Содержание
- 2. COURSE STRUCTURE: Determining cybersecurity fundamentals; Overview of different types of attacks, prevention and mitigation of threats;
- 3. COURSE STRUCTURE: Understanding types of Firewalls, proxy servers, IDS/IPS, honeypots, SIEMs and other logging tools; Building
- 4. Practice week 1
- 5. Pre security skills Network fundamentals How Internet works Linux fundamentals Windows fundamentals Basic math for cryptography
- 6. Cybersecurity Offensive security (Red team) Defensive security (Blue team) Offensive/Defensive security (Purple team) AppSec Engineers DevSecOps
- 7. Cybersecurity The art of protecting networks, devices, and data from unauthorized access or criminal use and
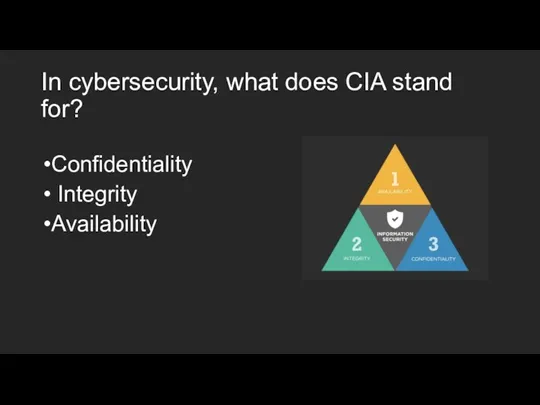
- 8. In cybersecurity, what does CIA stand for? Confidentiality Integrity Availability
- 9. CIA Triad Confidentiality: Private data stays private. Encryption, access control. Integrity: Data is free from unauthorized
- 10. Alice is buying books from an online retail site, and she finds that she is able
- 11. Alice is working on her university applications online, when the admissions website crashes. She is unable
- 12. Cyber attacks Malware attacks Phishing attacks Brute Force password attacks Man in the middle attacks IDOR
- 13. Malware attacks Malware, or malicious software, is any program or file that harms a computer or
- 14. Malware attacks Computer Viruses Computer Worms Trojan Horse Rootkits Ransomware Keyloggers Adware Spyware Bots and botnets
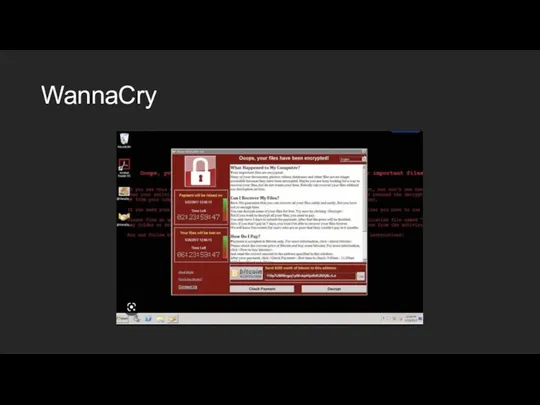
- 15. WannaCry
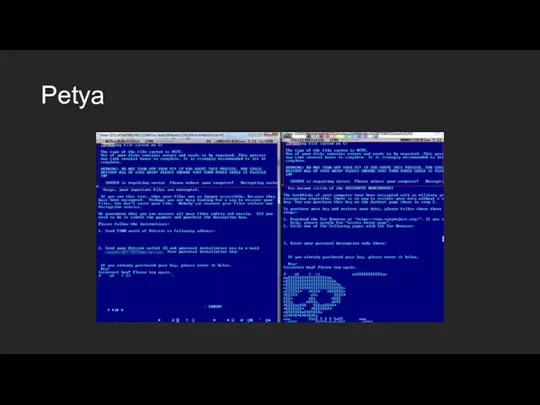
- 16. Petya
- 17. Malware analysis. How does Petya work? Malware analysis is the process of understanding the behavior and
- 18. Malware analysis. How does Petya work? Anti-virus databases hold the data needed for a signature-based scanner
- 19. Malware analysis. How does Petya work? Anti-virus databases also include malicious IP addresses, files, hashes and
- 20. Phishing attacks Phishing is when attackers send malicious emails designed to trick people into falling for
- 21. How Phishing Works Whether a phishing campaign is targeted or sent to as many victims as
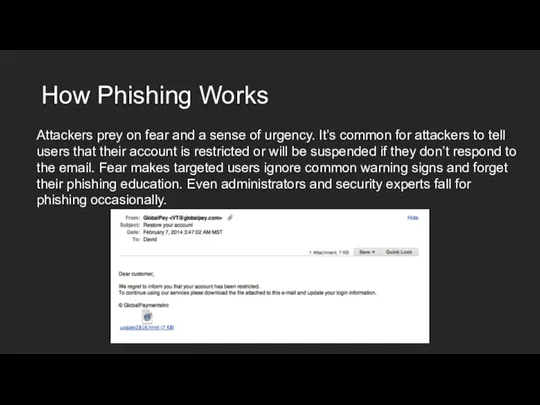
- 22. How Phishing Works Attackers prey on fear and a sense of urgency. It’s common for attackers
- 23. Types of modern phishing attacks Email phishing: the general term given to any malicious email message
- 24. Types of modern phishing attacks Malware: users tricked into clicking a link or opening an attachment
- 25. Types of modern phishing attacks Vishing: attackers use voice-changing software to leave a message telling targeted
- 26. Prevention of phishing Avoid clicking links: instead of clicking a link and authenticating into a web
- 27. Prevention of phishing Change passwords regularly: users should be forced to change their passwords every 30-45
- 28. Prevention of phishing Install firewalls: firewalls control inbound and outbound traffic. Malware installed from phishing silently
- 29. Brute Force password attacks A common threat web developers face is a password-guessing attack known as
- 30. Popular tools for brute force attacks Aircrack-ng John the Ripper Rainbow crack L0phtCrack Ophcrack Hashcat DaveGrohl
- 31. OWASP TOP 10 https://owasp.org/www-project-top-ten/ Globally recognized by developers as the first step towards more secure coding.
