Содержание
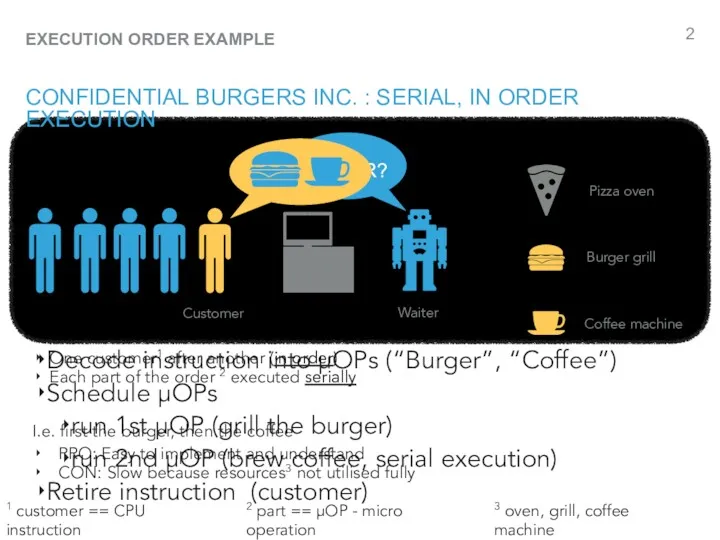
- 2. DONE ORDER? CONFIDENTIAL BURGERS INC. : SERIAL, IN ORDER EXECUTION Customer Waiter Pizza oven Burger grill
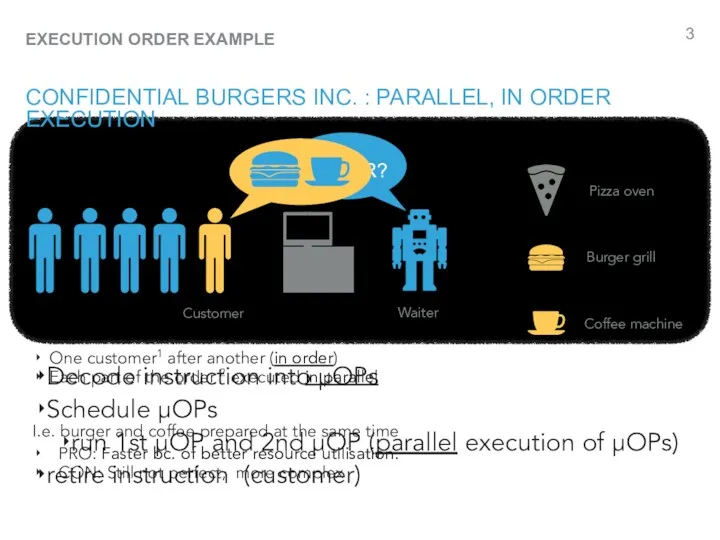
- 3. DONE ORDER? CONFIDENTIAL BURGERS INC. : PARALLEL, IN ORDER EXECUTION Customer Waiter Pizza oven Burger grill
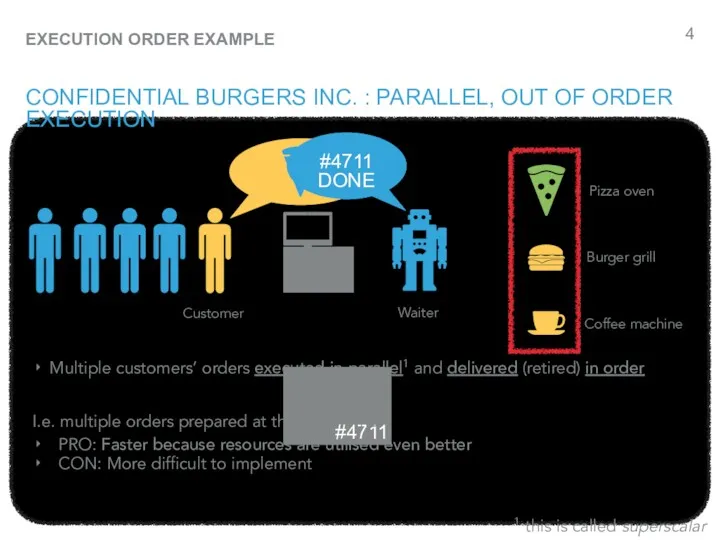
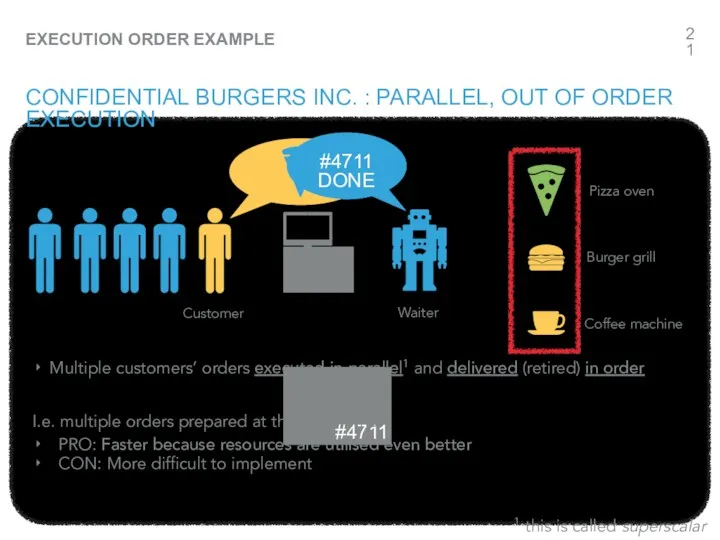
- 4. #4711 ORDER? YOUR ORDER ID: #4711 CONFIDENTIAL BURGERS INC. : PARALLEL, OUT OF ORDER EXECUTION Customer
- 5. CONFIDENTIAL BURGERS INC. Instruction CPU core Adding more resources increase parallelism & throughput. This is all
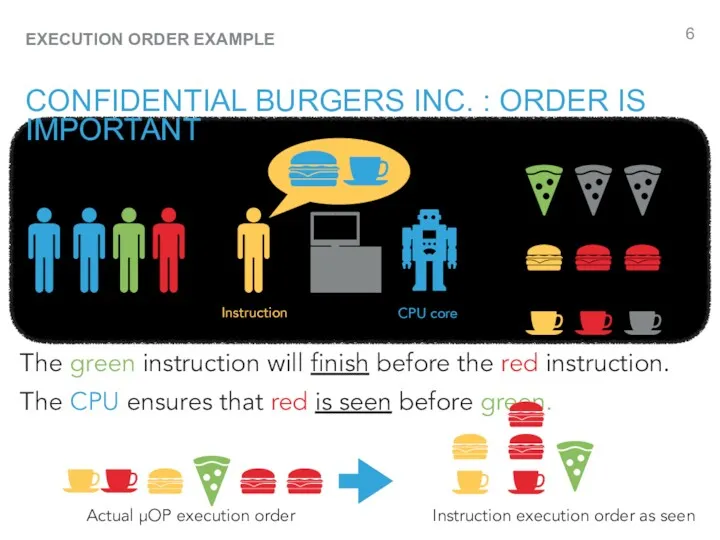
