Содержание
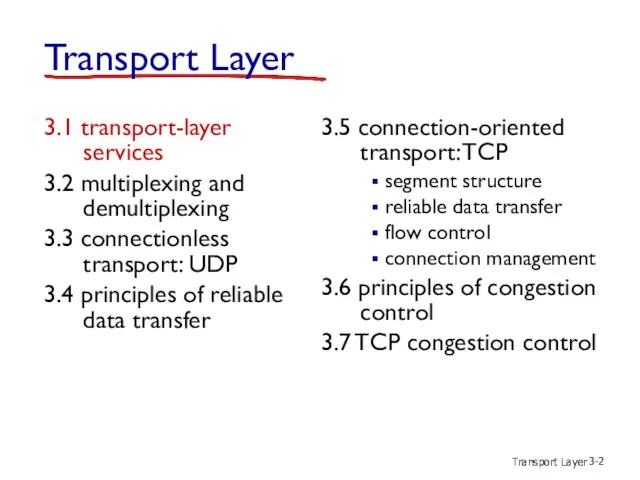
- 2. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
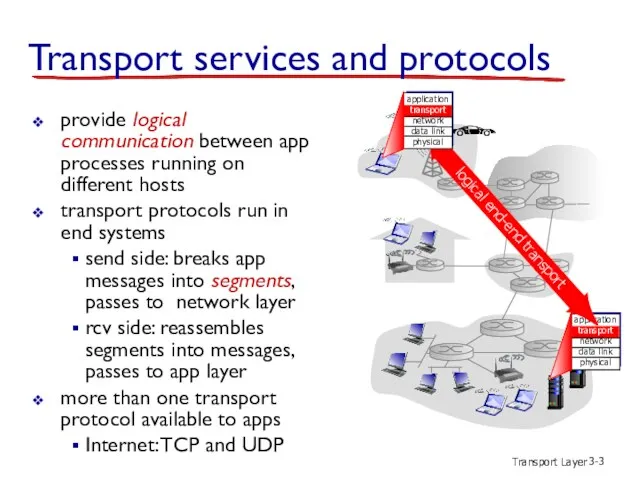
- 3. Transport Layer 3- Transport services and protocols provide logical communication between app processes running on different
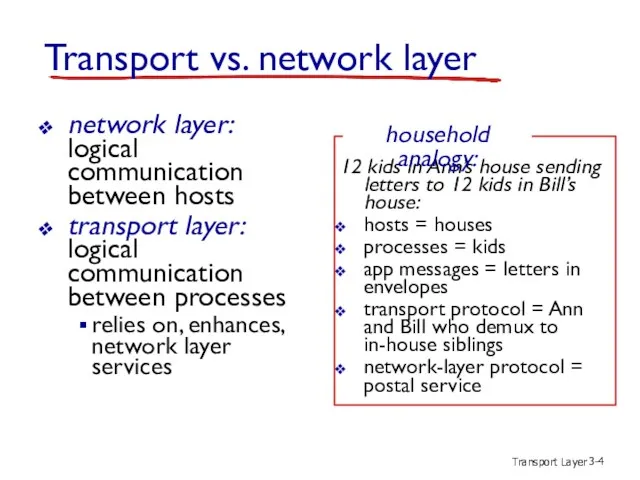
- 4. Transport Layer 3- Transport vs. network layer network layer: logical communication between hosts transport layer: logical
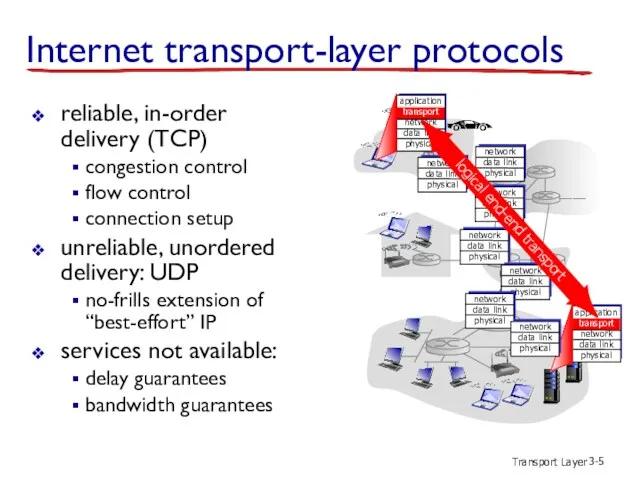
- 5. Transport Layer 3- Internet transport-layer protocols reliable, in-order delivery (TCP) congestion control flow control connection setup
- 6. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
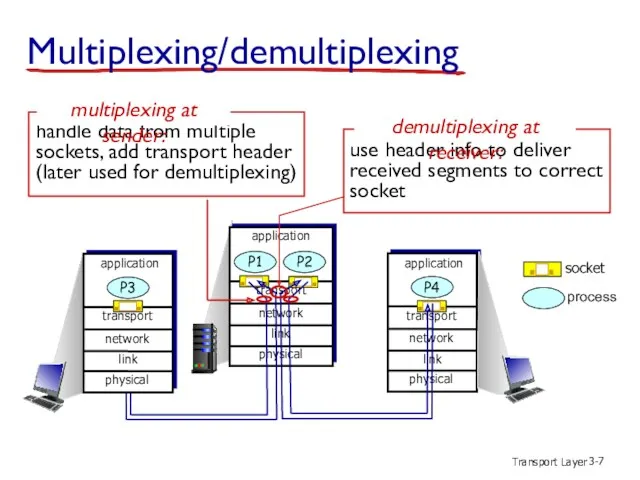
- 7. Transport Layer 3- Multiplexing/demultiplexing process socket transport application physical link network P2 P1 transport application physical
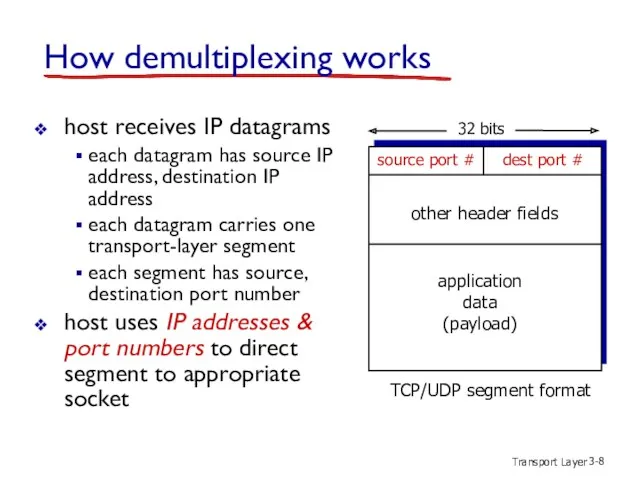
- 8. Transport Layer 3- How demultiplexing works host receives IP datagrams each datagram has source IP address,
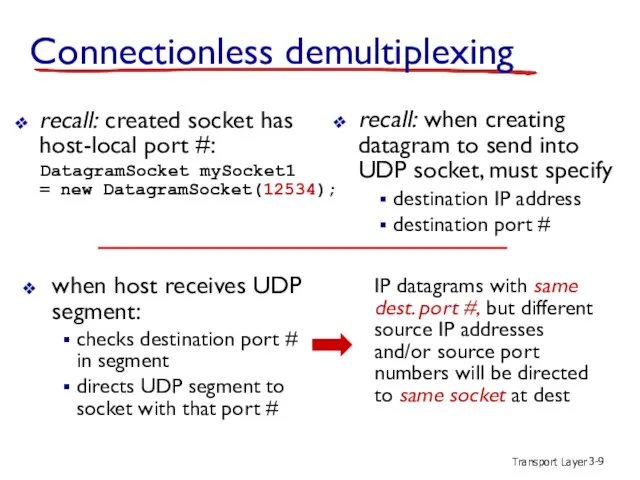
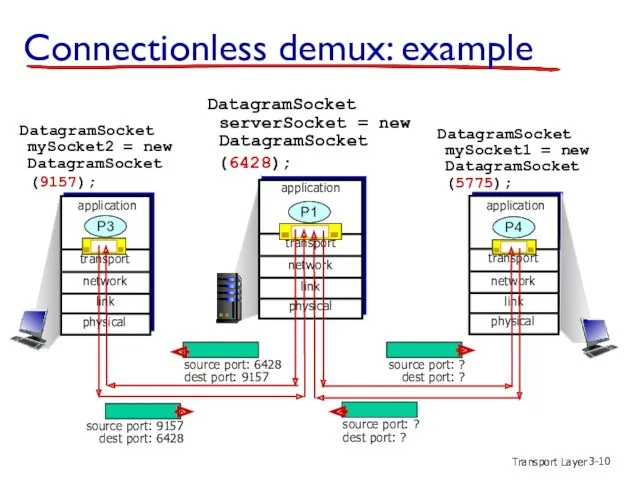
- 9. Transport Layer 3- Connectionless demultiplexing recall: created socket has host-local port #: DatagramSocket mySocket1 = new
- 10. Transport Layer 3- Connectionless demux: example DatagramSocket serverSocket = new DatagramSocket (6428); transport application physical link
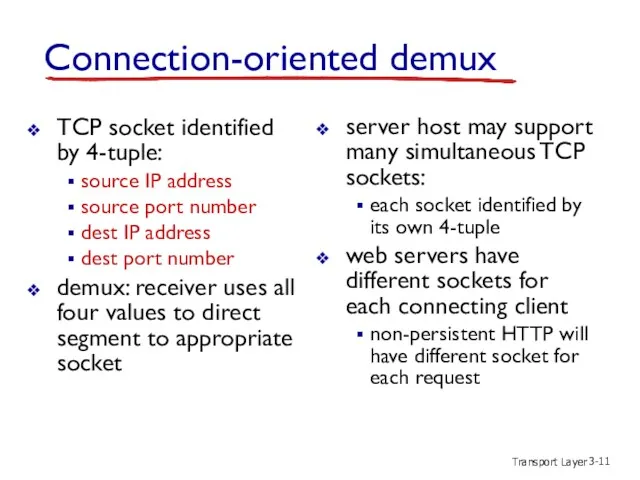
- 11. Transport Layer 3- Connection-oriented demux TCP socket identified by 4-tuple: source IP address source port number
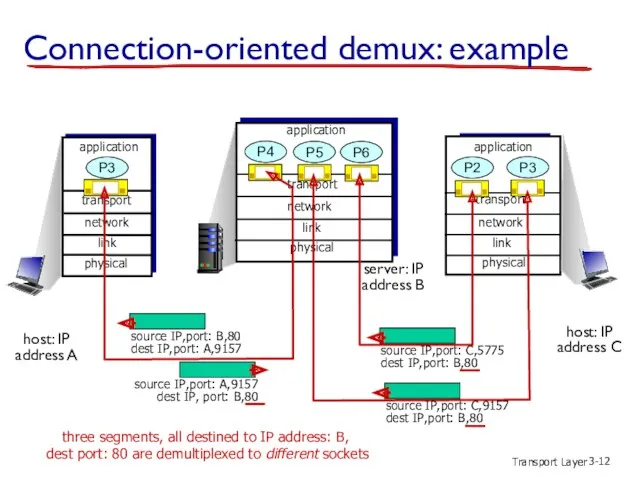
- 12. Transport Layer 3- Connection-oriented demux: example transport application physical link network P3 transport application physical link
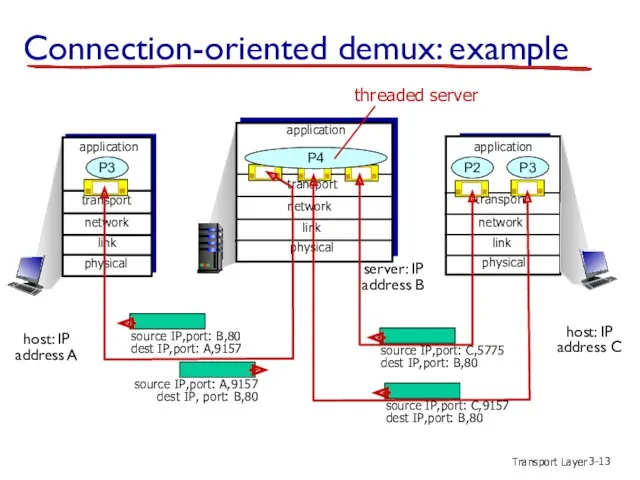
- 13. Transport Layer 3- Connection-oriented demux: example transport application physical link network P3 transport application physical link
- 14. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
