Содержание
- 2. Literature Ramez Elmasri, Shamkant B. Navathe. Fundamentals of database systems: Sevens edition. - Pearson Education, 2016.
- 3. Test questions 1. Describe threats to databases. 2. Describe purpose of inference control 3. What is
- 4. Contents Main Concepts Control Measures Common threats and challenges Database Security Priority Areas
- 5. 1. Main Concepts Types of Security Threats to Databases Database Security - Part of a Common
- 6. 1. Types of Security Legal and ethical issues on the right to access information - for
- 7. Threats to Databases Loss of integrity. Database integrity refers to the requirement to protect information from
- 8. Database Security - Part of a Common System Database security is a complex and challenging endeavor
- 9. Types of control measures Access control Inference control Flow control Data encryption 2. Control Measures
- 10. 1. Types of control measures To protect databases from threats, there are general types of control
- 11. 2. Access control Database access control is a method of allowing access to company’s sensitive data
- 12. 1. Discretionary Access Control (DAC) Discretionary Access Control is a type of access control system that
- 13. 2. Mandatory Access Control (MAC) With mandatory access control, this security policy is centrally controlled by
- 14. 3. Role Based Access Control (RBAC) Role-based access control (RBAC) is a policy-neutral access-control mechanism defined
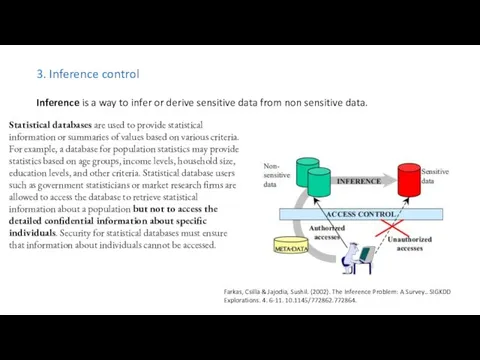
- 15. 3. Inference control Inference is a way to infer or derive sensitive data from non sensitive
- 16. 4. Flow control Flow Control − Distributed systems encompass a lot of data flow from one
- 17. 5. Data encryption Suppose we communicate data, but our data falls into the hands of a
- 18. 1. Insider threats 2. Human error 3. Exploitation of database software vulnerabilities 4. SQL/NoSQL injection attacks
- 19. 1. Insider threats An internal threat is a security risk from any of three sources with
- 20. 2. Human error Accidents, weak passwords, password sharing, and other unwise or uninformed user behaviours continue
- 21. 3. Exploitation of database software vulnerabilities Hackers make a living by detecting vulnerabilities in all types
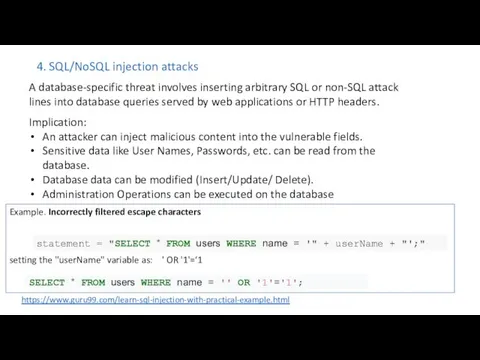
- 22. 4. SQL/NoSQL injection attacks A database-specific threat involves inserting arbitrary SQL or non-SQL attack lines into
- 23. 5. Buffer overflow exploitations Buffer overflow occurs when a process attempts to write more data to
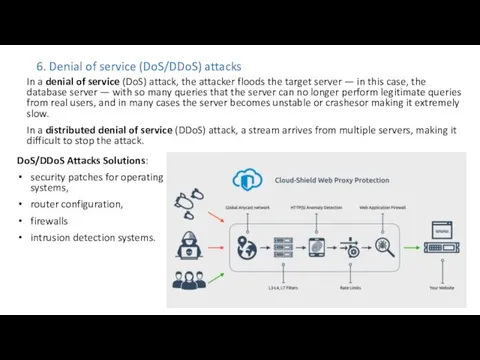
- 24. 6. Denial of service (DoS/DDoS) attacks In a denial of service (DoS) attack, the attacker floods
- 25. 7. Malware Malware is software written specifically to exploit vulnerabilities or otherwise cause damage to the
- 26. 8. Attacks on backups Threats are compounded by the following: Growing data volumes: Data capture, storage,
- 27. 1. Database Security Extension 2. Physical security, access controls and accounts 3. Encryption, software and applications
- 28. 1. Database Security Extension Because databases are nearly always network-accessible, any security threat to any component
- 29. 2. Physical security, access controls and accounts Physical security: Whether your database server is on-premise or
- 30. 3. Encryption, software and applications Encryption: ALL data—including data in the database, and credential data—should be
- 31. 4. Backup and Auditing Backup security: All backups, copies, or images of the database must be
- 33. Скачать презентацию













 MongoDB Authentication
MongoDB Authentication Программное обеспечение компьютера
Программное обеспечение компьютера ИТ в юриспруденции. Информационно-поисковые системы
ИТ в юриспруденции. Информационно-поисковые системы CSR
CSR Работаем с программами сервиса GOOGLE
Работаем с программами сервиса GOOGLE О чём может рассказать школьная библиотека
О чём может рассказать школьная библиотека Интерактивная проверка знаний при подготовке к сдаче ГИА по информатике
Интерактивная проверка знаний при подготовке к сдаче ГИА по информатике Types of data analysis Data analysis process
Types of data analysis Data analysis process Интерфейс и основные возможности графических редакторов
Интерфейс и основные возможности графических редакторов Разнообразие. Циклы
Разнообразие. Циклы Базы данных. Информационные системы. (Тема 1)
Базы данных. Информационные системы. (Тема 1) Понятие модели и моделирования
Понятие модели и моделирования Оценка деятельности служб защиты информации
Оценка деятельности служб защиты информации Взаимодействие со Службой занятости населения с помощью единой цифровой платформы Работа в России
Взаимодействие со Службой занятости населения с помощью единой цифровой платформы Работа в России Propositional logic
Propositional logic Использование особенностей ИСР для создания пользовательского интерфейса
Использование особенностей ИСР для создания пользовательского интерфейса Что такое инфографика
Что такое инфографика Оценка официальных пабликов Хабаровского края. Экспертное интервью
Оценка официальных пабликов Хабаровского края. Экспертное интервью Презентационные образцы мультимедийных презентаций 1 года обучения Оператор-пользователь ПЭВМ
Презентационные образцы мультимедийных презентаций 1 года обучения Оператор-пользователь ПЭВМ Процессор и его основные характеристики
Процессор и его основные характеристики Архивация данных. Обзор пакетов для архивации данных
Архивация данных. Обзор пакетов для архивации данных Аудитория пользователей интернета в России
Аудитория пользователей интернета в России Разработка модели и решение задачи управления запасами на примере компании К-спойлер
Разработка модели и решение задачи управления запасами на примере компании К-спойлер Режимы и способы обработки данных
Режимы и способы обработки данных Современные операционные системы
Современные операционные системы Урок информатики, 10 класс Технология создания презентации (гиперссылки и управляющие кнопки)
Урок информатики, 10 класс Технология создания презентации (гиперссылки и управляющие кнопки) Студия разработки мобильных и web приложений ООО JDG
Студия разработки мобильных и web приложений ООО JDG Глобальная компьютерная сеть Интернет
Глобальная компьютерная сеть Интернет