- 6. EXECUTION ORDER EXAMPLE CONFIDENTIAL BURGERS INC. : ORDER IS IMPORTANT The green instruction will finish before
- 7. MELTDOWN OUT OF ORDER EXECUTION
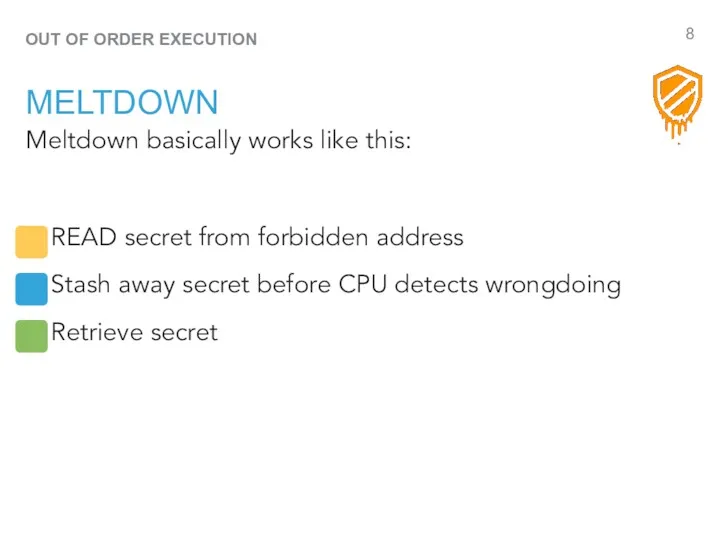
- 8. Meltdown basically works like this: READ secret from forbidden address Stash away secret before CPU detects
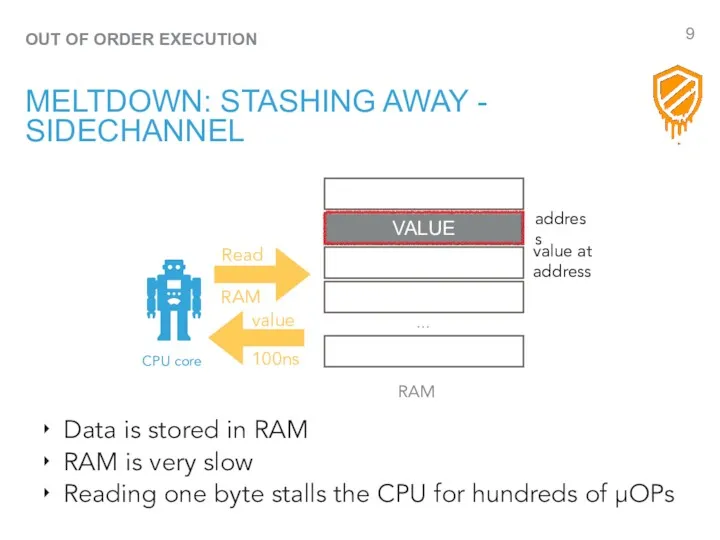
- 9. OUT OF ORDER EXECUTION MELTDOWN: STASHING AWAY - SIDECHANNEL … CPU core RAM Data is stored
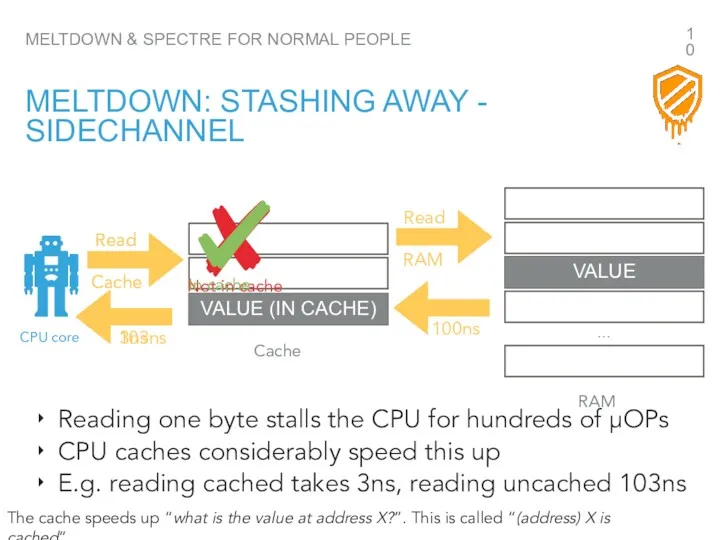
- 10. MELTDOWN & SPECTRE FOR NORMAL PEOPLE MELTDOWN: STASHING AWAY - SIDECHANNEL … CPU core VALUE VALUE
- 11. For a CPU the “READ value from memory at 4711” instruction looks like this (µOPs): Check
- 12. Meltdown basically works like this: READ secret from forbidden address Check that program may read from
