Содержание
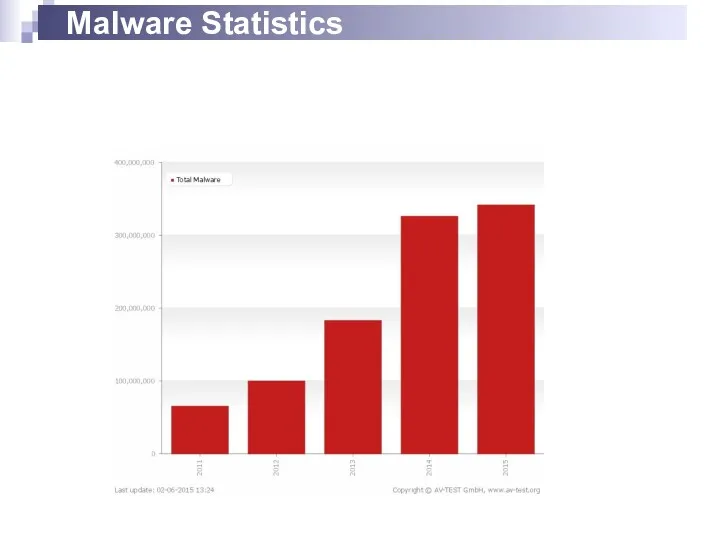
- 2. Malware Statistics
- 3. TROJANS AND BACKDOORS
- 4. Trojan Is defined as a "malicious, security breaking program that is disguised as something benign" A
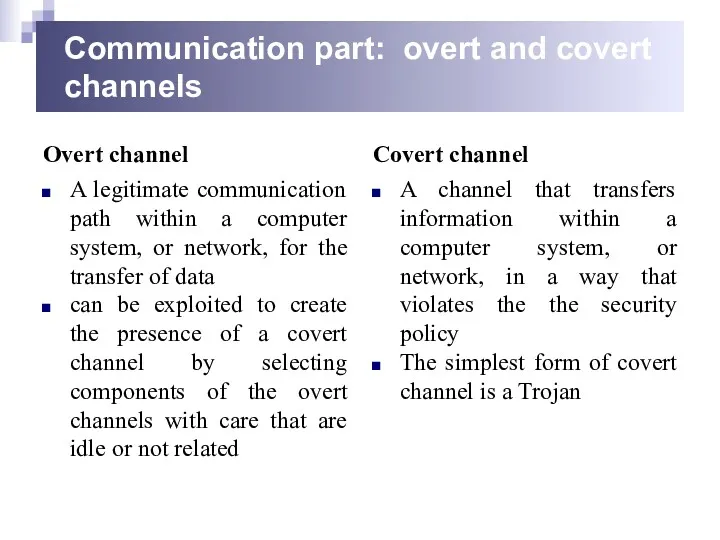
- 5. Communication part: overt and covert channels Overt channel A legitimate communication path within a computer system,
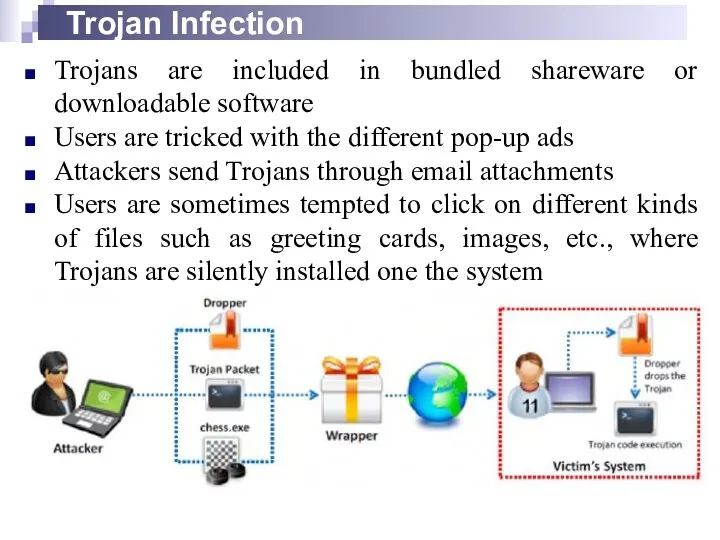
- 6. Trojan Infection Trojans are included in bundled shareware or downloadable software Users are tricked with the
- 7. Access points are used by Trojans Instant messenger applications (ICQ) IRC ( Internet Relay Chat )
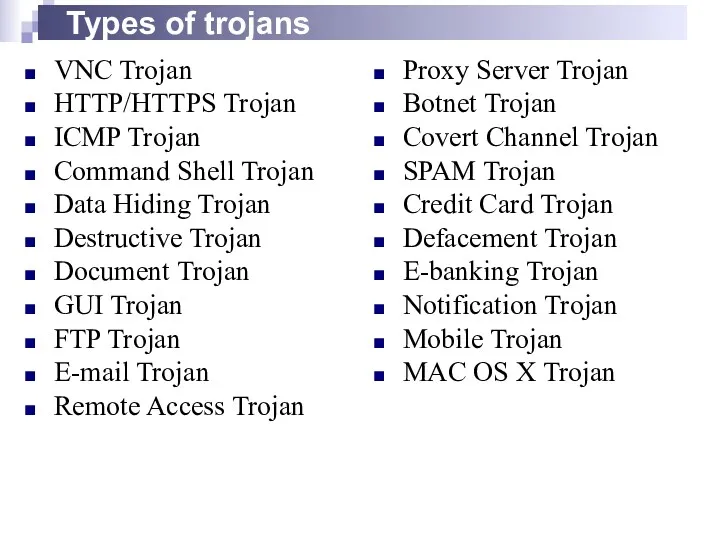
- 8. Types of trojans VNC Trojan HTTP/HTTPS Trojan ICMP Trojan Command Shell Trojan Data Hiding Trojan Destructive
- 9. Command shell trojans The command shell trojan gives remote control of a command shell on a
- 10. TROJAN DETECTION
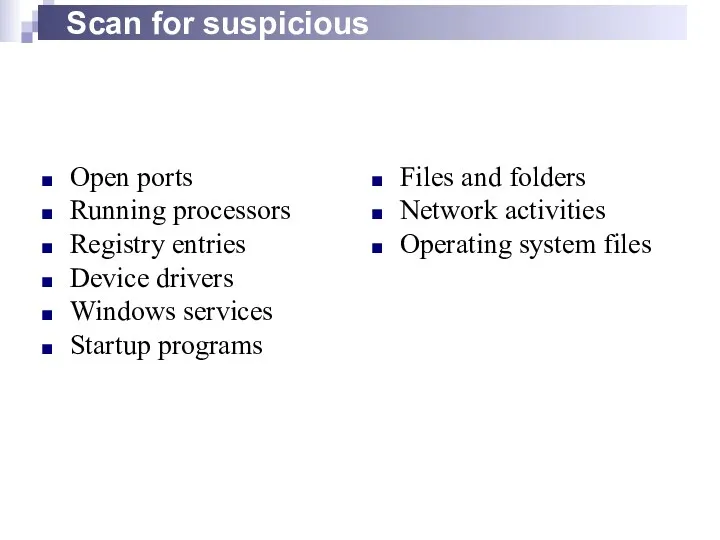
- 11. Scan for suspicious Open ports Running processors Registry entries Device drivers Windows services Startup programs Files
