Содержание
- 2. Agenda Memory forensics Why? How? Previous memory anti-forensic techniques Windows related Memory acquisition process – flawed
- 3. whoami As Carlos would say – nobody (but working on a privilege escalation) In six (and
- 4. Memory forensics – why? Disk forensics prevalent, but memory forensics increasingly popular Used by incident handlers…
- 5. Memory forensics – how? Two consecutive processes Memory acquisition Memory analysis Acquisition (software based) Many tools,
- 6. Memory forensics – how? (2) Acquisition internals User mode and kernel mode (driver) component Why driver?
- 7. Memory forensics – how? (3) Format differences Crash dump contains registers, but no first page and
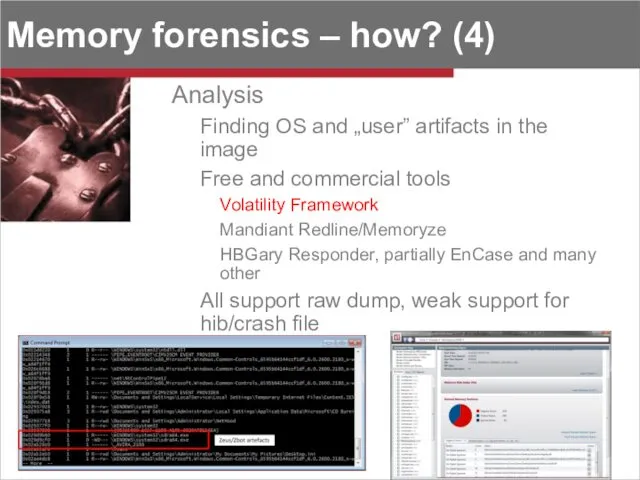
- 8. Memory forensics – how? (4) Analysis Finding OS and „user” artifacts in the image Free and
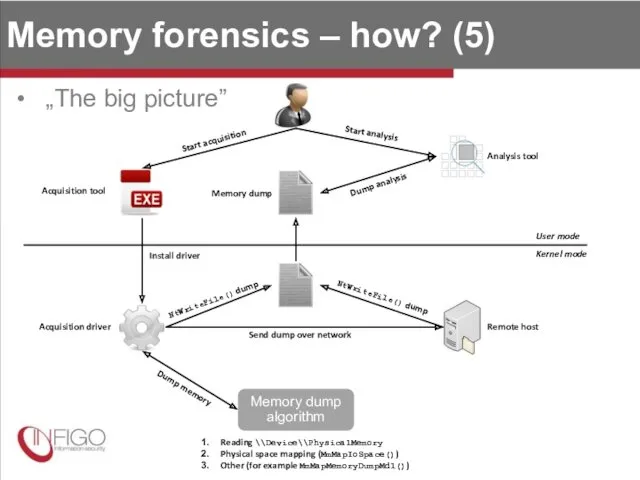
- 9. Memory forensics – how? (5) „The big picture” Start acquisition Acquisition tool Acquisition driver Memory dump
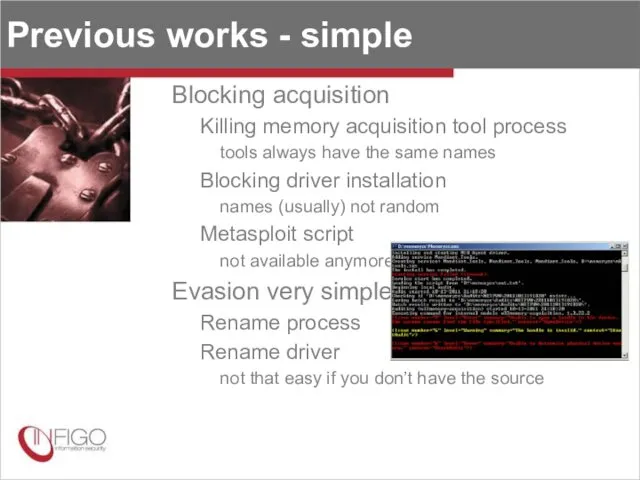
- 10. Previous works - simple Blocking acquisition Killing memory acquisition tool process tools always have the same
- 11. Previous works – advanced Blocking analysis Haruyama/Suzuki BH-EU-12: One-byte Modification for Breaking Memory Forensic Analysis minimal
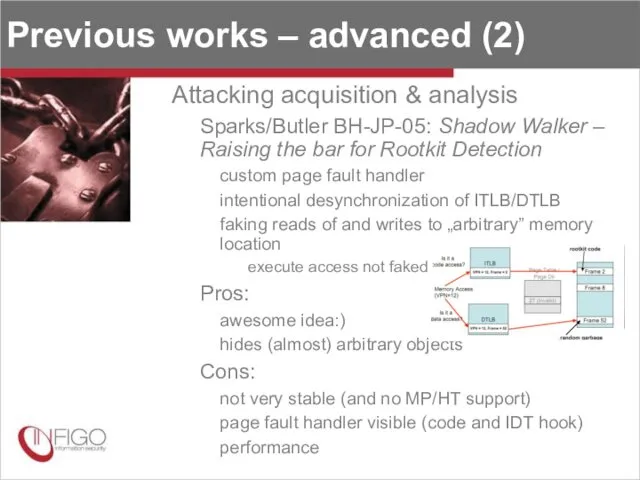
- 12. Previous works – advanced (2) Attacking acquisition & analysis Sparks/Butler BH-JP-05: Shadow Walker – Raising the
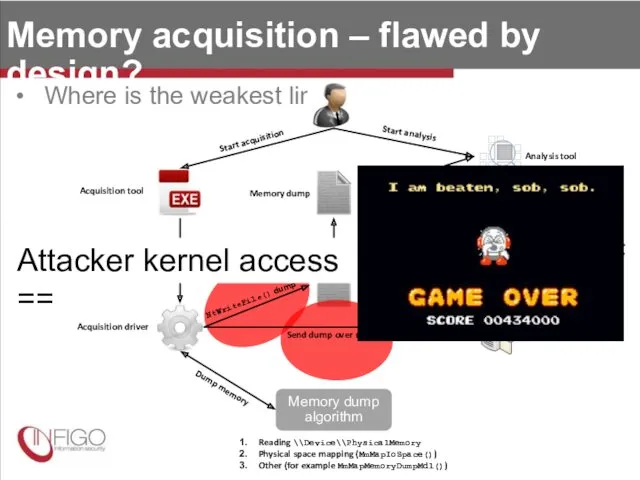
