Содержание
- 2. Unless otherwise noted, the content of these slides are licensed under a Creative Commons Attribution 3.0
- 3. Lets Meet some Nice People http://en.wikipedia.org/wiki/Alice_and_Bob
- 4. People With Bad Intent Carol, Carlos or Charlie, as a third participant in communications. Chuck, as
- 5. Paranoia Who is out to get you? If you are interesting or influential people want to
- 6. Alan Turing and Bletchley Park Top secret code breaking effort 10,000 people at the peak (team
- 7. http://en.wikipedia.org/wiki/Bombe
- 8. http://en.wikipedia.org/wiki/Colossus_computer http://en.wikipedia.org/wiki/Tony_Sale
- 9. http://nmap.org/movies.html
- 10. Security is always a Tradeoff "Perfect security" is unachievable - Must find the right tradeoff Security
- 11. Terminology Confidentiality Prevent unauthorized viewing of private information Integrity Information is from who you think it
- 12. Ensuring Confidentiality Encryption and Decryption
- 13. Terminology Plaintext is a message that will be put into secret form. Ciphertext is a transformed
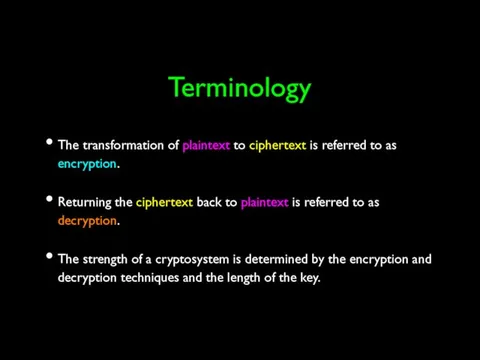
- 14. Terminology The transformation of plaintext to ciphertext is referred to as encryption. Returning the ciphertext back
- 15. Two Kinds of Systems Two basic types of cryptosystems exist, secret-key and public-key. In a secret-key
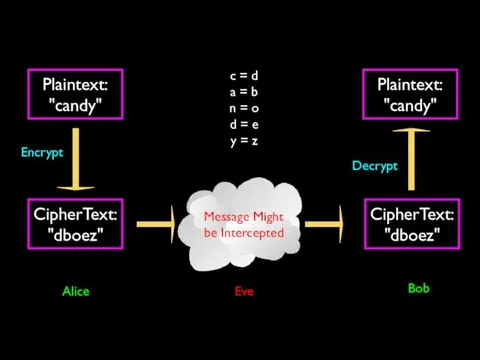
- 16. Plaintext: "candy" Message Might be Intercepted CipherText: "dboez" Encrypt CipherText: "dboez" Plaintext: "candy" Decrypt c =
- 17. Caeser Cipher http://en.wikipedia.org/wiki/Caesar_cipher Caesar cipher is one of the simplest and most widely known encryptionCaesar cipher
- 18. http://www.youtube.com/watch?v=zdA__2tKoIU Secret Decoder Ring
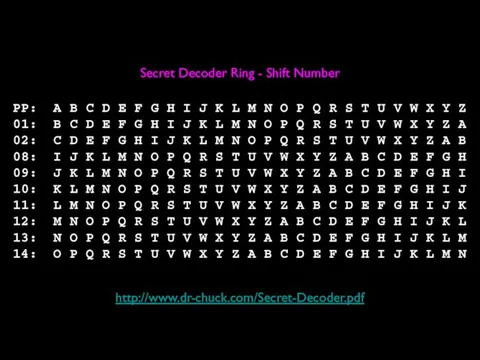
- 19. PP: A B C D E F G H I J K L M N O
- 20. Break the Code I CipherText: "upbtu" For each number 1..26, see if when you decrypt the
- 21. Break the Code II Uryyb, zl anzr vf Puhpx naq V arrq zbarl naq n wrg.
