Содержание
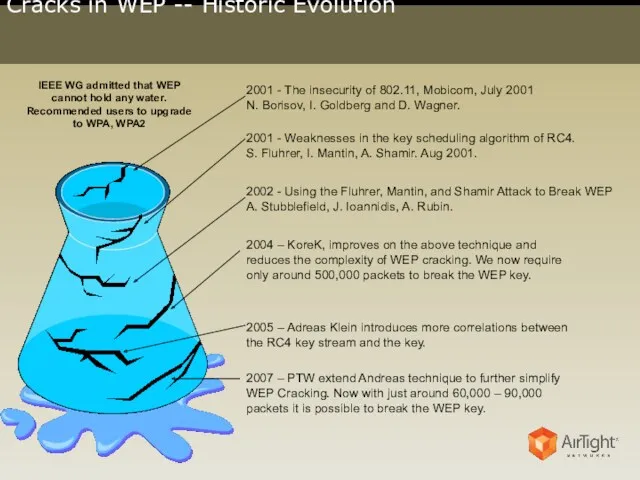
- 2. Cracks in WEP -- Historic Evolution 2001 - The insecurity of 802.11, Mobicom, July 2001 N.
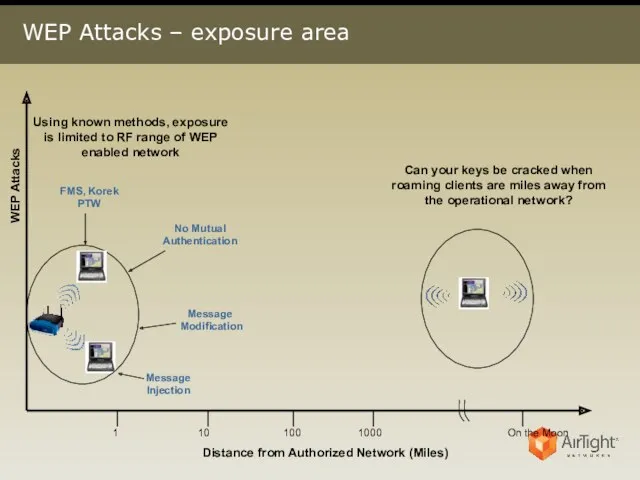
- 3. WEP Attacks – exposure area WEP Attacks Distance from Authorized Network (Miles) 1 10 100 1000
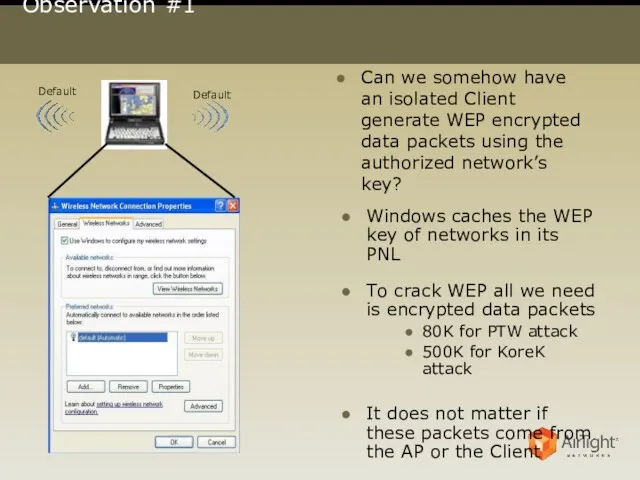
- 4. Observation #1 Can we somehow have an isolated Client generate WEP encrypted data packets using the
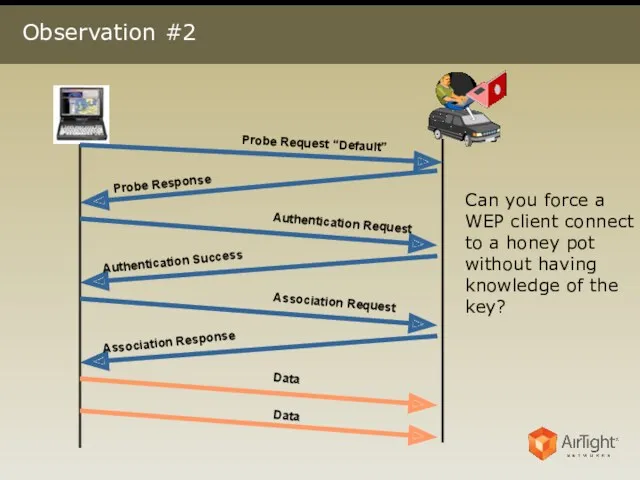
- 5. Observation #2 Can you force a WEP client connect to a honey pot without having knowledge
- 6. Caffé Latte – Attack timelines Every spoofed Association gives us encrypted data packets (either DHCP or
- 7. Can we speed it up? DAYS HOURS MINUTES
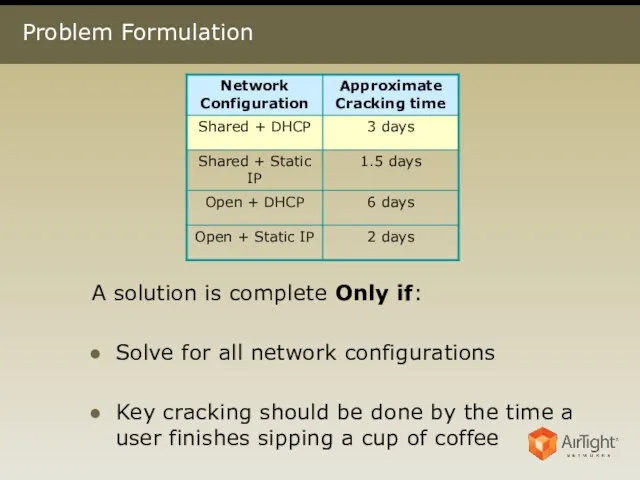
- 8. Problem Formulation A solution is complete Only if: Solve for all network configurations Key cracking should
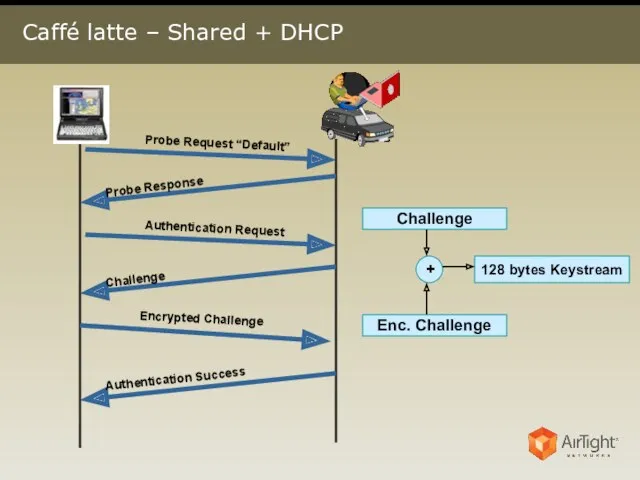
