- Главная
- Менеджмент
- Internal control and deontology - Chapter 7 IT auditing

Содержание
- 2. 1. Risks and opportunities Risks: (-) less oral communication and personal contacts ? errors, misunderstandings, …
- 3. 2. I/C in an IT environment Specific internal control aspects: Responsabilities: Who is responsible for the
- 4. Security: Physical security: fire, floods, inappropriate access, …. Technical security: use of passwords, pincodes, etc. What
- 6. Скачать презентацию
Слайд 2
1. Risks and opportunities
Risks:
(-) less oral communication and personal contacts ?
1. Risks and opportunities
Risks:
(-) less oral communication and personal contacts ?
errors, misunderstandings, … could arise and exist longer
(-) fewer formal registrations
(-) small programming errors are repeated frequently thus resulting in large errors
Opportunities
(+) time savings and more efficiency
(+) basic controls and checks can be programmed
(+) LOG files
(+) faster, better (more efficient) management reporting is possible (dashboards, mgt cockpits, etc)
Attention!:
Don’t forget: reliability of output depends on input (“garbage in = garbage out”)
Seggregation of duties is crucial
(-) fewer formal registrations
(-) small programming errors are repeated frequently thus resulting in large errors
Opportunities
(+) time savings and more efficiency
(+) basic controls and checks can be programmed
(+) LOG files
(+) faster, better (more efficient) management reporting is possible (dashboards, mgt cockpits, etc)
Attention!:
Don’t forget: reliability of output depends on input (“garbage in = garbage out”)
Seggregation of duties is crucial
Internal control and deontology Chapter 7
Слайд 3
2. I/C in an IT environment
Specific internal control aspects:
Responsabilities:
Who is responsible
2. I/C in an IT environment
Specific internal control aspects:
Responsabilities:
Who is responsible
for the design, development, (testing), implementation and maintenance of the IT systems? ? the IT department
Seggregation of duties is important:
Implementation, testing, apporval of new systems
Creation of user ID’s and passwords
Otherwise: same principles as in a non-automized environment
IT department should never make changes/alter the system without permission (unilateral)
Seggregation of duties is important:
Implementation, testing, apporval of new systems
Creation of user ID’s and passwords
Otherwise: same principles as in a non-automized environment
IT department should never make changes/alter the system without permission (unilateral)
Internal control and deontology Chapter 7
Слайд 4
Security:
Physical security: fire, floods, inappropriate access, ….
Technical security: use
Security:
Physical security: fire, floods, inappropriate access, ….
Technical security: use
of passwords, pincodes, etc.
What is a good password?:
passwords are personal
Frequently changed
complex (special signs)
Kept in a safe place
Automatic logging of (attempted) access to personal data
Security is not a one time effort!
logging and keeping track of access attempts
Privacy policy
Only using legal software versions
Contingency planning– continuïty – reputational damage
What is a good password?:
passwords are personal
Frequently changed
complex (special signs)
Kept in a safe place
Automatic logging of (attempted) access to personal data
Security is not a one time effort!