- 32. Security for everyone Knowing how to properly design a secure infrastructure is just as important as
- 33. Basic security principles CIA triad: Confidentiality, Integrity & Availability; Trust but verify: applies to all aspects
- 34. Secure architecture design Designing and configuring infrastructure with security in mind: Starting with a proper design;
- 35. Threat modeling Used to help determine possible impacts to infrastructure; Process to identify assets, threats, and
- 36. Reminder: Without any comprehensive design: Maintenance and documentation suffer; Vulnerabilities can go unpatched; Attackers can remain
- 37. Zero trust Attacks can come from anywhere on the network; Insiders; But near impossible to implement
- 38. Secure Users. Authentication and Authorization Authentication Begins with identification “ I am ____”; Verifying that identity
- 39. Secure Users. Separation of Duties. Organizations place some level of trust in their employees. Super admin,
- 40. Secure infrastructure What makes up our infrastructure? Servers (AD, file, web, database, application, etc.); Workstations (Mac,
- 41. Encryption Part of a defense in depth strategy; Used with access controls, permissions; Best practices for
- 42. Home assignment 1 Lab 1. --- DAY 1, DAY 2 and DAY 3.
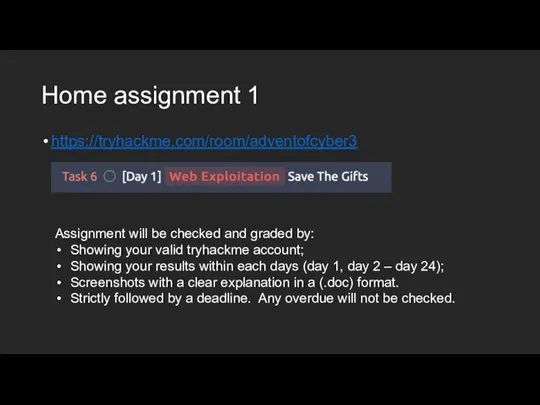
- 43. Home assignment 1 https://tryhackme.com/room/adventofcyber3 Assignment will be checked and graded by: Showing your valid tryhackme account;
- 45. Скачать презентацию



















 Расчетные методики ПП ЭкоСфера-предприятие. Расчет выбросов от автотранспорта (внутренний проезд)
Расчетные методики ПП ЭкоСфера-предприятие. Расчет выбросов от автотранспорта (внутренний проезд) Основы построения компьютерных сетей. Сетевые информационные технологии
Основы построения компьютерных сетей. Сетевые информационные технологии Подготовка к выгрузке данных в ФСПЭО из АИС Сетевой город. Образование версия 5.0 и АИС Е-Услуги
Подготовка к выгрузке данных в ФСПЭО из АИС Сетевой город. Образование версия 5.0 и АИС Е-Услуги Мемы
Мемы Web-программирование
Web-программирование Смарт-технологиялар
Смарт-технологиялар 10 Useful, Weird or Entertaining Websites to Waste Time On
10 Useful, Weird or Entertaining Websites to Waste Time On Пример библиографической записи для копирования в список найденных источников
Пример библиографической записи для копирования в список найденных источников Среда разработки
Среда разработки Павел Дуров. Создатель социальной сети вконтакте
Павел Дуров. Создатель социальной сети вконтакте Тестирование ПО. Методики тестирования. Лекция 5
Тестирование ПО. Методики тестирования. Лекция 5 Виды компьютерной графики
Виды компьютерной графики Создание робота-помощника на платформе Arduino
Создание робота-помощника на платформе Arduino Содержательный подход к измерению количества информации
Содержательный подход к измерению количества информации Линейный вычислительный процесс
Линейный вычислительный процесс Создание тестов с помощью конструктора RomeXoft MultiTester System 3.3
Создание тестов с помощью конструктора RomeXoft MultiTester System 3.3 Об универсальном анализе кода или Зачем нам ещё один анализатор, как его можно сделать и куда применять
Об универсальном анализе кода или Зачем нам ещё один анализатор, как его можно сделать и куда применять Обработка информации
Обработка информации Численные методы решения задач
Численные методы решения задач Штучний інтелект
Штучний інтелект Microsoft SQL Server
Microsoft SQL Server Операционные системы
Операционные системы Знакомство с рабочим местом webquik
Знакомство с рабочим местом webquik Методы шифрования
Методы шифрования Способы перевода из одной системы счисления в другую
Способы перевода из одной системы счисления в другую Массивы
Массивы Выработка и реализация сетевой политики, настройка телекоммуникационного оборудования ЛВС офисного центра
Выработка и реализация сетевой политики, настройка телекоммуникационного оборудования ЛВС офисного центра Операції над об’єктами та групами об’єктів. Урок 4
Операції над об’єктами та групами об’єктів. Урок 4