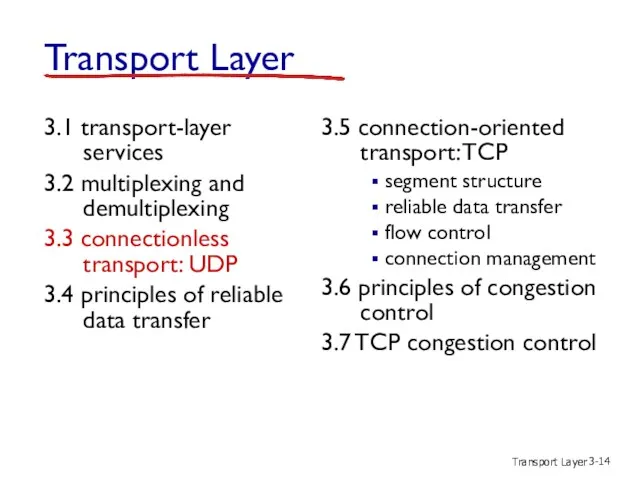
- 15. Transport Layer 3- UDP: User Datagram Protocol [RFC 768] “no frills,” “bare bones” Internet transport protocol
- 16. Transport Layer 3- UDP: segment header source port # dest port # 32 bits application data
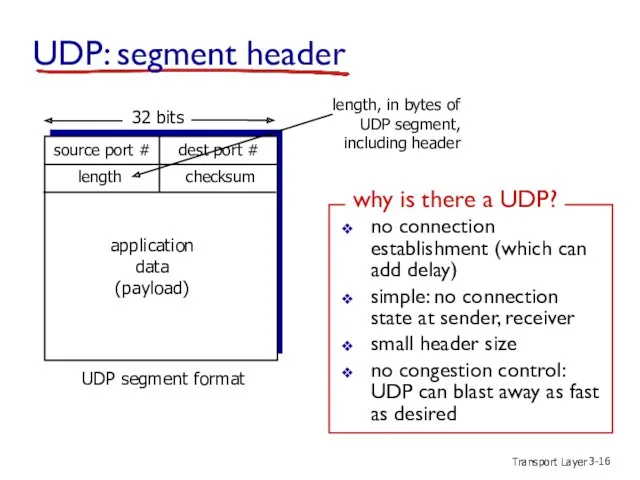
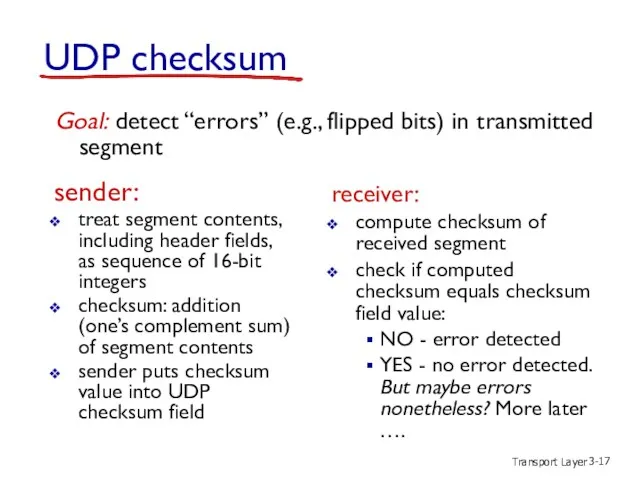
- 17. Transport Layer 3- UDP checksum sender: treat segment contents, including header fields, as sequence of 16-bit
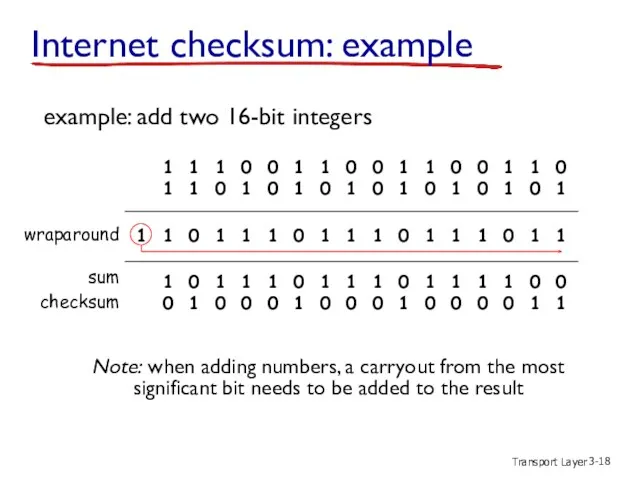
- 18. Transport Layer 3- Internet checksum: example example: add two 16-bit integers 1 1 1 1 0
- 19. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
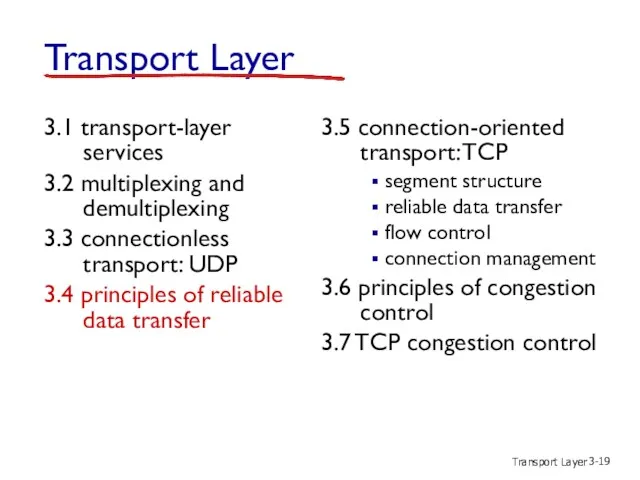
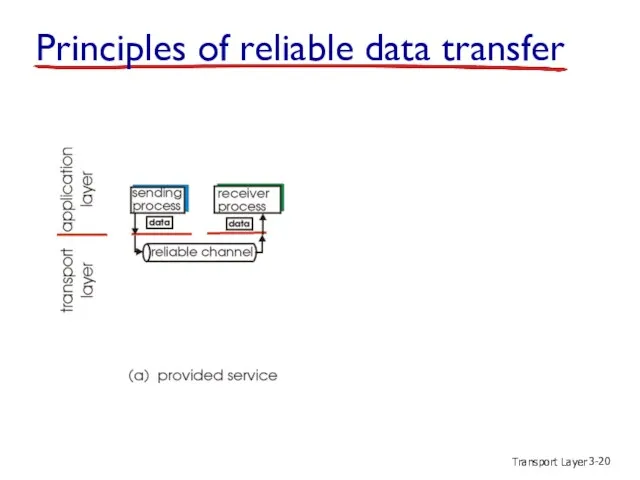
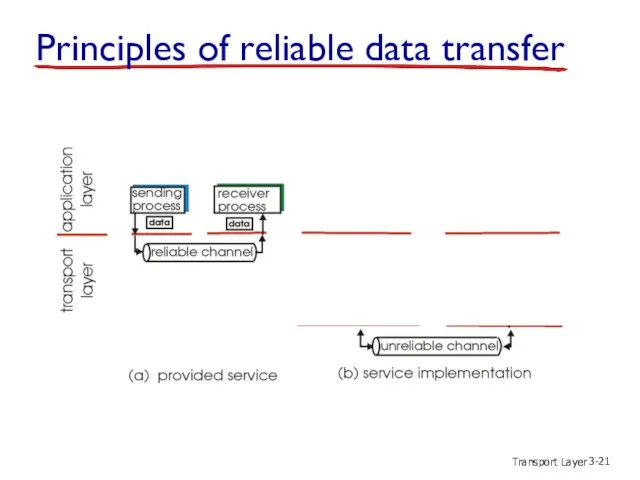
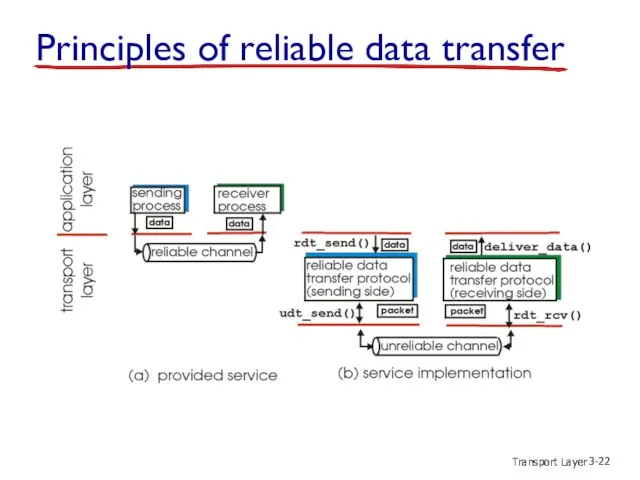
- 20. Transport Layer 3- Principles of reliable data transfer
- 21. Transport Layer 3- Principles of reliable data transfer
- 22. Transport Layer 3- Principles of reliable data transfer
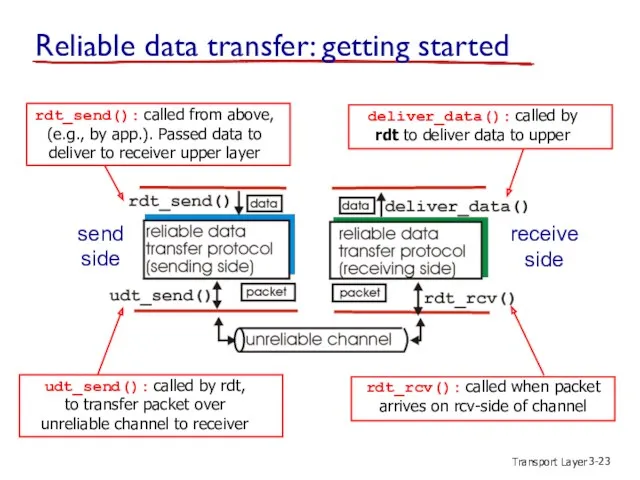
- 23. Transport Layer 3- Reliable data transfer: getting started send side receive side
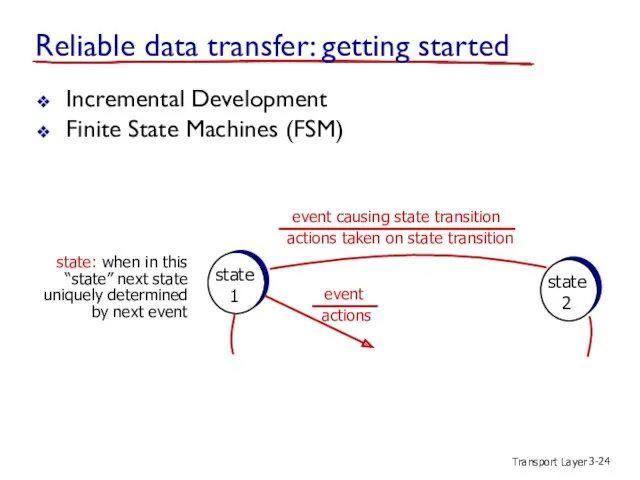
- 24. Transport Layer 3- Incremental Development Finite State Machines (FSM) state 1 state 2 event causing state
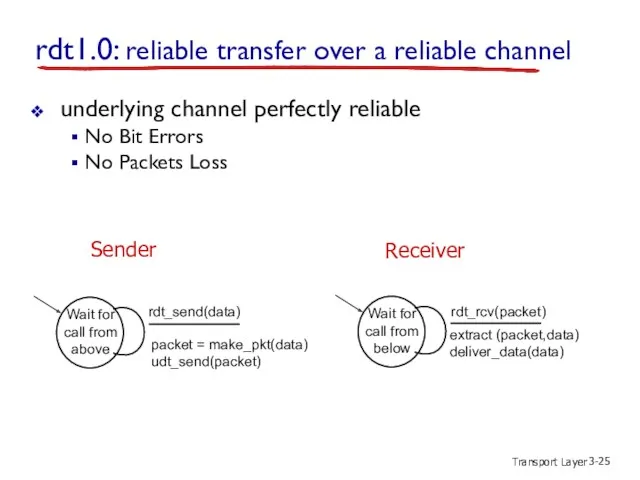
- 25. Transport Layer 3- rdt1.0: reliable transfer over a reliable channel underlying channel perfectly reliable No Bit
- 26. Transport Layer 3- Underlying channel Bit Errors How to detect errors? Checksum How to recover from
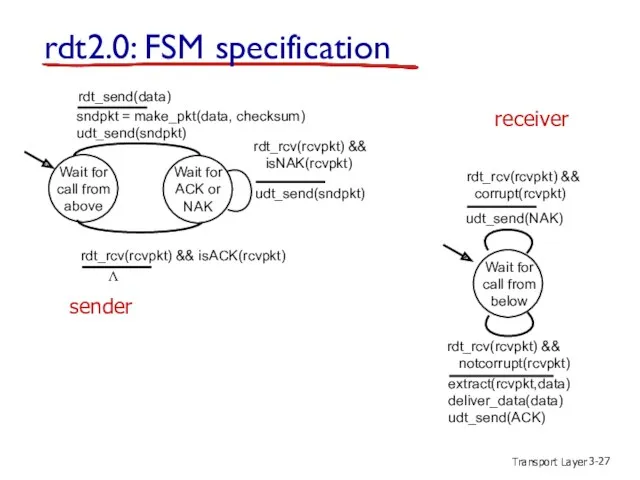
- 27. Transport Layer 3- rdt2.0: FSM specification Wait for call from above sndpkt = make_pkt(data, checksum) udt_send(sndpkt)
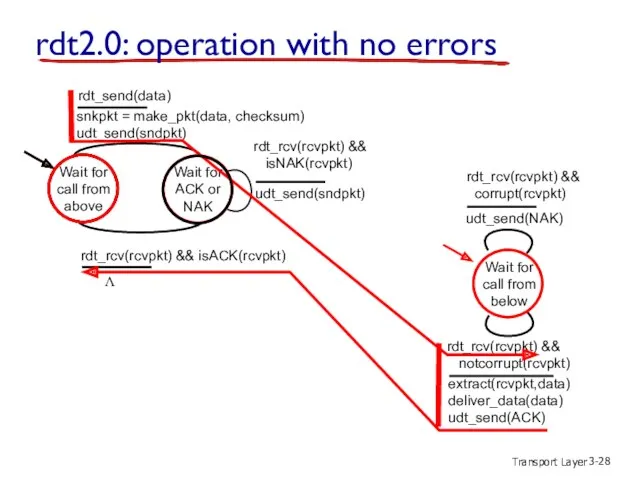
- 28. Transport Layer 3- rdt2.0: operation with no errors Wait for call from above snkpkt = make_pkt(data,
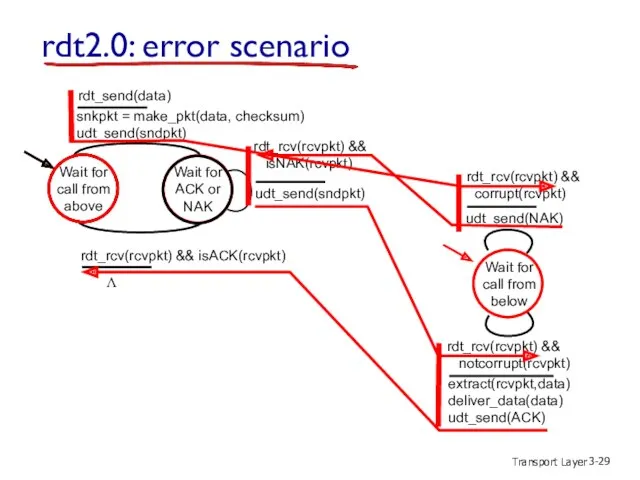
- 29. Transport Layer 3- rdt2.0: error scenario Wait for call from above snkpkt = make_pkt(data, checksum) udt_send(sndpkt)