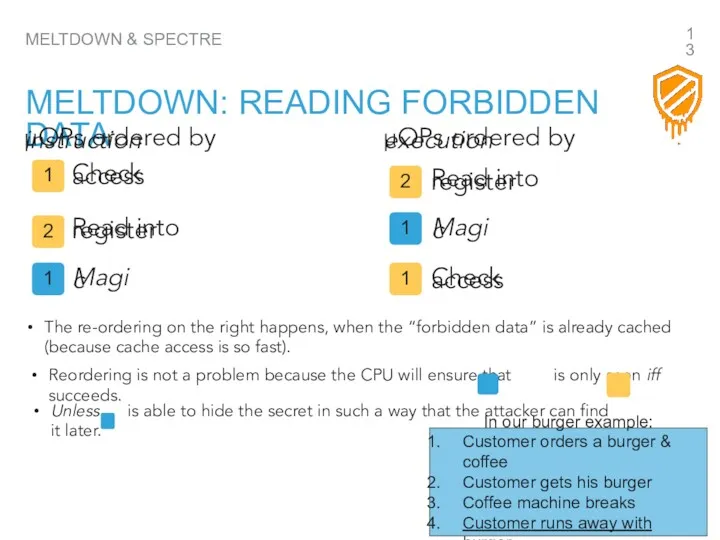
- 13. MELTDOWN & SPECTRE MELTDOWN: READING FORBIDDEN DATA µOPs ordered by instruction µOPs ordered by execution The
- 14. MELTDOWN & SPECTRE MELTDOWN For Meltdown two actors are needed The spy and a collector. The
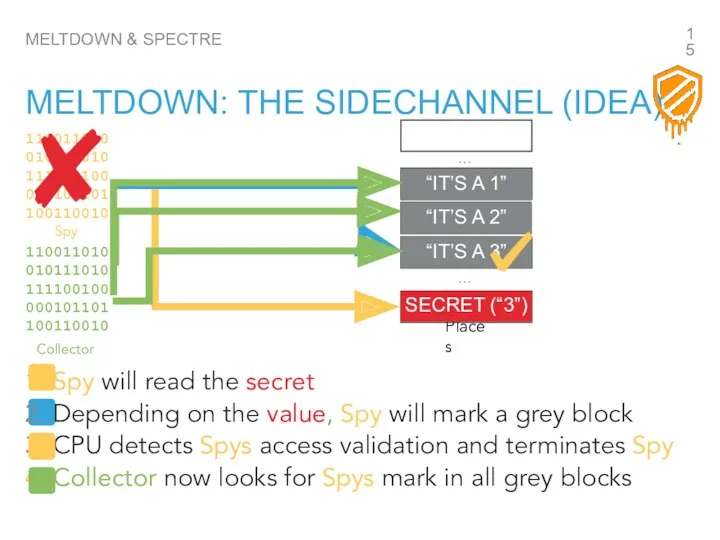
- 15. “IT’S A 1” MELTDOWN & SPECTRE MELTDOWN: THE SIDECHANNEL (IDEA) Spy will read the secret Depending
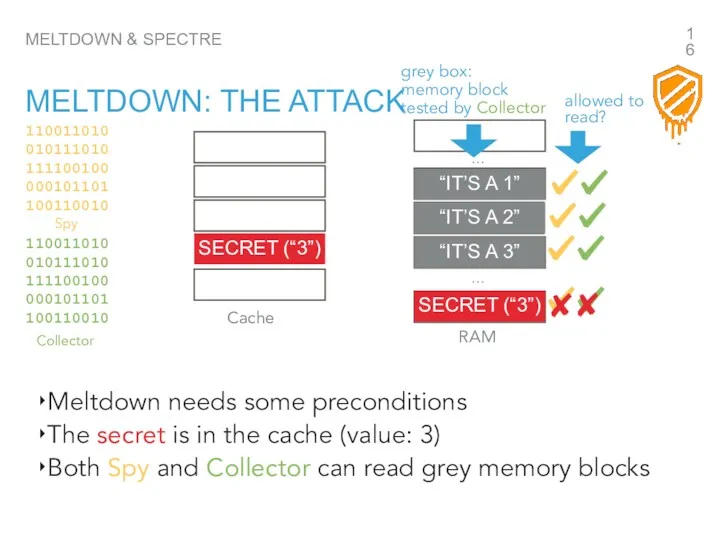
- 16. MELTDOWN & SPECTRE MELTDOWN: THE ATTACK … Meltdown needs some preconditions The secret is in the
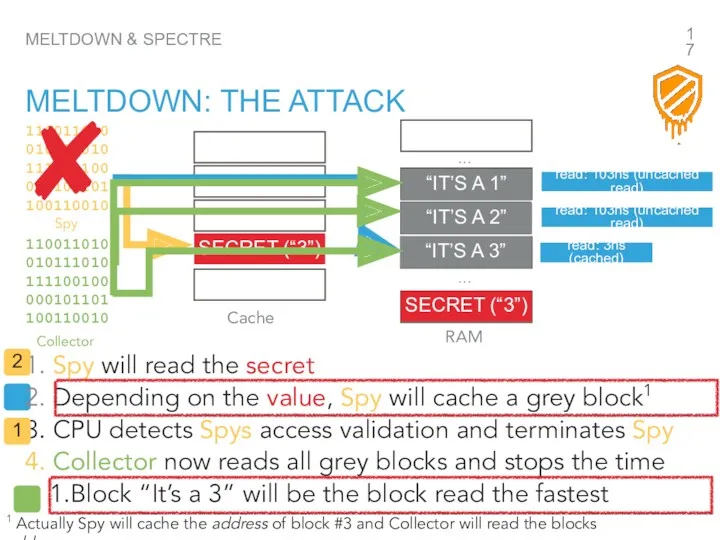
- 17. “IT’S A 1” MELTDOWN & SPECTRE MELTDOWN: THE ATTACK Spy will read the secret Depending on
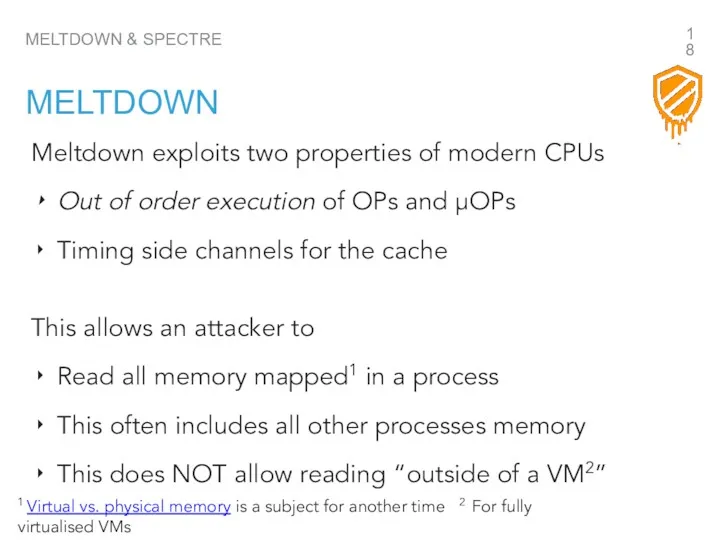