- 12. Scanning for suspicious processes Trojans camouflage themselves as genuine Windows services Use PEs (Portable Executable) to
- 13. Windows automatically execute instructions in the following section of the registry: Run RunServices RunOnce RunServicesOnce HKEY_CLASSES_ROOT\exefile\shell\open\command
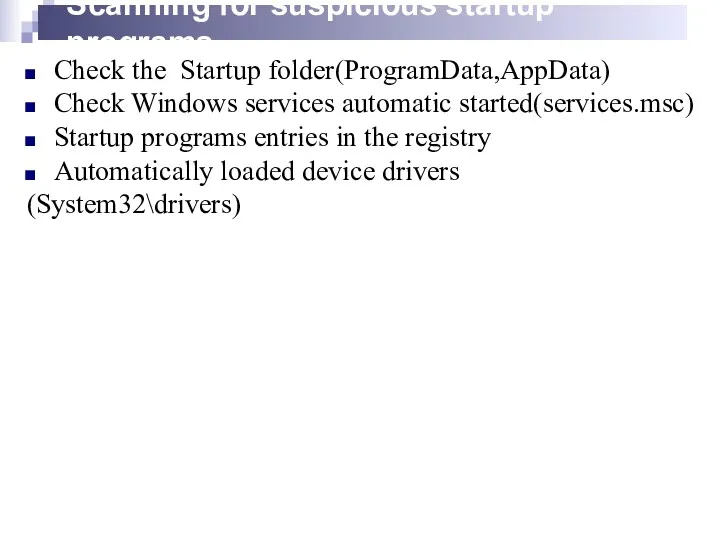
- 14. Scanning for suspicious startup programs Check the Startup folder(ProgramData,AppData) Check Windows services automatic started(services.msc) Startup programs
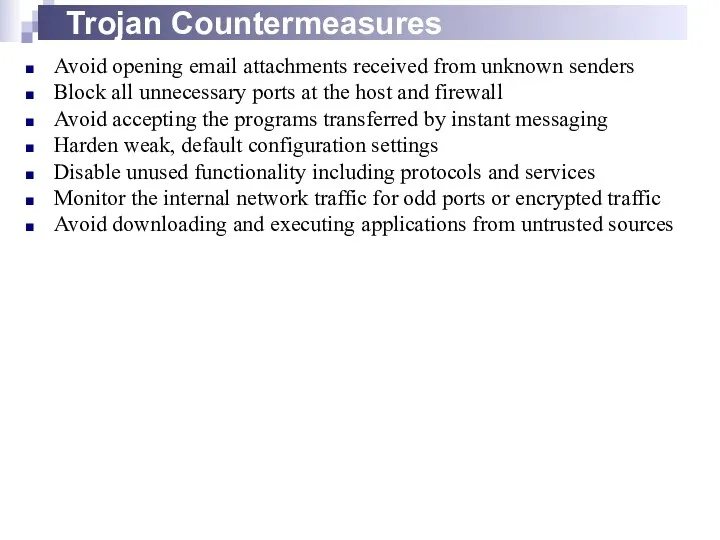
- 15. Trojan Countermeasures Avoid opening email attachments received from unknown senders Block all unnecessary ports at the
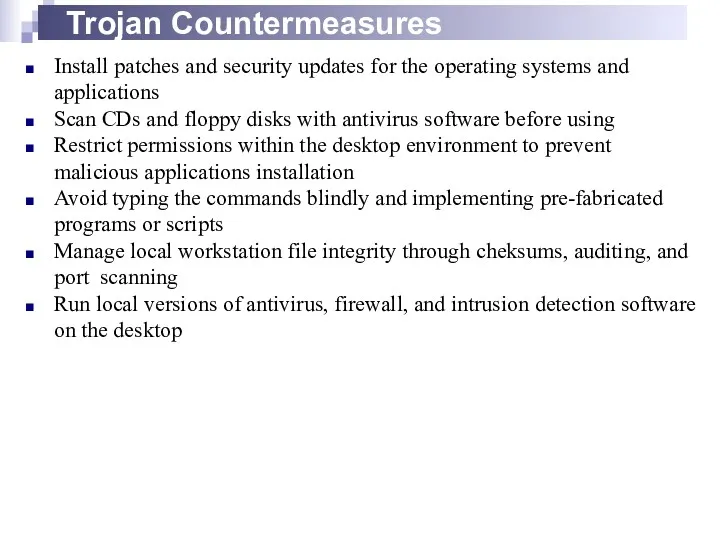
- 16. Trojan Countermeasures Install patches and security updates for the operating systems and applications Scan CDs and
- 17. Summary Trojans are malicious pieces of code that carry cracker software to a target system. They
- 18. VIRUSES AND WORMS
- 19. Introduction to Viruses A virus is a self-replicating program that produces its own code by attaching
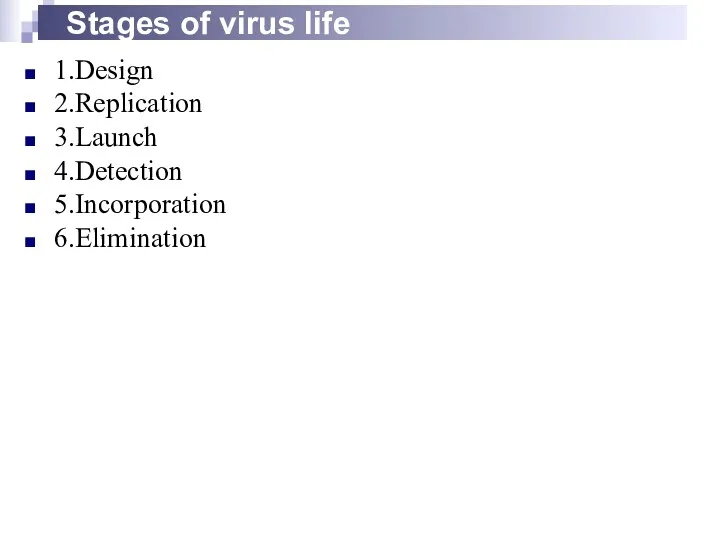