- 30. Transport Layer 3- rdt2.0 has a fatal flaw! what happens if ACK/NAK corrupted? Retransmit? handling duplicates:
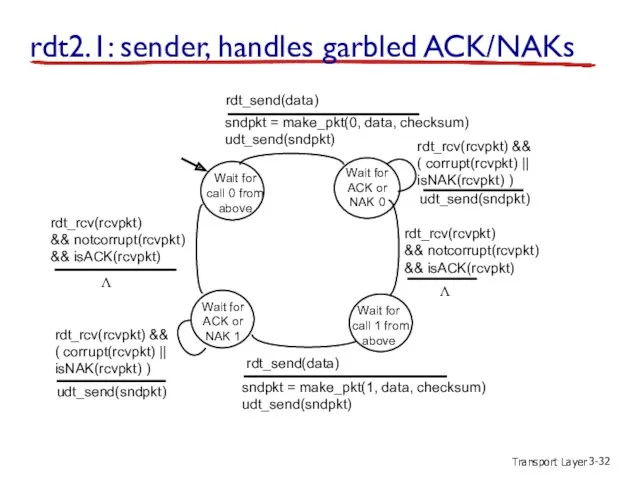
- 31. Transport Layer 3- rdt2.1: sender, handles garbled ACK/NAKs Resend packet when garbled ACK/NAK received Problem Duplicates
- 32. Transport Layer 3- rdt2.1: sender, handles garbled ACK/NAKs Wait for call 0 from above sndpkt =
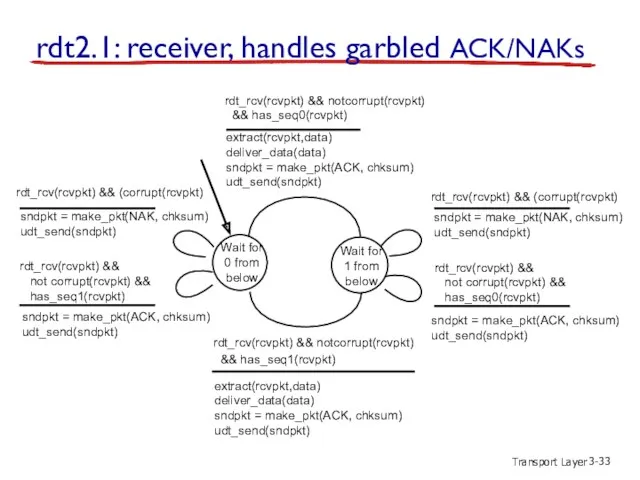
- 33. Transport Layer 3- sndpkt = make_pkt(NAK, chksum) udt_send(sndpkt) rdt_rcv(rcvpkt) && not corrupt(rcvpkt) && has_seq0(rcvpkt) rdt_rcv(rcvpkt) &&
- 34. Transport Layer 3- rdt2.1: discussion sender: seq # added to pkt two seq. #’s (0,1) will
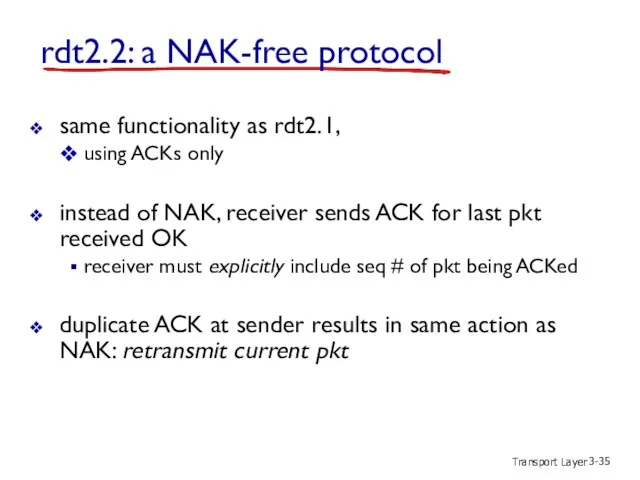
- 35. Transport Layer 3- rdt2.2: a NAK-free protocol same functionality as rdt2.1, using ACKs only instead of
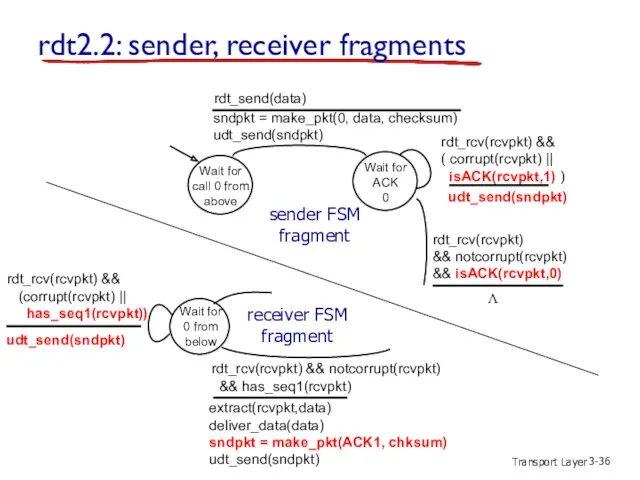
- 36. Transport Layer 3- rdt2.2: sender, receiver fragments
- 37. Transport Layer 3- rdt3.0: channels with errors and loss Underlying Channel Bit Errors Packet loss Error
- 38. Transport Layer 3- rdt3.0: how to detect packet loss? Sender waits “reasonable” amount of time for
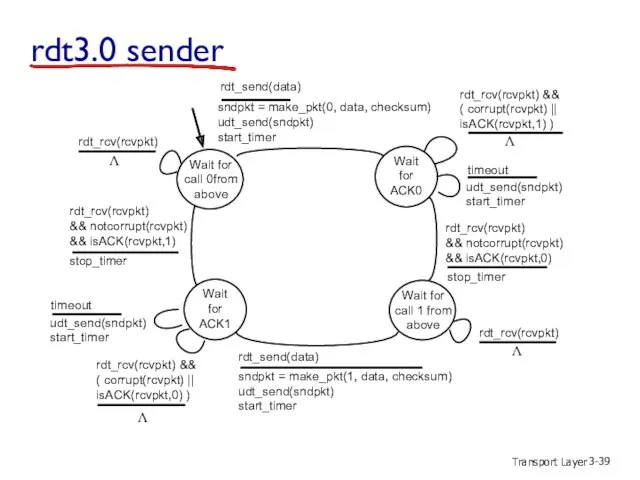
- 39. Transport Layer 3- rdt3.0 sender sndpkt = make_pkt(0, data, checksum) udt_send(sndpkt) start_timer rdt_send(data) rdt_rcv(rcvpkt) && (
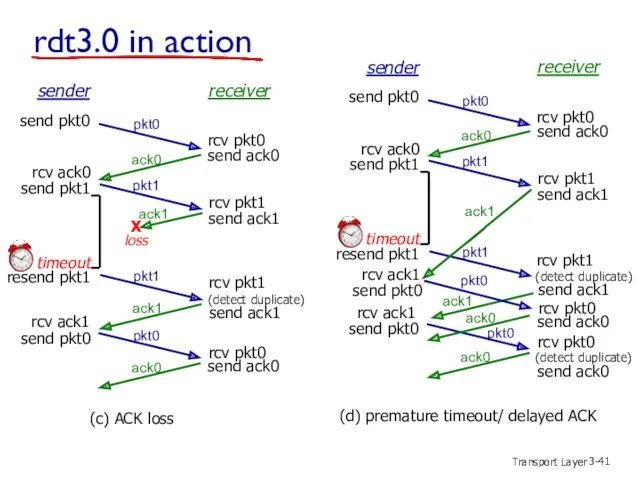
- 40. Transport Layer 3- sender receiver rcv pkt1 rcv pkt0 send ack0 send ack1 send ack0 rcv
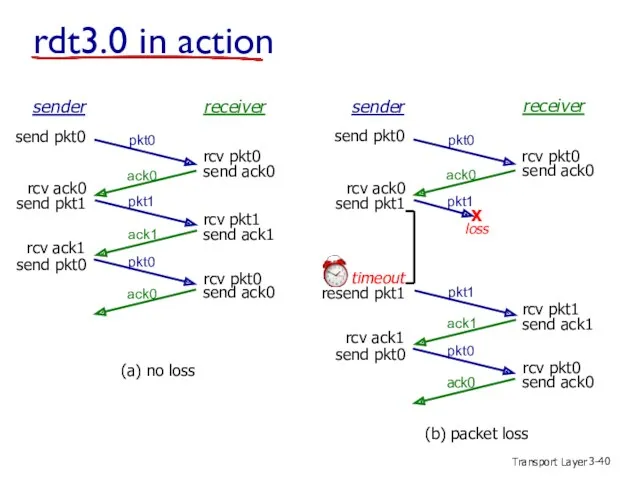
- 41. Transport Layer 3- rdt3.0 in action rcv pkt1 send ack1 (detect duplicate) sender receiver rcv pkt1
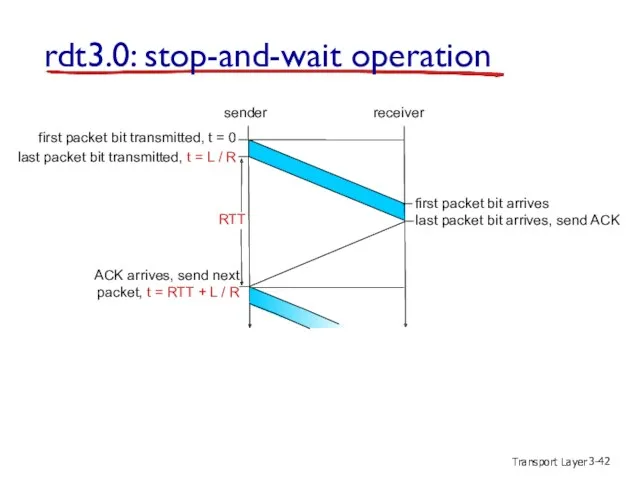
- 42. Transport Layer 3- rdt3.0: stop-and-wait operation first packet bit transmitted, t = 0 sender receiver RTT
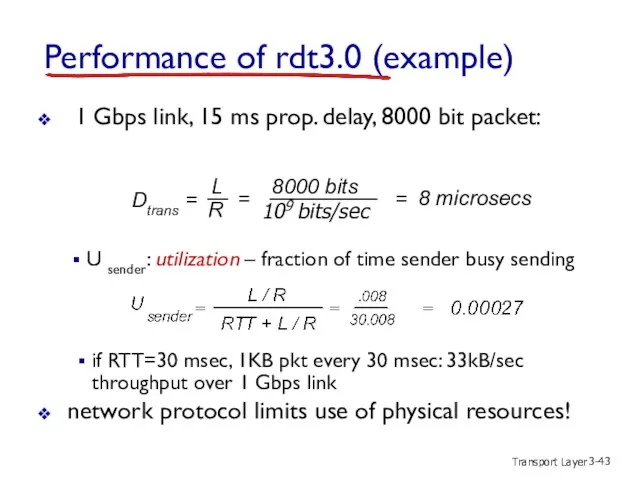
- 43. Transport Layer 3- Performance of rdt3.0 (example) 1 Gbps link, 15 ms prop. delay, 8000 bit
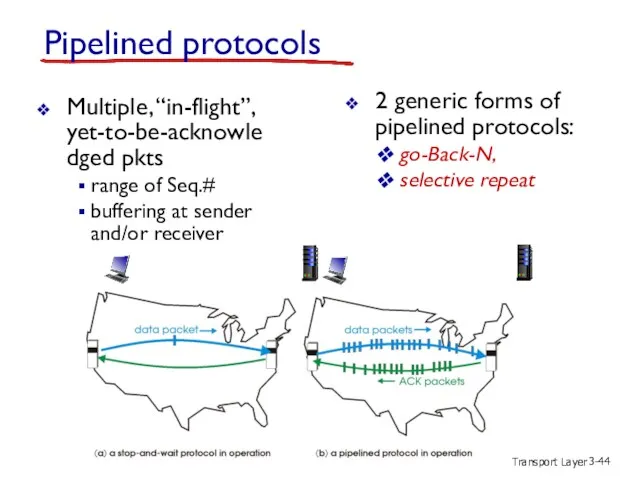