- 22. Cryptographic Hashes Integrity
- 23. Terminology Confidentiality Prevent unauthorized viewing of private information Integrity Information is from who you think it
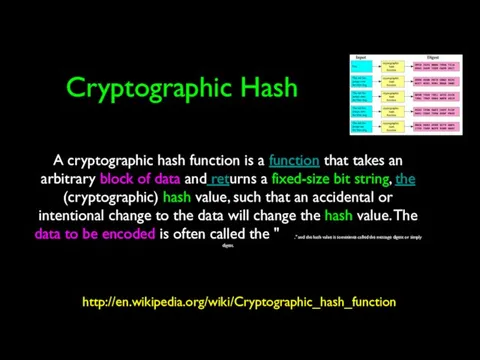
- 24. Cryptographic Hash http://en.wikipedia.org/wiki/Cryptographic_hash_function A cryptographic hash function is a function that takes an arbitrary block of
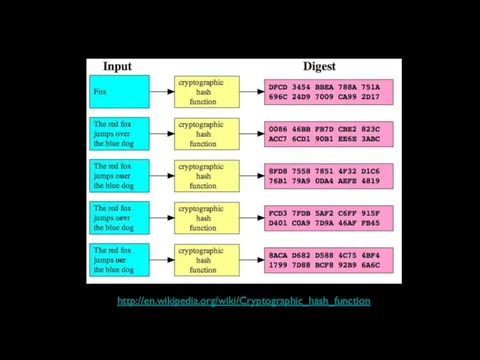
- 25. http://en.wikipedia.org/wiki/Cryptographic_hash_function
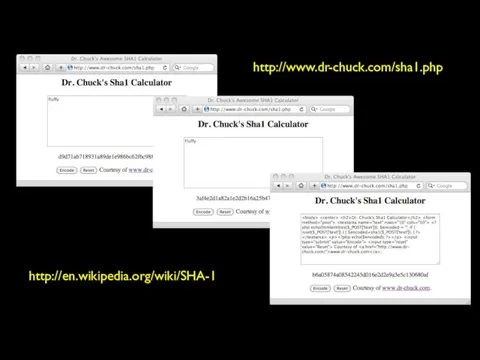
- 26. http://en.wikipedia.org/wiki/SHA-1 http://www.dr-chuck.com/sha1.php
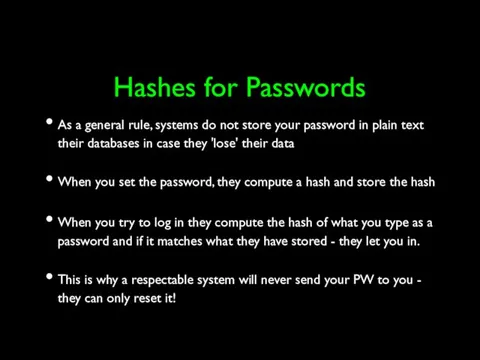
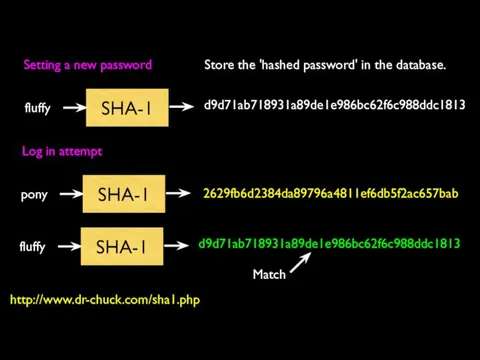
- 27. Hashes for Passwords As a general rule, systems do not store your password in plain text
- 28. SHA-1 fluffy d9d71ab718931a89de1e986bc62f6c988ddc1813 Store the 'hashed password' in the database. Setting a new password SHA-1 pony
- 29. Digital Signatures Message Integrity
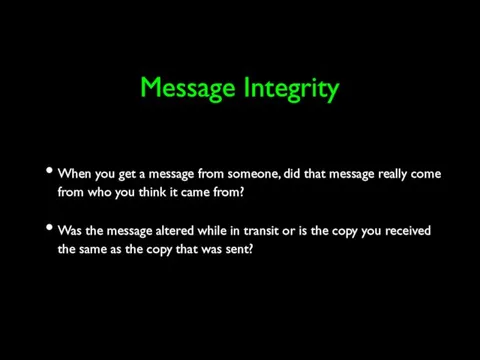
- 30. Message Integrity When you get a message from someone, did that message really come from who
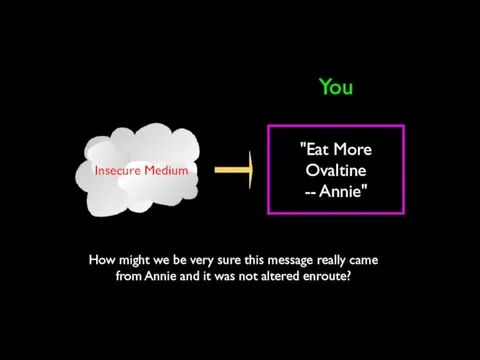
- 31. "Eat More Ovaltine -- Annie" You How might we be very sure this message really came
