Содержание
- 2. Chapter 10 - Sections & Objectives 10.0 Introduction 10.1 Application Layer Protocols Explain how the functions
- 3. 10.1 Application Layer Protocols
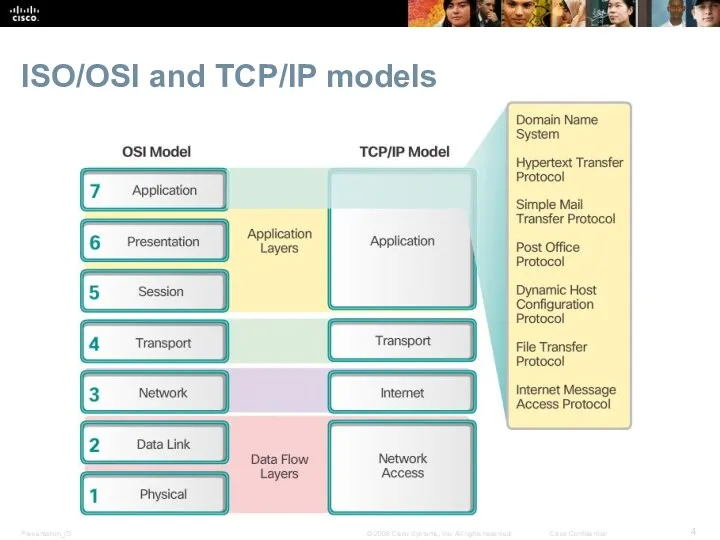
- 4. ISO/OSI and TCP/IP models
- 5. Application Layer Protocols Application, Presentation, Session Application Layer Closest to the end user. Application layer protocols
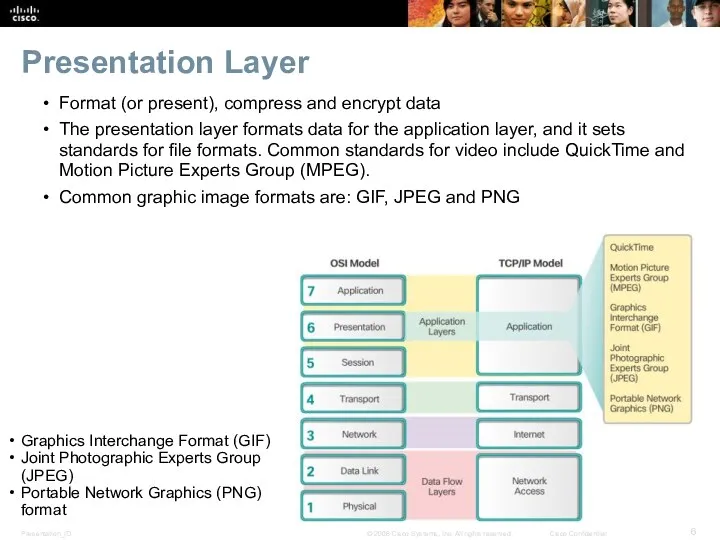
- 6. Presentation Layer Format (or present), compress and encrypt data The presentation layer formats data for the
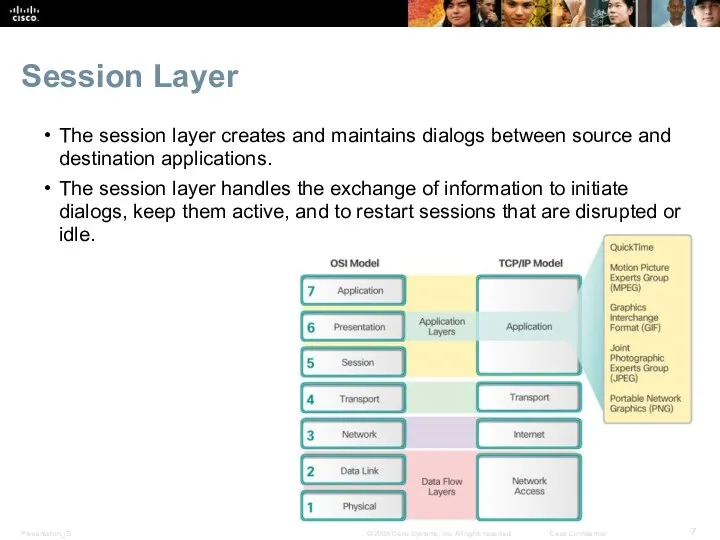
- 7. Session Layer The session layer creates and maintains dialogs between source and destination applications. The session
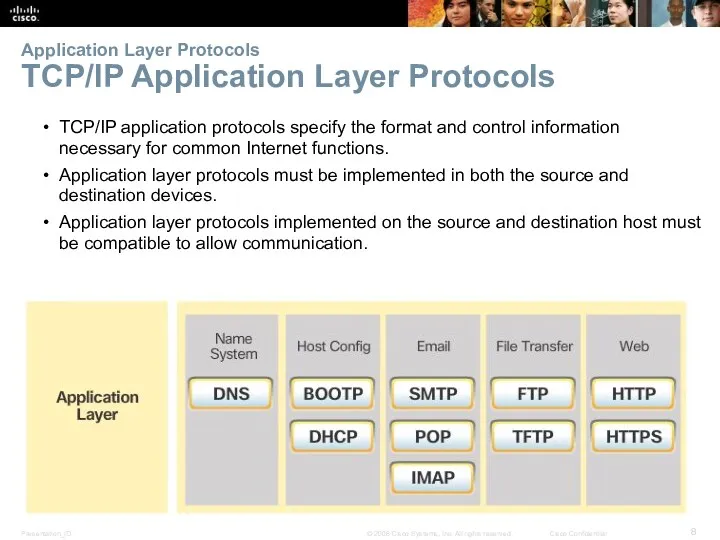
- 8. Application Layer Protocols TCP/IP Application Layer Protocols TCP/IP application protocols specify the format and control information