- 44. Transport Layer 3- Pipelined protocols Multiple, “in-flight”, yet-to-be-acknowledged pkts range of Seq.# buffering at sender and/or
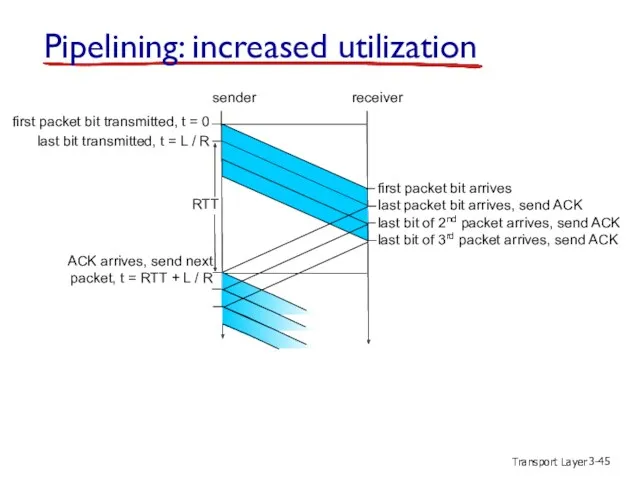
- 45. Transport Layer 3- Pipelining: increased utilization first packet bit transmitted, t = 0 sender receiver RTT
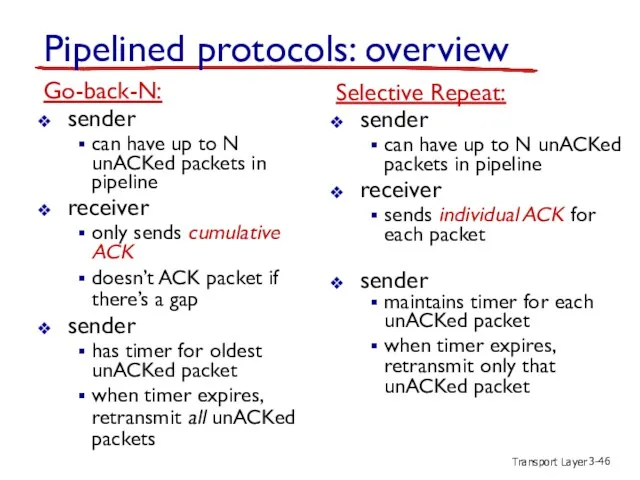
- 46. Transport Layer 3- Pipelined protocols: overview Go-back-N: sender can have up to N unACKed packets in
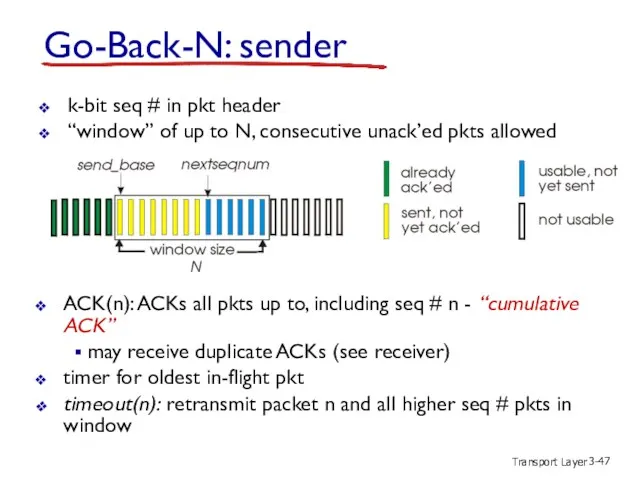
- 47. Transport Layer 3- Go-Back-N: sender k-bit seq # in pkt header “window” of up to N,
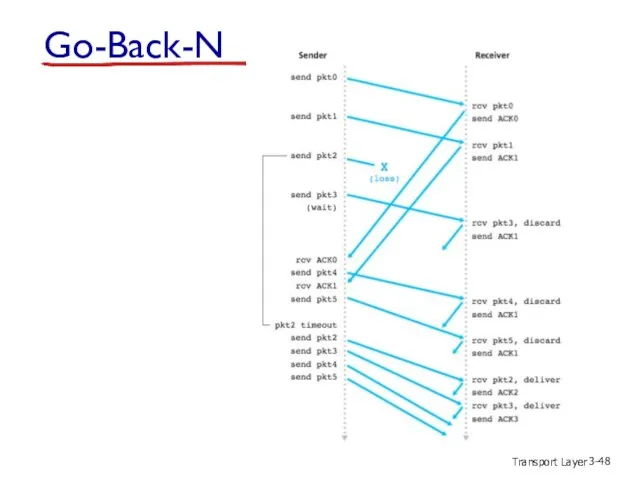
- 48. Transport Layer 3- Go-Back-N
- 49. Transport Layer 3- GBN: sender extended FSM start_timer udt_send(sndpkt[base]) udt_send(sndpkt[base+1]) … udt_send(sndpkt[nextseqnum-1]) timeout rdt_send(data) if (nextseqnum
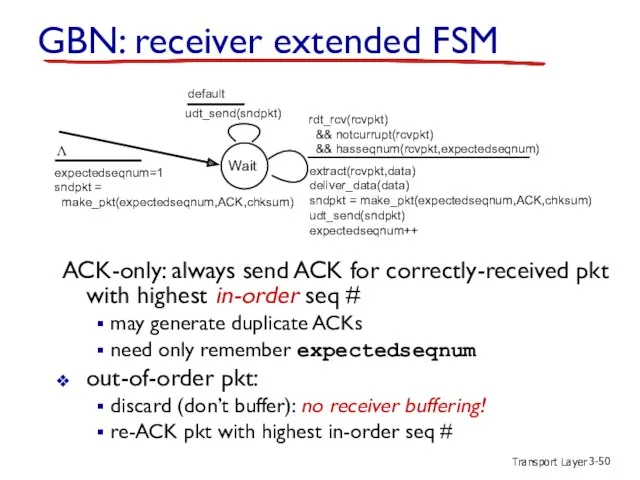
- 50. Transport Layer 3- ACK-only: always send ACK for correctly-received pkt with highest in-order seq # may
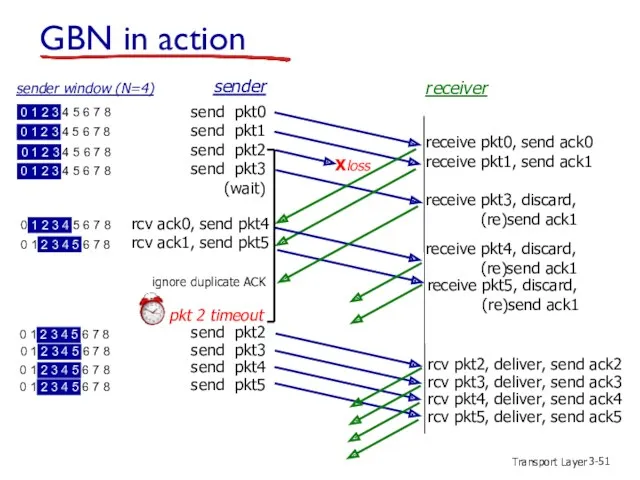
- 51. Transport Layer 3- GBN in action send pkt0 send pkt1 send pkt2 send pkt3 (wait) sender
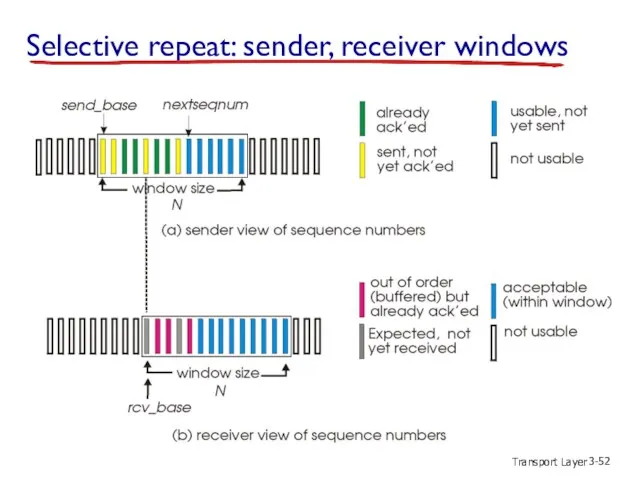
- 52. Transport Layer 3- Selective repeat: sender, receiver windows
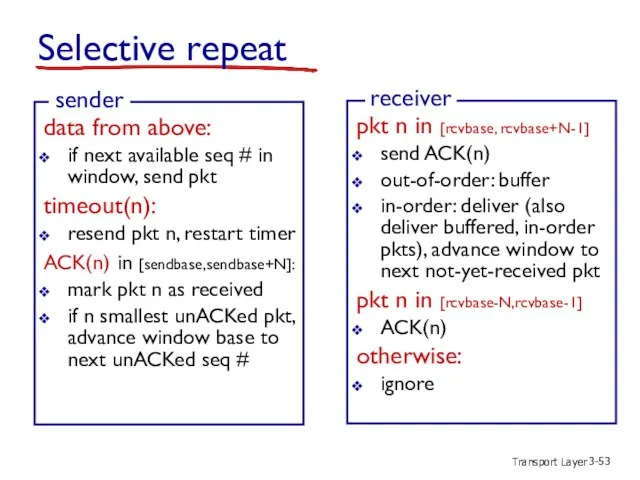
- 53. Transport Layer 3- Selective repeat data from above: if next available seq # in window, send
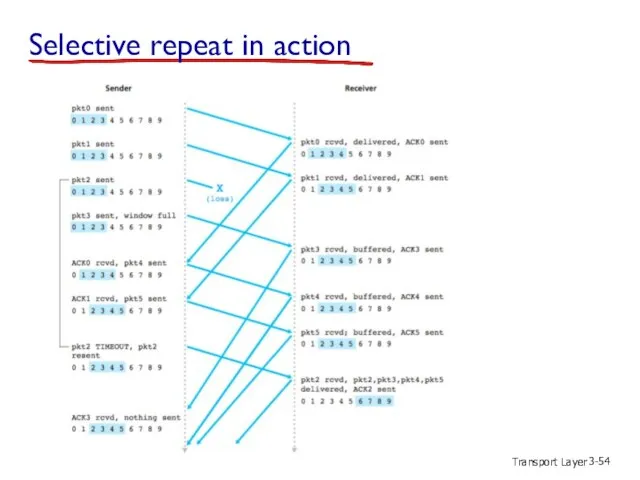
- 54. Transport Layer 3- Selective repeat in action
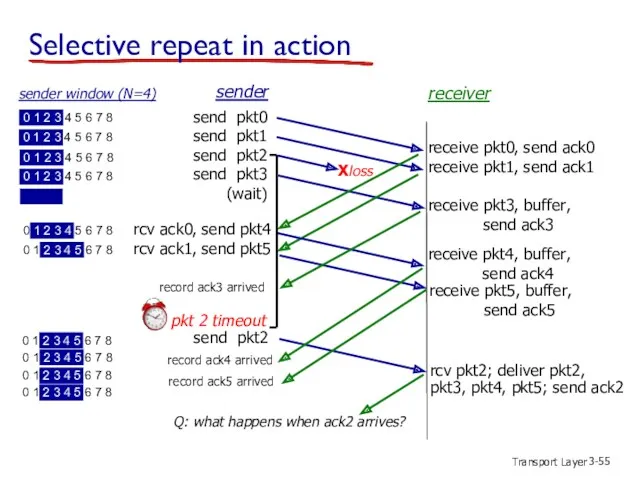
- 55. Transport Layer 3- Selective repeat in action send pkt0 send pkt1 send pkt2 send pkt3 (wait)
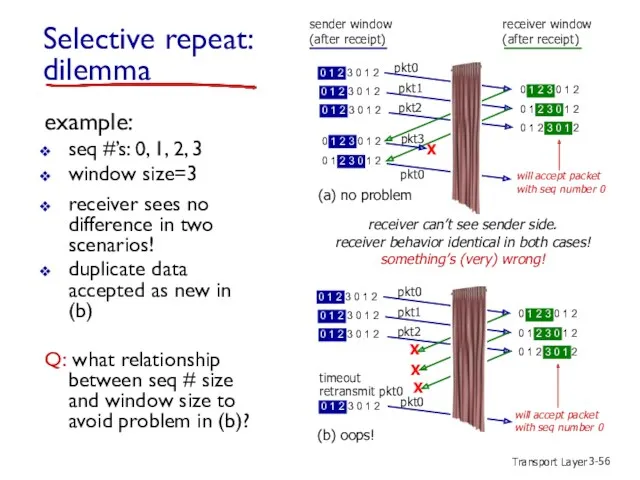
- 56. Transport Layer 3- Selective repeat: dilemma example: seq #’s: 0, 1, 2, 3 window size=3 receiver
- 57. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
- 58. Transport Layer 3- TCP: Overview RFCs: 793,1122,1323, 2018, 2581 full duplex data connection-oriented flow controlled congestion
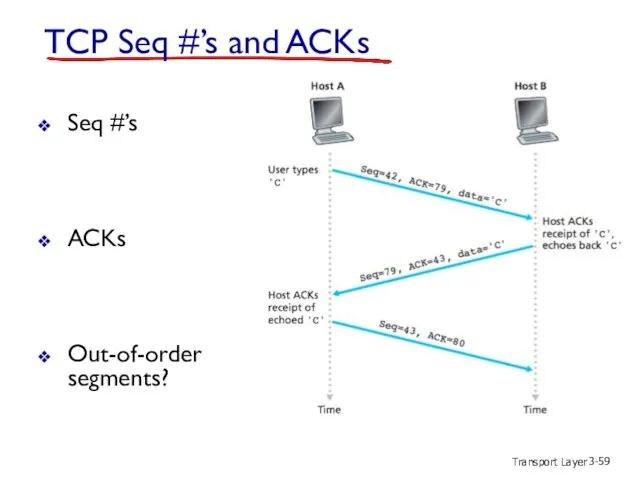
- 59. Transport Layer 3- TCP Seq #’s and ACKs Seq #’s ACKs Out-of-order segments?
