Слайд 2
Encryption is the process of transforming information so it is unintelligible
to eavesdroppers.
Decryption is the process of transforming encrypted information so that it is intelligible to the intended recipient.
A message to be encrypted is known as plaintext, and the encrypted version is called ciphertext. (A cipher is a secret code.)
In order to encrypt a message in a way that the receiver can decrypt it again, there must be a key, or password, that determines how the encryption is done.
Слайд 3

Слайд 4
Слайд 5
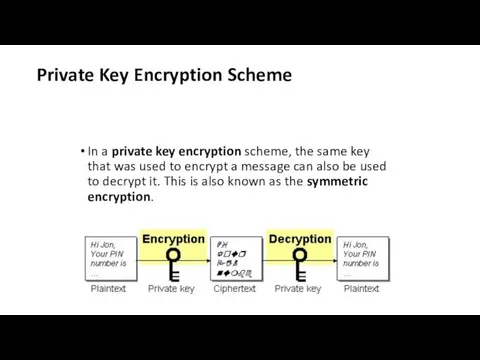
Private Key Encryption Scheme
In a private key encryption scheme, the
same key that was used to encrypt a message can also be used to decrypt it. This is also known as the symmetric encryption.
Слайд 6
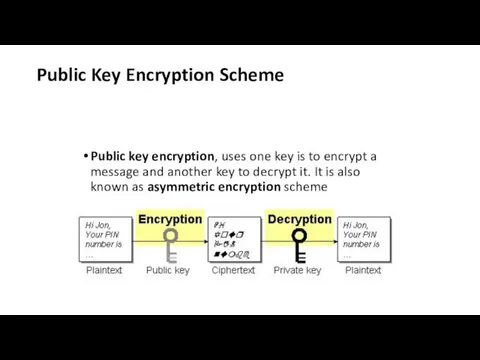
Public Key Encryption Scheme
Public key encryption, uses one key is to
encrypt a message and another key to decrypt it. It is also known as asymmetric encryption scheme
Слайд 7

Cryptography algorithms are mathematical functions used for encryption or decryption. These
mathematical calculations must eliminate any detectable patterns in the ciphertext that could make the code easy to break.
One popular encryption algorithm for use in electronic commerce is DES, which stands for Data Encryption Standard.
Another popular encryption algorithm for computers, especially for Internet applications, is RC4.
Слайд 8

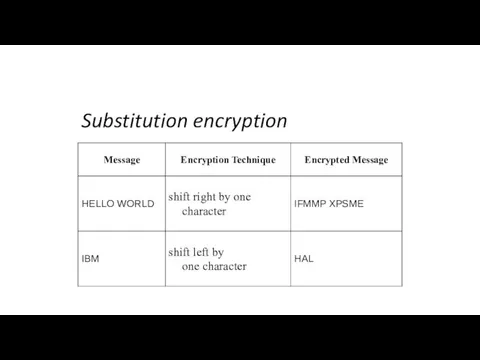
Substitution Cipher
The most basic type of private key encryption is the
substitution cipher. A substitution cipher changes the plaintext to ciphertext by replacing each element of the plaintext with its encrypted substitute. The elements might be individual letters, but they could also be words or phrases.
Probably the simplest of all substitution ciphers is the character-shift cipher, which substitutes letters based on their position in the alphabet.
Слайд 9

Passphrase key encryption
Instead of shifting each character of plaintext by
the same amount, it is used a secret password, or even better, a passphrase, as an encryption key. The letters of the passphrase can be used one at a time to tell us how many characters to shift the corresponding plaintext letter by.
Слайд 10

Vigenère cipher
The Vigenere cipher uses this table together with a keyword
to encipher a message. For example, suppose we wish to encipher the plaintext message:
TO BE OR NOT TO BE THAT IS THE QUESTION
Keyword - RELATIONS.
Слайд 11
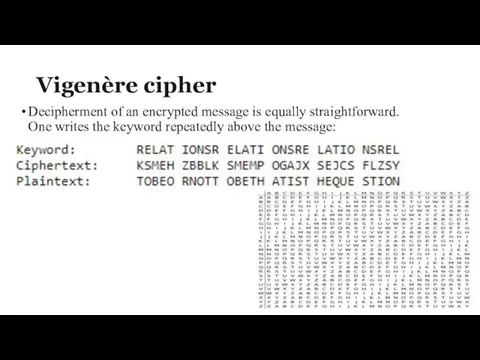
Vigenère cipher
Decipherment of an encrypted message is equally straightforward. One writes
the keyword repeatedly above the message:
Слайд 12

Слайд 13

Ex (right shift of 3)
THE QUICK BROWN FOX JUMPS OVER THE
LAZY DOG












 Законы распределения и их применение для расчетов и анализа
Законы распределения и их применение для расчетов и анализа Мультисервисные сети
Мультисервисные сети Кибербуллинг в социальных сетях
Кибербуллинг в социальных сетях Процессор и системная плата
Процессор и системная плата Оформление документов Microsoft Office Word
Оформление документов Microsoft Office Word Алгоритм работы с презентацией
Алгоритм работы с презентацией Инфокоммуникационная сеть, как большая и сложная система
Инфокоммуникационная сеть, как большая и сложная система 3D принтеры: возможности и перспективы
3D принтеры: возможности и перспективы Презентация Компьютерные вирусы
Презентация Компьютерные вирусы Презентация Логические схемы
Презентация Логические схемы Типи даних мови С#
Типи даних мови С# Решение задач с помощью электронных таблиц. 9 класс
Решение задач с помощью электронных таблиц. 9 класс Использование новых информационных технологий в специальной (коррекционной) школе VIII вида
Использование новых информационных технологий в специальной (коррекционной) школе VIII вида Базы данных в протеомике
Базы данных в протеомике Написание вводной и методической частей статьи либо заявки на получение гранта. (Лекция 5)
Написание вводной и методической частей статьи либо заявки на получение гранта. (Лекция 5) Программирование на языке Паскаль
Программирование на языке Паскаль Помехоустойчивое кодирование. Линейные коды
Помехоустойчивое кодирование. Линейные коды Construction and optimization of algorithms
Construction and optimization of algorithms Информационная система голосового управления персональным компьютером
Информационная система голосового управления персональным компьютером Итоги петровских преобразований. Урок по истории России в 10 класс. Интегрированный урок история + информатика
Итоги петровских преобразований. Урок по истории России в 10 класс. Интегрированный урок история + информатика Арифметические операции в позиционных системах счисления (4). 8 класс
Арифметические операции в позиционных системах счисления (4). 8 класс Memory management. Implementation issues & segmentation
Memory management. Implementation issues & segmentation Бұлттық есептеулер
Бұлттық есептеулер Сжатие, архивация и разархивация данных. Архиваторы. Работа с архивами. Урок 16
Сжатие, архивация и разархивация данных. Архиваторы. Работа с архивами. Урок 16 Информационно-коммуникативные технологии. Загадочный мир символов или слияние внутреннего и внешнего с помощью смайла
Информационно-коммуникативные технологии. Загадочный мир символов или слияние внутреннего и внешнего с помощью смайла Усложнение и методы анализа поточных шифрсистем. АПС 2-2-2. Тема 2
Усложнение и методы анализа поточных шифрсистем. АПС 2-2-2. Тема 2 Программирование на Python. Урок 7. Взаимодействие с игроком Pygame
Программирование на Python. Урок 7. Взаимодействие с игроком Pygame Автоматизация взаимодействия с клиентами (CRM) в филиале компании ЕвроАвтоКар
Автоматизация взаимодействия с клиентами (CRM) в филиале компании ЕвроАвтоКар