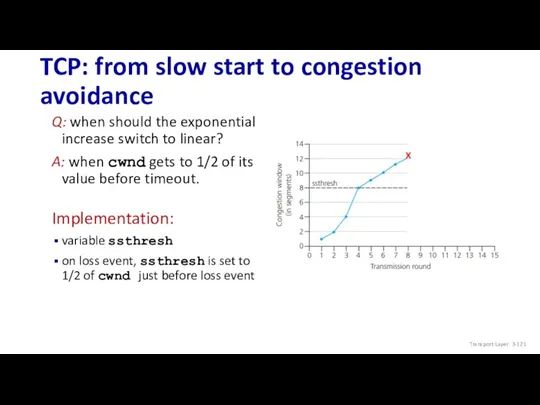
- 121. TCP: from slow start to congestion avoidance Q: when should the exponential increase switch to linear?
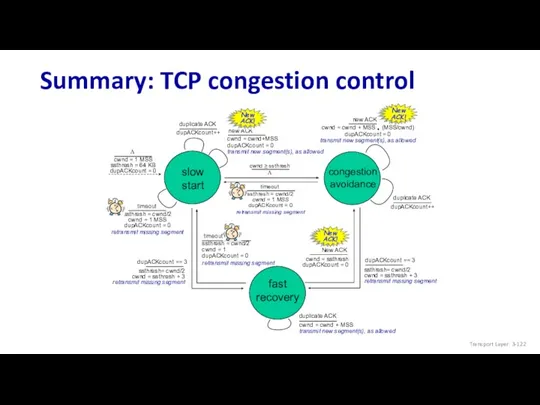
- 122. Summary: TCP congestion control Transport Layer: 3-
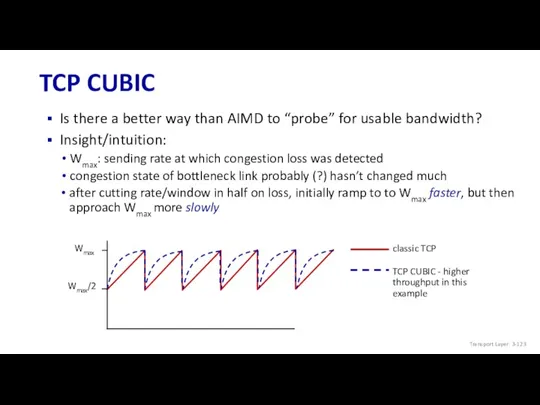
- 123. TCP CUBIC Is there a better way than AIMD to “probe” for usable bandwidth? Insight/intuition: Wmax:
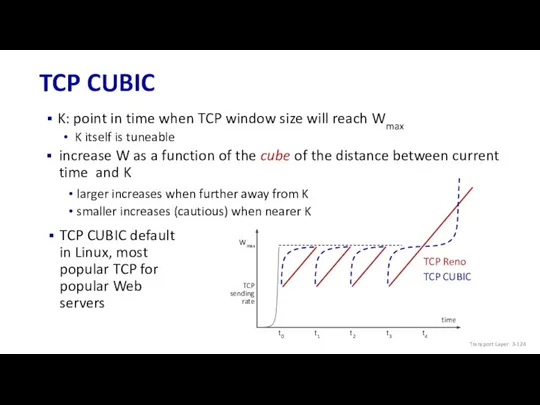
- 124. TCP CUBIC K: point in time when TCP window size will reach Wmax K itself is
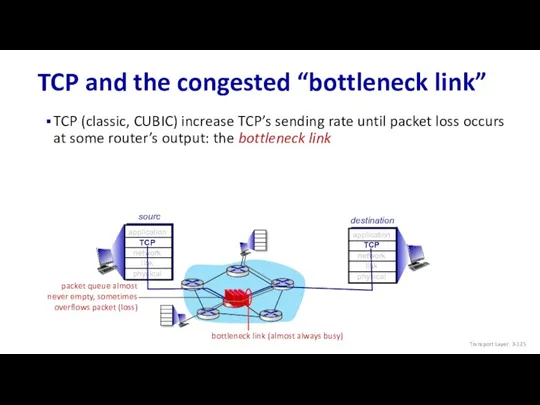
- 125. TCP and the congested “bottleneck link” TCP (classic, CUBIC) increase TCP’s sending rate until packet loss
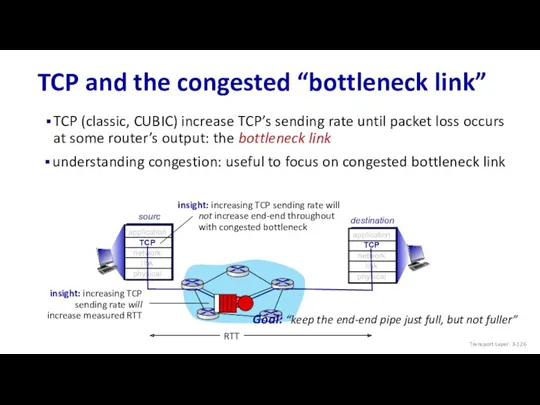
- 126. TCP and the congested “bottleneck link” TCP (classic, CUBIC) increase TCP’s sending rate until packet loss
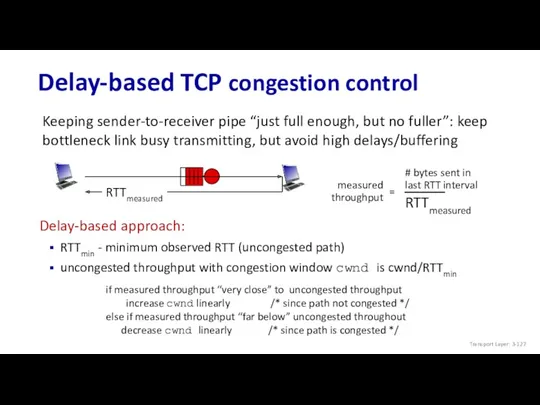
- 127. Delay-based TCP congestion control Keeping sender-to-receiver pipe “just full enough, but no fuller”: keep bottleneck link
- 128. Delay-based TCP congestion control congestion control without inducing/forcing loss maximizing throughout (“keeping the just pipe full…
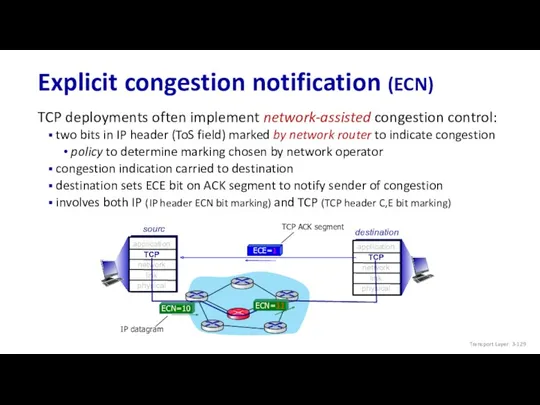
- 129. Explicit congestion notification (ECN) TCP deployments often implement network-assisted congestion control: two bits in IP header
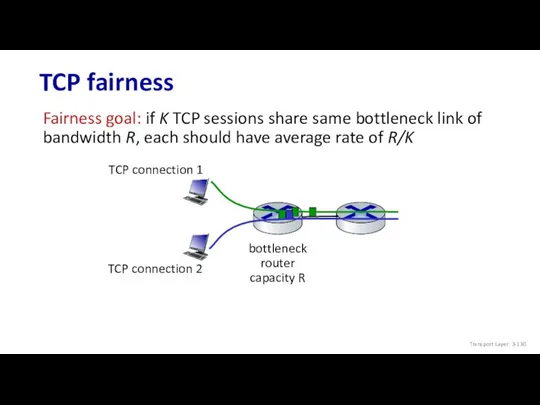