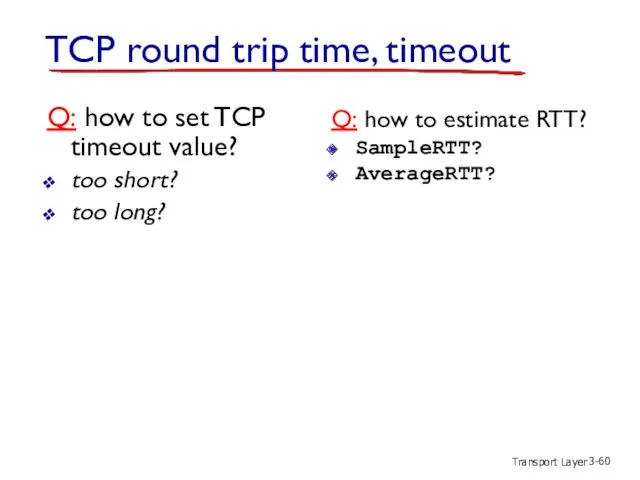
- 60. Transport Layer 3- TCP round trip time, timeout Q: how to set TCP timeout value? too
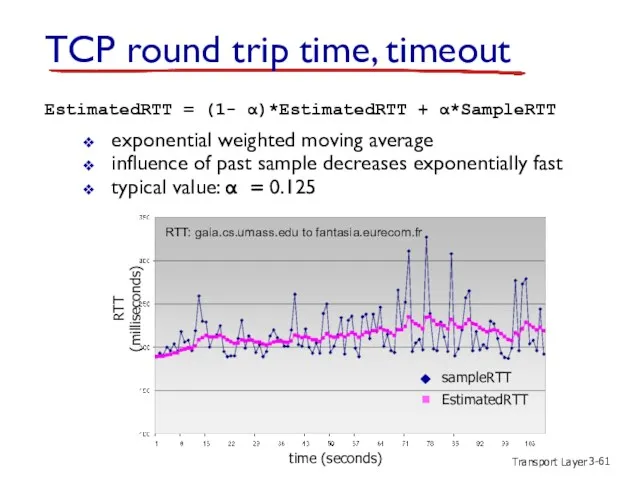
- 61. Transport Layer 3- EstimatedRTT = (1- α)*EstimatedRTT + α*SampleRTT exponential weighted moving average influence of past
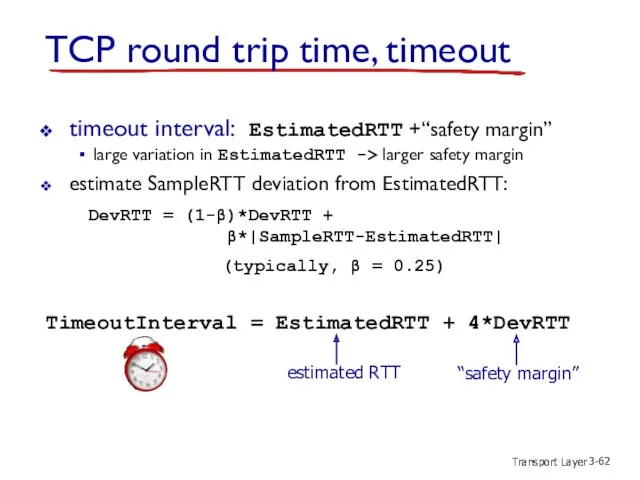
- 62. Transport Layer 3- timeout interval: EstimatedRTT +“safety margin” large variation in EstimatedRTT -> larger safety margin
- 63. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
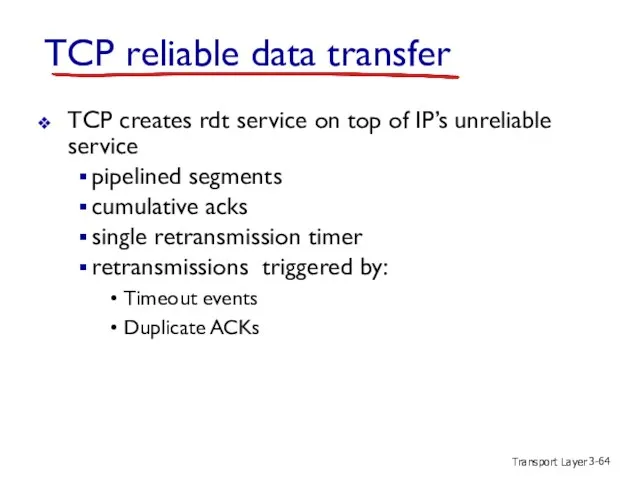
- 64. Transport Layer 3- TCP reliable data transfer TCP creates rdt service on top of IP’s unreliable
- 65. Transport Layer 3- TCP sender events: 1. Data rcvd from app 2. Timeout 3. ACK rcvd
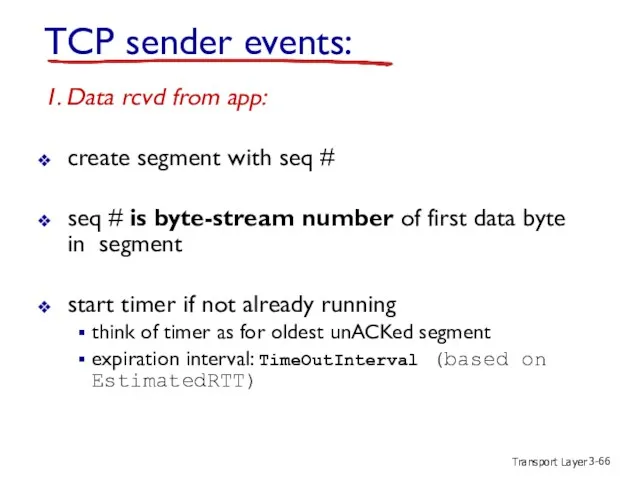
- 66. Transport Layer 3- TCP sender events: 1. Data rcvd from app: create segment with seq #
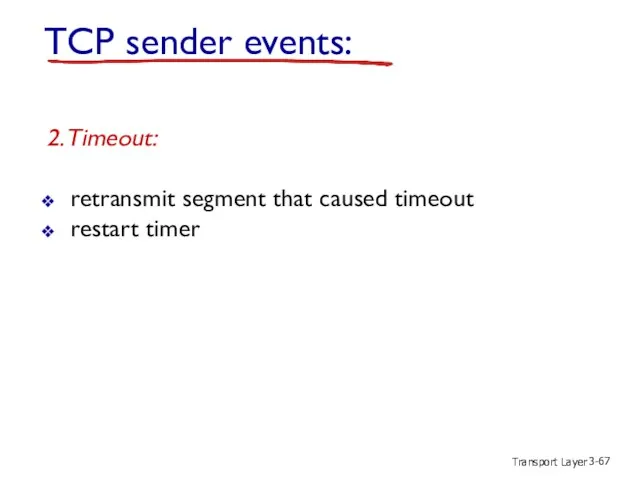
- 67. Transport Layer 3- TCP sender events: 2. Timeout: retransmit segment that caused timeout restart timer
- 68. Transport Layer 3- TCP sender events: 3. ACK rcvd: If ACK acknowledges previously unACKed segments update
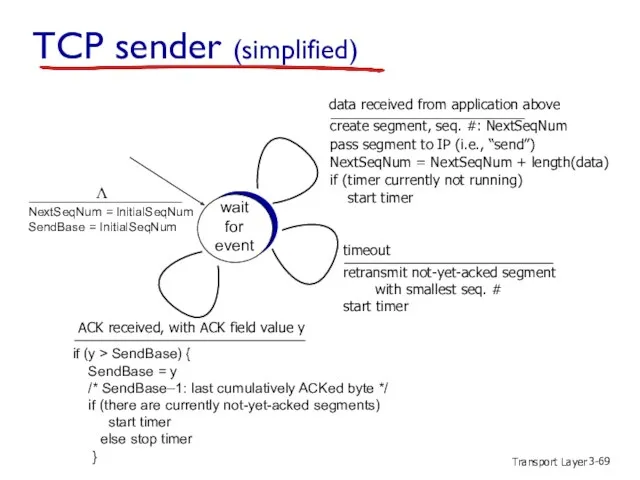
- 69. Transport Layer 3- TCP sender (simplified) wait for event NextSeqNum = InitialSeqNum SendBase = InitialSeqNum Λ
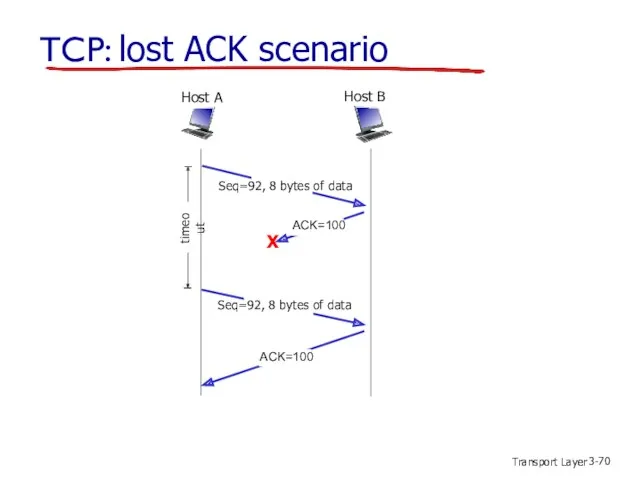
- 70. Transport Layer 3- TCP: lost ACK scenario Host B Host A Seq=92, 8 bytes of data
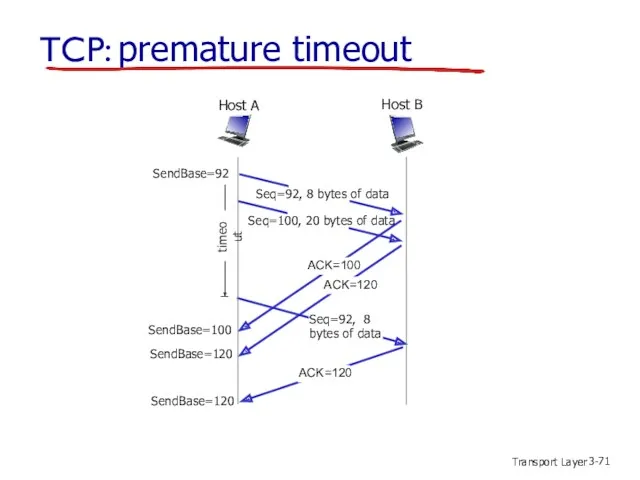
- 71. Transport Layer 3- TCP: premature timeout Host B Host A Seq=92, 8 bytes of data Seq=92,
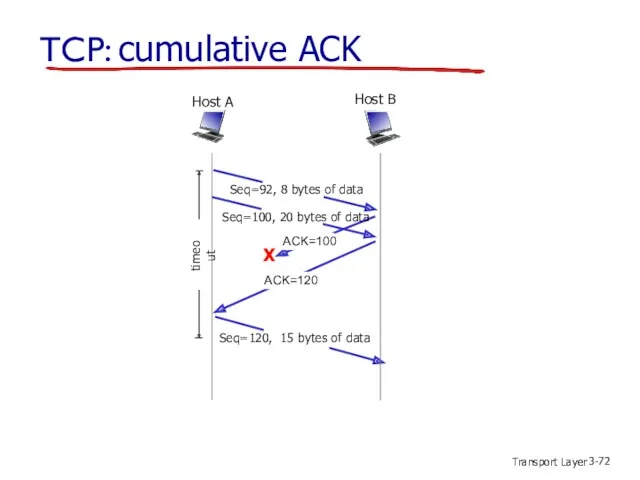
- 72. Transport Layer 3- TCP: cumulative ACK X Host B Host A Seq=92, 8 bytes of data
- 73. Transport Layer 3- TCP ACK generation [RFC 1122, RFC 2581] event at receiver arrival of in-order
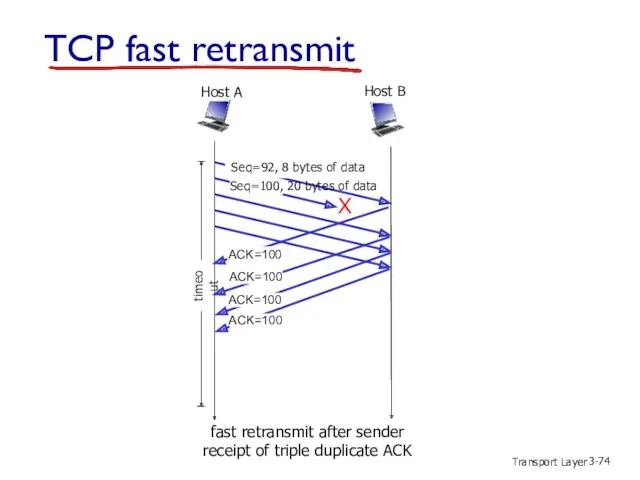
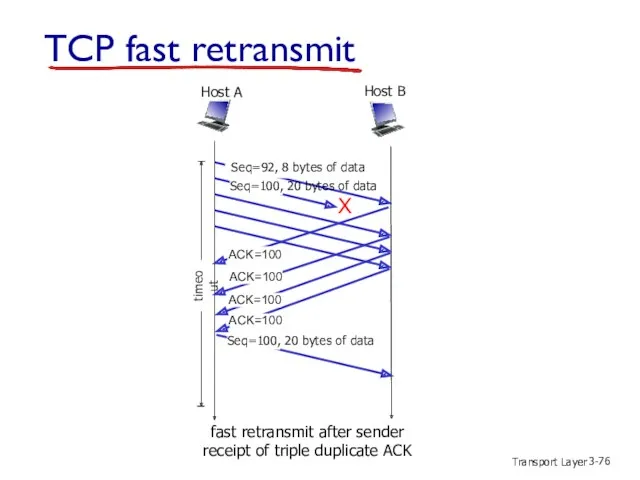
- 74. Transport Layer 3- X fast retransmit after sender receipt of triple duplicate ACK Host B Host
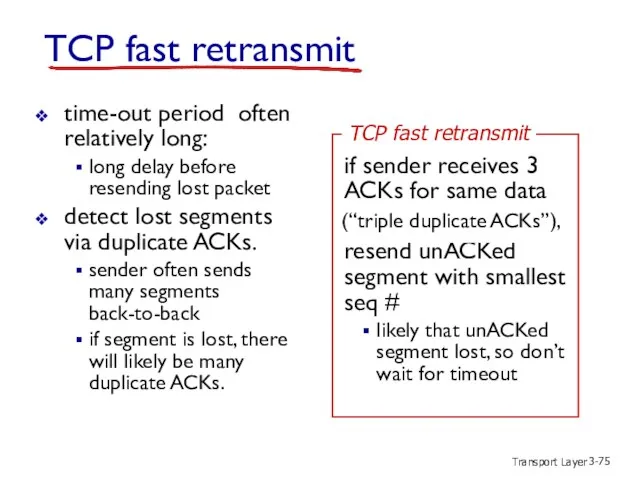
- 75. Transport Layer 3- TCP fast retransmit time-out period often relatively long: long delay before resending lost
- 76. Transport Layer 3- X fast retransmit after sender receipt of triple duplicate ACK Host B Host
- 77. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
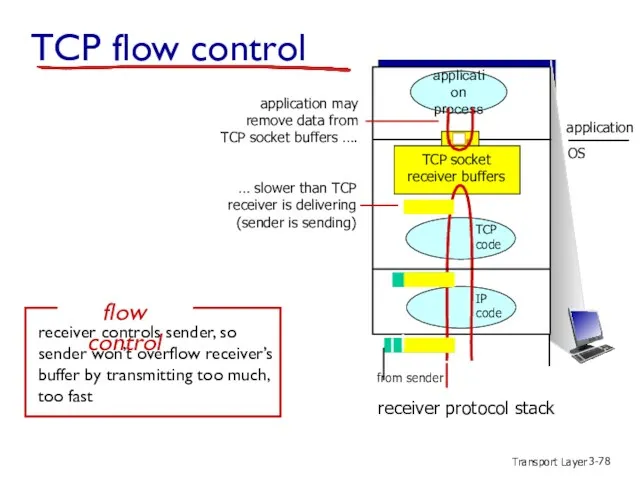
- 78. Transport Layer 3- TCP flow control application process TCP code IP code receiver protocol stack application
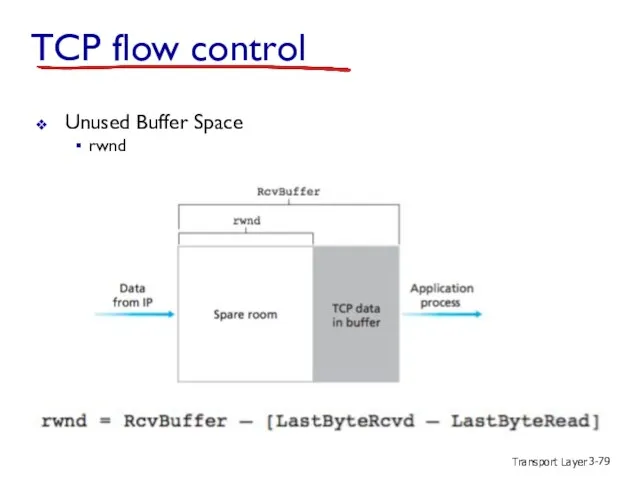
- 79. Transport Layer 3- TCP flow control Unused Buffer Space rwnd
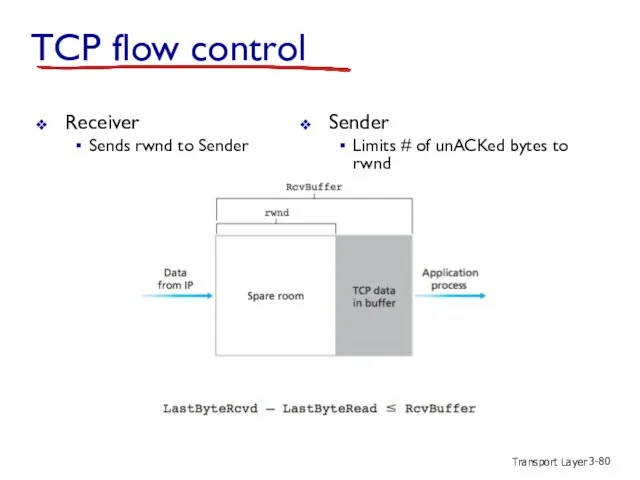
- 80. Transport Layer 3- TCP flow control Receiver Sends rwnd to Sender Sender Limits # of unACKed
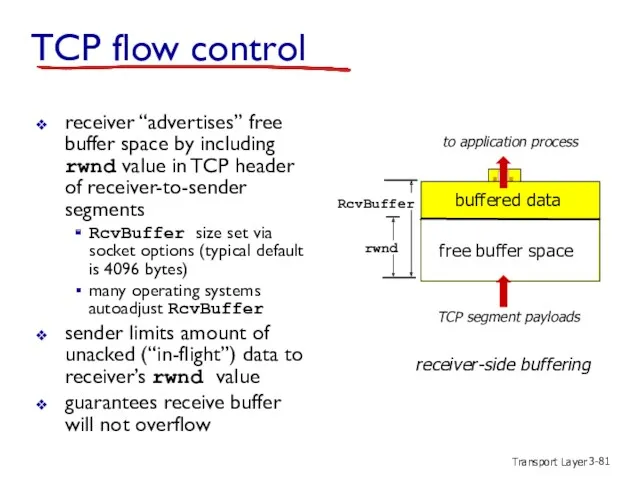