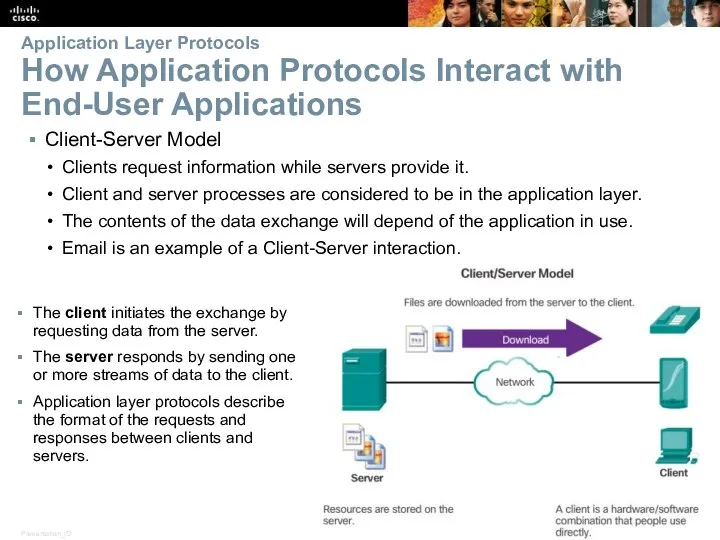
- 9. Application Layer Protocols How Application Protocols Interact with End-User Applications Client-Server Model Clients request information while
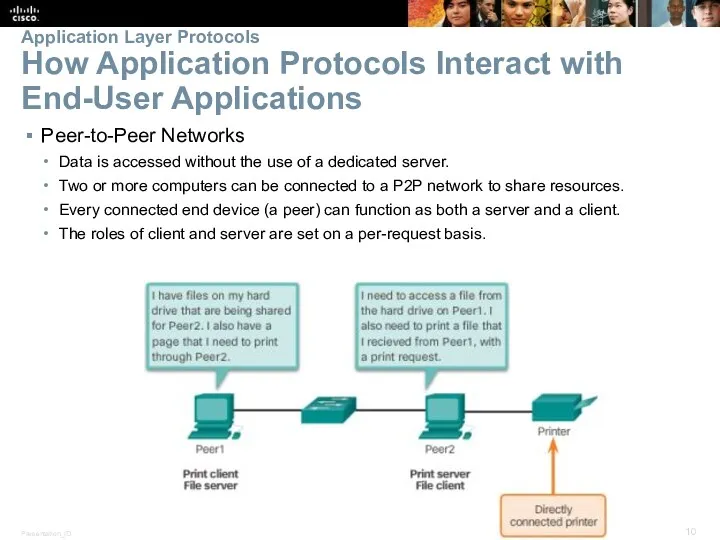
- 10. Peer-to-Peer Networks Data is accessed without the use of a dedicated server. Two or more computers
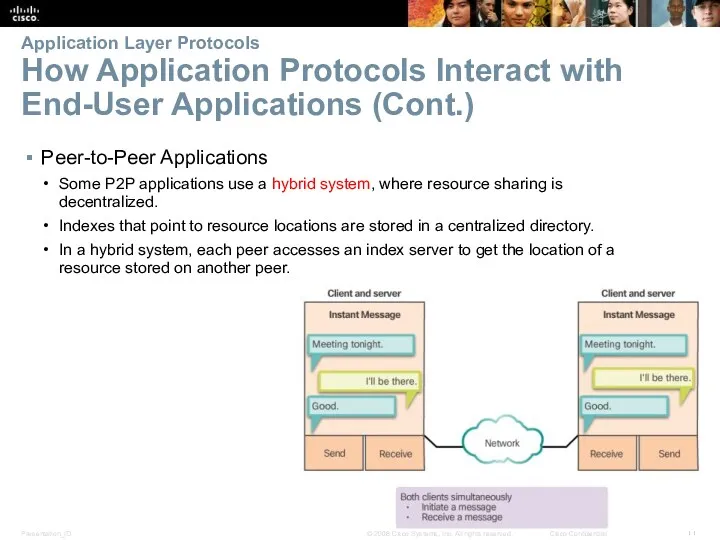
- 11. Application Layer Protocols How Application Protocols Interact with End-User Applications (Cont.) Peer-to-Peer Applications Some P2P applications
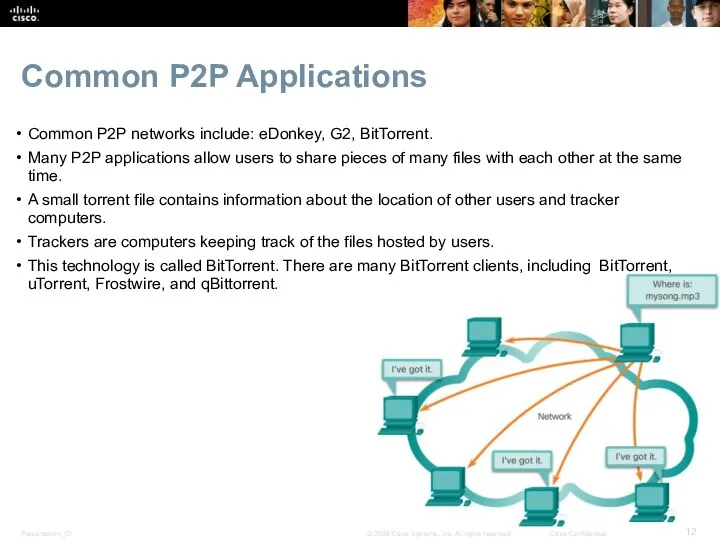
- 12. Common P2P Applications Common P2P networks include: eDonkey, G2, BitTorrent. Many P2P applications allow users to
- 13. 10.2 Well-Known Application Layer Protocols and Services
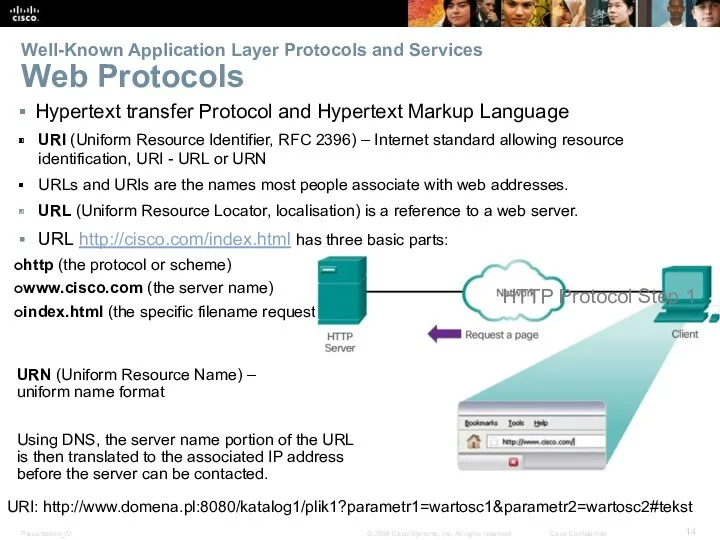
- 14. Well-Known Application Layer Protocols and Services Web Protocols Hypertext transfer Protocol and Hypertext Markup Language URI