- 130. TCP fairness Fairness goal: if K TCP sessions share same bottleneck link of bandwidth R, each
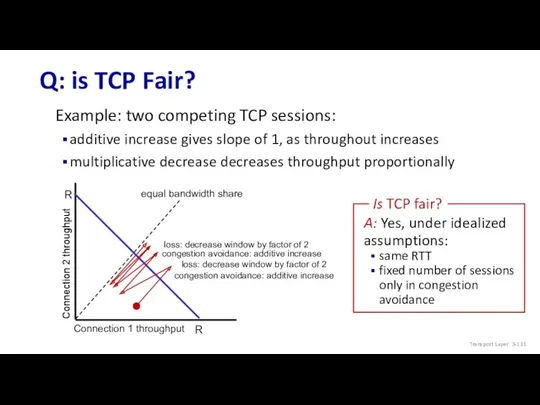
- 131. Q: is TCP Fair? Example: two competing TCP sessions: additive increase gives slope of 1, as
- 132. Fairness: must all network apps be “fair”? Fairness and UDP multimedia apps often do not use
- 133. Transport layer: roadmap Transport-layer services Multiplexing and demultiplexing Connectionless transport: UDP Principles of reliable data transfer
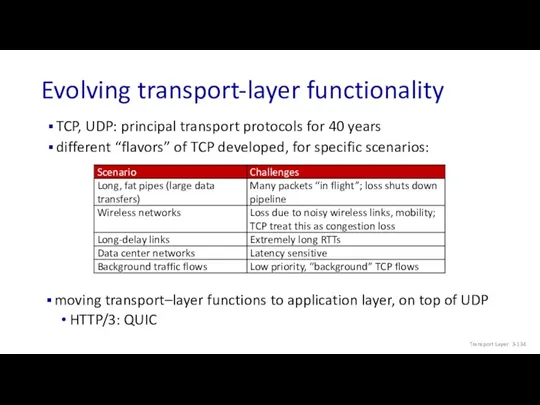
- 134. TCP, UDP: principal transport protocols for 40 years different “flavors” of TCP developed, for specific scenarios:
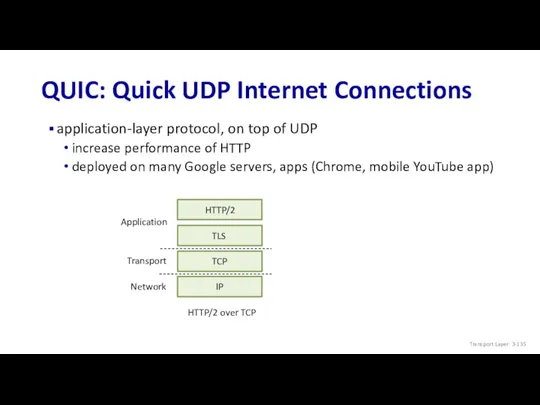
- 135. application-layer protocol, on top of UDP increase performance of HTTP deployed on many Google servers, apps
- 136. QUIC: Quick UDP Internet Connections adopts approaches we’ve studied in this chapter for connection establishment, error
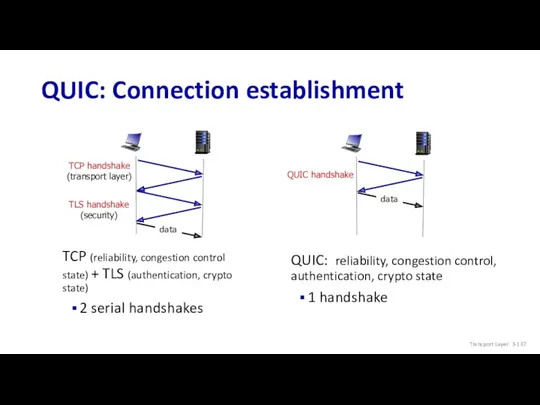
- 137. QUIC: Connection establishment TCP handshake (transport layer) TLS handshake (security) TCP (reliability, congestion control state) +
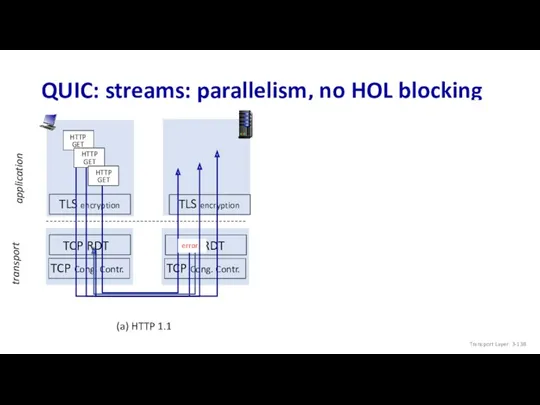
- 138. QUIC: streams: parallelism, no HOL blocking (a) HTTP 1.1 TLS encryption transport application (b) HTTP/2 with
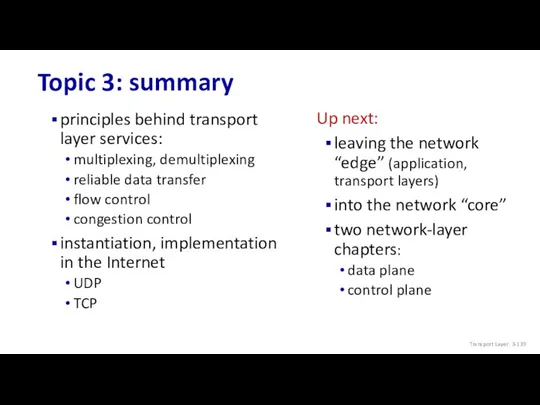
- 139. Topic 3: summary Transport Layer: 3- principles behind transport layer services: multiplexing, demultiplexing reliable data transfer