- 81. Transport Layer 3- TCP flow control rwnd RcvBuffer TCP segment payloads to application process receiver “advertises”
- 82. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
- 83. Transport Layer 3- TCP Connection Management Connection-Oriented TCP Variables Seq #s Buffers Flow Control (rwnd)
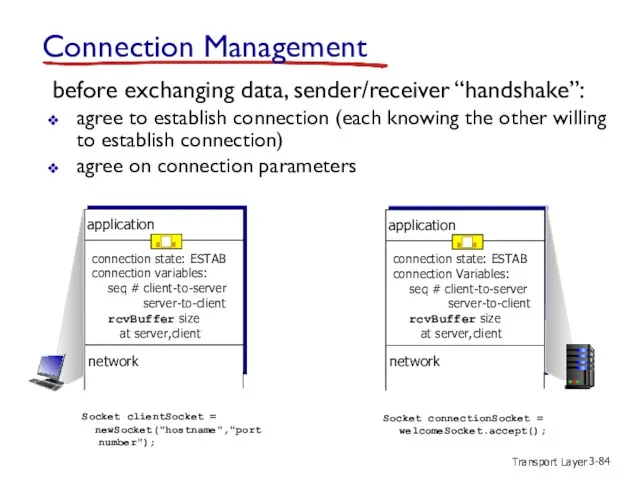
- 84. Transport Layer 3- Connection Management before exchanging data, sender/receiver “handshake”: agree to establish connection (each knowing
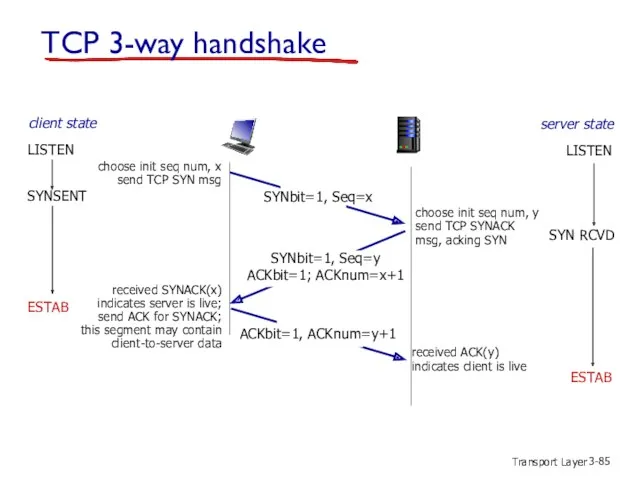
- 85. Transport Layer 3- TCP 3-way handshake ESTAB
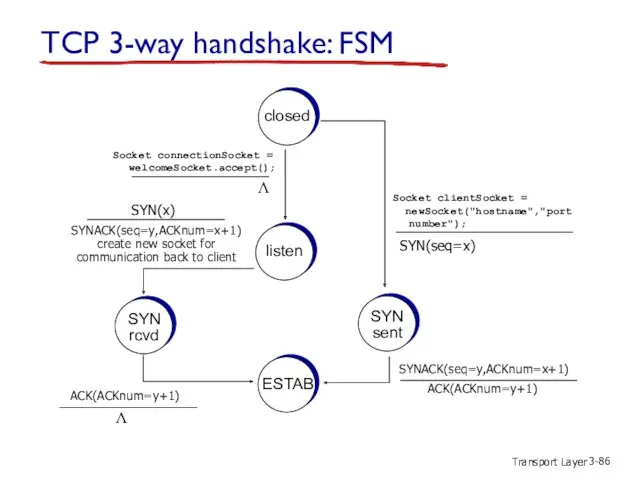
- 86. Transport Layer 3- TCP 3-way handshake: FSM closed Λ listen SYN rcvd SYN sent ESTAB Socket
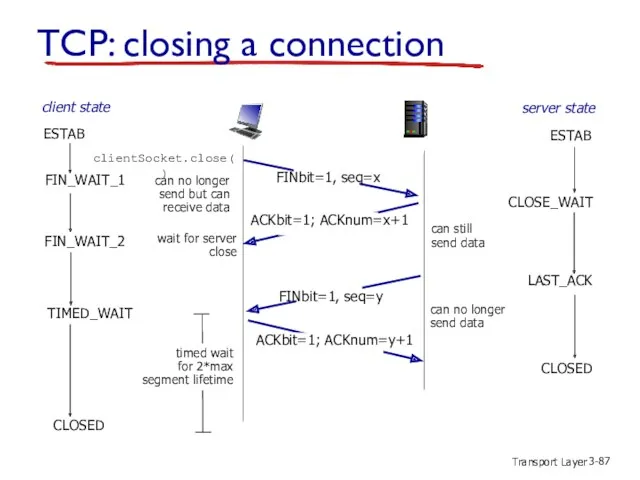
- 87. Transport Layer 3- TCP: closing a connection client state server state ESTAB ESTAB
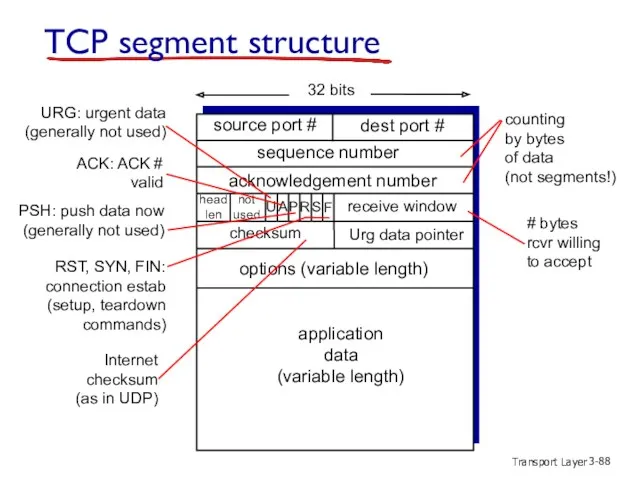
- 88. Transport Layer 3- TCP segment structure source port # dest port # 32 bits application data
- 89. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
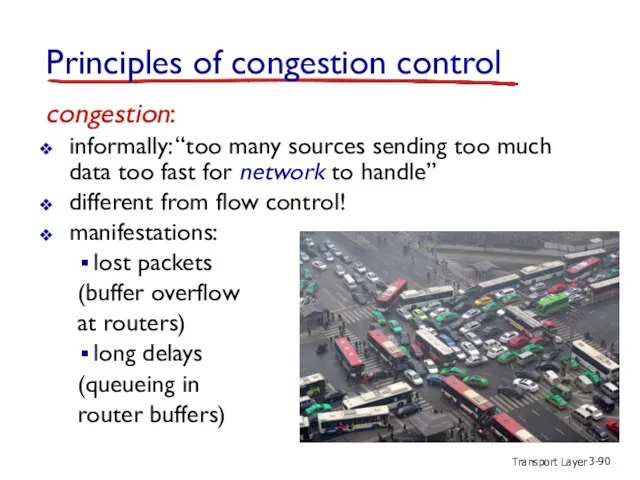
- 90. Transport Layer 3- congestion: informally: “too many sources sending too much data too fast for network
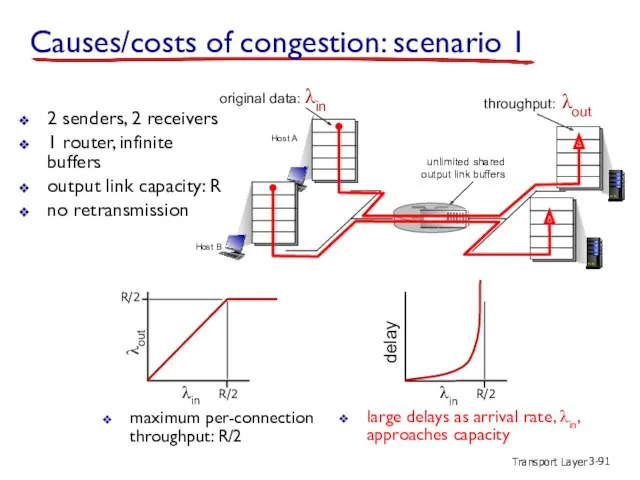
- 91. Transport Layer 3- Causes/costs of congestion: scenario 1 2 senders, 2 receivers 1 router, infinite buffers
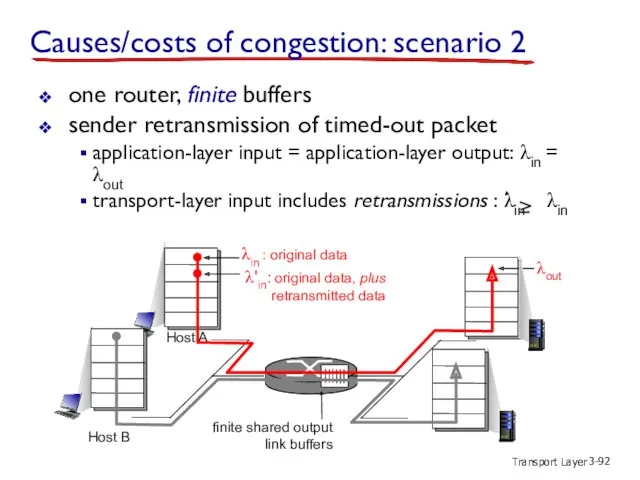
- 92. Transport Layer 3- one router, finite buffers sender retransmission of timed-out packet application-layer input = application-layer
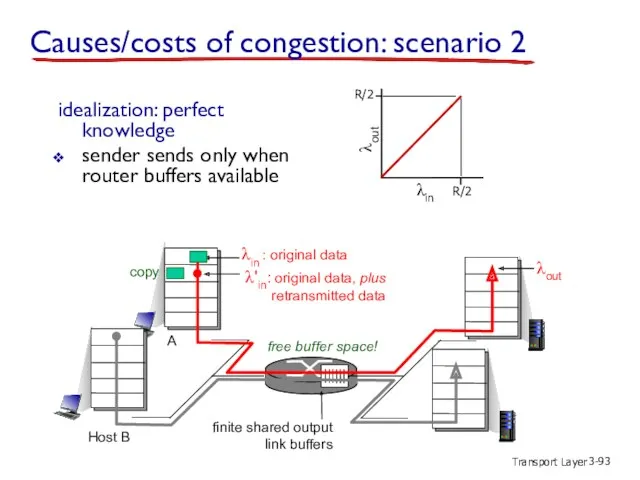
- 93. Transport Layer 3- idealization: perfect knowledge sender sends only when router buffers available finite shared output
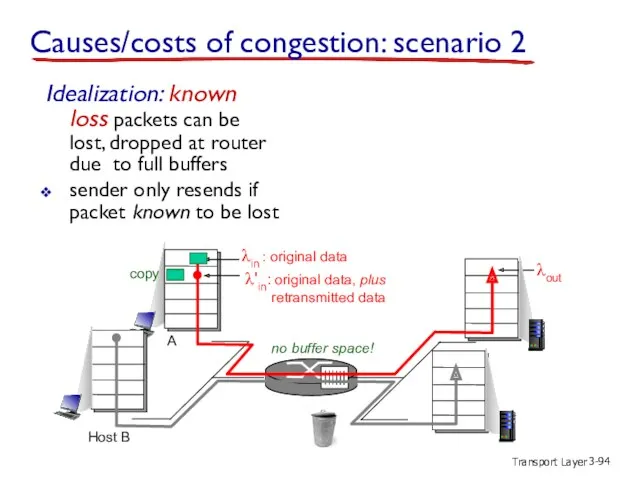
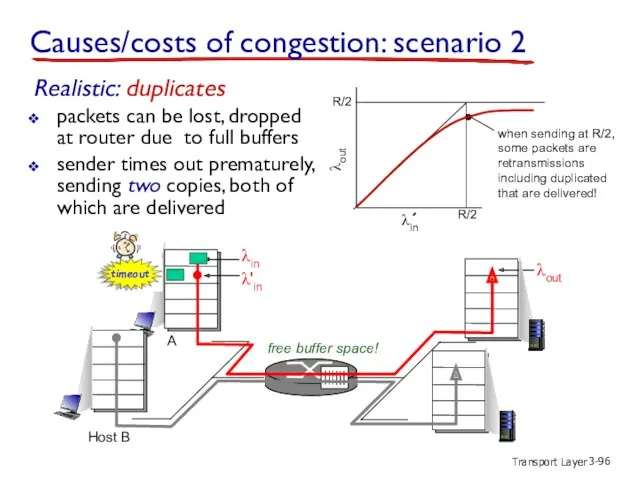
- 94. Transport Layer 3- λin : original data λout λ'in: original data, plus retransmitted data copy no
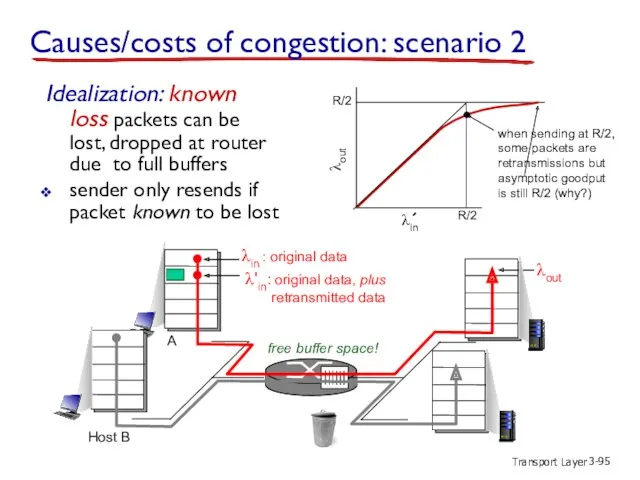
- 95. Transport Layer 3- λin : original data λout λ'in: original data, plus retransmitted data free buffer
- 96. Transport Layer 3- A λin λout λ'in copy free buffer space! R/2 R/2 λout Host B
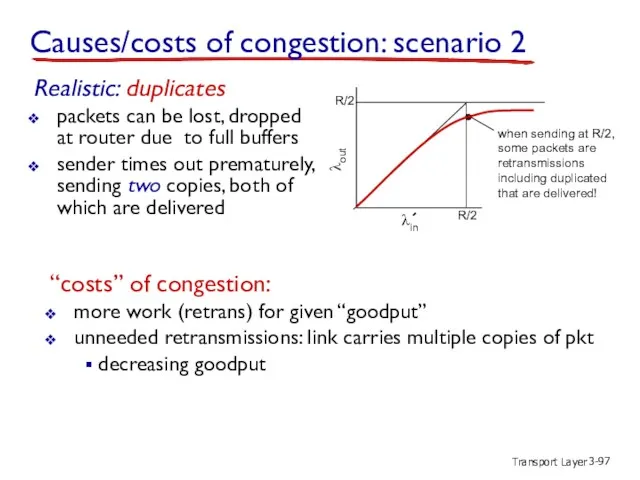
- 97. Transport Layer 3- R/2 λout “costs” of congestion: more work (retrans) for given “goodput” unneeded retransmissions:
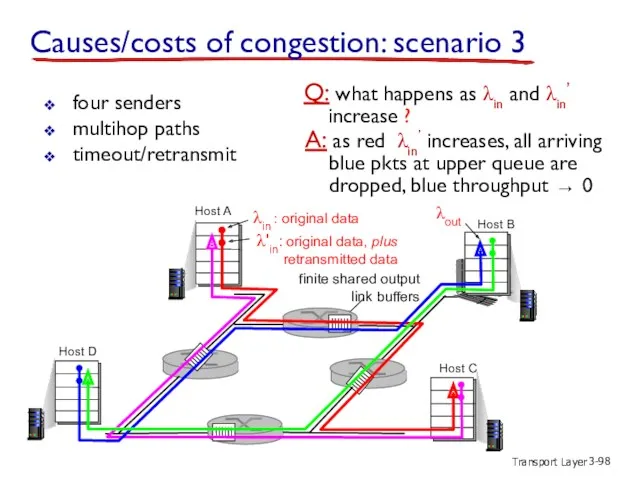
- 98. Transport Layer 3- four senders multihop paths timeout/retransmit Q: what happens as λin and λin’ increase
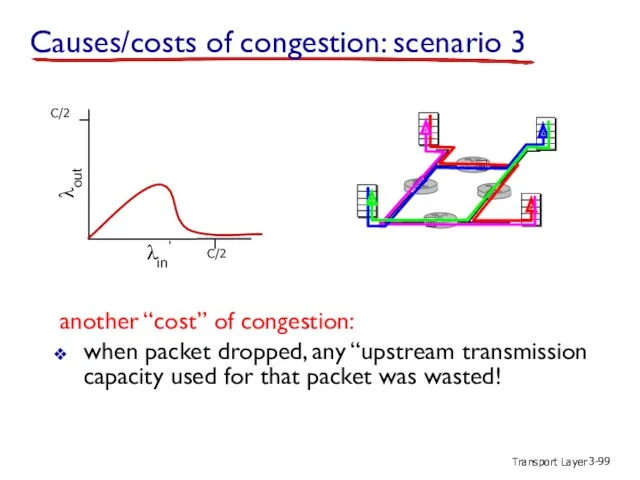
- 99. Transport Layer 3- another “cost” of congestion: when packet dropped, any “upstream transmission capacity used for
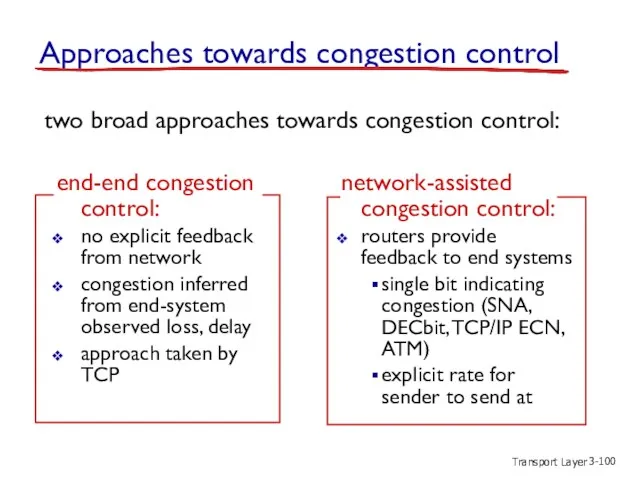
- 100. Transport Layer 3- Approaches towards congestion control two broad approaches towards congestion control: end-end congestion control:
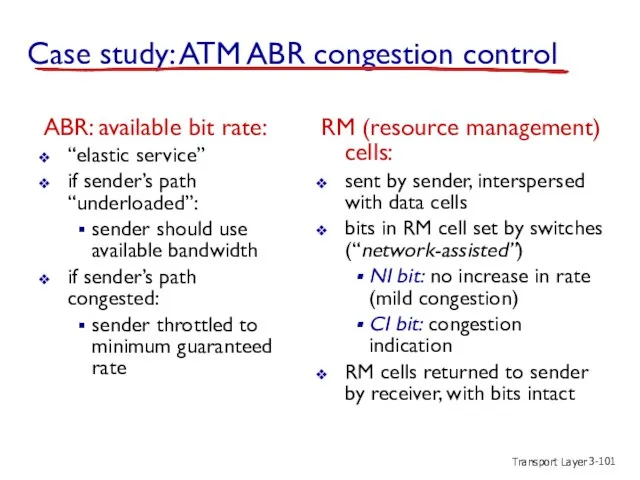