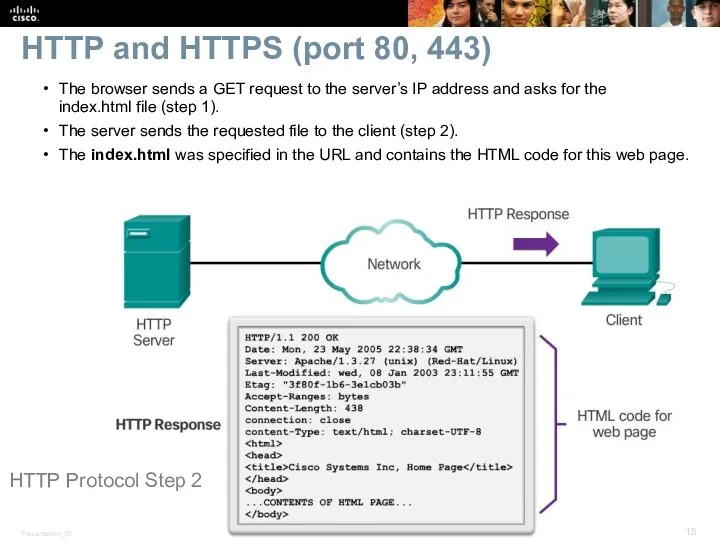
- 15. HTTP and HTTPS (port 80, 443) The browser sends a GET request to the server’s IP
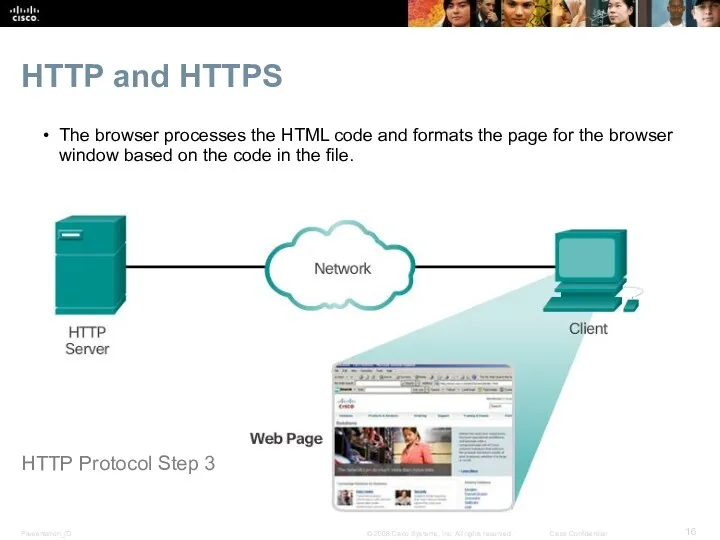
- 16. HTTP and HTTPS The browser processes the HTML code and formats the page for the browser
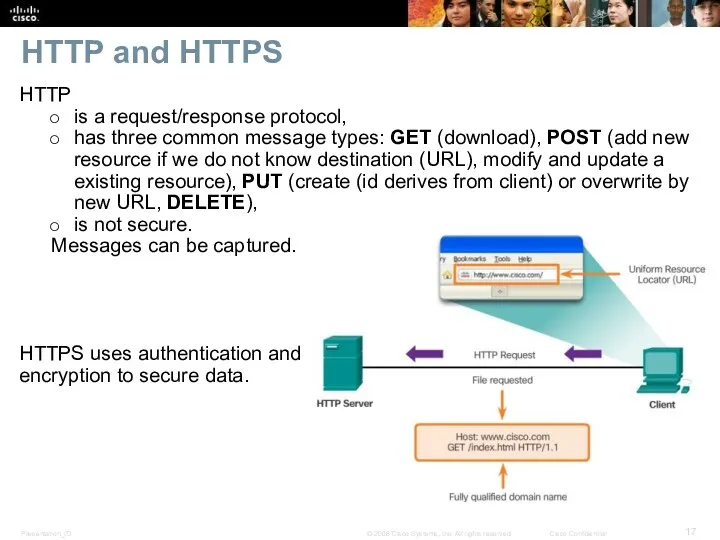
- 17. HTTP and HTTPS HTTP is a request/response protocol, has three common message types: GET (download), POST
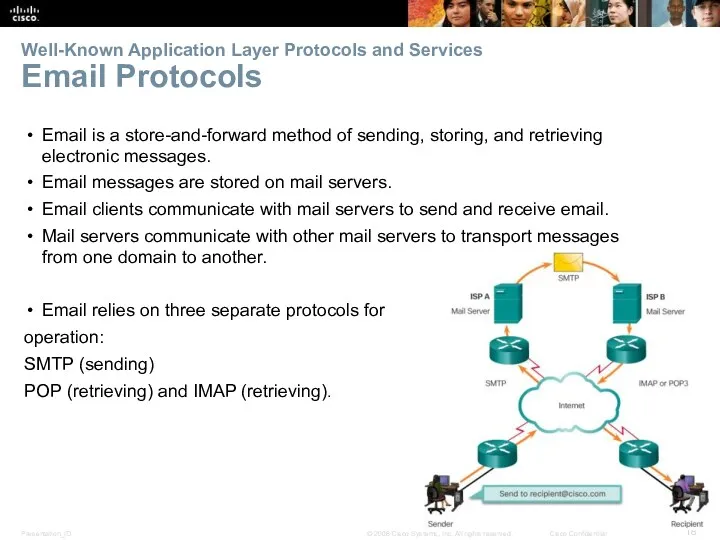
- 18. Well-Known Application Layer Protocols and Services Email Protocols Email is a store-and-forward method of sending, storing,
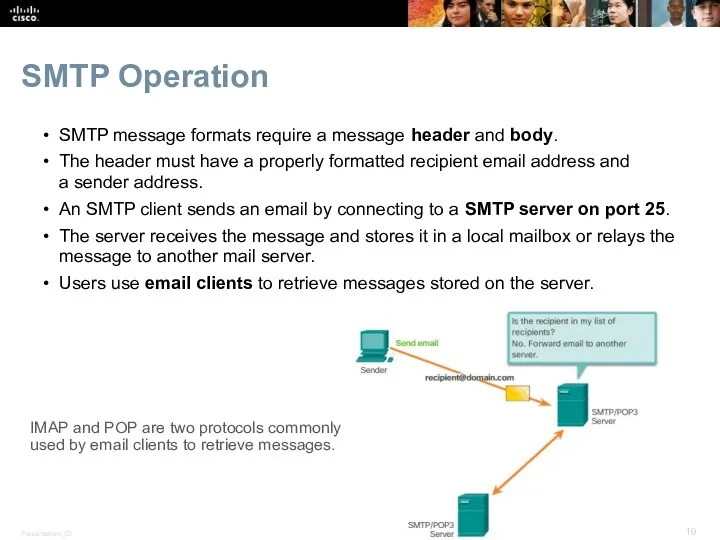
- 19. SMTP Operation SMTP message formats require a message header and body. The header must have a
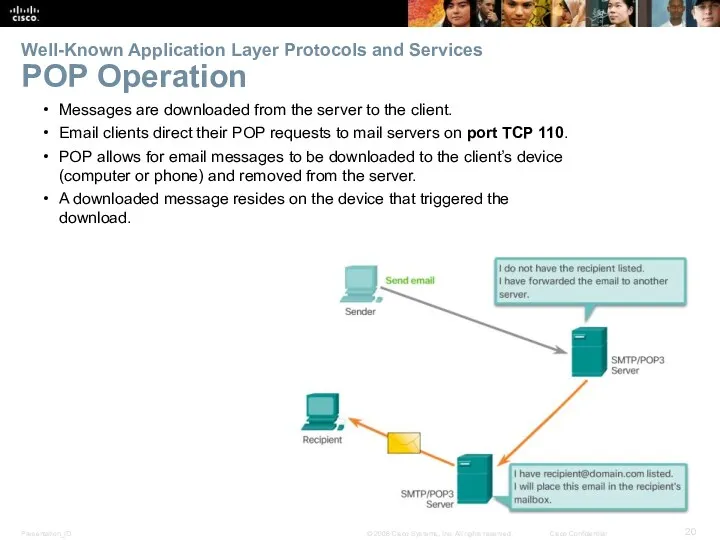
- 20. Well-Known Application Layer Protocols and Services POP Operation Messages are downloaded from the server to the