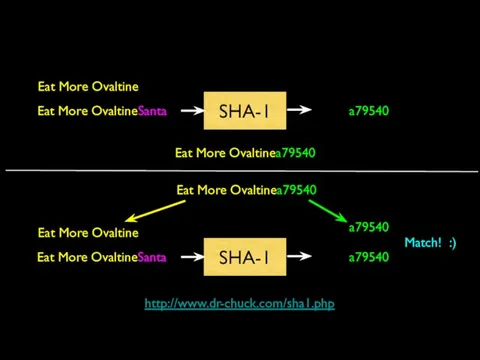
- 32. Simple Message Signing Shared secret transported securely 'out of band' Before sending the message, concatenate the
- 33. Receiving a Signed Message Receive message + digest from insecure transport Remove digest and add secret
- 34. Eat More Ovaltine Eat More OvaltineSanta SHA-1 a79540 Eat More Ovaltinea79540 Eat More Ovaltinea79540 Eat More
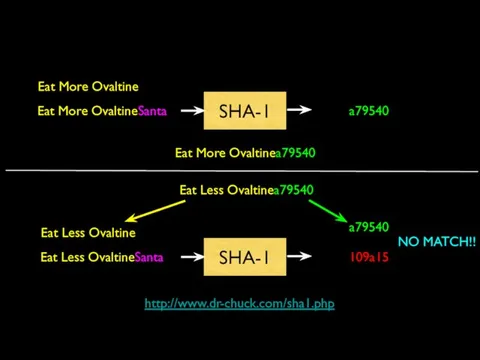
- 35. Eat More Ovaltine Eat More OvaltineSanta SHA-1 a79540 Eat More Ovaltinea79540 Eat Less Ovaltinea79540 Eat Less
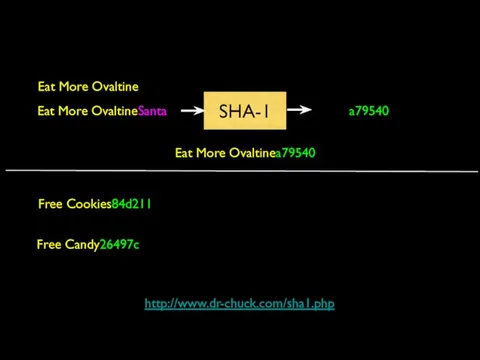
- 36. Eat More Ovaltine Eat More OvaltineSanta SHA-1 a79540 Eat More Ovaltinea79540 Free Cookies84d211 Free Candy26497c http://www.dr-chuck.com/sha1.php
- 37. Secret Key Shortcomings Every pair of people/systems needs a secret key In the Internet, key distribution
- 38. Public Key Encryption Confidentiality
- 39. Grezvabybtl Pbasvqragvnyvgl Cerirag hanhgubevmrq ivrjvat bs cevingr vasbezngvba Vagrtevgl Vasbezngvba vf sebz jub lbh guvax vg
- 40. Terminology Confidentiality Prevent unauthorized viewing of private information Integrity Information is from who you think it