- 13. Memory acquisition – flawed by design? Where is the weakest link? Start acquisition Acquisition tool Acquisition
- 14. Sounds familiar? Of course it does, it’s an old technique! Darren Bilby – DDefy rootkit (BH-JP-06)
- 15. Defeating Windows memory forensics Introducing Dementia PoC tool for hiding objects in memory dumps User mode
- 16. Dementia – How? Intercepting NtWriteFile() calls Two methods inline hook stable even on multi(core)processor systems, but
- 17. Dementia – Detecting forensic app? OK, we have the „hook” in place, but what now? Is
- 18. Dementia – Hiding? Hook installed and memory dump detected - what’s next? Memory is read and
- 19. Dementia – Hiding? (2) That sounds fine… .. but we’re dealing with undocumented kernel structures, functions,
- 20. Dementia – Hiding Processes Get the target process EPROCESS block „Unlink” the process from the various
- 21. Dementia – Hiding Processes (2) Hiding processes is deceptively simple However, traces of process activity are
- 22. Dementia – Hiding Threads All threads of target process are hidden Clear „Thre” allocations Remove thread
- 23. Dementia – Hiding Handles and Objects Rather deep cleansing Hide process handle table Unlink it from
- 24. Dementia – Hiding Handles and Objects (2) Wait, there is more! PspCidTable and csrss.exe handle table
- 25. Dementia – Hiding Memory Allocations All process memory allocations are described by VADs – Virtual Address
- 26. Dementia – Hiding Drivers Apart from the process hiding, drivers can be hidden too Unlink from
- 27. Finally!
