Содержание
- 2. 1. 2FA authentification 1.1What is 2FA authentification? 1.2 What are the types of 2FA? 1.3 What
- 3. Two-factor authentication (2FA) is a specific type of multi-factor authentication (MFA) that strengthens access security by
- 4. Why is 2FA Important? Two-factor authentication (2FA) is the foundational element of a zero trust security
- 5. What are the types of 2FA? There are a number of different second factors that can
- 6. What are the types of 2FA? SMS 2FA Simplicity. Ubiquitousness. Speed and access. Phone number requirements
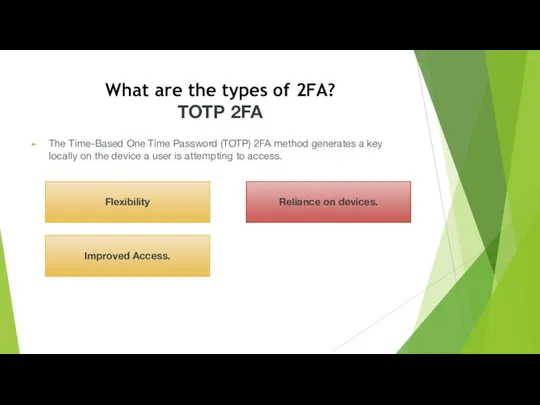
- 7. What are the types of 2FA? TOTP 2FA The Time-Based One Time Password (TOTP) 2FA method
- 8. What are the types of 2FA? Push-Based 2FA Push-based 2FA improves on SMS and TOTP 2FA
- 9. What are the types of 2FA? WebAuthn Convenience. Scalable. More secure. Complex account recovery. Reliance on
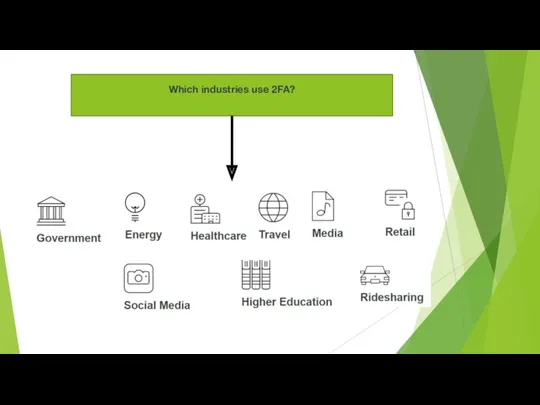
- 10. Which industries use 2FA?
- 11. What are the Factors of Authentication? Knowledge Factor Inherence Factor Time Factor Possession Factor Location Factor
- 12. What Threats Does 2FA Address? Stolen Passwords Social Engineering Key Logging Phishing Attempts Brute-Force Attacks
- 13. 2FA To The Rescue 2FA is an extra layer of security used to make sure that
- 14. Common Types of 2FA Hardware Tokens for 2FA Probably the oldest form of 2FA, hardware tokens
- 15. Common Types of 2FA SMS Text-Message and Voice-based 2FA SMS-based 2FA interacts directly with a user’s
- 16. Common Types of 2FA SMS Text-Message and Voice-based 2FA The most popular form of two-factor authentication
- 17. Common Types of 2FA Push Notification for 2FA Rather than relying on the receipt and entry
- 18. 2. Brute Force Attack Definition A brute force attack is a hacking method that uses trial
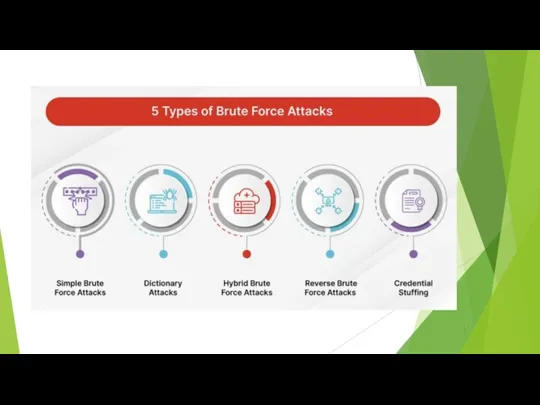
- 19. Types of Brute Force Attacks 1. Simple Brute Force Attacks A simple brute force attack occurs
- 20. Types of Brute Force Attacks 2. Dictionary Attacks A dictionary attack is a basic form of
- 21. Types of Brute Force Attacks 3. Hybrid Brute Force Attacks A hybrid brute force attack is
- 22. Types of Brute Force Attacks 4. Reverse Brute Force Attacks A reverse brute force attack sees
- 23. Types of Brute Force Attacks 5. Credential Stuffing Credential stuffing preys on users’ weak password etiquettes.