- 20. Stages of virus life 1.Design 2.Replication 3.Launch 4.Detection 5.Incorporation 6.Elimination
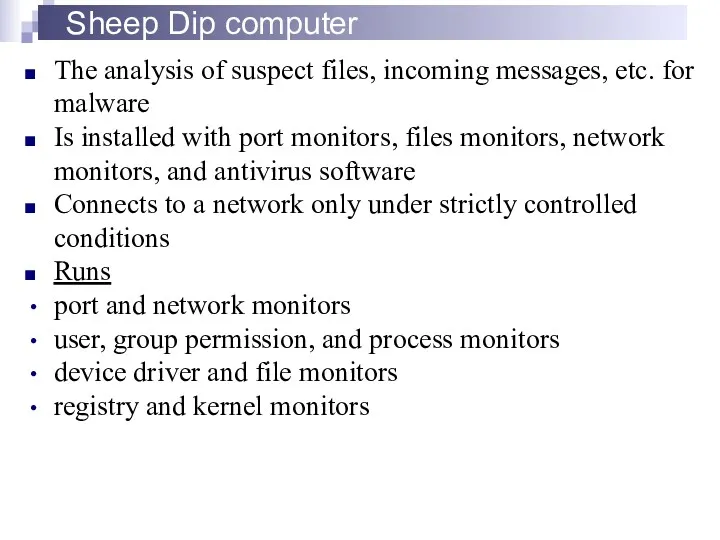
- 21. Sheep Dip computer The analysis of suspect files, incoming messages, etc. for malware Is installed with
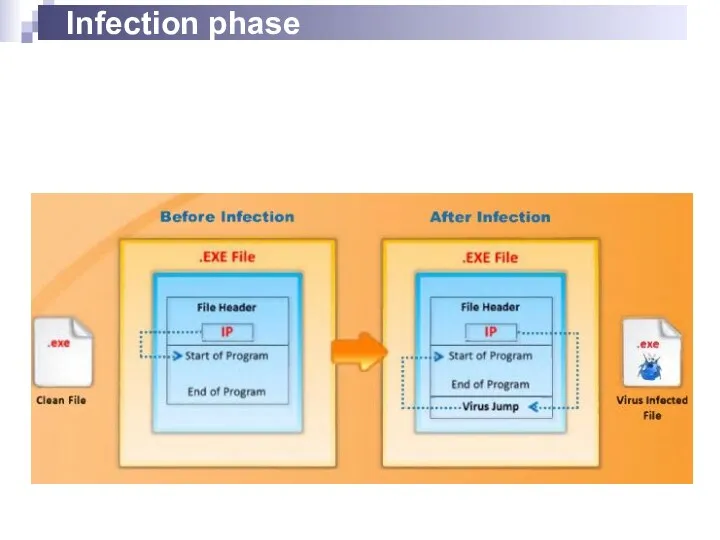
- 22. Infection phase
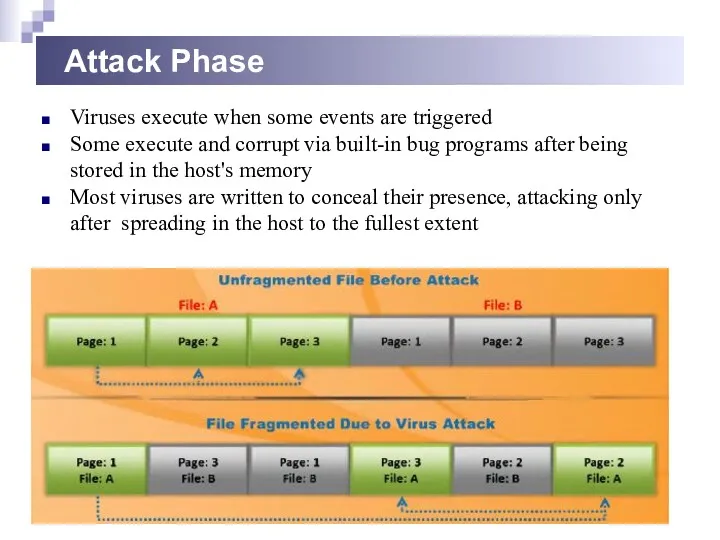
- 23. Attack Phase Viruses execute when some events are triggered Some execute and corrupt via built-in bug
- 24. Indications of virus attacks Programs take longer to load The hard drive is always full, even
- 25. How does a computer get infected by viruses When a user accepts files and download s
- 26. Types of viruses (what do they infect) System or boot sector viruses File viruses Multipartite viruses
- 27. Types of viruses (how do they infect) Stealth viruses Tunneling viruses Encryption viruses Polymorphic viruses Metamorphic
- 28. Computer worms Computer worms are malicious programs that replicate, execute, and spread across network connections independently,
- 29. Virus vs Worm Virus cannot be spread to other computers unless an infected file is replicated
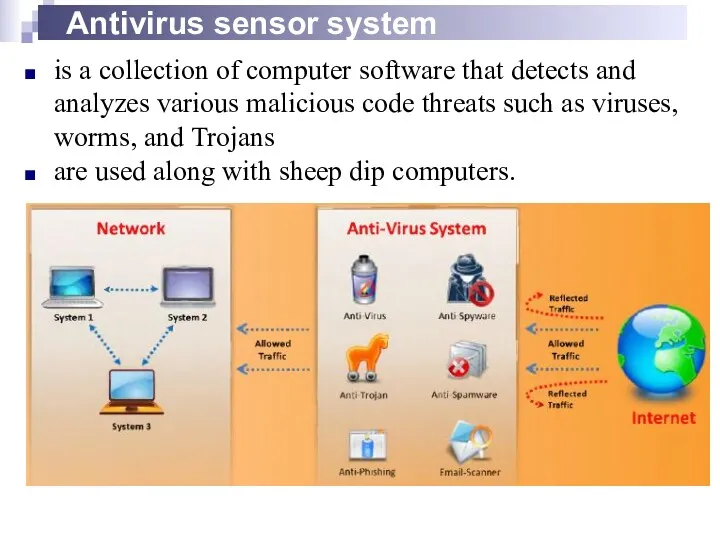