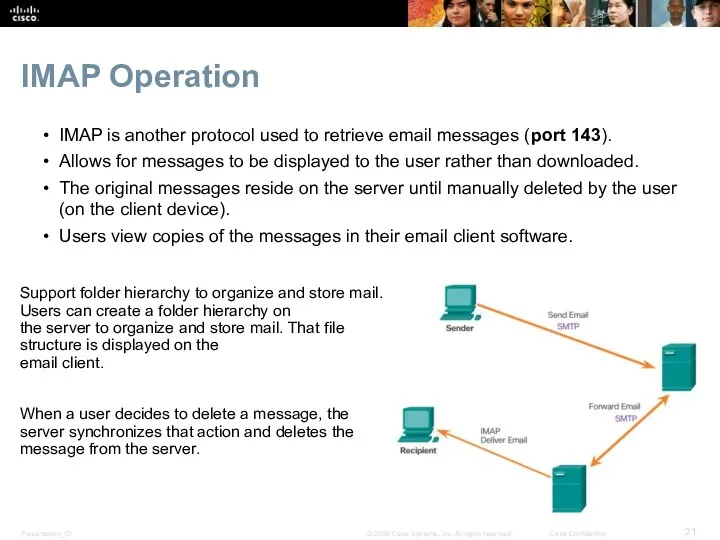
- 21. IMAP Operation IMAP is another protocol used to retrieve email messages (port 143). Allows for messages
- 22. Email port numbers in the practice
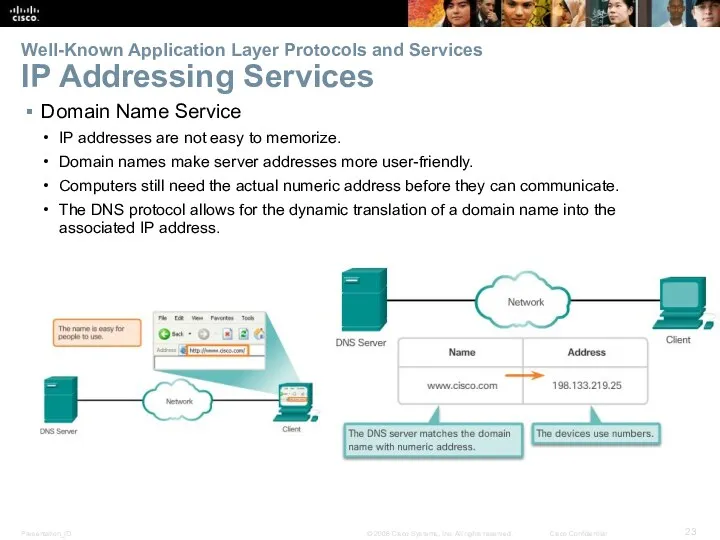
- 23. Well-Known Application Layer Protocols and Services IP Addressing Services Domain Name Service IP addresses are not
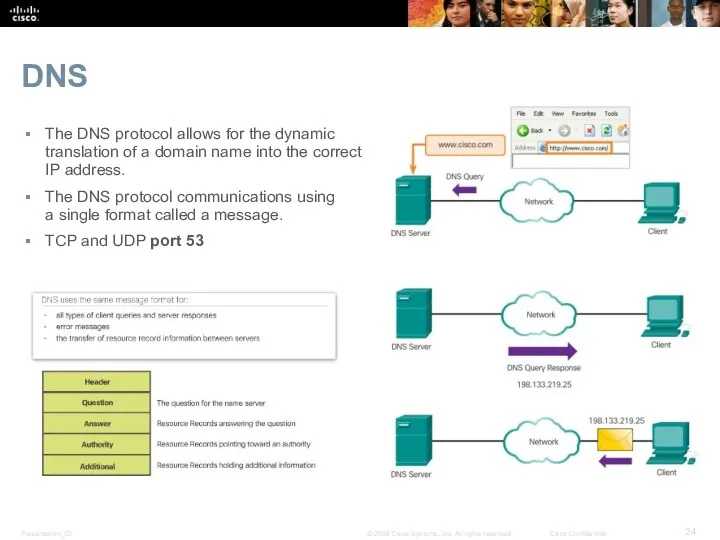
- 24. DNS The DNS protocol allows for the dynamic translation of a domain name into the correct
- 25. DNS Message Format DNS supports different types of records. Some of these record types are: A
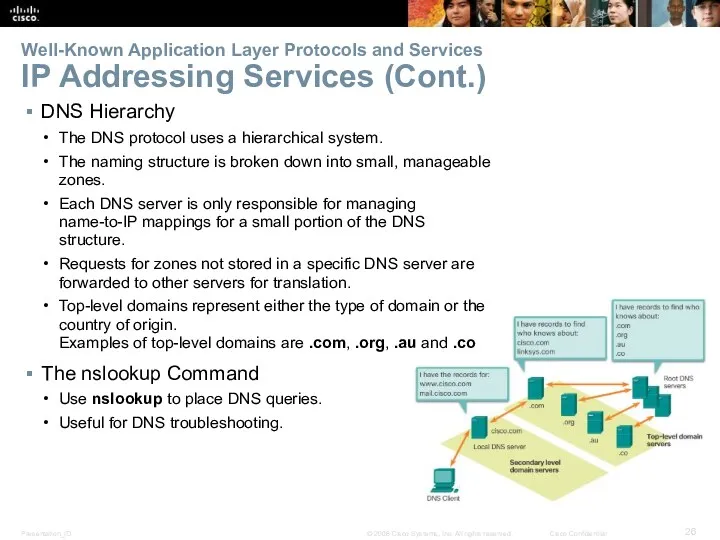
- 26. Well-Known Application Layer Protocols and Services IP Addressing Services (Cont.) DNS Hierarchy The DNS protocol uses
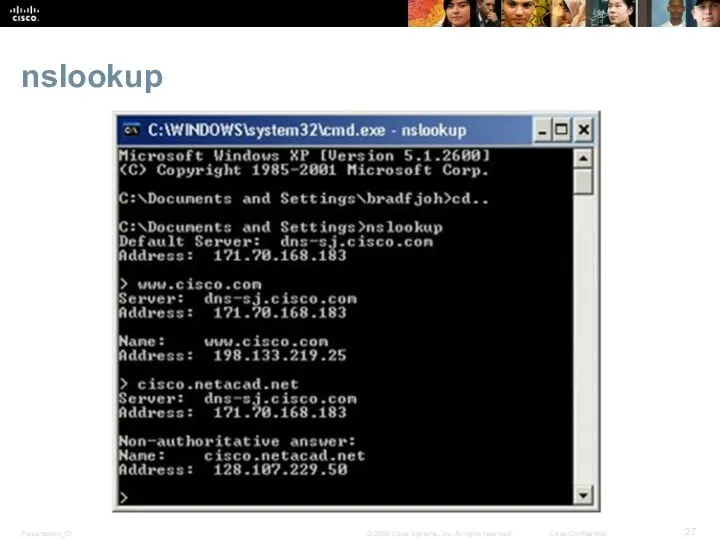
- 27. nslookup
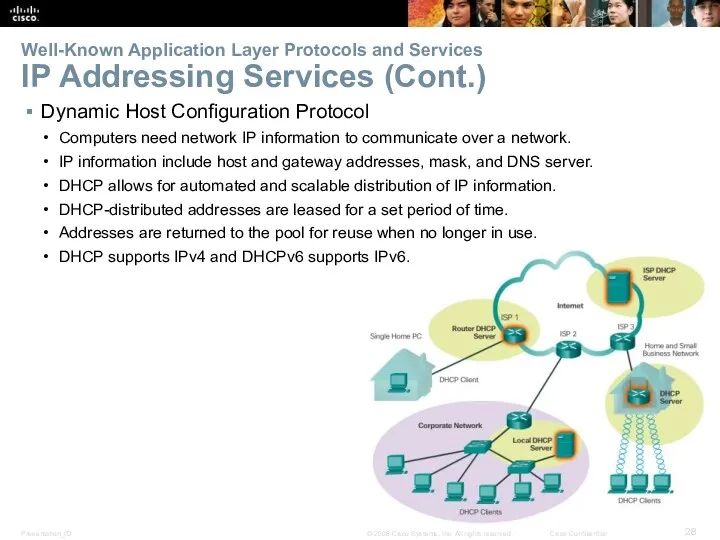