- 140. Additional Topic 3 slides Transport Layer: 3-
- 141. Go-Back-N: sender extended FSM Transport Layer: 3- base=1 nextseqnum=1 Λ
- 142. Go-Back-N: receiver extended FSM Transport Layer: 3- Wait rdt_rcv(rcvpkt) && notcorrupt(rcvpkt) && hasseqnum(rcvpkt,expectedseqnum) extract(rcvpkt,data) deliver_data(data) sndpkt
- 143. TCP sender (simplified) Transport Layer: 3- wait for event NextSeqNum = InitialSeqNum SendBase = InitialSeqNum Λ
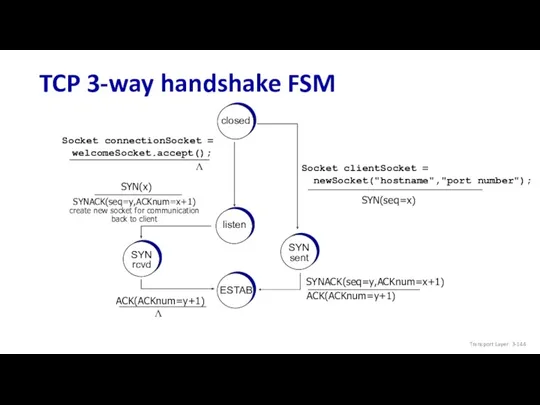
- 144. TCP 3-way handshake FSM Transport Layer: 3- closed Λ listen SYN rcvd SYN sent ESTAB Socket
- 145. Transport Layer: 3- Closing a TCP connection client state server state ESTAB ESTAB
- 146. TCP throughput avg. TCP thruput as function of window size, RTT? ignore slow start, assume there
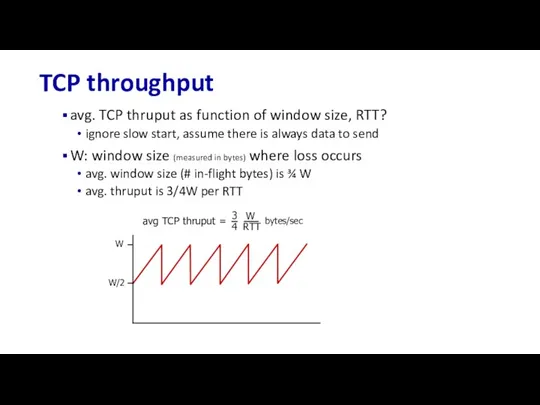
- 148. Скачать презентацию


![UDP: User Datagram Protocol [RFC 768] Transport Layer: 3-](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/201592/slide-24.jpg)









![TCP Receiver: ACK generation [RFC 5681] Event at receiver arrival](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/201592/slide-83.jpg)





 Компьютерные технологии интеллектуальной поддержки управленческих решений
Компьютерные технологии интеллектуальной поддержки управленческих решений Задача линейного программирования и способы решения