- 18. Meltdown exploits two properties of modern CPUs Out of order execution of OPs and µOPs Timing
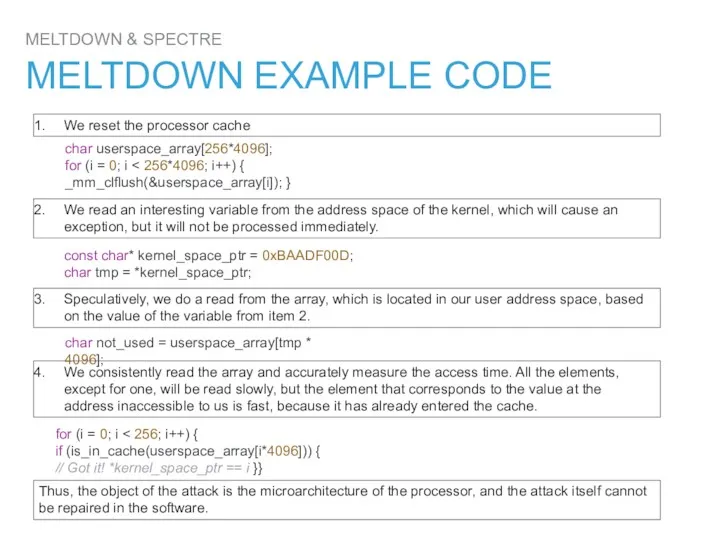
- 19. MELTDOWN & SPECTRE MELTDOWN EXAMPLE CODE We reset the processor cache We read an interesting variable
- 20. SPECTRE SPECULATIVE EXECUTION
- 21. #4711 ORDER? YOUR ORDER ID: #4711 CONFIDENTIAL BURGERS INC. : PARALLEL, OUT OF ORDER EXECUTION Customer
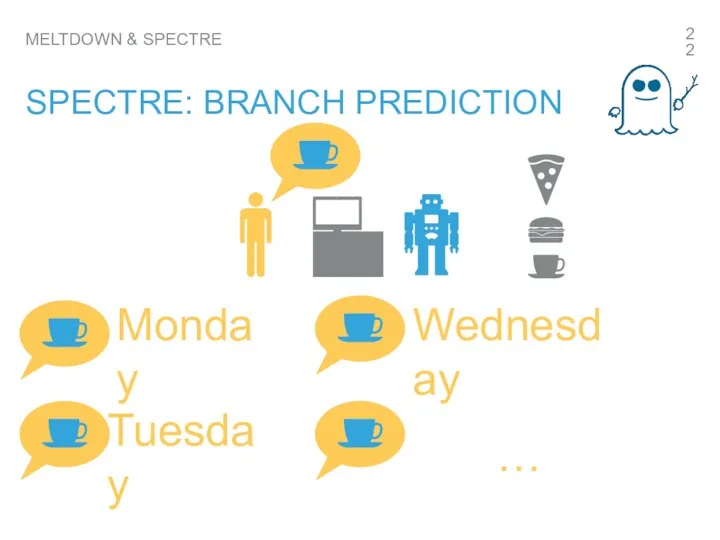
- 22. MELTDOWN & SPECTRE SPECTRE: BRANCH PREDICTION
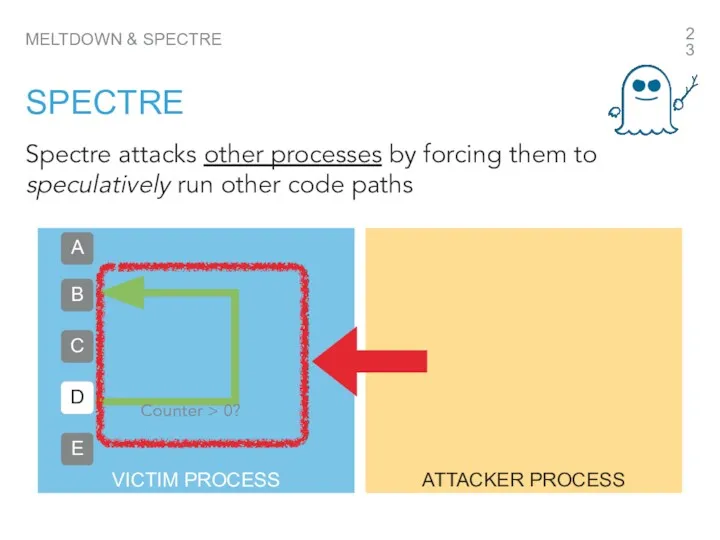
- 23. Spectre attacks other processes by forcing them to speculatively run other code paths MELTDOWN & SPECTRE
- 24. Spectre works like this: force victim to leak secret stash away secret retrieve secret MELTDOWN &