- 30. Antivirus sensor system is a collection of computer software that detects and analyzes various malicious code
- 31. Malware analysis
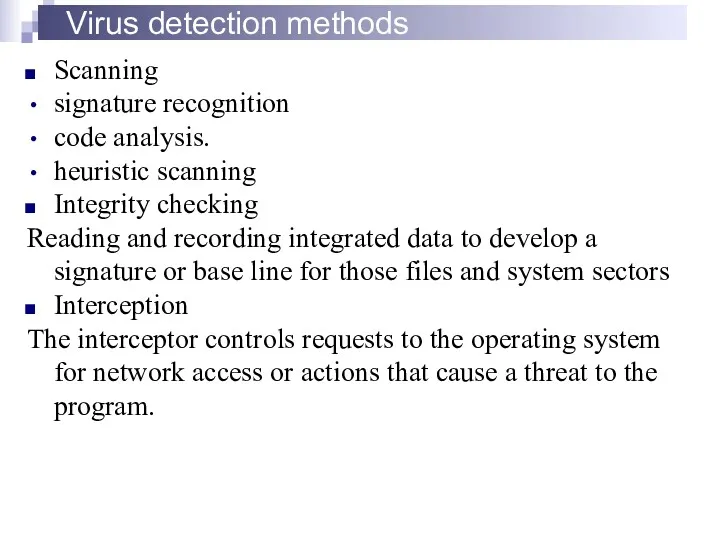
- 32. Virus detection methods Scanning signature recognition code analysis. heuristic scanning Integrity checking Reading and recording integrated
- 33. Virus and worms countermeasures Install antivirus software that detects and removes infections as they appear Generate
- 35. Скачать презентацию














 Темпоральные логики и их применение в верификации реагирующих программных систем
Темпоральные логики и их применение в верификации реагирующих программных систем Концепция машины с хранимой в памяти программой. (Тема 2)
Концепция машины с хранимой в памяти программой. (Тема 2) Комп’ютерні віруси
Комп’ютерні віруси Информационные технологии. ИТ. Web – технологии. Лекция 4
Информационные технологии. ИТ. Web – технологии. Лекция 4 Презентация Оператор ветвления Case
Презентация Оператор ветвления Case Подсистема ввода-вывода. Файловые системы