Задача линейного программирования и способы решения Презентация Необычное кулинарное путешествие
Презентация Необычное кулинарное путешествие Середовище описання і виконання алгоритмів
Середовище описання і виконання алгоритмів Графики и диаграммы
Графики и диаграммы Цифровой офис
Цифровой офис Технологии проектирования компьютерных систем. Методы проектирования цифровых устройств. (Лекция 1)
Технологии проектирования компьютерных систем. Методы проектирования цифровых устройств. (Лекция 1) Основы html/css
Основы html/css Форматирование текста. Обработка текстовой информации. 7 класс
Форматирование текста. Обработка текстовой информации. 7 класс Электронные сервисы Фонда социального страхования РФ (ФСС) - круглый стол
Электронные сервисы Фонда социального страхования РФ (ФСС) - круглый стол Презентация к уроку информатики в 8 классе на тему Измерение информации
Презентация к уроку информатики в 8 классе на тему Измерение информации Облачный сервис 1С:Предприятие 8 через Интернет (1сfresh.com)
Облачный сервис 1С:Предприятие 8 через Интернет (1сfresh.com) Перевод чисел в позиционных системах счисления
Перевод чисел в позиционных системах счисления Виртуальная и дополненная реальность и их отличия. Иммерсивные технологии и здоровье человека
Виртуальная и дополненная реальность и их отличия. Иммерсивные технологии и здоровье человека Возможная архитектура (состав инструментов) электронного правительства