- 41. Public Key Encryption Proposed by Whitfield Diffie and Martin Hellman in 1976 Public-key cryptosystems rely on
- 42. https://www.youtube.com/watch?v=ROCray7RTqM http://en.wikipedia.org/wiki/Whitfield_Diffie http://en.wikipedia.org/wiki/Martin_Hellman http://en.wikipedia.org/wiki/Ralph_Merkle
- 43. Public Key A message encrypted with one of the keys can only be decrypted with the
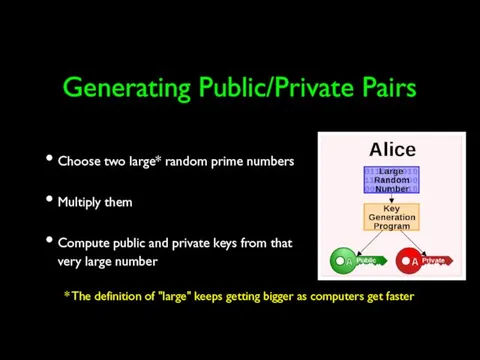
- 44. Generating Public/Private Pairs Choose two large* random prime numbers Multiply them Compute public and private keys
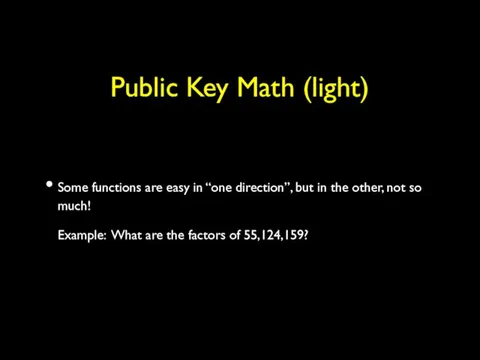
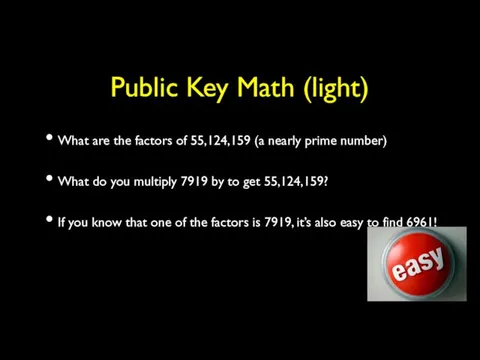
- 45. Public Key Math (light) Some functions are easy in “one direction”, but in the other, not
- 46. Public Key Math (light) What are the factors of 55,124,159 (a nearly prime number) What do
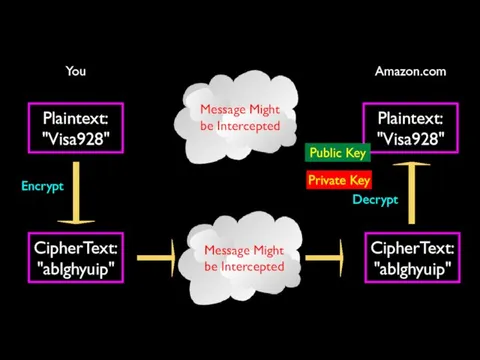
- 47. Plaintext: "Visa928" Public Key Private Key You Amazon.com
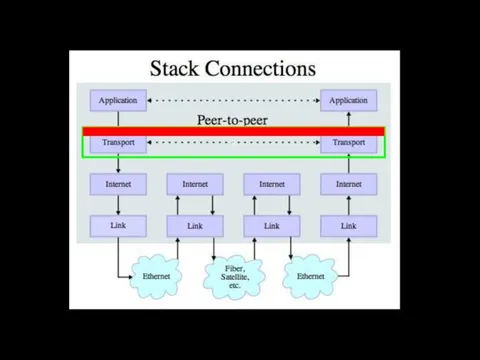
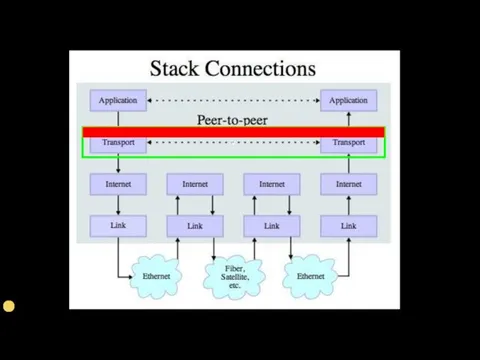
- 48. Secure Sockets Layer (SSL) Security for TCP http://en.wikipedia.org/wiki/Secure_Sockets_Layer
- 49. v
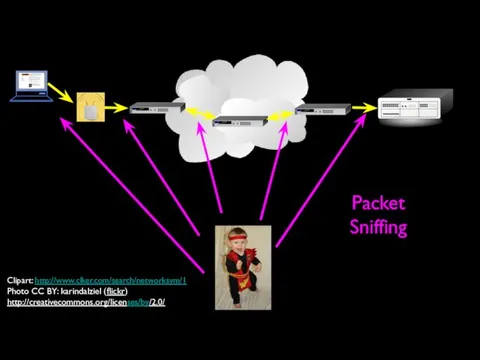
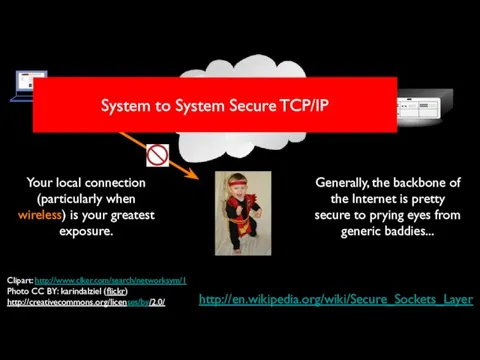