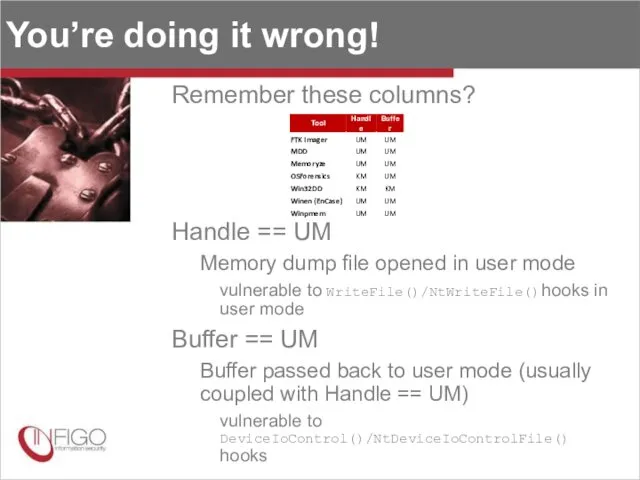
- 28. You’re doing it wrong! Remember these columns? Handle == UM Memory dump file opened in user
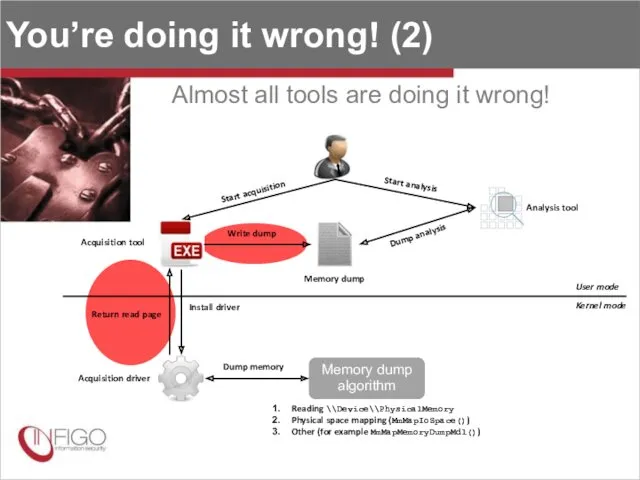
- 29. You’re doing it wrong! (2) Almost all tools are doing it wrong! Start acquisition Acquisition tool
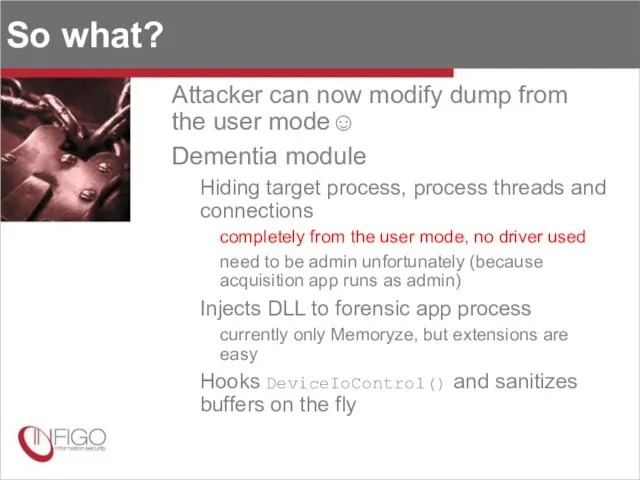
- 30. So what? Attacker can now modify dump from the user mode☺ Dementia module Hiding target process,
- 31. Dementia user mode - internals Sounds simpler than the kernel mode Actually, it is much harder!
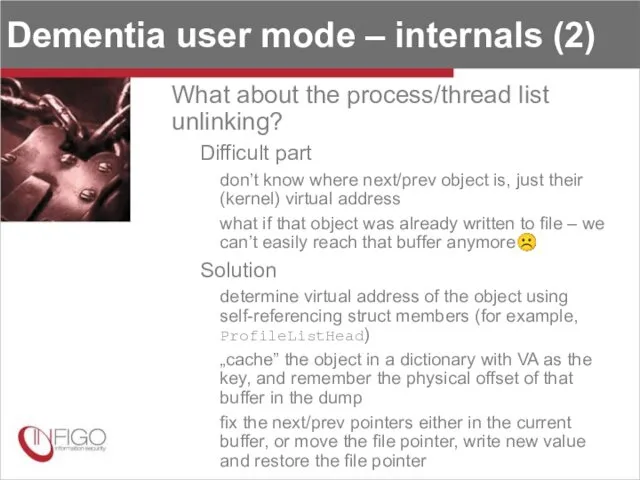
- 32. Dementia user mode – internals (2) What about the process/thread list unlinking? Difficult part don’t know
- 33. Demo again!