Возможная архитектура (состав инструментов) электронного правительства Сектор удаленного обслуживания центральной городской библиотеки
Сектор удаленного обслуживания центральной городской библиотеки Глобальные сети. Основные понятия и определения
Глобальные сети. Основные понятия и определения Моделирование БП для КИС. Определение КИС.1. Тема 2
Моделирование БП для КИС. Определение КИС.1. Тема 2 Информация и её свойства. Информация и информационные процессы. Информатика. 7 класс
Информация и её свойства. Информация и информационные процессы. Информатика. 7 класс Історія засобів опрацювання інформаційних об’єктів. Технічні характеристики складових комп’ютера. Практична робота №2
Історія засобів опрацювання інформаційних об’єктів. Технічні характеристики складових комп’ютера. Практична робота №2 Системный анализ безопасности
Системный анализ безопасности Организация ввода и вывода данных. Начала программирования
Организация ввода и вывода данных. Начала программирования Обработка массива
Обработка массива Презентация на урок Фрагмент текста и операции с ним
Презентация на урок Фрагмент текста и операции с ним Алгоритми та їх виконавці
Алгоритми та їх виконавці Стохастические модели
Стохастические модели Язык разметки гипертекста
Язык разметки гипертекста Kofax Transformation Modules 5. Introduction to Class Training
Kofax Transformation Modules 5. Introduction to Class Training