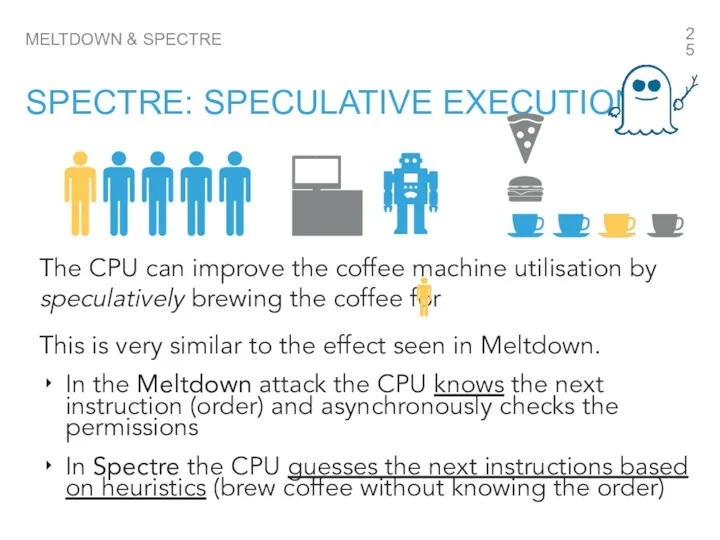
- 25. MELTDOWN & SPECTRE SPECTRE: SPECULATIVE EXECUTION This is very similar to the effect seen in Meltdown.
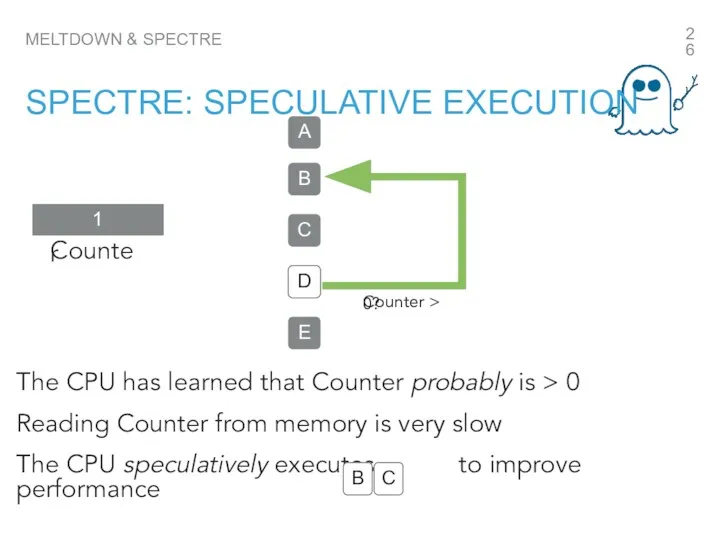
- 26. MELTDOWN & SPECTRE SPECTRE: SPECULATIVE EXECUTION A B C D E D The CPU has learned
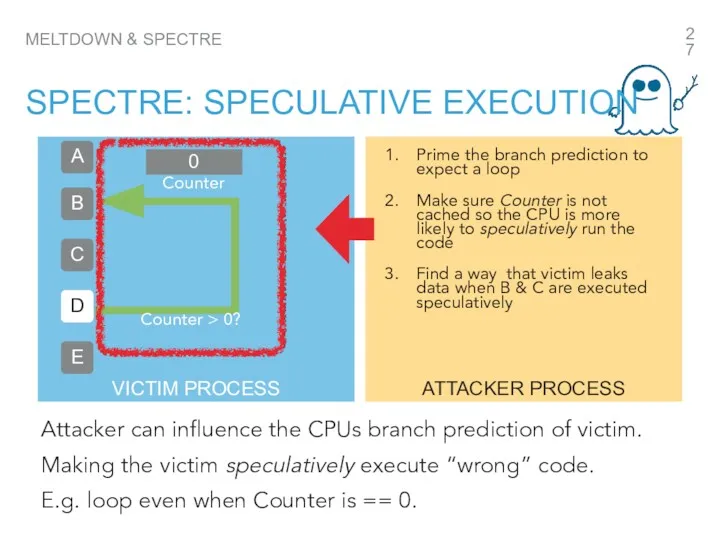
- 27. VICTIM PROCESS MELTDOWN & SPECTRE SPECTRE: SPECULATIVE EXECUTION A B C D E D Attacker can
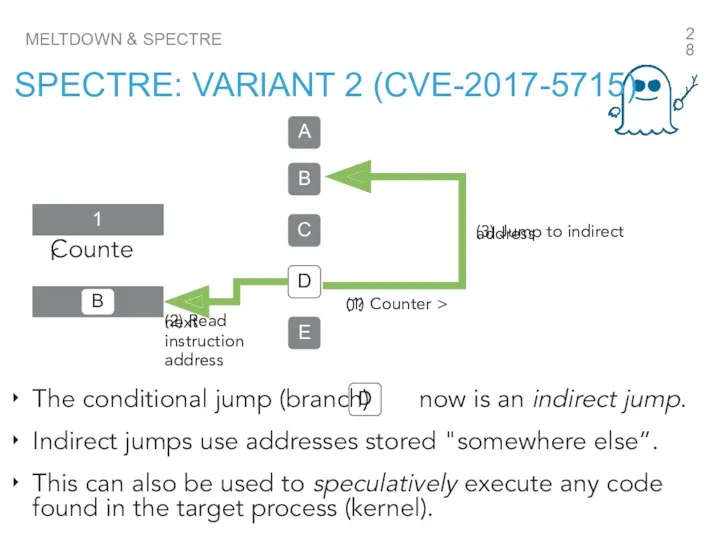
- 28. MELTDOWN & SPECTRE SPECTRE: VARIANT 2 (CVE-2017-5715) A B C D E D The conditional jump
- 30. Скачать презентацию







 Складская логистика. (Раздел 2.2)
Складская логистика. (Раздел 2.2) Менеджер по оценке и аттестации персонала