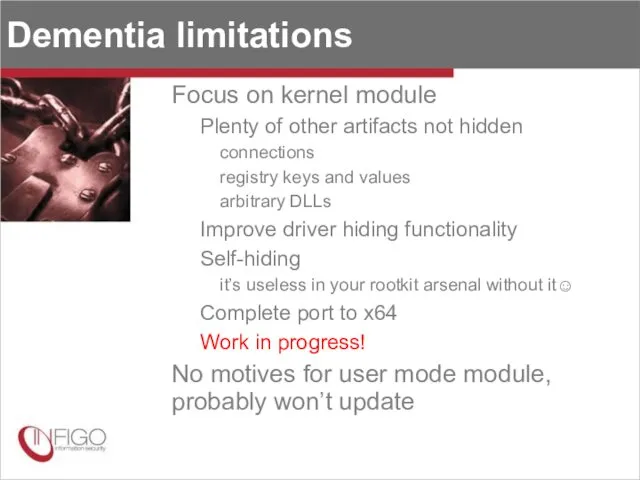
- 34. Dementia limitations Focus on kernel module Plenty of other artifacts not hidden connections registry keys and
- 35. Conclusions & possible solutions Acquisition tools should utilize drivers correctly! Current method is both insecure and
- 37. Скачать презентацию














 Шаблон презентации проекта
Шаблон презентации проекта Другие нейросети. Урок 4.3
Другие нейросети. Урок 4.3 Алгоритмизация и программирование
Алгоритмизация и программирование Цифровой логический уровень архитектуры ЭВМ
Цифровой логический уровень архитектуры ЭВМ Среда программирования Рaskal АВС
Среда программирования Рaskal АВС Использование R для контроля обработки резьбы
Использование R для контроля обработки резьбы Отчет по учебной практике ПМ08. Разработка дизайна веб-приложений
Отчет по учебной практике ПМ08. Разработка дизайна веб-приложений Динамика на web-страницах. Всё о JS. Библиотеки
Динамика на web-страницах. Всё о JS. Библиотеки Безопасный интернет детям
Безопасный интернет детям Введение в дисциплину SEO продвижение. Занятие 1
Введение в дисциплину SEO продвижение. Занятие 1 Тестировщик программного обеспечения. Занятие 7
Тестировщик программного обеспечения. Занятие 7 Информационные преступления и информационная безопасность
Информационные преступления и информационная безопасность Система управления базами данных Access. Лекция 1
Система управления базами данных Access. Лекция 1 Программирование на языке Си
Программирование на языке Си Вредоносное программное обеспечение. Вирусы
Вредоносное программное обеспечение. Вирусы Основные операторы. Решение задач с использованием основных операторов. Тема 3
Основные операторы. Решение задач с использованием основных операторов. Тема 3 Автоматизированная система оперативного управления перевозками (АСОУП)
Автоматизированная система оперативного управления перевозками (АСОУП) Кодирование графической информации
Кодирование графической информации Файлы и файловые структуры. Компьютер как универсальное устройство для работы с информацией. Информатика. 7 класс
Файлы и файловые структуры. Компьютер как универсальное устройство для работы с информацией. Информатика. 7 класс Криптография. Основные задачи криптографии
Криптография. Основные задачи криптографии Определение количества информации. 8 класс
Определение количества информации. 8 класс Принципы построения распределенных баз данных
Принципы построения распределенных баз данных История чисел и систем счисления
История чисел и систем счисления 8 класс. Кодирование и обработка числовой информации
8 класс. Кодирование и обработка числовой информации УСЛОВНЫЙ ОПЕРАТОР
УСЛОВНЫЙ ОПЕРАТОР Системы счисления. Перевод чисел из одной системы счисления в другую систему счисления
Системы счисления. Перевод чисел из одной системы счисления в другую систему счисления Проект Старые диски
Проект Старые диски Представление информации. Языки. Кодирование
Представление информации. Языки. Кодирование