- 101. Transport Layer 3- Case study: ATM ABR congestion control ABR: available bit rate: “elastic service” if
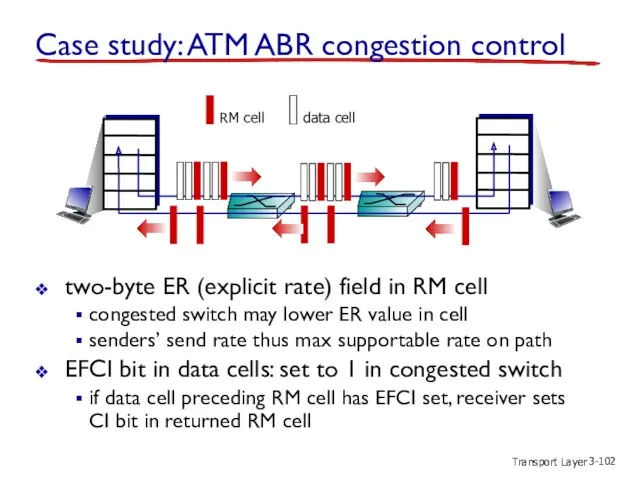
- 102. Transport Layer 3- Case study: ATM ABR congestion control two-byte ER (explicit rate) field in RM
- 103. Transport Layer 3- Transport Layer 3.1 transport-layer services 3.2 multiplexing and demultiplexing 3.3 connectionless transport: UDP
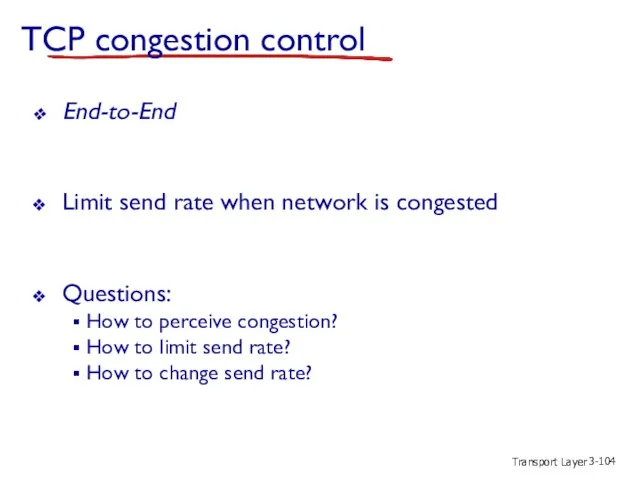
- 104. Transport Layer 3- TCP congestion control End-to-End Limit send rate when network is congested Questions: How
- 105. Transport Layer 3- How to perceive congestion? Implicit End-to-End Feedback ACK Received: ? ACK not Received:
- 106. Transport Layer 3- How to limit send rate? Limit # of unACKed bytes in pipeline cwnd
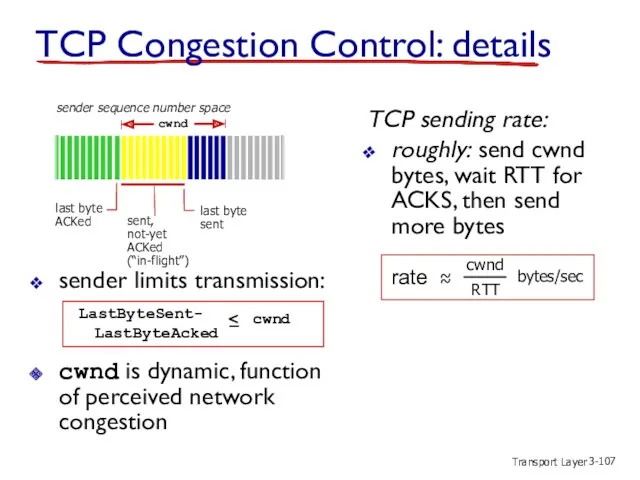
- 107. Transport Layer 3- TCP Congestion Control: details sender limits transmission: cwnd is dynamic, function of perceived
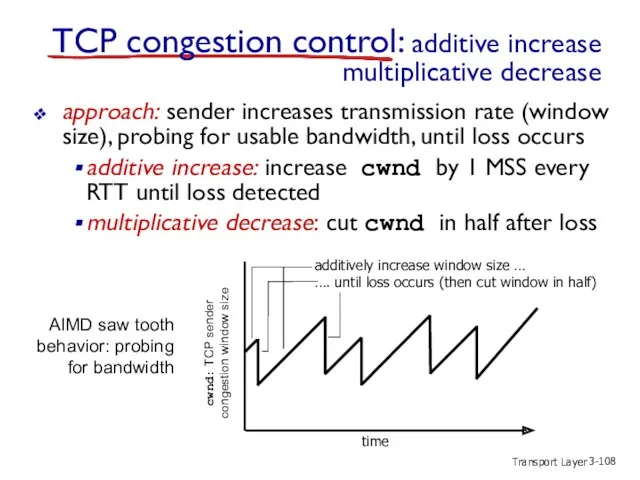
- 108. Transport Layer 3- TCP congestion control: additive increase multiplicative decrease approach: sender increases transmission rate (window
- 109. Transport Layer 3- Success Event If ACK received – increase the cwnd Slowstart Increase Exponentially Connection
- 110. Transport Layer 3- Loss Event If segment lost – decrease the cwnd Timeout Cut cwnd to
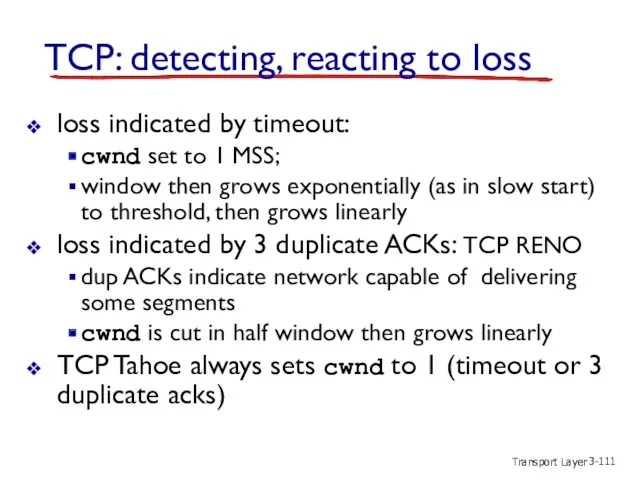
- 111. Transport Layer 3- TCP: detecting, reacting to loss loss indicated by timeout: cwnd set to 1
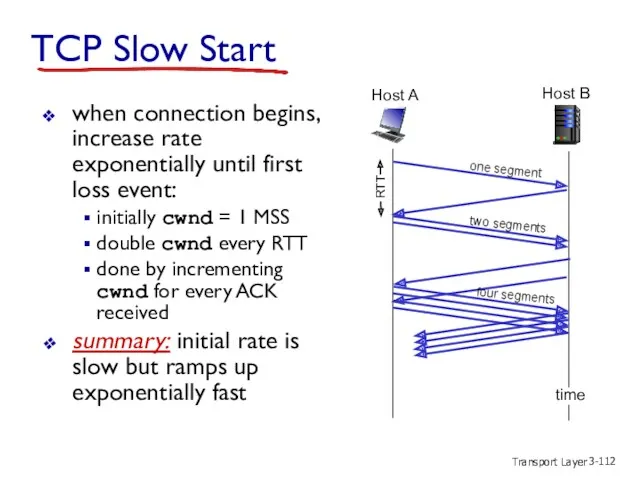
- 112. Transport Layer 3- TCP Slow Start when connection begins, increase rate exponentially until first loss event:
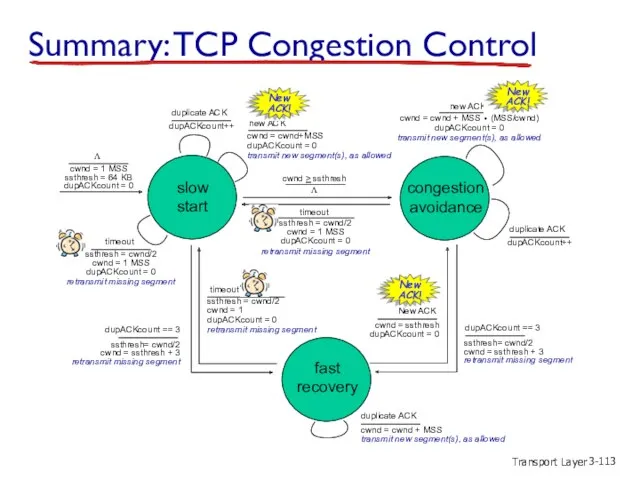
- 113. Transport Layer 3- Summary: TCP Congestion Control
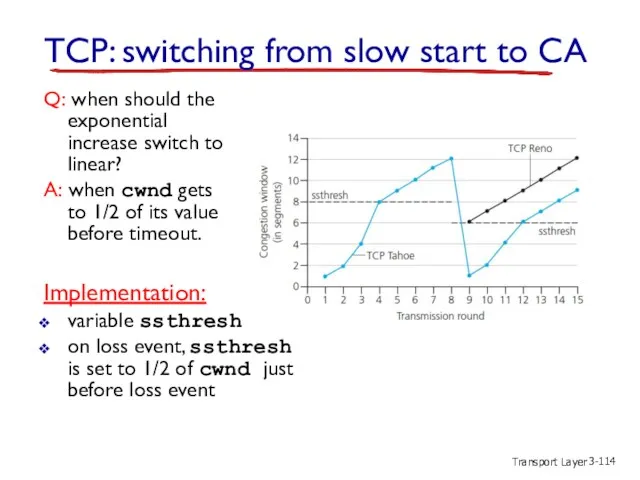
- 114. Transport Layer 3- Q: when should the exponential increase switch to linear? A: when cwnd gets
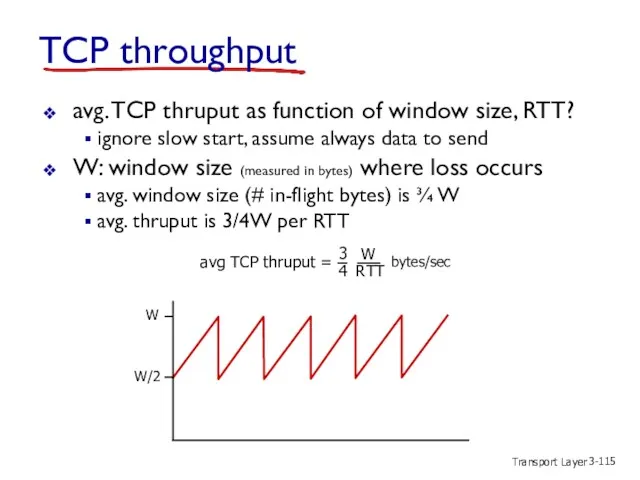
- 115. Transport Layer 3- TCP throughput avg. TCP thruput as function of window size, RTT? ignore slow
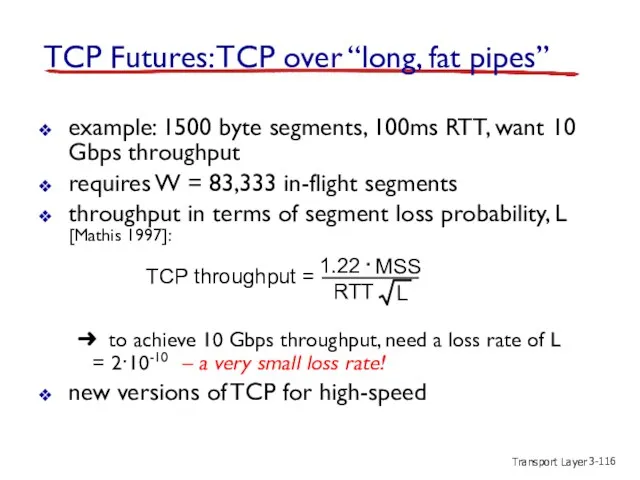
- 116. Transport Layer 3- TCP Futures: TCP over “long, fat pipes” example: 1500 byte segments, 100ms RTT,
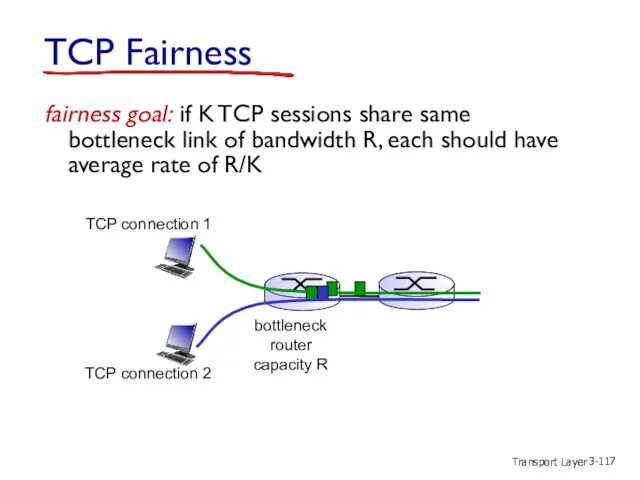
- 117. Transport Layer 3- fairness goal: if K TCP sessions share same bottleneck link of bandwidth R,
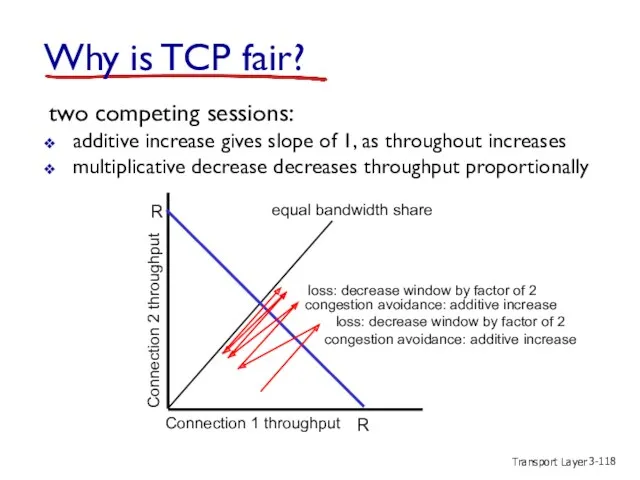
- 118. Transport Layer 3- Why is TCP fair? two competing sessions: additive increase gives slope of 1,
- 119. Transport Layer 3- Fairness (more) Fairness and UDP multimedia apps often do not use TCP do
- 121. Скачать презентацию
![Transport Layer 3- UDP: User Datagram Protocol [RFC 768] “no](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/425901/slide-14.jpg)