Менеджер по оценке и аттестации персонала Операционное управление и организация строительства
Операционное управление и организация строительства Мотивация персонала
Мотивация персонала Управление качеством проекта
Управление качеством проекта Программа обучения менеджеров
Программа обучения менеджеров Корпоративные стратегии
Корпоративные стратегии Диаграмма Исикавы и Парето
Диаграмма Исикавы и Парето Производственный менеджмент
Производственный менеджмент Комплектация тележки горничной
Комплектация тележки горничной Таможенный менеджмент
Таможенный менеджмент Модель менеджмента в Германии
Модель менеджмента в Германии Организация и проведение контроля качества оборонной продукции на этапах жизненного цикла в организациях, участвующих в ГОЗ
Организация и проведение контроля качества оборонной продукции на этапах жизненного цикла в организациях, участвующих в ГОЗ Стандарти оперативного управління виробництвом MRP. Система планування виробничих ресурсів MAP
Стандарти оперативного управління виробництвом MRP. Система планування виробничих ресурсів MAP Қызметкерлерді таңдау және іріктеу үдерісі
Қызметкерлерді таңдау және іріктеу үдерісі Инновационная программа менеджера
Инновационная программа менеджера Проект для Души. Тренинг
Проект для Души. Тренинг HRАрхитектор
HRАрхитектор Управление рисками. Статистические показатели. Вариация
Управление рисками. Статистические показатели. Вариация Организация складского хозяйства предприятия
Организация складского хозяйства предприятия Разработка концепции исследования систем управления
Разработка концепции исследования систем управления Кеңсе меңгерушісі
Кеңсе меңгерушісі Социальные группы в организации и управление групповым поведением. (Тема 5)
Социальные группы в организации и управление групповым поведением. (Тема 5) Выбор альтернатив УР в условиях неопределенности и риска
Выбор альтернатив УР в условиях неопределенности и риска Операционная система предприятия
Операционная система предприятия Системный подход к управлению
Системный подход к управлению Теории управления персоналом
Теории управления персоналом Разработка проекта по снижению текучести персонала
Разработка проекта по снижению текучести персонала