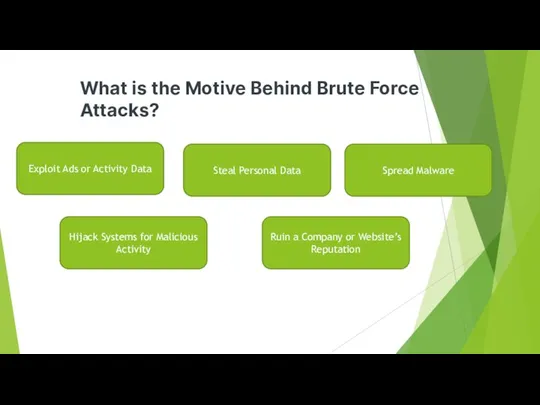
- 25. What is the Motive Behind Brute Force Attacks? Exploit Ads or Activity Data Steal Personal Data
- 26. What is the Motive Behind Brute Force Attacks? Exploit Ads or Activity Data A hacker may
- 27. What is the Motive Behind Brute Force Attacks? Steal Personal Data Hacking into a user’s personal
- 28. What is the Motive Behind Brute Force Attacks? Spread Malware Brute force attacks are often not
- 29. What is the Motive Behind Brute Force Attacks? Hijack Systems for Malicious Activity Brute force attacks
- 30. What is the Motive Behind Brute Force Attacks? Ruin a Company or Website’s Reputation Brute force
- 31. Brute Force Attack Tools Brute force attack tools include password-cracking applications, which crack username and password
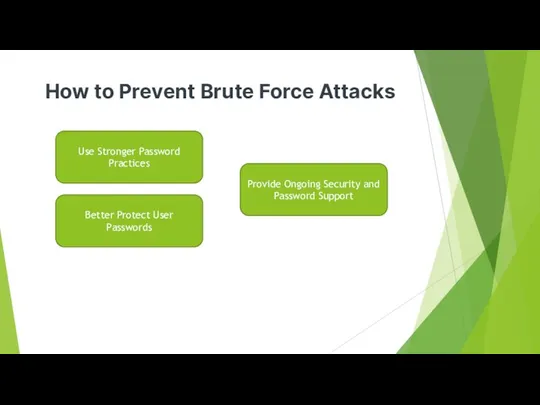
- 32. How to Prevent Brute Force Attacks Use Stronger Password Practices Better Protect User Passwords Provide Ongoing
- 34. Скачать презентацию

























 Разработка рекомендаций по оценке безопасности информационных систем
Разработка рекомендаций по оценке безопасности информационных систем Принципы работы в сети. Исключения
Принципы работы в сети. Исключения Частотные методы улучшения изображений. Лекция 3
Частотные методы улучшения изображений. Лекция 3 Программы Microsoft Office: PowerPoint 2010, Word 2010
Программы Microsoft Office: PowerPoint 2010, Word 2010 Стандартизация сетей. Модель OSI
Стандартизация сетей. Модель OSI Пример слайда. Sydney Opera House is Australia’s
Пример слайда. Sydney Opera House is Australia’s История технологий шифрования
История технологий шифрования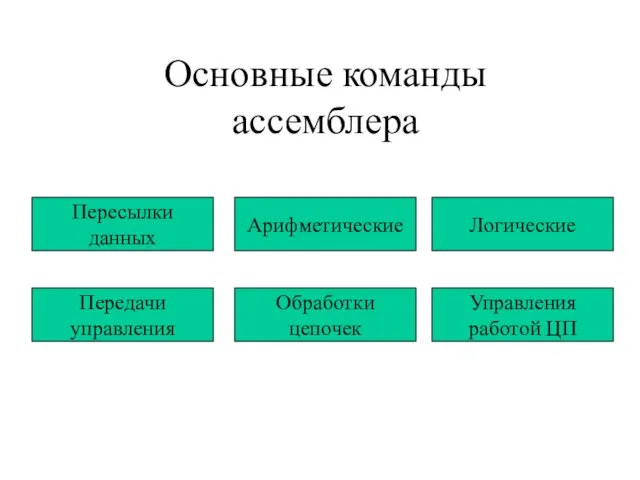 Основные команды ассемблера
Основные команды ассемблера Вкладені цикли. Покрокове введення та виведення даних. Лекція №8
Вкладені цикли. Покрокове введення та виведення даних. Лекція №8 Media & newspapers
Media & newspapers Сборочное моделирование. Решения по управлению жизненным циклом, продукт IBM/Dassault Systemes
Сборочное моделирование. Решения по управлению жизненным циклом, продукт IBM/Dassault Systemes Российское движение школьников. Информационно-медийное направление
Российское движение школьников. Информационно-медийное направление Интернет-коммуникации. Автоматизация
Интернет-коммуникации. Автоматизация Графический метод решения уравнений в Excel
Графический метод решения уравнений в Excel Электронный листок нетрудоспособности на территории Ленинградской области
Электронный листок нетрудоспособности на территории Ленинградской области Построение и анализ алгоритмов. Алгоритмы на графах. МОД в задаче коммивояжёра. (Лекция 6.2)
Построение и анализ алгоритмов. Алгоритмы на графах. МОД в задаче коммивояжёра. (Лекция 6.2) История серии видеоигр: Crysis, Wolfenstein, Dead Space
История серии видеоигр: Crysis, Wolfenstein, Dead Space Блогеры вместо СМИ
Блогеры вместо СМИ Путешествие по сказкам. Блок-схема. 6 класс
Путешествие по сказкам. Блок-схема. 6 класс Массивы. Строки. Пользовательские типы.(Тема 3)
Массивы. Строки. Пользовательские типы.(Тема 3) Интерактивная компьютерная графика
Интерактивная компьютерная графика Кодирование и шифрование данных
Кодирование и шифрование данных Мобильное рабочее место
Мобильное рабочее место Электронные таблицы. Программа MS Excel
Электронные таблицы. Программа MS Excel Візуальна система формування набору об’єктів нерухомості на карті
Візуальна система формування набору об’єктів нерухомості на карті Создание и форматирование таблиц в текстовом редакторе
Создание и форматирование таблиц в текстовом редакторе Текстовые редакторы. Урок 10
Текстовые редакторы. Урок 10 Создание веб-сайтов
Создание веб-сайтов