![Transport Layer 3- GBN: sender extended FSM start_timer udt_send(sndpkt[base]) udt_send(sndpkt[base+1])](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/425901/slide-48.jpg)

![Transport Layer 3- TCP ACK generation [RFC 1122, RFC 2581]](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/425901/slide-72.jpg)




 Чем полезен интернет — польза всемирной паутины
Чем полезен интернет — польза всемирной паутины Примеры разработки программ. Задача о разложении функции. Задача о площади пересечения прямоугольников
Примеры разработки программ. Задача о разложении функции. Задача о площади пересечения прямоугольников Решения для электронного правительства и электронизация государственных услуг — БАРС Груп
Решения для электронного правительства и электронизация государственных услуг — БАРС Груп Журнал Музет. Декабрь 2015
Журнал Музет. Декабрь 2015 Сети, их администрирование
Сети, их администрирование Своя игра информатика 5 класс
Своя игра информатика 5 класс Нейронные сети
Нейронные сети Программное обеспечение для построения систем управления и диспетчеризации различных объектов
Программное обеспечение для построения систем управления и диспетчеризации различных объектов Оператор безусловного перехода GOTO
Оператор безусловного перехода GOTO Современные системы программирования. Состав системы программирования
Современные системы программирования. Состав системы программирования Presentation template
Presentation template Тест по теме:Условный оператор Диск
Тест по теме:Условный оператор Диск Протоколы обмена для линий последовательной передачи данных
Протоколы обмена для линий последовательной передачи данных ZOOM в картинках. Часть 1 (регистрация и настройка)
ZOOM в картинках. Часть 1 (регистрация и настройка) АО ТАСКОМ. Личный Кабинет. Инструкция по оформлению заявок
АО ТАСКОМ. Личный Кабинет. Инструкция по оформлению заявок Стратегическая сессия. Торговый дом КВАРЦ
Стратегическая сессия. Торговый дом КВАРЦ Операторы языка Бейсик. 10 класс
Операторы языка Бейсик. 10 класс Платформа синтеза индивидуальных и системы распределённых ситуационных центров
Платформа синтеза индивидуальных и системы распределённых ситуационных центров Операційні системи
Операційні системи Морское приключение
Морское приключение Реляциялық деректер қоры және SQL тілі
Реляциялық деректер қоры және SQL тілі Классификация программного обеспечения компьютера
Классификация программного обеспечения компьютера Телеграмм-бот по игре Dota
Телеграмм-бот по игре Dota Unity Timeline
Unity Timeline Информация. Субъективный подход к определению информации
Информация. Субъективный подход к определению информации Сетевое и системное администрирование
Сетевое и системное администрирование Динамическая память, динамические переменные
Динамическая память, динамические переменные 3D модуль графического редактора AutoCAD
3D модуль графического редактора AutoCAD