- 50. Packet Sniffing Clipart: http://www.clker.com/search/networksym/1 Photo CC BY: karindalziel (flickr) http://creativecommons.org/licenses/by/2.0/
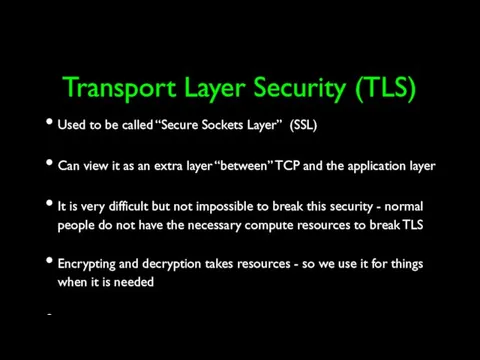
- 51. Transport Layer Security (TLS) Used to be called “Secure Sockets Layer” (SSL) Can view it as
- 52. Secure Application Protocols There are often secure and unencrypted application protocols http://www.facebook.com https://www.facebook.com Your browser tells
- 53. http://en.wikipedia.org/wiki/Secure_Sockets_Layer Generally, the backbone of the Internet is pretty secure to prying eyes from generic baddies...
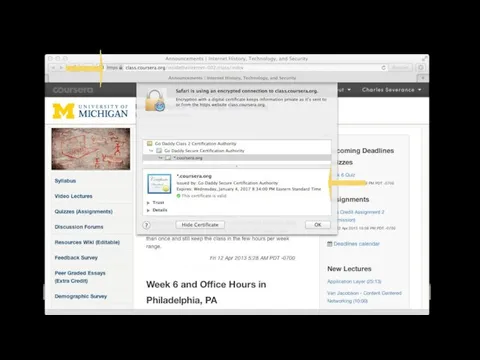
- 54. Certificate Authorities Integrity
- 56. Digital Certificates http://en.wikipedia.org/wiki/Public_key_certificate In cryptography, a public key certificate (also known as a digital certificate or
- 57. Certificate Authority (CA) http://en.wikipedia.org/wiki/Certificate_authority Text A certificate authority is an entity that issues digital certificatesA certificate
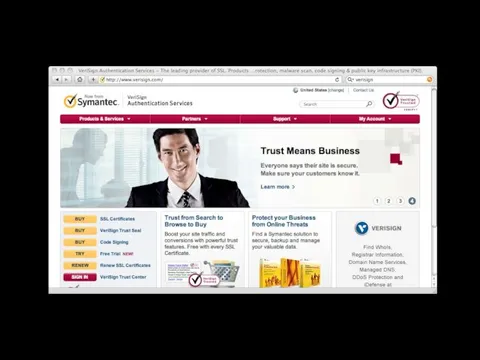
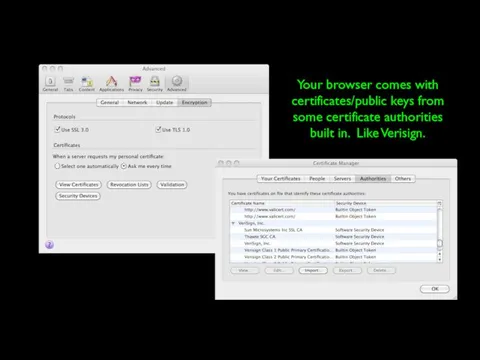
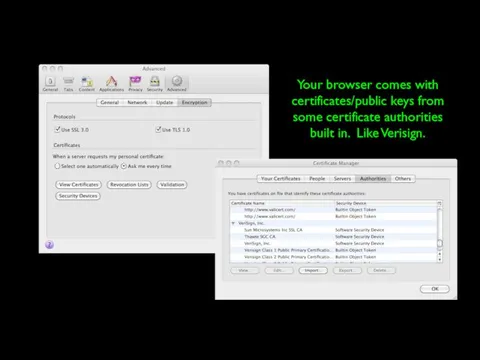
- 59. Your browser comes with certificates/public keys from some certificate authorities built in. Like Verisign.