logging and keeping track of access attempts
Privacy policy
Only using legal software versions
Contingency planning– continuïty – reputational damage
Internal control and deontology Chapter 7
Следующая -
Internal communication audit


 Современные подходы к управлению качеством
Современные подходы к управлению качеством Деловые коммуникации. Личная эффективность как основа коммуникативной компетентности
Деловые коммуникации. Личная эффективность как основа коммуникативной компетентности Понятие менеджмента. Роль менеджера в работе организации
Понятие менеджмента. Роль менеджера в работе организации Командная работа (распределение ролей в группе по Р.М.Белбину)
Командная работа (распределение ролей в группе по Р.М.Белбину) Внешняя среда организации
Внешняя среда организации РТК Центр вечер
РТК Центр вечер Performance Measurement
Performance Measurement Стандарты в области КСО. Руководства, используемые при разработке нефинансовых отчетов
Стандарты в области КСО. Руководства, используемые при разработке нефинансовых отчетов Социология управления
Социология управления Impact-mapping. Исходные предпосылки
Impact-mapping. Исходные предпосылки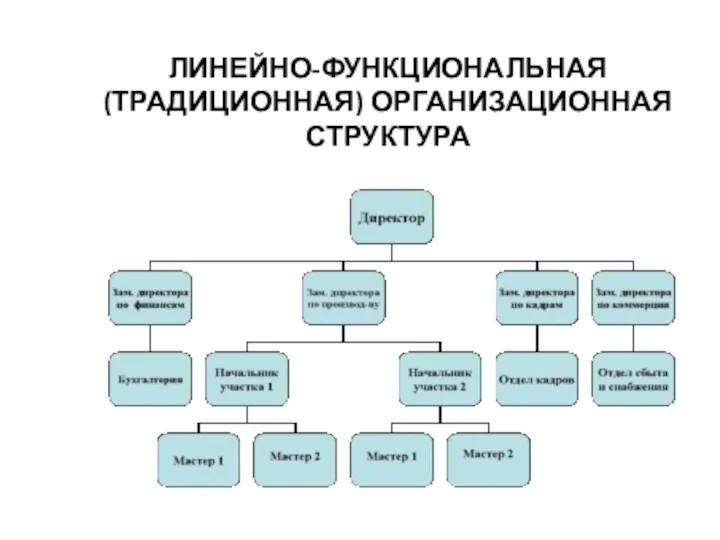 Линейно-функциональная организационная структура
Линейно-функциональная организационная структура Resource Planning
Resource Planning Проектные механизм в реализации мероприятий целевых программ
Проектные механизм в реализации мероприятий целевых программ Ростелеком. Обучение
Ростелеком. Обучение Эмоциональный интеллект и работа в стрессовых ситуациях. Самоорганизация для достижения результатов. Урок 3
Эмоциональный интеллект и работа в стрессовых ситуациях. Самоорганизация для достижения результатов. Урок 3 Стратегический менеджмент
Стратегический менеджмент Защита отчетов по производственной и преддипломной практикам. Специальность 38.00.00 Экономика и управление
Защита отчетов по производственной и преддипломной практикам. Специальность 38.00.00 Экономика и управление Организация производства сложной кулинарной продукции в горячем цехе закусочной на 54 места с разработкой авторского блюда
Организация производства сложной кулинарной продукции в горячем цехе закусочной на 54 места с разработкой авторского блюда Авторитарлық стиль. Шешімді бір адам қабылдайды, ол жарлық, бұйрық түрінде келеді
Авторитарлық стиль. Шешімді бір адам қабылдайды, ол жарлық, бұйрық түрінде келеді Работа системы управление рисками в таможенных органах Республики Узбекистан
Работа системы управление рисками в таможенных органах Республики Узбекистан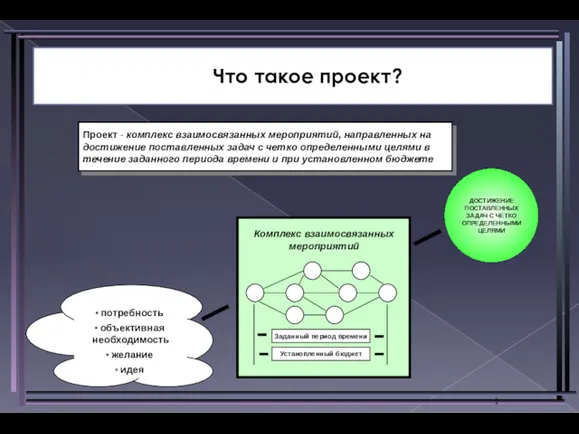 Что такое проект?
Что такое проект? Отбор, наем и адаптация персонала
Отбор, наем и адаптация персонала Транспортная классификация грузов и грузовых перевозок
Транспортная классификация грузов и грузовых перевозок Managers and Managing
Managers and Managing Кадровая политика предприятия: состояние и направления совершенствования (на примере ОАО МАЗ)
Кадровая политика предприятия: состояние и направления совершенствования (на примере ОАО МАЗ) История и методология науки управления
История и методология науки управления История менеджмента. Управленческие революции. Школы научного управления
История менеджмента. Управленческие революции. Школы научного управления Major building systems
Major building systems