- 28. Well-Known Application Layer Protocols and Services IP Addressing Services (Cont.) Dynamic Host Configuration Protocol Computers need
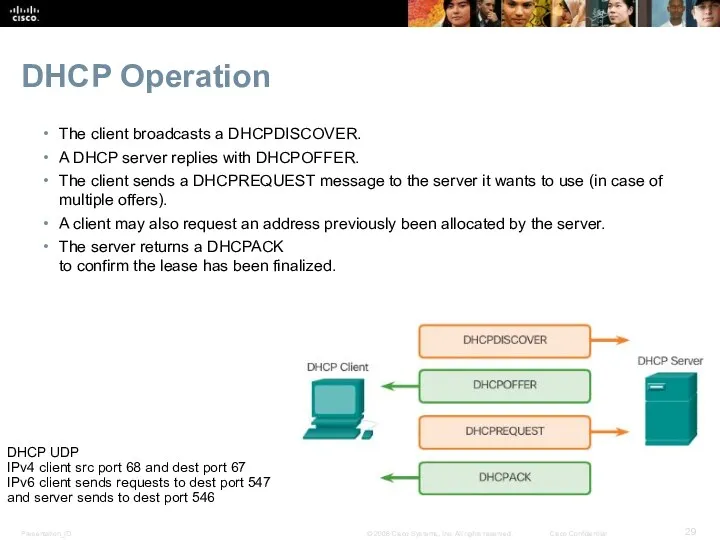
- 29. DHCP Operation The client broadcasts a DHCPDISCOVER. A DHCP server replies with DHCPOFFER. The client sends
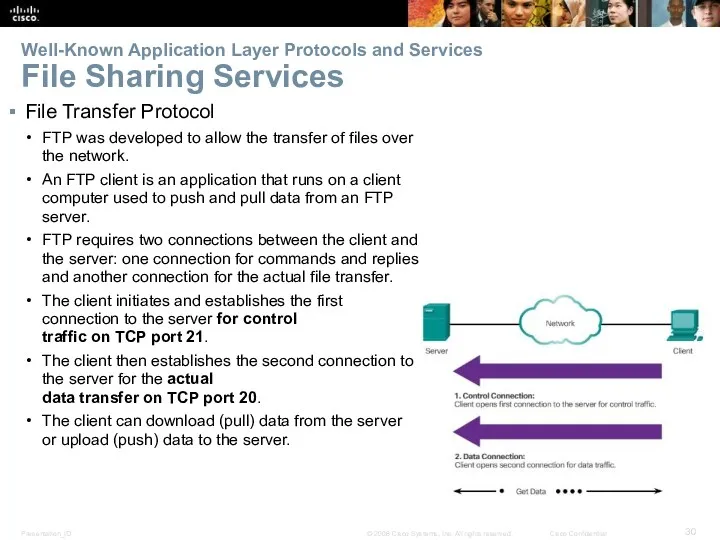
- 30. Well-Known Application Layer Protocols and Services File Sharing Services File Transfer Protocol FTP was developed to
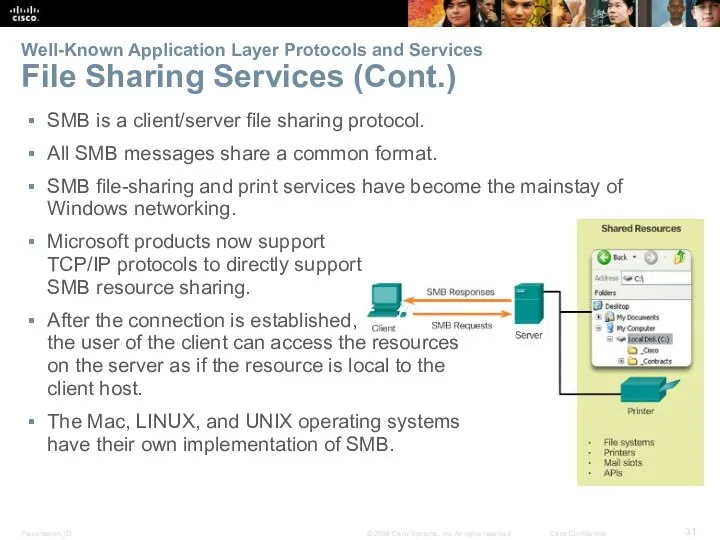
- 31. Well-Known Application Layer Protocols and Services File Sharing Services (Cont.) SMB is a client/server file sharing
- 32. 10.3 Summary
- 33. Explain the operation of the application layer in providing support to end-user applications. Explain how well-known
- 34. Chapter 10 New Terms and Commands Hypertext Transfer Protocol (HTTP) File Transfer Protocol (FTP) Trivial File