- 9. Caffé latte – Shared + DHCP
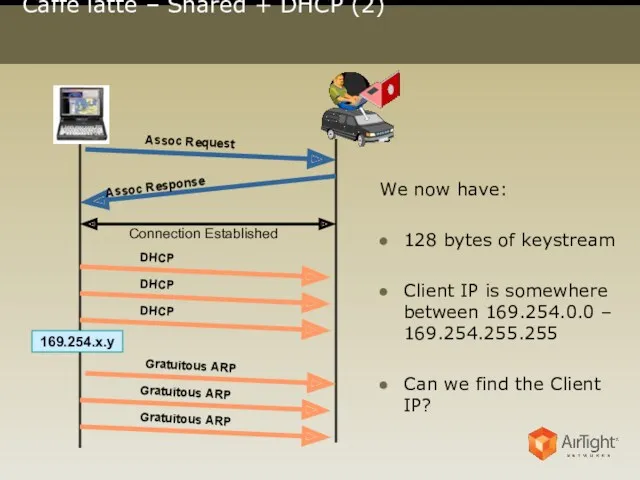
- 10. Caffé latte – Shared + DHCP (2) We now have: 128 bytes of keystream Client IP
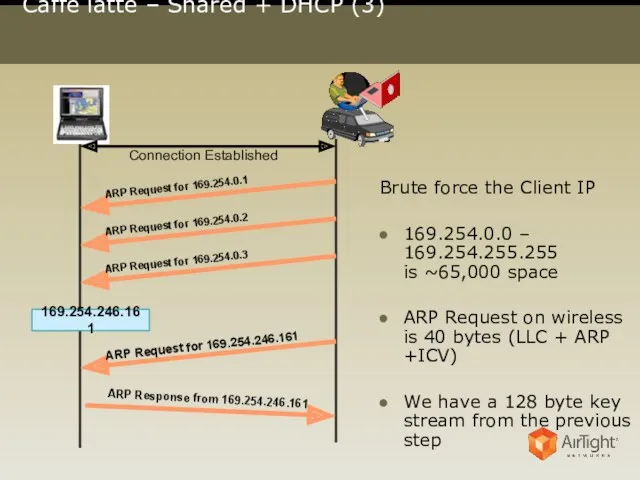
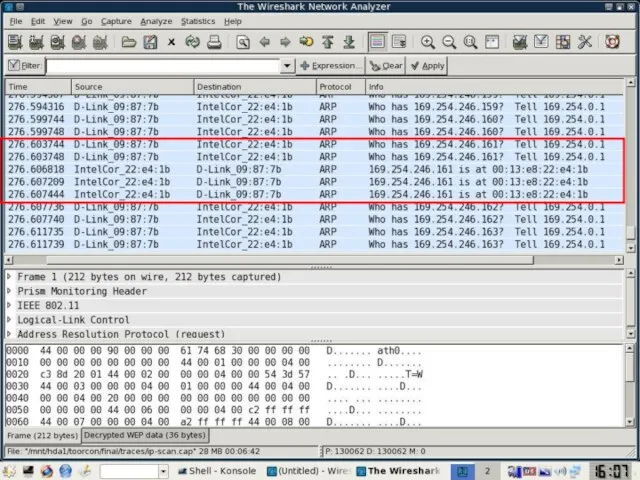
- 11. Caffé latte – Shared + DHCP (3) 169.254.246.161 Connection Established Brute force the Client IP 169.254.0.0
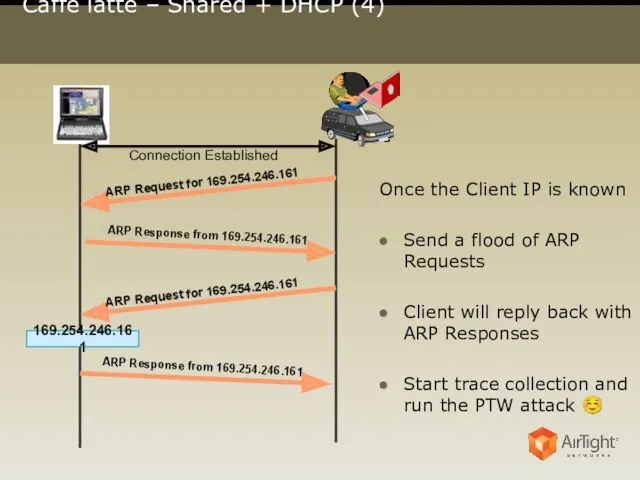
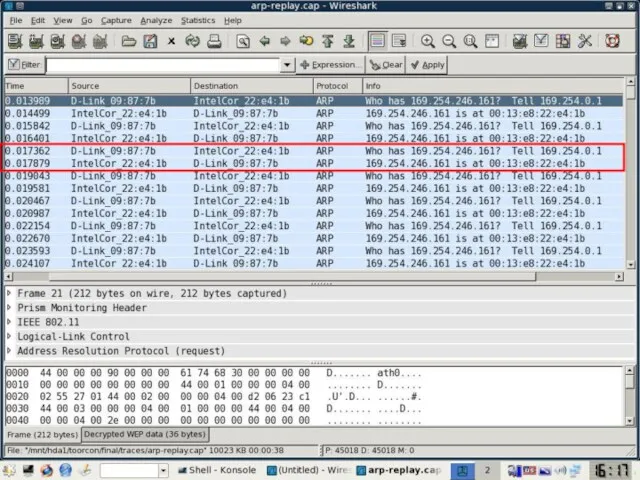
- 13. Caffé latte – Shared + DHCP (4) 169.254.246.161 Connection Established Once the Client IP is known
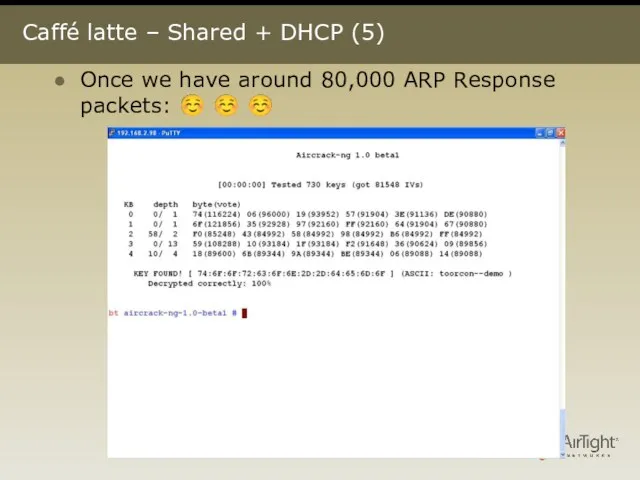
- 15. Caffé latte – Shared + DHCP (5) Once we have around 80,000 ARP Response packets: ☺
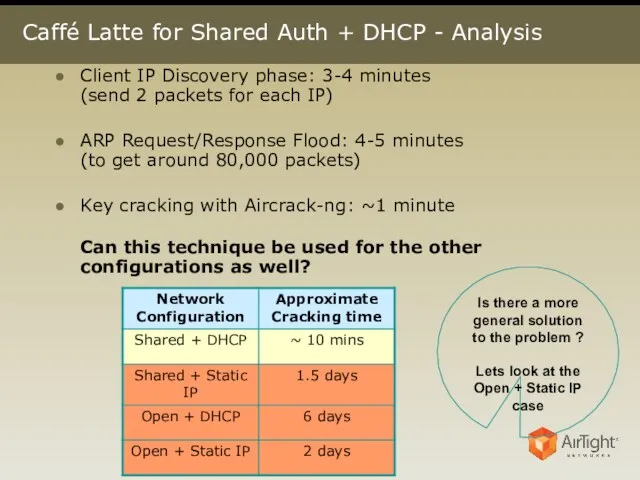
- 16. Caffé Latte for Shared Auth + DHCP - Analysis Client IP Discovery phase: 3-4 minutes (send
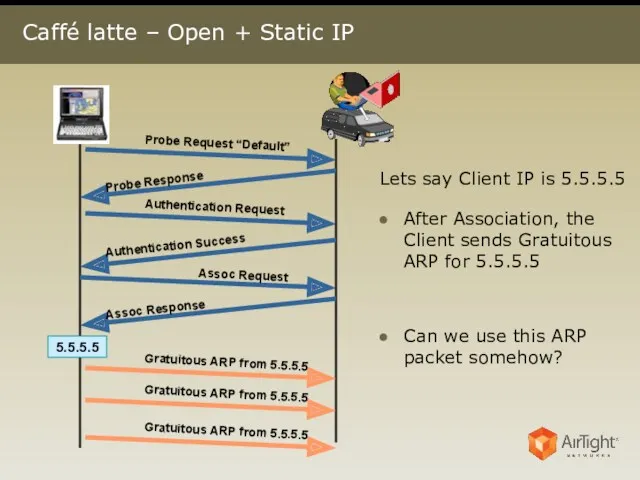
- 17. Caffé latte – Open + Static IP 5.5.5.5 Lets say Client IP is 5.5.5.5 After Association,