Подсистема ввода-вывода. Файловые системы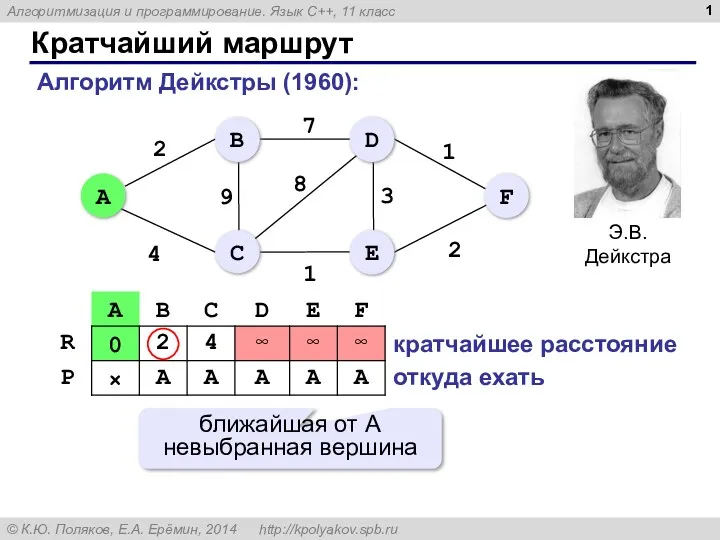 Кратчайший маршрут. Алгоритмизация и программирование. Язык С++, 11 класс
Кратчайший маршрут. Алгоритмизация и программирование. Язык С++, 11 класс Симплекс-метод
Симплекс-метод Методические особенности подготовки учащихся к итоговой аттестации по информатике с учетом требований нового образовательного стандарта
Методические особенности подготовки учащихся к итоговой аттестации по информатике с учетом требований нового образовательного стандарта Интернет в работе переводчика
Интернет в работе переводчика Очередность работ при последовательной схеме технологического процесса
Очередность работ при последовательной схеме технологического процесса Қоғамның негізгі секторларындағы ICT рөлі. ICT стандарттары
Қоғамның негізгі секторларындағы ICT рөлі. ICT стандарттары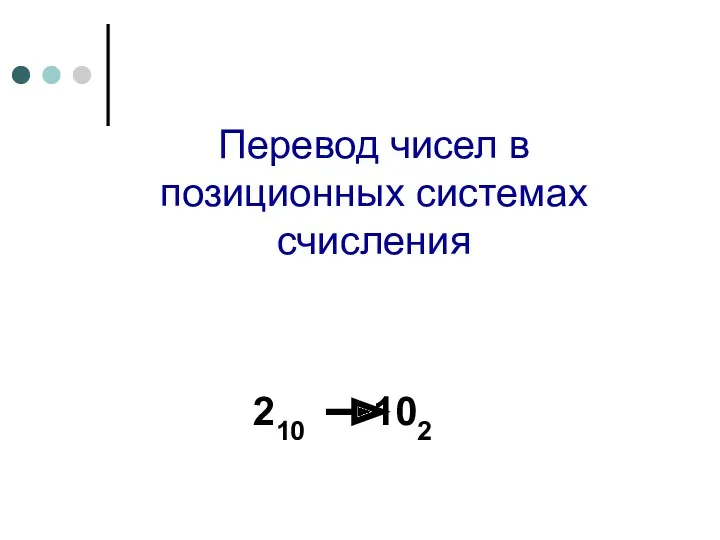 Перевод чисел из одной системы счисления в другую
Перевод чисел из одной системы счисления в другую Информатика и ИКТ. Введение
Информатика и ИКТ. Введение Урок Алгоритмы с повторение
Урок Алгоритмы с повторение Визитки X-профиль
Визитки X-профиль Всероссийская форумная компания
Всероссийская форумная компания Массив вида N*N
Массив вида N*N Информационные технологии в дополнительном образовании детей
Информационные технологии в дополнительном образовании детей Базы данных и системы управления ими
Базы данных и системы управления ими Компьютерные сети, Интернет и мультимедиа технологии. Основы сетей передачи данных
Компьютерные сети, Интернет и мультимедиа технологии. Основы сетей передачи данных Smart Technologies. Automation and Robotics
Smart Technologies. Automation and Robotics Разработка и использование стиля. Форматирование символов, абзацев и заголовков Word 2007
Разработка и использование стиля. Форматирование символов, абзацев и заголовков Word 2007 Лекция Программное обеспечение
Лекция Программное обеспечение Электронная библиотека Национальной библиотеки Республики Саха (Якутия)
Электронная библиотека Национальной библиотеки Республики Саха (Якутия) Влияние социальных сетей на личность подростка
Влияние социальных сетей на личность подростка Организация отказоустойчивой сети
Организация отказоустойчивой сети Програмні засоби комп'ютерної графіки
Програмні засоби комп'ютерної графіки