- 35. Chapter 10 New Terms and Commands IMAP Port 25 (SMTP) TCP Port 110 (POP) Domain name
- 38. Скачать презентацию











 Website quick critique report
Website quick critique report Что такое персональные данные. Персональные данные в сети Интернет
Что такое персональные данные. Персональные данные в сети Интернет Штрих-код
Штрих-код Cyberbullying
Cyberbullying Онлайн-платформы для создания электронных учебных курсов
Онлайн-платформы для создания электронных учебных курсов Электронная таблица
Электронная таблица Создание бизнес-доклада. (Тема 12)
Создание бизнес-доклада. (Тема 12) Разработка и эксплуатация АИС
Разработка и эксплуатация АИС Сети передачи данных
Сети передачи данных Компьютерные системы контроля в машиностроении. (Лекция 1)
Компьютерные системы контроля в машиностроении. (Лекция 1) Види векторної анімації: покадрова, руху, форми, з використанням криволінійних шляхів
Види векторної анімації: покадрова, руху, форми, з використанням криволінійних шляхів Электронные образовательные ресурсы
Электронные образовательные ресурсы ChatGPT для SEO специалиста
ChatGPT для SEO специалиста Урок 27.Преобразование информации путём рассуждений
Урок 27.Преобразование информации путём рассуждений Введение в вебтехнологии
Введение в вебтехнологии PHP. Управляющие конструкции
PHP. Управляющие конструкции Разработка тестов. Занятие 6
Разработка тестов. Занятие 6 Крутых идей для видео в TikTok
Крутых идей для видео в TikTok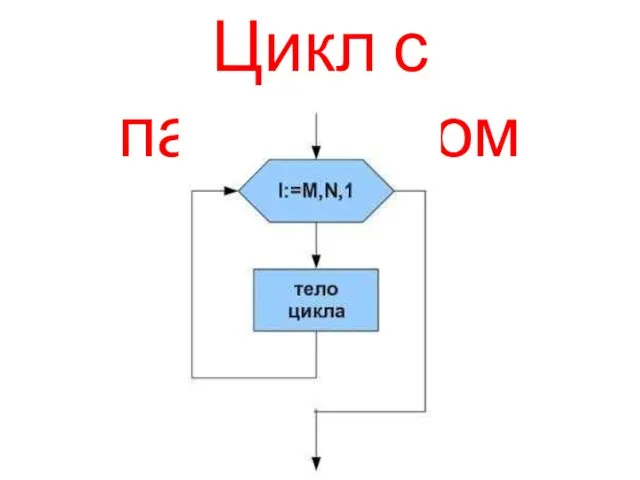 Цикл с параметром
Цикл с параметром Computer software Operating systems
Computer software Operating systems Правила компьютерного набора текста
Правила компьютерного набора текста Computer Science 686 Spring 2007. Intel EM64T and VT Extensions
Computer Science 686 Spring 2007. Intel EM64T and VT Extensions ВКР: Разработка игрового приложения жанра “Shooter” с использованием движка Unity
ВКР: Разработка игрового приложения жанра “Shooter” с использованием движка Unity Mobile SMARTS для ЕГАИС
Mobile SMARTS для ЕГАИС Устройство и функционирование информационной системы
Устройство и функционирование информационной системы Изучение методов создания прототипа модели с использованием установок аддитивного производства
Изучение методов создания прототипа модели с использованием установок аддитивного производства Презентация урока по информатике на тему Истинность и ложность высказываний. 3 класс
Презентация урока по информатике на тему Истинность и ложность высказываний. 3 класс Технологии проектирования информационных систем. Структурные модели предметной области
Технологии проектирования информационных систем. Структурные модели предметной области