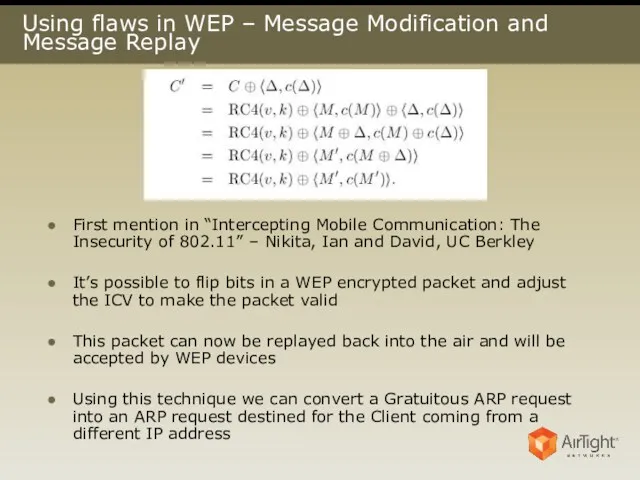
- 18. Using flaws in WEP – Message Modification and Message Replay First mention in “Intercepting Mobile Communication:
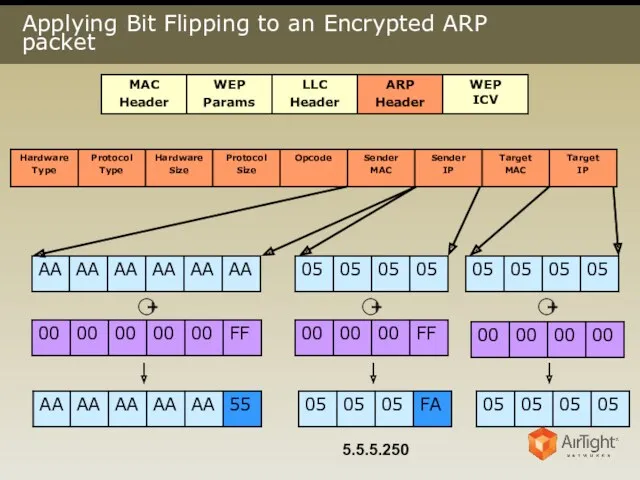
- 19. Applying Bit Flipping to an Encrypted ARP packet + + + 5.5.5.250
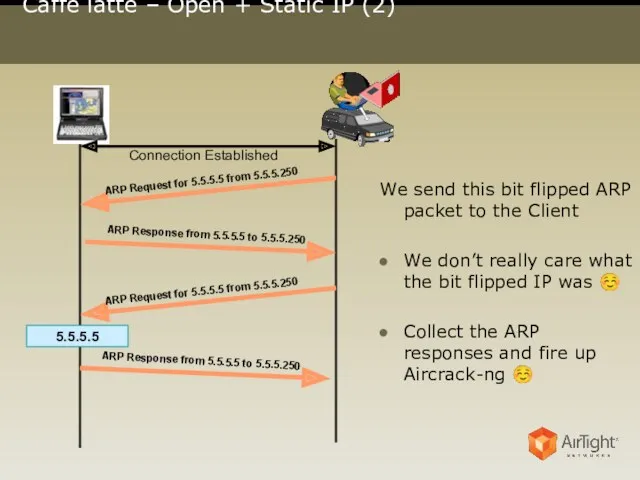
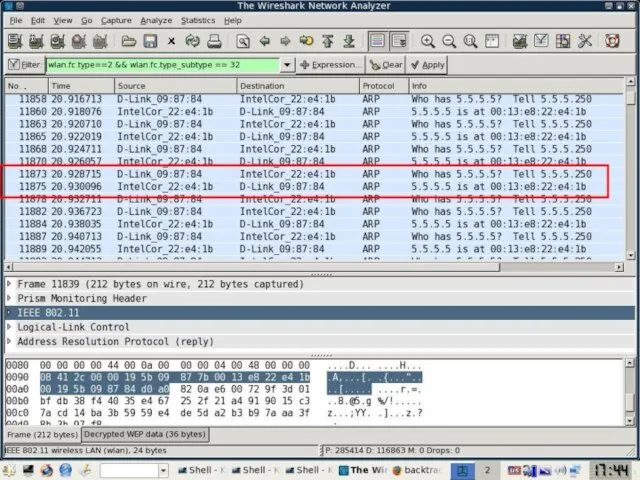
- 20. Caffé latte – Open + Static IP (2) 5.5.5.5 Connection Established We send this bit flipped
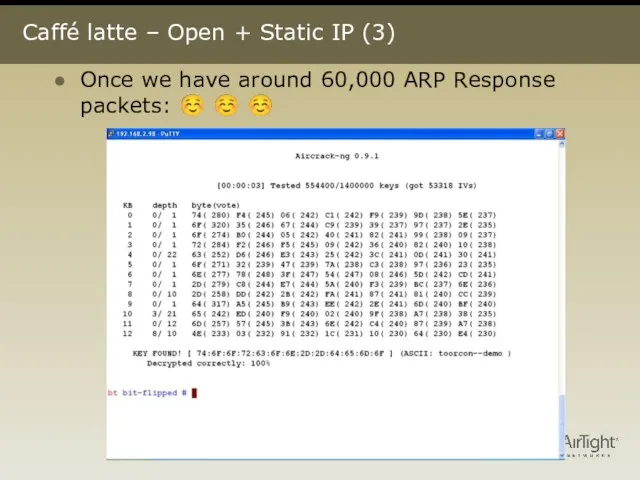
- 22. Caffé latte – Open + Static IP (3) Once we have around 60,000 ARP Response packets:
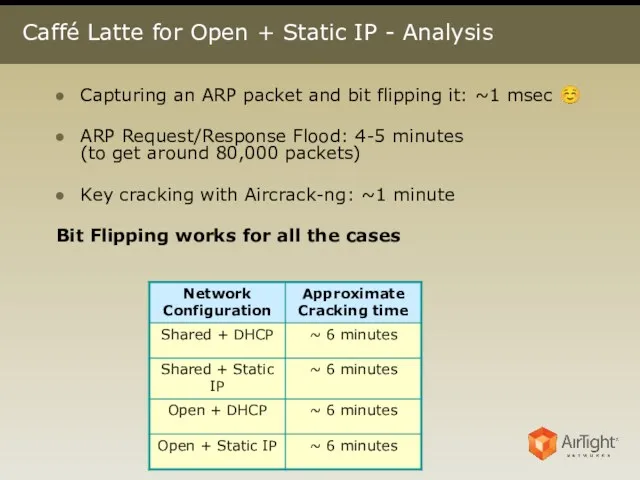
- 23. Caffé Latte for Open + Static IP - Analysis Capturing an ARP packet and bit flipping
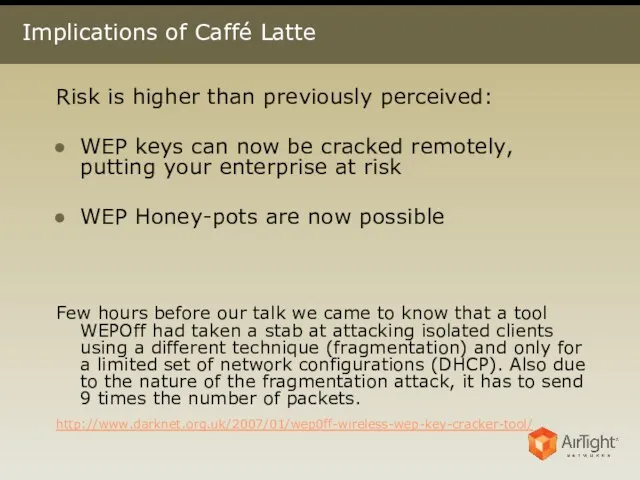
- 24. Implications of Caffé Latte Risk is higher than previously perceived: WEP keys can now be cracked