- 60. Public-Key Issues Public-key cryptosystems have the problem of securely associating a public key with an individual
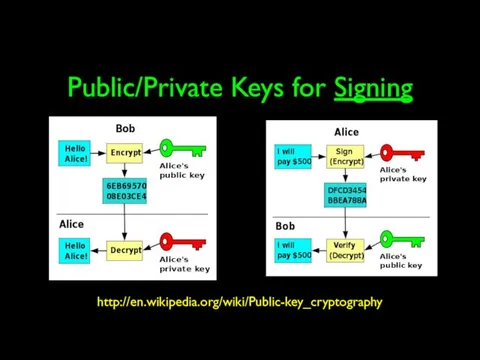
- 61. Public/Private Keys for Signing http://en.wikipedia.org/wiki/Public-key_cryptography
- 62. Digital Certificates http://en.wikipedia.org/wiki/Public_key_certificate In cryptography, a public key certificate (also known as a digital certificate or
- 63. Certificate Authority (CA) http://en.wikipedia.org/wiki/Certificate_authority Text A certificate authority is an entity that issues digital certificatesA certificate
- 65. Your browser comes with certificates/public keys from some certificate authorities built in. Like Verisign.
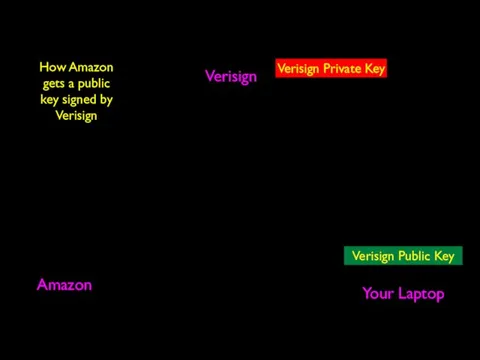
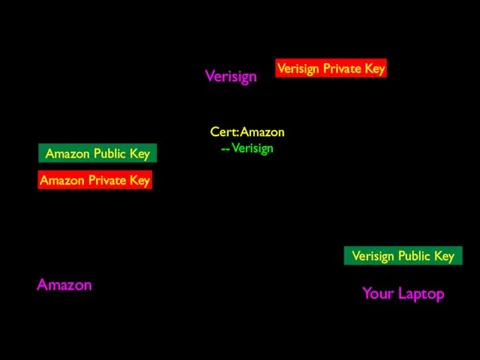
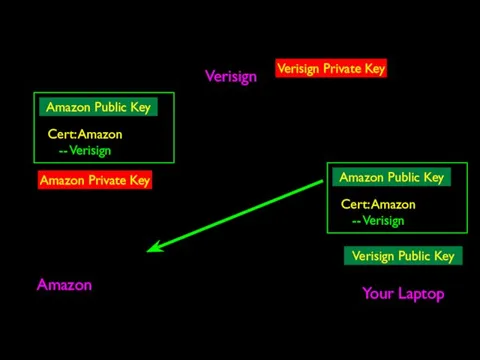
- 66. Verisign Amazon Your Laptop Verisign Public Key Verisign Private Key How Amazon gets a public key
- 67. Verisign Amazon Your Laptop Verisign Public Key Verisign Private Key Amazon Private Key Cert: Amazon --
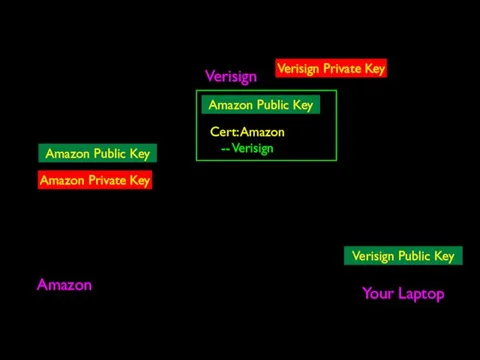
- 68. Verisign Amazon Your Laptop Verisign Public Key Verisign Private Key Amazon Private Key Amazon Public Key
- 69. Verisign Amazon Your Laptop Verisign Public Key Verisign Private Key Amazon Private Key Amazon Public Key
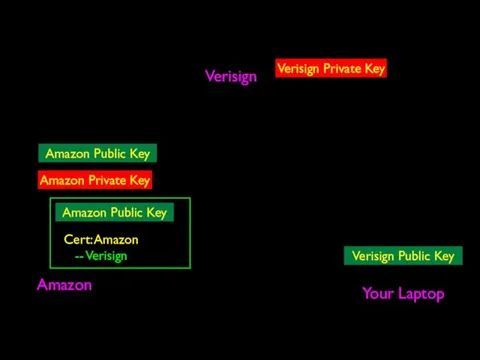
- 70. Verisign Amazon Your Laptop Verisign Public Key Verisign Private Key Amazon Private Key Amazon Public Key
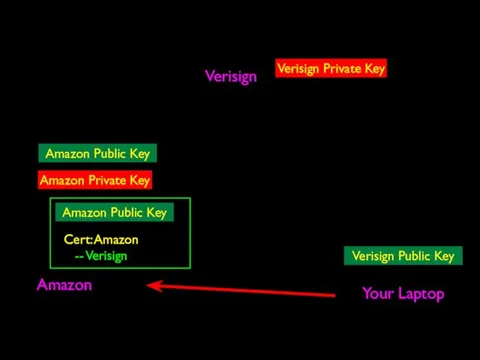
- 71. Verisign Amazon Your Laptop Verisign Public Key Verisign Private Key Amazon Private Key
- 72. Certificate Authority (CA) http://en.wikipedia.org/wiki/Certificate_authority Text A certificate authority is an entity that issues digital certificatesA certificate
- 73. v
- 74. Summary Message Confidentiality / Message Integrity Encrypting / Decrypting Message digests and message signing Shared Secret
- 76. Скачать презентацию







































 Электронный учебник: кому и зачем он нужен?
Электронный учебник: кому и зачем он нужен? Основы программирования
Основы программирования Азы программирования на языке LabView. Первая модель робота LegoWeDo