- 25. Advisory Yet another reason to upgrade to WPA/WPA2 Road warriors need to be careful even more
- 27. Скачать презентацию


 Программное обеспечение компьютера
Программное обеспечение компьютера Основы разработки веб-сайта. Как зарабатывать деньги в интернете
Основы разработки веб-сайта. Как зарабатывать деньги в интернете Кодирование и обработка графической информации
Кодирование и обработка графической информации Технологии послойного прототипирования
Технологии послойного прототипирования Управление показом презентации
Управление показом презентации Установка и деинсталляция программ в ОС Linux
Установка и деинсталляция программ в ОС Linux Исполнители вокруг нас. Разнообразие исполнителей. Формальные исполнители. Автоматизация
Исполнители вокруг нас. Разнообразие исполнителей. Формальные исполнители. Автоматизация Основные операторы языка Си. Условия, циклы. (Лекция 2)
Основные операторы языка Си. Условия, циклы. (Лекция 2) Функциональные возможности Microsoft Office
Функциональные возможности Microsoft Office Кодирование числовой информации
Кодирование числовой информации This work is licensed under a Creative Commons Attribution-ShareAlike 3.0
This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 Аппаратное и программное обеспечение сетей
Аппаратное и программное обеспечение сетей Учебное пособие Векторный редактор Inscape
Учебное пособие Векторный редактор Inscape Изучение понятий: информация, информатизация и информационные технологии, информационные процессы, информационное общество
Изучение понятий: информация, информатизация и информационные технологии, информационные процессы, информационное общество Система електронних платежів в Україні: проблеми та перспективи розвитку
Система електронних платежів в Україні: проблеми та перспективи розвитку Работа в СУБД PostgreSQL. Индексы и оптимизация запросов
Работа в СУБД PostgreSQL. Индексы и оптимизация запросов Перерізи. Поняття про перерізи
Перерізи. Поняття про перерізи Операционные системы. Управление процессами. (Лекция 10)
Операционные системы. Управление процессами. (Лекция 10) Інноватика та інтелектуальна власність
Інноватика та інтелектуальна власність презентация Основы классификации (объектов)
презентация Основы классификации (объектов) Локальные сети. Параметры сетей и их стандарты
Локальные сети. Параметры сетей и их стандарты Home Wi-Fi tweaks
Home Wi-Fi tweaks Предметная область базы данных
Предметная область базы данных Организация глобальных сетей
Организация глобальных сетей Филворд My family по английскому языку, 3 класс
Филворд My family по английскому языку, 3 класс Blender 3D Мастерская Третье измерение ver. 2.0 Наноград, Сочи 2017
Blender 3D Мастерская Третье измерение ver. 2.0 Наноград, Сочи 2017 Логические элементы
Логические элементы HTML тілі және оның негізі
HTML тілі және оның негізі