Азы программирования на языке LabView. Первая модель робота LegoWeDo DS Программирование Python. Генерация списков и словарей
DS Программирование Python. Генерация списков и словарей Дорожная карта. Твой план дальнейших действий
Дорожная карта. Твой план дальнейших действий Основы социальной информатики. Информационная безопасность
Основы социальной информатики. Информационная безопасность Технологии хранения информации и больших объемов данных. Лекция 1
Технологии хранения информации и больших объемов данных. Лекция 1 Понятие системы, как семантической модели. Структура системного анализа
Понятие системы, как семантической модели. Структура системного анализа Табличное решение логических задач
Табличное решение логических задач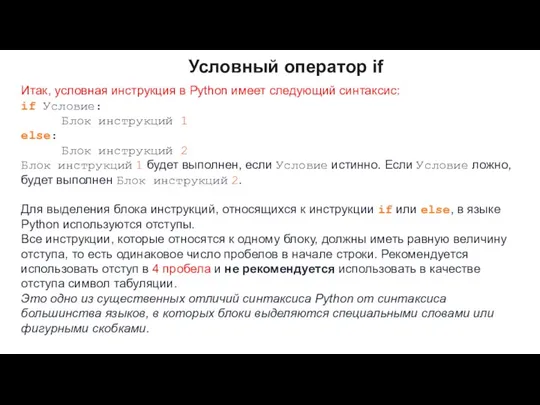 Условный оператор if
Условный оператор if Офисные пакеты
Офисные пакеты Використання багаторядкових текстових полів (урок 34)
Використання багаторядкових текстових полів (урок 34) Электронный листок нетрудоспособности
Электронный листок нетрудоспособности Профессия Менеджер по контекстной рекламе
Профессия Менеджер по контекстной рекламе Макет и требования к ИС по обеспечению закупочной деятельности
Макет и требования к ИС по обеспечению закупочной деятельности Отношения между понятиями
Отношения между понятиями Анализ алгоритмов. Лекция 2
Анализ алгоритмов. Лекция 2 Modelling and Simulation IS 331. Lec (3)
Modelling and Simulation IS 331. Lec (3) Фоторедактирование как профессиональная деятельность
Фоторедактирование как профессиональная деятельность Компьютерные вирусы
Компьютерные вирусы Базы данных. SQL
Базы данных. SQL Ақпаратты қорғау негіздері
Ақпаратты қорғау негіздері Advertising Media
Advertising Media Систематический подход к защите персональных данных в организации
Систематический подход к защите персональных данных в организации Адресация и маршрутизация в IP-сетях
Адресация и маршрутизация в IP-сетях Язык программирования общего назначения Python
Язык программирования общего назначения Python Программирование. Оператор Mod в Visual Basic
Программирование. Оператор Mod в Visual Basic Сортировщик банкнот DoCash DC-45 F
Сортировщик банкнот DoCash DC-45 F